Enhancing PCI compliance security with SAST and SCA
February 8, 2022
0 mins readThe Payment Card Industry Data Security Standard, also known as PCI DSS is a thorough process that reviews a company's systems and policies for handling and storage of sensitive consumer cardholder data.
PCI DSS is a really important part of the payments industry. It helps ensure that end users data is kept safe and secure. And it’s maintained and governed by the PCI Security Standards Council, who also govern elements like the requirements of the standard that accreditor vendors need to meet for PCI DSS certification. Currently, MasterCard and Visa with some exceptions mandate merchants and service providers to be PCI DSS compliant. In the case of a breach and the affected entity was not PCI DSS compliant when the breach occurred, additional penalties such as fines will be due.
These checks are critical not only to the wider payments industry but also to create a level of trust with users knowing their data is protected. The PCI compliance process is a number of checks, usually by an accredited third party, to ensure that secure data handling processes are in place.
In this post, we’ll take a deeper look at the requirements of PCI DSS, as well as how the use of static application security testing (SAST) and software composition analysis (SCA) tools can help you meet them more easily. We’ll also walk through using Snyk to handle both your SAST and SCA needs for PCI DSS. Let’s go!
PCI compliance requirements
There are 12 PCI DSS requirements for building and maintaining a secure network and systems. The requirements cover things like access to sensitive cardholder data, internal systems, application infrastructure, and developing and maintaining secure systems and applications.
Here’s the full list of requirements at a high level:
Installing and maintaining a firewall configuration to protect cardholder data. The purpose of a firewall is to scan all network traffic, block untrusted networks from accessing the system.
Changing vendor-supplied defaults for system passwords and other security parameters. Default passwords are easily discovered through public information and can be used by malicious individuals to gain unauthorized access to systems.
Protecting stored cardholder data. Encryption, hashing, masking and truncation are methods used to protect cardholder data.
Encrypting transmission of cardholder data over open, public networks. Strong encryption, including using only trusted keys and certifications reduces risk of being targeted by malicious individuals through hacking.
Protecting all systems against malware and performing regular updates of antivirus software. Malware can enter a network through numerous ways, including Internet use, employee email, mobile devices or storage devices. Up-to-date anti-virus software or supplemental anti-malware software will reduce the risk of exploitation via malware.
Developing and maintaining secure systems and applications. Vulnerabilities in systems and applications allow unscrupulous individuals to gain privileged access. Security patches should be immediately installed to fix vulnerability and prevent exploitation and compromise of cardholder data.
Restricting access to cardholder data to only authorized personnel. Systems and processes must be used to restrict access to cardholder data on a “need to know” basis.
Identifying and authenticating access to system components. Each person with access to system components should be assigned a unique identification (ID) that allows accountability of access to critical data systems.
Restricting physical access to cardholder data. Physical access to cardholder data or systems that hold this data must be secure to prevent the unauthorized access or removal of data.
Tracking and monitoring all access to cardholder data and network resources. Logging mechanisms should be in place to track user activities that are critical to prevent, detect or minimize impact of data compromises.
Testing security systems and processes regularly. New vulnerabilities are continuously discovered. Systems, processes and software need to be tested frequently to uncover vulnerabilities that could be used by malicious individuals.
Maintaining an information security policy for all personnel. A strong security policy includes making personnel understand the sensitivity of data and their responsibility to protect it.
The full compliance list, available on the PCI Security Standards Council website, goes into a lot more detail. For example, point 6 on developing and maintaining secure systems for example covers specific vulnerability types like:
Injection Flaws (SQL Injection)
Buffer overflows
Insecure cryptographic storage
Insecure communications
Improper error handling
Improper access control
Cross-site request forgery (CSRF)
Broken authentication and session management.
If you’re using Snyk, all of these security issues can be easily found and automatically remediated within the process workflows and pipelines your team is using.
How Snyk Code and Snyk Open Source can help
To show PCI compliance in action, we’re going to use Snyk to secure PrestaShop, an open source ecommerce platform from the PHP ecosystem. Snyk offers a few ways to find and fix, and in this example, we’ll use the Snyk CLI to scan for vulnerabilities in dependencies, and then use PHPStorm with the Snyk plugin to scan code.
To follow along with the example below, you'll need to have Git, PHP, and the Composer dependency manager installed.
Get set up
To follow along, you’ll need to start up a free Snyk account. You can get up and running in a few minutes — no credit card required!
Next, you’ll need to install the Snyk CLI locally. The great thing about the Snyk CLI is that there’s just one install for the whole platform. So you can use it to scan your code, dependencies, containers, and IaC. You can get started quickly by checking out our Snyk CLI cheat sheet.
After that, clone the PrestaShop repository (version 1.7.8.3 at time of writing) to your local environment:
1git clone https://github.com/PrestaShop/PrestaShop.gitAnd with PHP Composer installed, run:
1composer updateScan for open source vulnerabilities
First, let’s check for open source vulnerabilities against the Composer manifest., To do this in the root directory of the cloned repository, run:
1snyk testIn this case it returns 8 issues and 11 vulnerable paths being loaded in along with some suggested fixes.
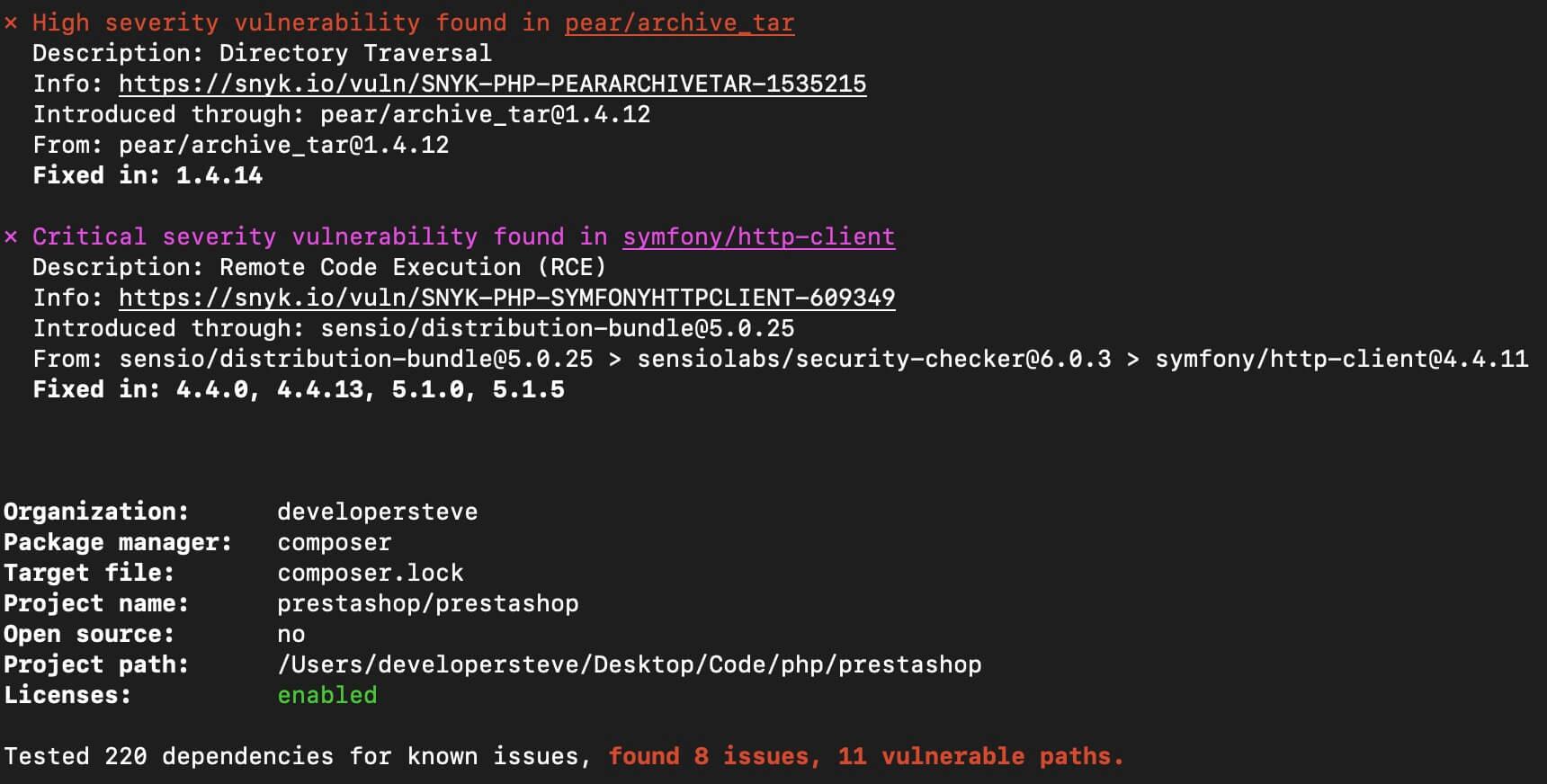
With these vulnerabilities, it looks like I’ll just have to upgrade the libraries to a version that has fixes in place. Fortunately, Snyk is not only able to identify vulnerable paths, but is also able to fix issues via an automatic pull request into the connected repository.
To learn more about connecting a repository check out our Git repository integrations documentation.
Scan for vulnerabilities in your code
Now that you’ve seen the Snyk CLI in action, let's test for vulnerabilities in the codebase using PHPStorm with the Snyk plugin.
This will check each code language file in the project to see if there are any possible vulnerabilities. In our example, it brings back 252 possible vulnerabilities (99 [high], 131 [medium], 22 [low]) in the code which will need further investigation.
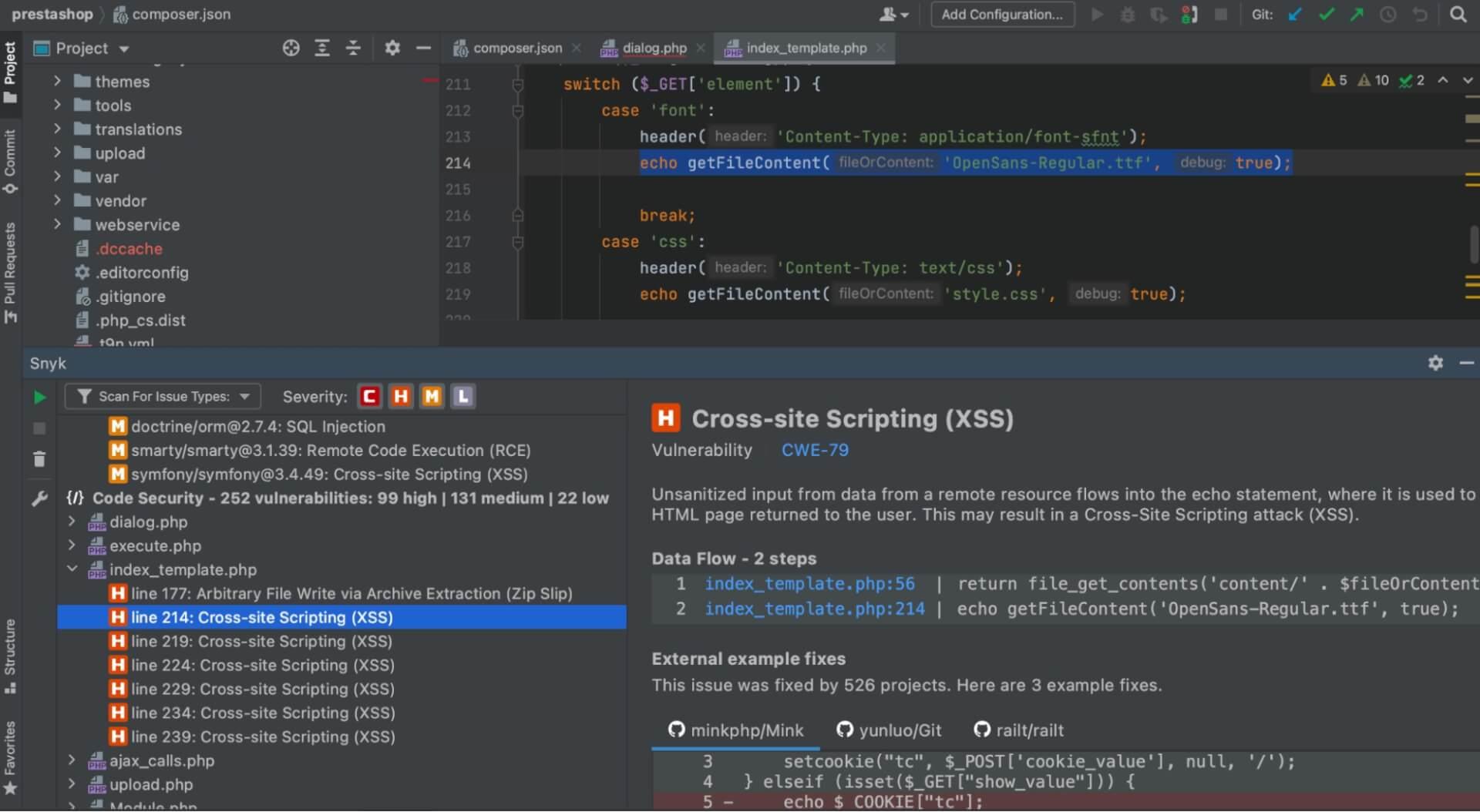
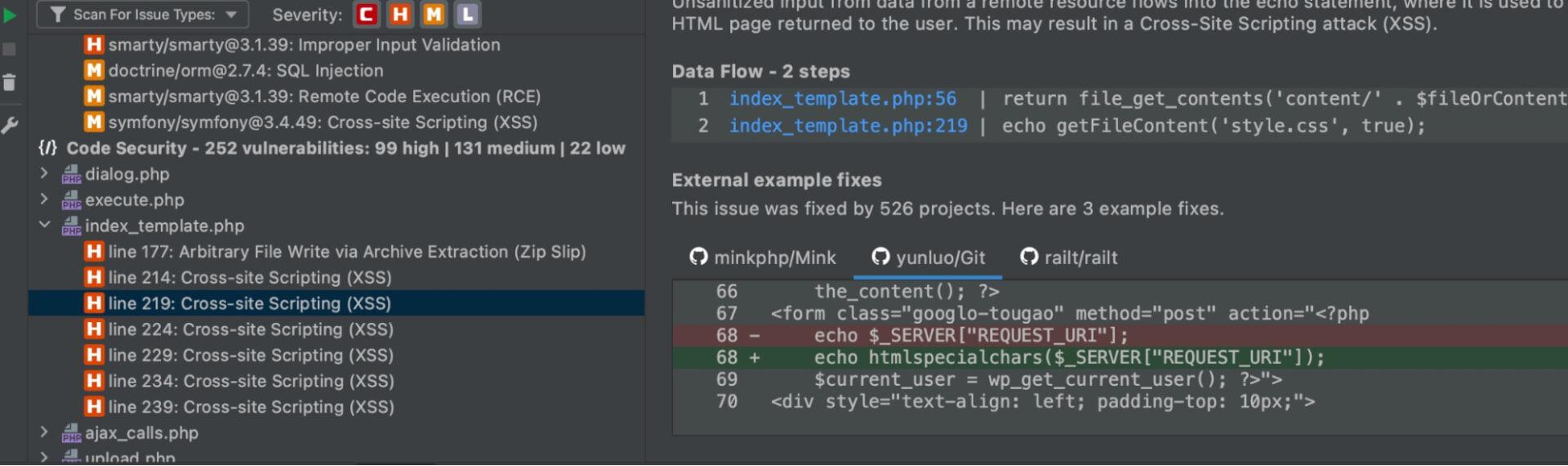
To fix these vulnerabilities, I can look into the highlighted code points from the scan to do further investigation and document my findings and fixes. Using PHPStorm with the Snyk plugin makes this process easier because I can step through each file and investigate further at the code level.
The PHPStorm Snyk plugin also allows me to trace back through each function in a file and gives examples of fixes used in other projects that had the same type of issue.
Stay PCI compliant
From developer to CTO/CISO going through the PCI DSS compliance process does not have to be an arduous task, providing there are processes and tools in place to streamline the process. Knowing the requirements and having the tools and processes in place to stay compliant is key. And for the developers reading this, documenting your code is a crucial part of the PCI requirements and is a good way to keep track of changes and notes for a future developer.
As you’ve seen, Snyk can help you streamline the PCI DSS compliance process, but the best part is you can easily integrate Snyk scanning into CI/CD and code pipelines, which helps automate and document ongoing issues. Sign up for a free account and make it easier to stay compliant.
Secure your code with cutting edge intel
Learn about the full range of Snyk Code SAST functionality in only 30 minutes.





















