Streamline Kubernetes security in Amazon Web Services
February 27, 2020
0 mins readIntegration with Amazon Web Services Elastic Container Registry (ECR) is one of our most popular use cases with Snyk Container and so we’re happy to announce that we’ve made it simpler to integrate Snyk Container vulnerability scanning within your Amazon Elastic Kubernetes Service (EKS) and ECR services.
As new workloads are launched in EKS it’s important to know where the underlying containers are coming from and if they’re safe. Snyk Container detects workloads as they are created or modified in EKS and then connects to registries like ECR to scan the container image for vulnerabilities and provide fix recommendations for detected issues. As part of our EKS integration, we also alert you, the developer, to potential configuration issues in the workload that could make your application easier to attack.
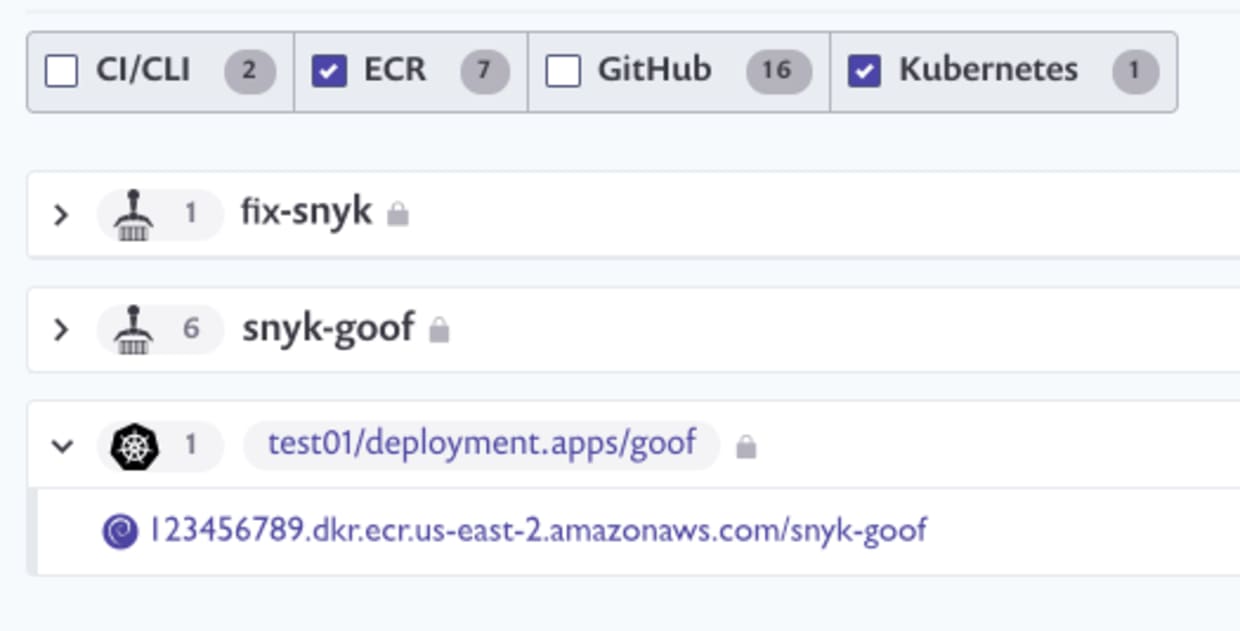
Detect and secure running workloads in your EKS clusters using native AWS services
The rate of change in modern applications makes it challenging to keep up with all the workloads running in Kubernetes clusters, particularly since they can pull a new container image every time they launch. Snyk Container integrates with EKS and ECR to detect workloads as they’re launched in EKS, and then connects to ECR (or other registries) to find the source container image and scan it for vulnerabilities. We use the image property of the container in the pod to locate the source image and make the connection, and for EKS and ECR specifically, we use AWS IAM to authenticate the connection.
The Snyk Kubernetes controller gives you additional visibility into your Kubernetes cluster beyond analysis of container image vulnerabilities. We can also analyze the workload configuration to help prioritize fixes. In the example below, the deployment configuration has no CPU or memory limits, no restrictions on running as root or writing to the root file system, and no system capabilities have been removed, as shown by the “FAIL” badge. If you have high severity vulnerabilities in a workload running with insecure configurations, you’ve opened yourself up to greater risk as attackers have both a way in, and also the elevated potential to cause problems.
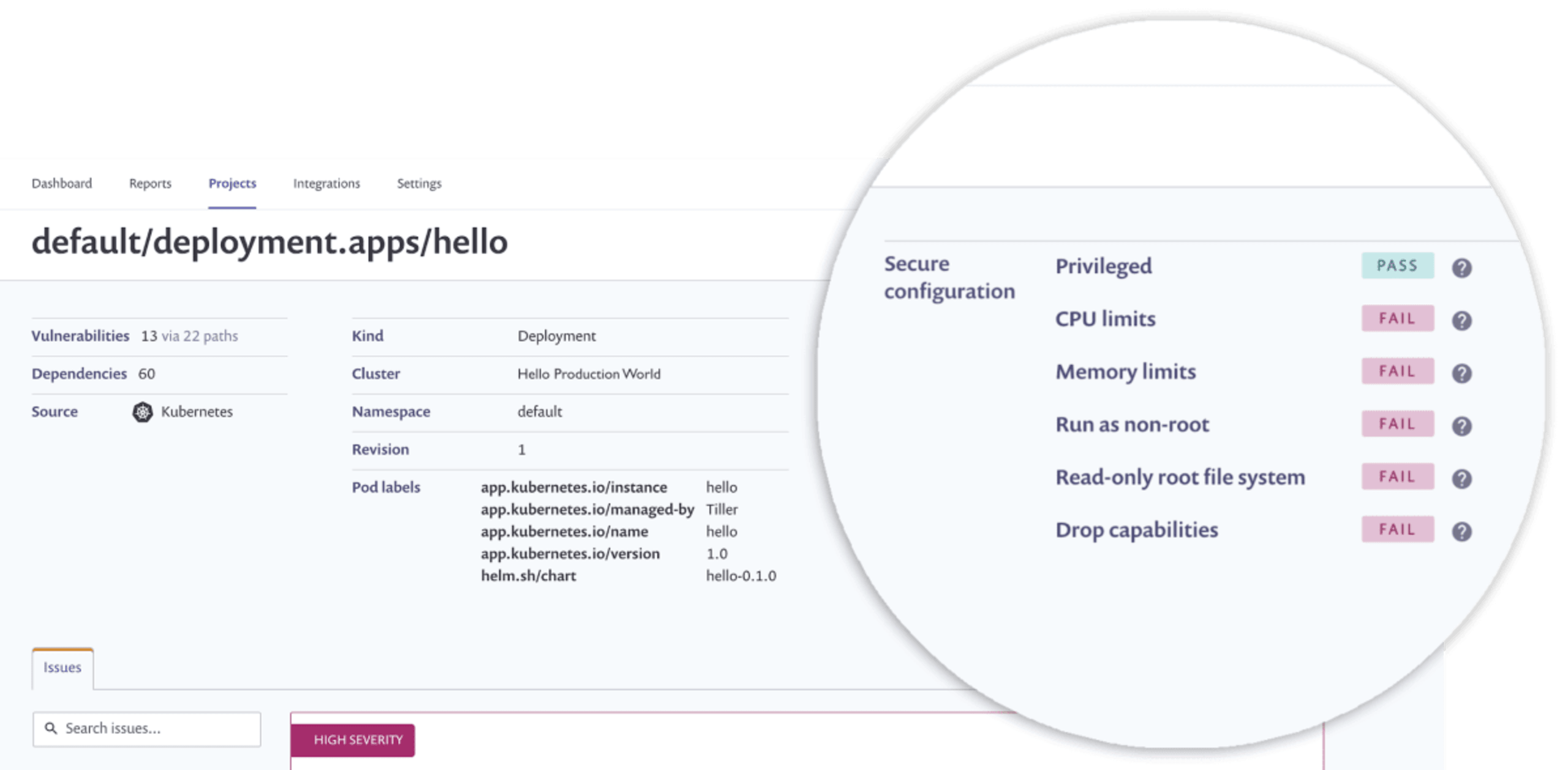
Optimize container images with guided recommendations
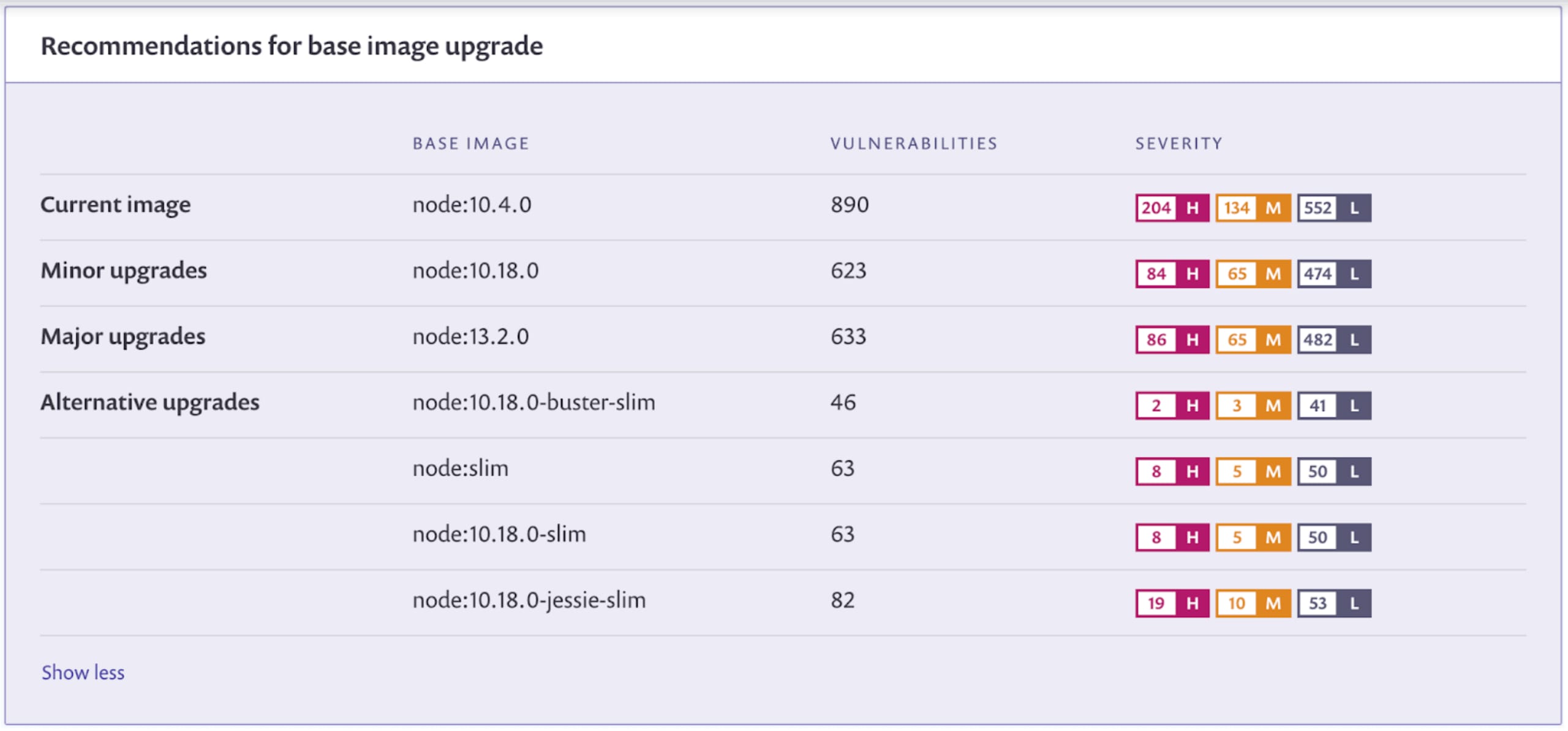
Snyk Container helps developers quickly address vulnerabilities by providing guided recommendations for base image upgrades. Often the base image is one of the primary sources of vulnerabilities in containers. Popular base images are designed to be very simple, enabling you to quickly start a wide range of projects, which means they may be loaded with unnecessary operating system tools and packages. What most container scanning tools provide is a long list of vulnerabilities, with no guidance for developers on which layer those vulnerabilities come from in the image, nor with any recommendations for upgrading the base image.
Not only does Snyk have one of the most comprehensive vulnerability databases available for containers and open source dependencies, but for containers we also add guidance for selecting base images with fewer vulnerabilities. In the example below you can see the current image as well as a Minor Upgrade recommendation, with minimal changes but also with a reduced number of vulnerabilities. We also provide Major and Alternative upgrade recommendations, which introduce bigger changes and might require more testing to ensure compatibility with your application, but they can greatly reduce the vulnerability count as well.
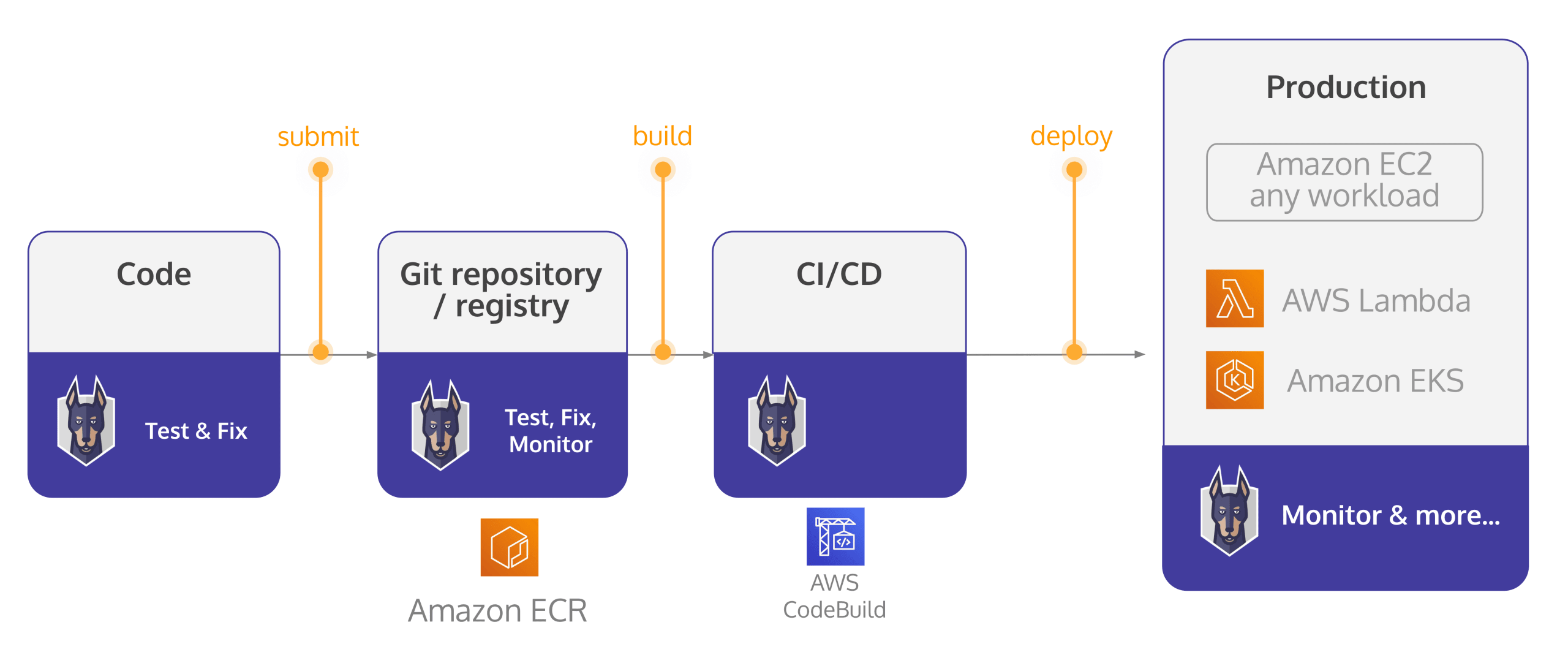
Snyk and AWS: container security and open source security throughout the development lifecycle
Detecting containerized workloads as they’re launched in EKS is not necessarily the only way you might want to add vulnerability detection to application pipelines in AWS. Snyk can integrate with CI tools like AWS CodeBuild to add vulnerability detections for both container builds and open source dependencies. We can also integrate directly with registries like ECR, Docker Hub and others to scan images you already have stored in those locations.
For developers, finding vulnerabilities earlier helps maintain the pace of development and releases. For security teams early detection leads to fewer issues that need to be “virtually patched” or have exception policies in production. With Snyk, we help you do all of this without disrupting the development workflow you’re used to.
Getting started
It’s easy to get started with Snyk and AWS. You can signup for a free Snyk account and start scanning containers in ECR and other registries. You can learn more about our AWS integrations for Snyk Container in our documentation and if you want to scan your open source dependencies you can do that as part of the free Snyk offering as well.
If you’re attending KubeCon EU this year come visit us! We’ll be in Booth S34.
Snyk folks will be participating in three different break-outs:
Patrick Debois, Director of DevOps Relations, will help you answer the question “How Secure Is Your Build/Server?” at Cloud Native Security Day on March 30.
Hayley Denbraver, Developer Relations, is going to talk about research she’s done on vulnerabilities in public Helm charts in the “Uncharted Territories: Discovering Vulnerabilities in Public Helm Charts” session on 1st April.
And we’ve put a panel together to talk about “Kubernetes and Cloud Native Security: A State of the Union” on 1st April including the following folks:
Gareth Rushgrove, Snyk Product Manager and CNCF Ambassador
Kirsten Newcomer, Red Hat Principal Product Manager
Scott Coulton, Microsoft Cloud Developer Advocate, Docker Captain, and CNCF Ambassador
Phil Estes, Distinguished Engineer & CTO, Container Architecture Strategy, IBM & Chair of OCI Technical Oversight Board
Rags Srinivas, Developer Relations at Snyk
Stay secure!
Secure infrastructure from the source
Snyk automates IaC security and compliance in workflows and detects drifted and missing resources.
