Announcing Snyk’s developer-first Infrastructure as Code security capabilities
August 17, 2020
0 mins readWe’re thrilled to announce the launch of our developer-first Infrastructure as Code security capabilities, enabling developers to find and fix misconfigurations that can lead to security problems.
With the rise in popularity of technologies such as Docker, Kubernetes, and Terraform, developers are writing and maintaining more and more configuration in addition to building the application itself.
At Snyk, we believe in empowered development teams—being able to use the right tool for the job, rapidly making changes to both your application and the infrastructure to deliver business value quicker. Knowing how to securely deploy to Kubernetes, or how to securely provision infrastructure with Terraform can be overwhelming, to say the least, and easy to get wrong.
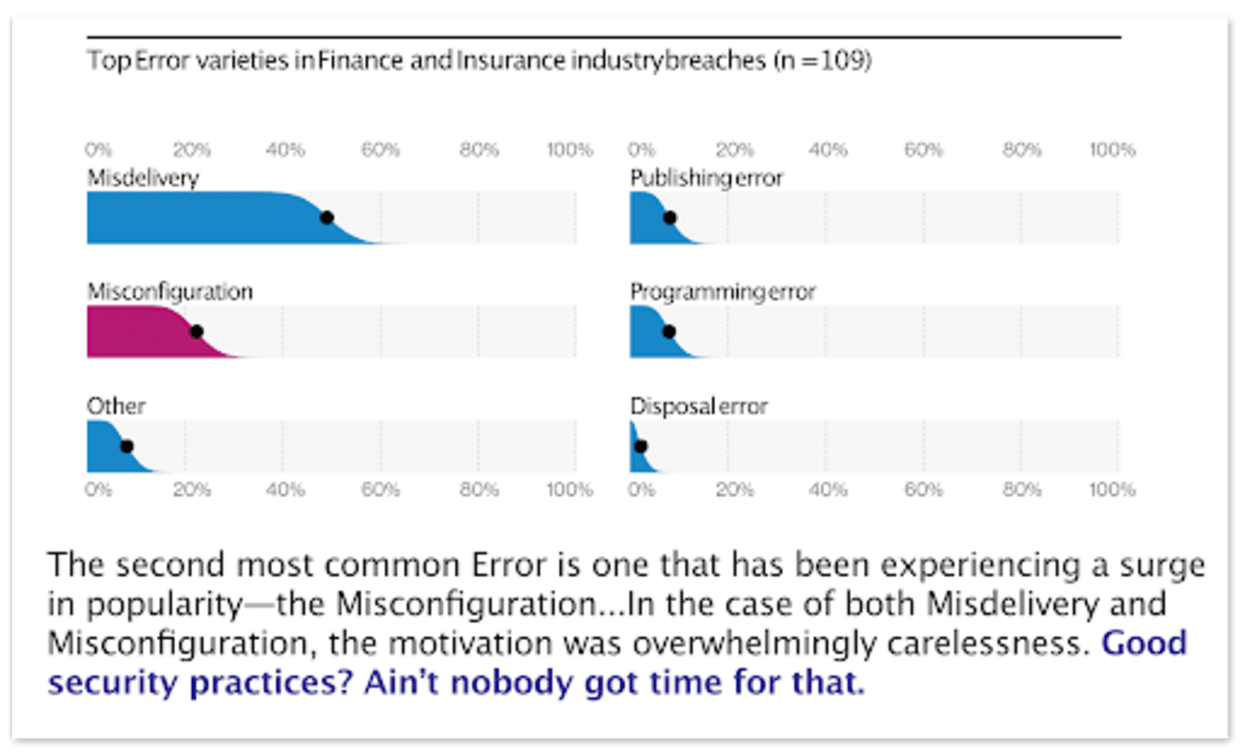
These configuration files can lead to security problems if not handled correctly. The consequences are potentially severe, such as an exposed blobstore bucket with customer data or a publicly accessible server. News stories and research articles abound, including the Verizon Business 2020 Data Breach Investigations Report, in which they discovered that misconfigurations—such as insecure cloud storage and improper network rules—was the second most common error leading to breaches in the finance and insurance sector.
Typically these security needs are handled by a few experts in the company, who can quickly become a bottleneck as teams move faster. What organizations need are expert systems that scale this expertise to the development teams themselves.
With the launch of Snyk Infrastructure as Code, we are empowering development teams to be secure by default, in line with our philosophy of shifting security left, whilst giving security teams visibility and confidence that the company is safe and developers can keep working iteratively.
Snyk IaC in action
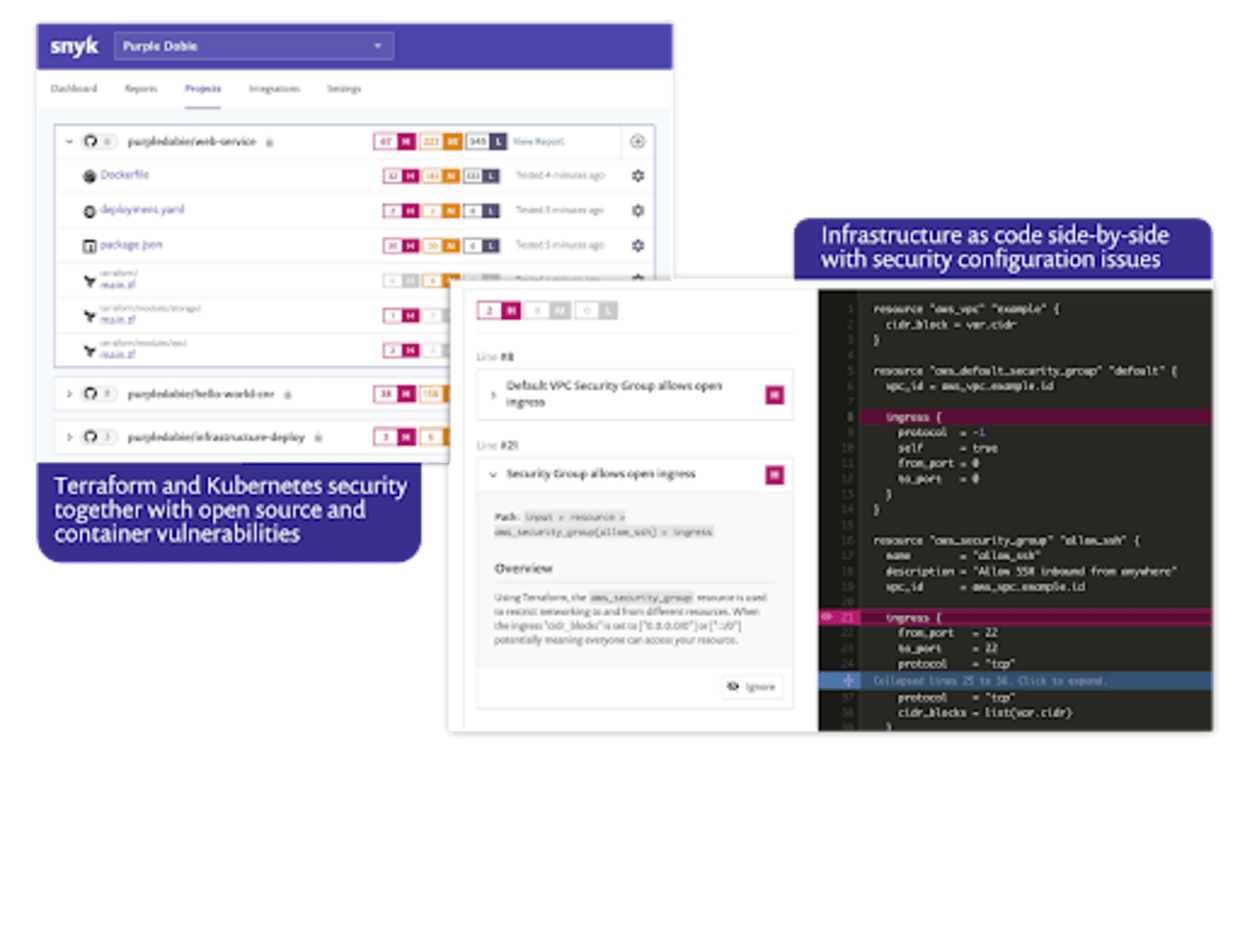
Here is a demo of a Terraform module being imported from GitHub and scanned for misconfigurations. In this case CIS benchmarks that are not being met are highlighted to the developer directly in the file itself for easy remediation.
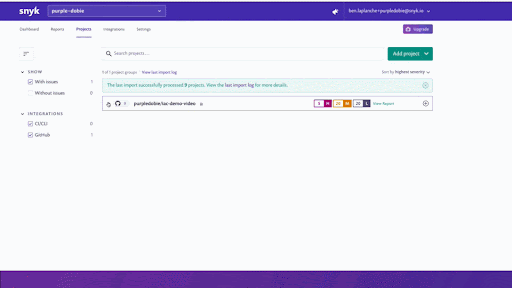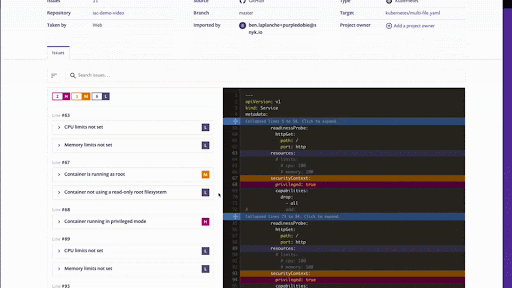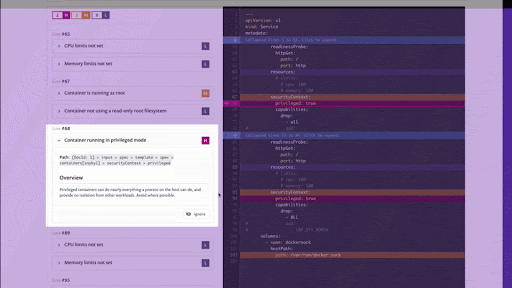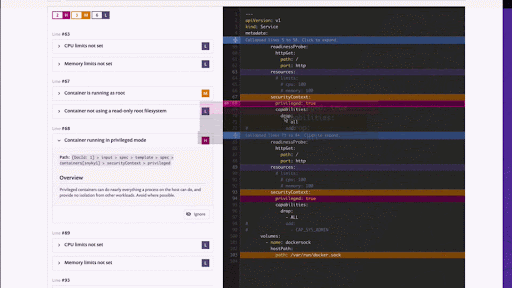
With Snyk we want to make tools that developers can use everywhere. That’s why we’re also making this functionality available in our CLI tool. That way you can get feedback as early as possible in your development cycle.

Snyk Infrastructure as Code is available today for all users, with support for Kubernetes, Helm Charts, and Terraform AWS resources.
If you already have a Snyk account, you can try out this functionality for free straight away. Hit import on your existing project and your Kubernetes and Terraform configuration files will be identified and scanned.
Secure infrastructure from the source
Snyk automates IaC security and compliance in workflows and detects drifted and missing resources.