Fixing insecure Kubernetes configuration at the source
April 8, 2020
0 mins readWe're happy to announce today the public availability of a whole new feature in Snyk, to help you find and fix security issues in your Kubernetes configuration files.
Configuration management shifting left
Traditionally, developers have been responsible for just writing the code — someone else was responsible for quality. Yet another person was responsible for deploying it. And, another team was responsible for running it in production. But increasingly we're seeing more and more responsibilities shift to the development teams, with specialists providing expert support and consultancy. We've seen software packaging move from a specialism in IT, to developers writing Dockerfiles. We've seen the rise of DevOps, "you build it, you run it" and development teams owning services in production. And we're now also seeing configuration increasingly become a developer domain problem with the rise of infrastructure as code and tools like Terraform, Kubernetes and AWS Cloud Formation.
Guy Podjarny, one of the founders of Snyk, has recently written about the growing scope of the application. One of the things we've been thinking about for a long time at Snyk is what these shifts mean for security, and how to help developers out there with these new responsibilities.
Managing all your application vulnerabilities in one place
The growing scope of the application means more and more different types of security issues fall into the developers’ domain. Snyk already helps developers find vulnerable dependencies in Java, Python, Go (and more) applications, as well as in Docker container images. We now want to help find and fix security issues in your Kubernetes configuration files. This is powerful on its own, but combined with our other tools it's even more interesting. With Snyk you can now see the vulnerabilities in libraries you rely on, as well as whether the configuration that runs your app in production leaves those vulnerabilities wide open to attackers.
Fixing the problem at its source
For the first release of our new Kubernetes configuration security features, we are focused on integrating directly into your source control system of choice. We're launching initially with support for GitHub, GitLab, BitBucket Cloud, and Azure Repos. To get started, just import your repositories into Snyk and you'll see a new type of project for the Kubernetes configuration files:
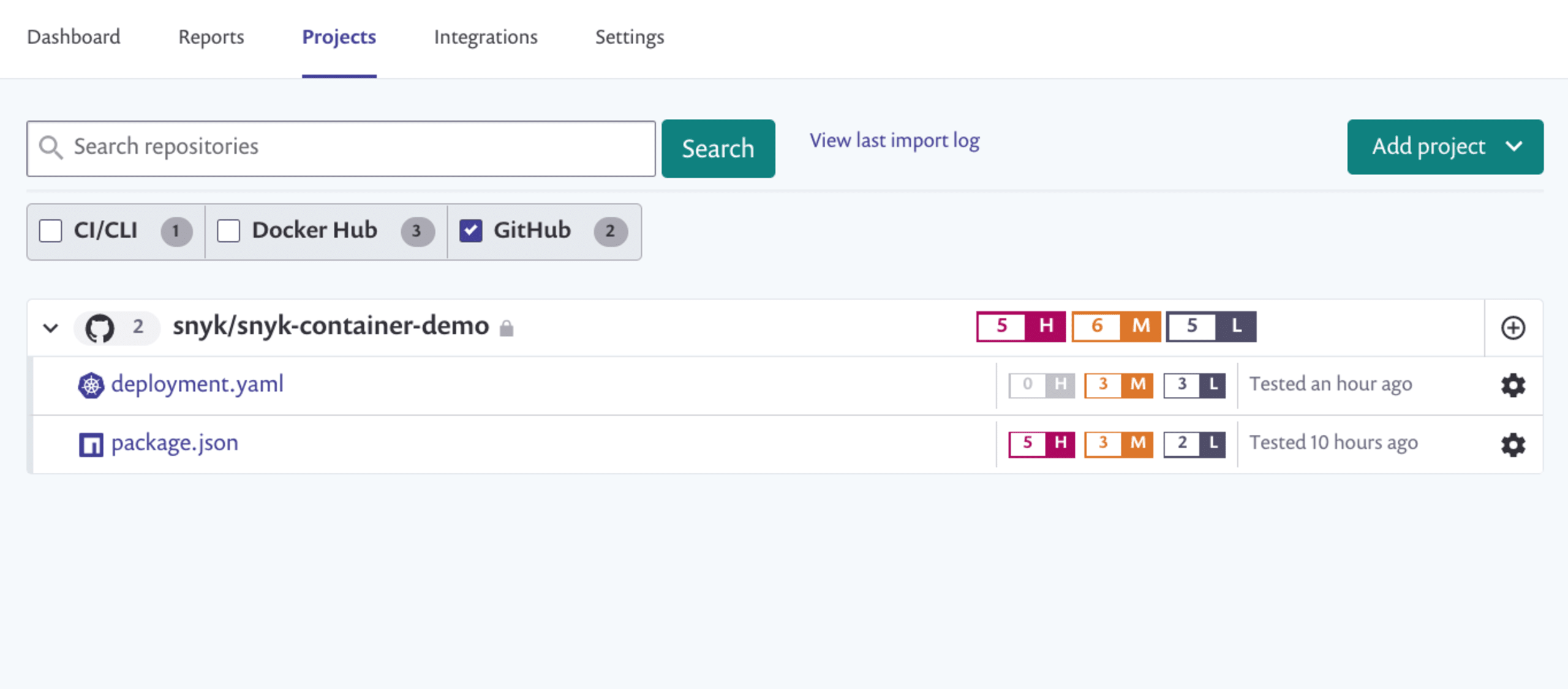
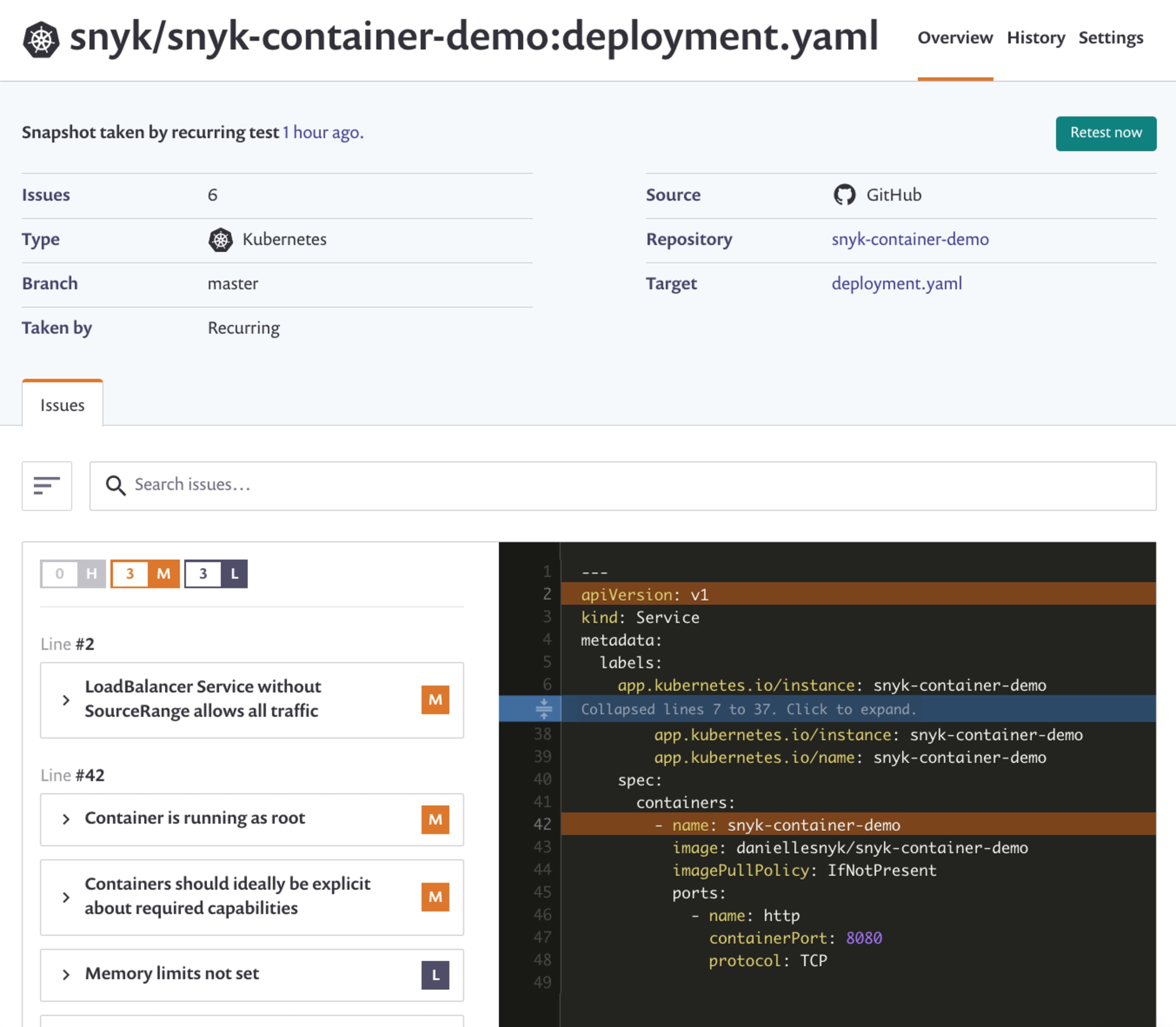
Clicking on those projects reveals a new page that shows all of the issues we've detected. Do you have pods running as root? Or without read-only file systems? Or with all the capabilities of the Linux host? Snyk detects those problems and puts them in context for you.
Not just for Kubernetes experts
As a project like Kubernetes becomes more popular, an increasing number of end-users want to use it without necessarily having to become experts in all of the minutia. Much of what we're highlighting in this new feature is well-known in the Kubernetes contributor community, but it's still too easy to make mistakes. Many new users won't even know about the various configuration options that can make their Kubernetes applications more secure. With this feature, we aim to help more developers adopt Kubernetes securely.
Try the new functionality today
This feature is available to all Snyk users on free and paid plans. We are rolling out the feature steadily and the plan is to have it enabled on every account in a week or so. If you are an on-premises Snyk customer, please contact your account team to discuss our on-prem support options.
Thanks to all of the beta users who provided valuable feedback on the features so far, and look out for lots of enhancements coming soon. Check out the documentation for the setup instructions to get started, and let us know what you think.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.