Python security insights
How secure is the Python ecosystem? Based on millions of scans performed by Snyk, this report analyzes the security of Python projects. Read this report to learn about common security issues and trends.

The security footprint of Python projects
47% of Python projects are vulnerable
An average Python project has around 35 dependencies. Out of these, 17 are direct dependencies and 18 are indirect dependencies.
In 47% of these projects, dependencies are introducing vulnerabilities. An average vulnerable project consists of 33 known vulnerabilities, out of which 10% are critical severity vulnerabilities, 26% are high severity, 26% medium severity, and 38% low severity.
The good news – you can eliminate 87% of known vulnerabilities by upgrading the vulnerable package!
Snyk’s automated fix PRs will help you automatically find, prioritize and fix vulnerabilities in your Python dependencies.
Vulnerabilities in projects by severity
Critical
10%
High
26%
Medium
26%
Low
38%
Common security issues in Python projects
OWASP top 10 found in the majority of Python projects
Snyk Code – Snyk’s Static Application Security Testing (SAST) solution – was trained using over 120K Python projects on GitHub. Over 60% of these projects were found to include issues on OWASP’s 2021 top 10 list with XSS (Cross Site Scripting) found in 20% of projects.
There are two issues specific to Python, though:
Unicode issues: Like most programming languages older than 10 years, Python has a history of issues related to handling encoding in strings.
Closing API calls: When interacting with external resources such as file or network streams, calling the close function signals the system to flush the content as well as to free any handles.
Top 5 Python Issues Reported by Snyk Code
XXS
28%
TLS Cert Disabled
23%
Path Traversal
23%
Hardcoded Secret
14%
SQL Injection
12%
Commonly downloaded Python packages
Python packages are healthy!
What open source packages are Python developers using? How healthy are these projects? Are these packages secure? How are they included in projects? To answer these questions we looked at two key datasets – the 1000 most downloaded packages from PyPI and the 1000 most common packages used in the Python projects monitored by Snyk.
To examine PyPI package downloads, we used Snyk Advisor – a free, online, research tool that helps you decide which open source packages or container base images to use to build your Python project. Containing all projects from PyPI, Snyk Advisor calculates a health score based on packages’ popularity, security, maintenance, and community strength. For the 1000 most downloaded Python packages from PyPI, Snyk Advisor suggests an average high health score of 81%!
| Package | # of downloads* | Health score | Last release date** | Age | License | Contributors | Dependencies |
|---|---|---|---|---|---|---|---|
| urllib3 | 158,893,228 | 98.50% | Jun 25, 2021 | 12 years | MIT | 250 | 0 |
| boto3 | 134,136,171 | 95.50% | Jul 28, 2021 | 7 years | Apache-2.0 | 110 | 6 |
| six | 128,572,888 | 86.93% | May 5, 2021 | 11 years | MIT | 60 | 0 |
| botocore | 128,304,032 | 97.00% | Jul 27, 2021 | 9 years | Apache-2.0 | 130 | 4 |
| requests | 116,360,262 | 97.00% | Jul 13, 2021 | 10 years | Apache-2.0 | 410 | 7 |
| certifi | 113,424,297 | 85.70% | May 30, 2021 | 10 years | MPL-2.0 | 30 | 0 |
| setuptools | 113,270,733 | 95.64% | Jul 19, 2021 | 15 years | MIT | 380 | 0 |
| idna | 112,275,170 | 83.60% | May 29, 2021 | 8 years | BSD-3-Clause | 20 | 0 |
| chardet | 107,130,519 | 88.43% | Dec 10, 2020 | 15 years | LGPL-2.1 | 40 | 0 |
| python-dateutil | 100,233,788 | 94.14% | Jul 14, 2021 | 13 years | Apache-2.0 OR BSD-2-Clause | 110 | 1 |
* Average monthly downloads for the period of March 21 - June 21.
** At the time of writing.
*** In the latest version.
The most vulnerable packages in Python projects
#1 downloaded package on PyPi is vulnerable
With millions of downloads a week, urllib3 is the most downloaded Python package on PyPI. It is also the 3rd most used package in the projects monitored by Snyk.
While the latest version of the package is safe to use, previous versions include security vulnerabilities, including high and medium severity issues. Version 1.24.3, downloaded over 2 million times a week, includes a high severity CRLF injection vulnerability. Version 1.26.3, downloaded over 1.5 million times a week contains an Improper Certificate Validation vulnerability.
| Package | Use | Vulnerabilities | Minimum known vuln free version | Weekly downloads |
|---|---|---|---|---|
| urllib3 | HTTP client | Critical – 0, High – 3, Medium – 6, Low – 1 | 1.26.6 (latest) | 38M |
| pillow | Imaging library | Critical – 1, High – 18, Medium – 7, Low – | 8.3.1 (latest) | 8.3M |
| PyYAML | YAML parser and emitter | Critical – 4, High – 0, Medium – 0, Low – 0 | 5.4 | 21M |
| ipaddress | IPv4/IPv6 manipulation library | Critical – 0, High – 1, Medium – 2, Low – 0 | – | 1.5M |
| cryptography | Cryptographic recipes and primitives | Critical – 0, High – 4, Medium – 3, Low – 0 | – | 11.2M |
| django | High-level Python Web framework | Critical – 0, High – 8, Medium – 15, Low – 5 | 3.1.13 | 1.6M |
| jinja2 | A fast and expressive template engine | Critical – 0, High – 1, Medium – 4, Low – 5 | 2.11.3 | 17M |
| pygments | A syntax highlighting package | Critical -1, High – 2, Medium – 0, Low – 0 | 2.7.4 | 6M |
| requests | HTTP client | Critical -1, High – 0, Medium – 5, Low – 0 | 2.20.0 | 37M |
| rsa | RSA implementation | Critical -0, High – 2, Medium – 3, Low – 0 | 4.7 | 16M |
Vulnerabilities in Python containers
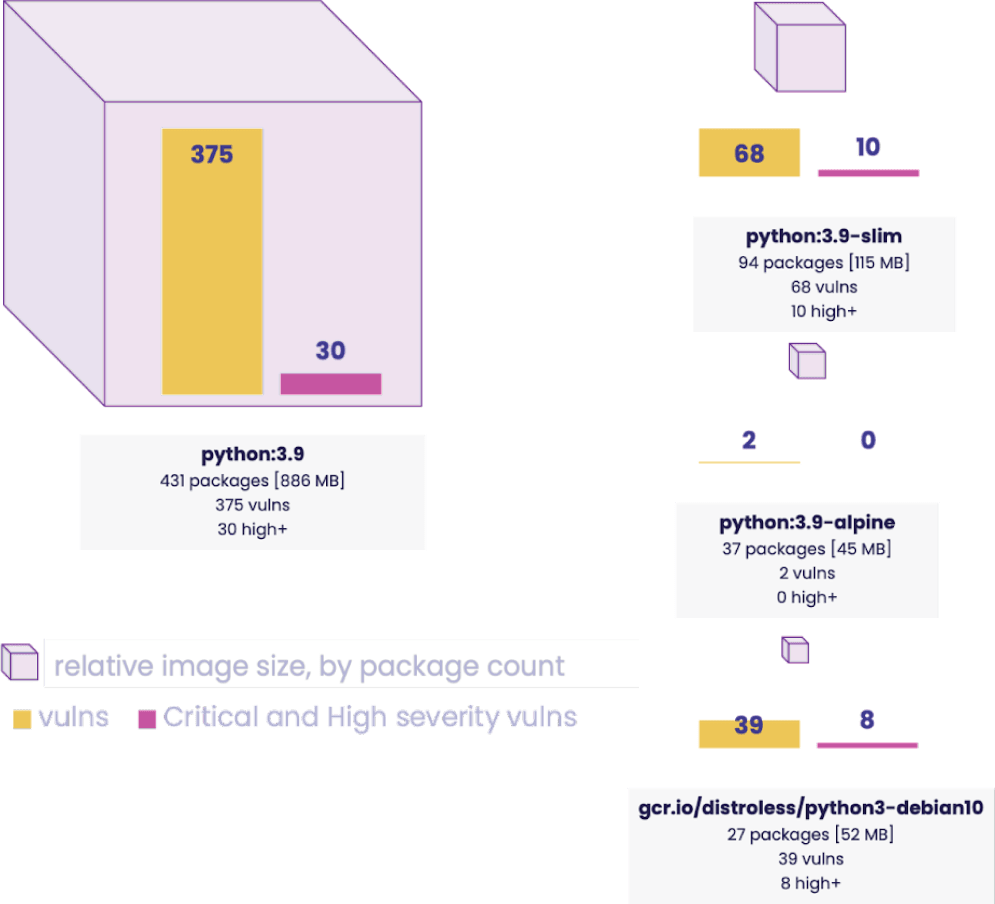
Most container vulnerabilities can be fixed using slimmer images
While it’s pretty easy to get a Python app running in a container, as with so much in life the “easy way” isn’t always the best way. Containers come with pre-installed Linux packages, which may or may not be important to making your app run but will impact your vulnerability reports.
Popular Python base images vary in size and the number of vulnerabilities they introduce. “Fat” images like :3.9, :3.8, and :3.7 are the most common, despite all the best practices stating you should use a slimmer base image to reduce attack surface. You can get both worlds in containers through the use of multi-stage builds, starting with the bigger images to simplify building and testing your code and then moving the required production packages to a slim image in the final stage.
A word about this report
Snyk performs millions of monthly scans of hundreds of thousands of Python projects, providing us with the ability to describe what an average Python project looks like and give you an idea of what you might find when you scan one of your Python projects. The data used for this report was taken from the Snyk Intel Vulnerability Database, hundreds of thousands of Python projects monitored by Snyk, the same number of projects used as a training set for Snyk Code, and Snyk Advisor.
Download the full report
The vast majority of our survey respondents are still early in their Python adoption journey, so if you don’t think you’re in that top 7%, you’re not alone. Our full Python Security Insights report has more details on what’s holding people back, and what they’re doing today, and how they’d like to improve.




















