In this section
Understanding Cloud Security - Essential to Your Cybersecurity
What is Cloud Security?
Cloud computing has been widely adopted among organizations of all sizes thanks to the scalability, flexibility, and speed of deployment it allows. By using public and/or private clouds, organizations can deploy software, including cloud native applications, without the cost and complexity associated with on-premise IT infrastructure.
Public cloud providers prioritize security since their business model requires maintaining public trust, yet the perimeters that bound traditional on-site IT infrastructure disappear in the cloud. Cloud environments are interconnected, giving attackers many potential entry points they can use to enter and traverse networks. Furthermore, it’s difficult to maintain visibility and control over cloud native applications and data due to the rapidly-evolving and distributed nature of cloud environments.
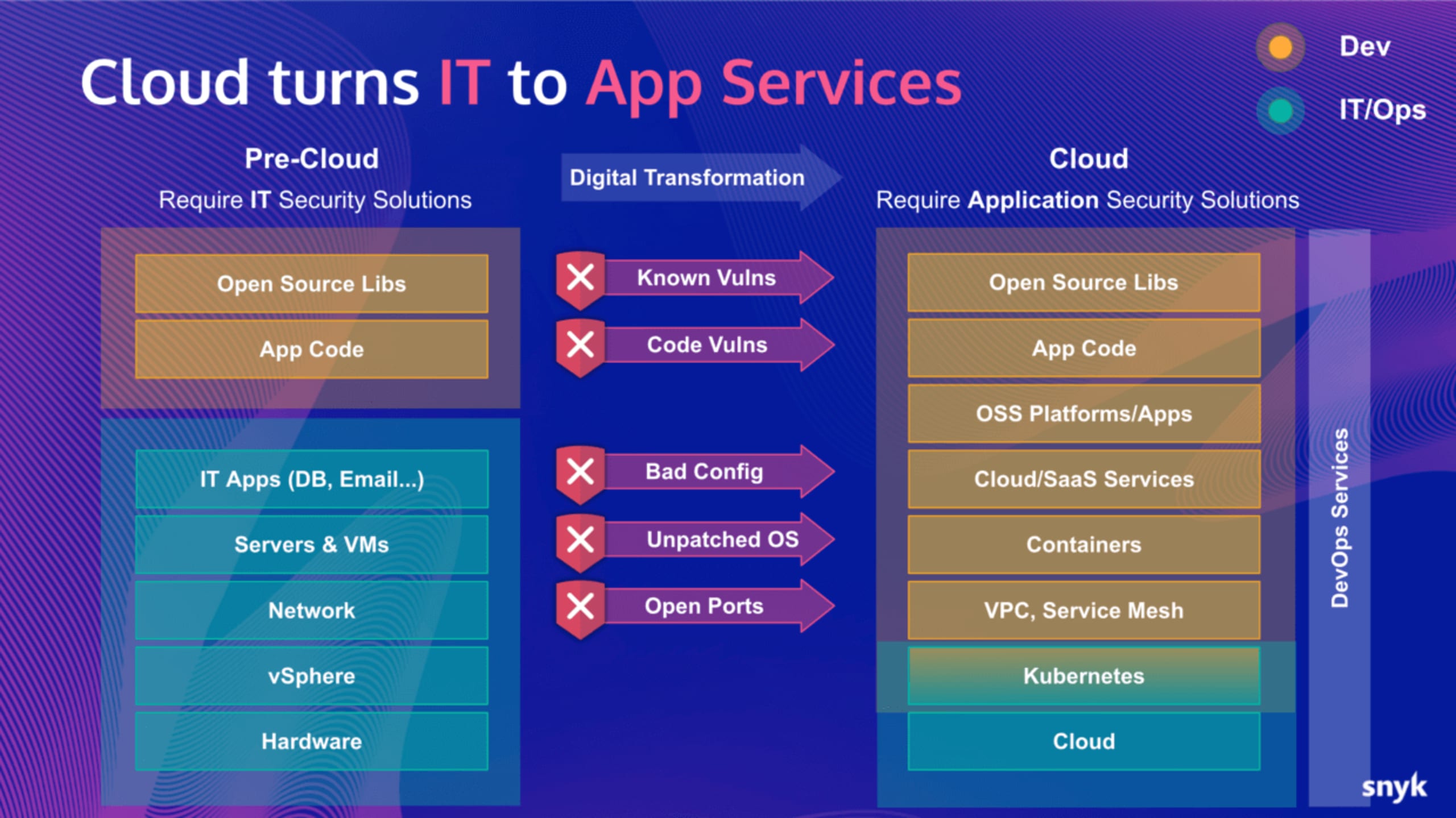
Developers need new methods when securing cloud native applications built with modern approaches like CI/CD, serverless applications, and containers. It’s no longer feasible to secure applications once they’re in production.
What is cloud based security?
Cloud security is the techniques and tools used to secure cloud infrastructure, applications, and data. Traditional security approaches focused on securing internal networks from external threats, but the cloud’s perimeter is loosely defined and cloud infrastructure operates differently from data center infrastructure in many respects. By implementing cloud security, organizations can ensure data privacy, control access to networks and resources, maintain compliance, and free IT teams to focus on other tasks.
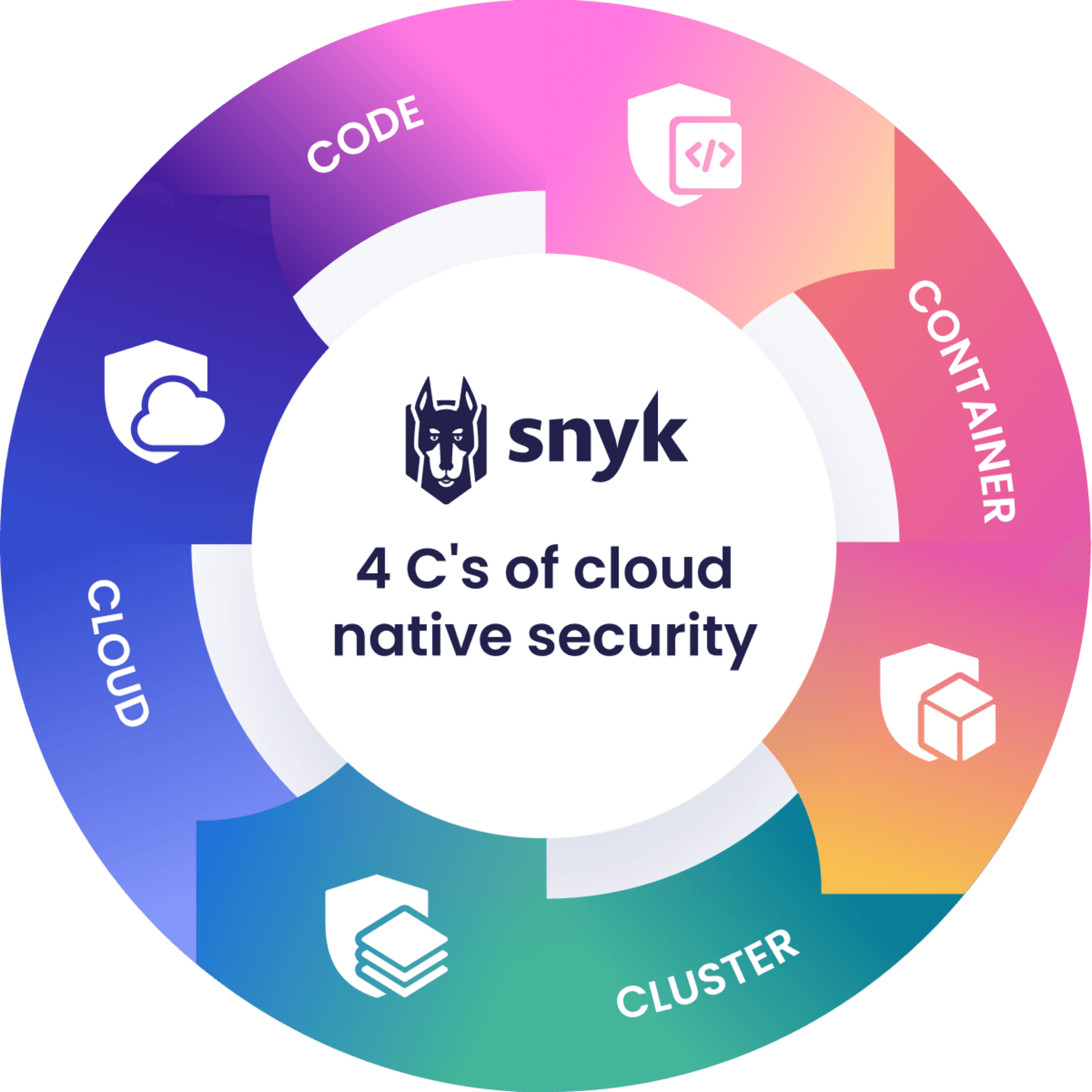
According to Kubernetes, the 4 C's of Cloud Native security are:
Cloud
Clusters
Containers
Code
Why is cloud security important?
Cloud security is important due to the interconnected nature of cloud architectures. While cloud providers have comprehensive security programs — their business model depends on it — hackers can bypass security checks, often by compromising identities (as happened in an attack on U.S. companies and federal agencies using Microsoft cloud services).
Without robust cloud security, all it takes is for an attacker to breach a single weak device or misconfigured cloud resource. They can then traverse interfaces with other cloud systems to uncover data which they can then replicate to their own cloud account or their own servers.
For this reason cloud providers and users must secure access from at each interface between end-user devices, applications, cloud resources, and networks.
In addition to its role in protecting against cyber threats, cloud security is important since it provides continuity in case of a network outage or power outage at a data center. Such interruptions can have short-term damage, such as the inability to access data when you need it, or longer-term repercussions like permanent data loss. A cloud security program should include plans for application and data backups and network outages.
Five benefits of cloud security
Maintain customer trust
Simplify administration
Unified security
Privacy and compliance
Resiliency
Cloud models are an efficient way to run applications and store data without the costs and lengthy time frames associated with on-premise system deployment and maintenance. They can also limit visibility and control over critical processes. By building a robust cloud security program, organizations can gain benefits including:
Maintain customer trust: Users can access data and applications from anywhere using any device while knowing their data is safe from cybersecurity threats or accidental deletion.
Simplified administration: Legacy IT security required manual configurations and frequent security updates. Cloud security takes a proactive approach that offers around-the-clock protection with little or no manual intervention required once it’s in place.
Unified security: Cloud computing allows users to access workflows from any device or endpoint, which is difficult to manage using traditional approaches. Cloud security centralizes network monitoring and streamlines the process of updating software and policies. All security administration happens in one place.
Privacy and compliance: Cloud security allows developers to write and automatically enforce policies to ensure data privacy and regulatory compliance.
Resiliency: Cloud security makes it simpler to implement disaster recovery plans since administration happens in a unified place.
What are the types of cloud security?
There are several aspects of cloud security:
Data security focuses on protecting data at rest and in transit.
Identity & Access Management (IAM) controls traffic between each zone of cloud architecture using identification and access controls.
Governance and compliance focuses on ensuring cloud architecture complies with organizational or governmental regulations.
Data and business continuity builds redundancy to ensure systems can be recovered in case of network outage or data loss.
With this in mind, let’s consider each type of cloud computing security in depth:
Data security
Sensitive data needs to be secured both at rest in public cloud resources and in transit to prevent unauthorized access or leakage. Since users can access cloud data over the internet from any location or device, IT teams require new approaches to securing data.
A number of tools and techniques are available to secure cloud data:
Encryption: This uses an algorithm to encode information both at rest and in transit. If attackers are able to breach barriers and access data, they will have to decrypt the data to see it in its original form. This requires a level of computing power that is economically unfeasible for most attackers, so encryption is an important tool for data security.
VPNs: Virtual private networks (VPNs) allow you to securely send data through potentially insecure connections by encrypting the data and routing it through a remote server run by the VPN host. This secures your data and disguises your identity and location.
Cloud security architecture: Cloud native breaches often exploit errors or vulnerabilities in cloud deployments, access data through poorly configured or insecure interfaces, then exfiltrate that data to the attacker’s network. For this reason it’s a best practice to isolate the components of the cloud architecture such as applications, containers, virtual machines, and data. Tools such as virtual private clouds and Azure VNet accomplish this by partitioning workloads into subnets. Granular security policies, IAM configurations, firewalls, and routing configurations can then be applied to control access.
Cloud service monitoring: Since cloud services exist outside of internal networks and devices, IT teams require a way to gain visibility into the cloud service itself to monitor data. This corresponds to traditional methods of monitoring internal network traffic, but multi-cloud management needs to integrate with different cloud providers and address the increased complexity associated with cloud deployments. Customers using a single cloud provider also need to establish and maintain visibility of their network traffic to ensure security.
It’s worth noting that each of these tools and techniques protect against malicious attackers as well as human errors that lead to data leaks or corruption. Implementing them is the first step towards reducing the impact of a compromise.
Identity & access management (IAM)
Cloud computing models include an array of technologies including database and object storage services, software such as operating systems and virtual machines, and the hardware at the user’s end, often bring-your-own devices (BYOD). Controlling traffic between these zones is a key aspect of cloud security. IAM allows you to gain visibility and control over all these users and endpoints.
IAM includes:
Authentication and authorization: Access controls are a key method for restricting users, both legitimate and malicious, from potentially compromising information and systems. Strong password management and multi-factor authentication are two examples of good authentication and authorization tools.
Role-based access controls: Using role-based rather than individual access controls. These are easier to change when a user changes roles. Privileges should always be granted on a “least privilege” basis, and more extensive privileges require stronger authentication. By granting “least privilege” access you can ensure that if an attacker gains access to an account, they’re not able to get any further into the system, or access important data such as API keys.
Cross-zone security: This includes port blocking, requiring permissions, granular security enforcement, and more.
The ideal would be for security teams to oversee every instance of identification and authentication, but resource limitations mean individual users need a basic understanding of how they can reduce the risk of breach through their credentials. This includes training around strong passwords and multi-factor authentication. IAM principles reinforce the importance of secure cloud architecture, and having a dedicated role such as a Cloud Security Architect to make sure it’s properly setup and managed.
Governance and compliance
Cloud environments add new dimensions to compliance with regulatory requirements around user privacy, such as SOC 2, PCI and HIPAA, and internal requirements. Compliance processes need to address the infrastructure itself, as well as interfaces between in-house systems, cloud infrastructure, and the internet.
Automating policies and controls is one approach for ensuring compliance in cloud environments. These should include policies for tracking, prioritizing, and mitigating threats against essential systems, policies for securing data, role-based access controls, use of encryption and logging, and safe user behavior policies such as around passwords.
Automate cloud compliance in your developers' workflows
Snyk automates cloud compliance checks and generates reports for executives and audtiors.
Data resilience and business continuity
This aspect of cloud security builds measures for redundancy so data and business operations stay live in the event of a disaster or unforeseen data loss. Backups for both data and systems help ensure uninterrupted operations. It also includes steps to test backups and instructions for recovering data. Data that is backed up correctly in the cloud can also protect you from ransomware attacks. If an attacker encrypts all of your live files, you can simply retrieve them from your backups without paying the ransom!
Cloud security vs. application security vs. cloud native application security
The lines between application security and cloud security are increasingly blurred, particularly when using cloud native architectures such as serverless and containers. Developers have more input into the cloud with approaches such as policy as code (PaC) and infrastructure as code (IaC), replacing manual procedures with standardized, repeatable methods written as code.
This means that developers are increasingly responsible for the security of both the applications they write and the infrastructure where those applications run. Developers are increasingly sensitive to security concerns, with 61% of developers saying switching to cloud native technologies has increased their security concerns.
This raises the question of who is responsible for securing the cloud since there are many teams involved: security, operations, and development teams within the client organization and the cloud provider, respectively.
Cloud Security vs cybersecurity
Cloud security is a specialized subset of cybersecurity focused on protecting data, applications, and services in cloud environments. It addresses unique risks like misconfigurations, insecure APIs, and shared infrastructure vulnerabilities. Cybersecurity, on the other hand, broadly encompasses measures to safeguard networks, devices, and data from cyber threats across all environments, including on-premises systems and cloud platforms.
Secure your configurations from IDE to running clouds.
Empower developers to develop cloud infrastructure securely and fix issues from IaC source code
Who is responsible for securing the cloud?
Public cloud providers generally follow a shared responsibility model for cloud security, which assigns responsibility for cloud security to the party who owns each aspect of the cloud.
Providers are typically responsible for securing networks, cloud infrastructure, and servers used for physical hosting of data and workloads. Customers are responsible for choosing a secure provider, governing user access, ensuring compliance with organizational and government regulations, and configuring and maintaining systems securely.
Security responsibilities depend on cloud service type
Security requirements can vary with the type of cloud service being used. These cloud service types include:
Software as a Service (SaaS)
SaaS customers’ primary responsibility is ensuring they use secure access protocols. Providers are responsible for securing the backend. Many attacks take advantage of SaaS application integrations with other platforms, so it’s important to have visibility over user workflows and data.
Platform as a Service (PaaS)
PaaS companies provide a “sandbox” clients can rent to develop applications on the provider’s infrastructure. Providers are responsible for securing the operating system, middleware, and runtime environment, while clients are responsible for end-user devices and networks, applications, data, and user access. Building applications in PaaS environments entails a loss of visibility that makes it harder to detect movements or unauthorized use by attackers in a cloud environment. Systematic security controls and visibility tools need to be in place to detect and prevent suspicious activity.
Infrastructure as a Service (IaaS)
IaaS providers offer alternatives to building costly on-premise infrastructure, allowing customers to rent hardware and computing infrastructure on an as-needed basis. Providers are responsible for securing their physical servers, networks, and data, while customers are responsible for everything that runs on the provider’s infrastructure, including their operating system, applications and middleware, along with user access, resource configurations, and end-user devices and networks.
Cloud security environments
The “cloud” is often referred to as a place, but it’s more useful to think of it as a model for storing data and running workloads in a distributed environment. There are several types of cloud environments, including:
Public clouds
These are third-party services where customers share the provider’s resources with other customers. Customers typically access public clouds through a web browser. Public clouds invest heavily in security and the majority of public cloud breaches arise from customer misconfigurations or other errors. 99 percent of cloud security failures will be the customer’s fault through 2025, according to Gartner.
Private clouds
Private clouds provide customers with an exclusive environment, either managed externally by a third-party provider or internally as a modern approach to the traditional data center. They can be seen as more secure than public clouds since they are isolated by the user’s firewall, but are still susceptible to security challenges such as identity-based breaches.
Gov clouds
Gov clouds are built specifically to provide isolated cloud environments for government customers who may be dealing with sensitive or classified data, and must comply with strict security regulations.
Multi-cloud
These blend multiple cloud services from separate providers of the same type (for example, public clouds or private clouds). Multi-Cloud setups often happen in companies with distributed teams working on different projects with their own timelines and technical requirements; these teams might end up choosing different cloud providers based on the needs of their project. It can also happen after mergers and acquisitions, each company involved might be using different cloud providers. Multi-cloud usage adds security complexity because of the need to have specific cloud security expertise and tooling on hand for each cloud in use.
Hybrid cloud
Hybrid clouds blend third-party or on-site private cloud data centers with public clouds. Some businesses use what Gartner calls “bi-modal” usage, both workloads in the cloud and in the datacenter, particularly during migration periods and digital transformation efforts.
On-site vs. off-site clouds
Customers have the option to access cloud environments managed off-site by an external provider or an in-house, on-site cloud that allows customized configurations of every resource. Off-site cloud services are delivered remotely and allow customers to offload the costs associated with hardware, maintenance, and security, while on-site clouds require the customer to manage networks, storage, servers, and security of the cloud environment.
Secure your cloud environments with Snyk
The software development process has changed, so security needs to be built into every stage of the software development lifecycle, which is not considered after the application is in production. Traditional infrastructure has been replaced by code that defines infrastructure, services, and application containers. Applications themselves now consist of substantial proportions of open-source code. They're built to run in containers, virtual machines, and serverless architecture and include instructions for deploying and configuring the infrastructure they'll run using tools like Kubernetes and Terraform.
Cloud security needs to support developers as they design and code cloud-native applications throughout the CI/CD pipeline. Snyk offers several tools to help developers incorporate cloud security into their applications and workflows:
Developer First Security
Snyk's developer security tools allow developers to incorporate security from the first lines of code. Snyk includes open source dependency scanners, container security, and infrastructure security as part of its platform.
Infrastructure as Code (IaC) security
IaC templates define the state you want cloud infrastructure to run as, like automated run-books that capture the intricacies of manual deployments and distill them into repeatable steps that can be tested before they are run. IaC allows you to introduce best practices of software development into infrastructure definitions.
Snyk IaC simplifies compliance testing for security and architecture policies whenever code changes occur. It supports AWS, Azure, and GCP infrastructure, as well as Kubernetes and Terraform IaC tools. Snyk IaC consolidates visibility and governance across developer workflows, pipelines, and cloud environments using a single policy engine and ruleset. The tool also enables teams to swiftly address cloud issues by automatically connecting them to the relevant IaC source code in Git workflows, ensuring faster remediation by the responsible developers. Simply fix, retest, and redeploy.
Container security — including runtime through Sysdig
Snyk Container helps developers secure applications and containers at once. Its base image tools allow you to quickly resolve vulnerabilities by upgrading to more secure base images. Its scanning features allow you to automatically uncover and remediate vulnerabilities in containers both within the IDE environment and the running environment. Snyk's partnership with Sysdig extends Snyk Container, enabling you to protect the runtime Kubernetes environment and deliver feedback and visibility to developers.
Shift left & DevSecOps principles
Traditional application security focuses on scanning and fixing vulnerabilities in production. Due to the complexity of modern cloud environments and the speed of application releases this traditional approach no longer works. The modern DevSecOps approach to security incorporates security into the development process from the beginning. This shift left security approach is a fundamental part of cloud native application development and corresponding tools.
Secure your configurations from IDE to running clouds.
Empower developers to develop cloud infrastructure securely and fix issues from IaC source code