Fix cloud security issues faster and at the source with Snyk IaC
April 4, 2023
0 mins readSnyk Cloud update
This blog has been updated to reflect Snyk Cloud’s renaming to Snyk IaC. All cloud-related capabilities are now included in Snyk IaC or the greater Snyk platform.
Current cloud security tools create silos between engineering and security teams by focusing on identifying vulnerabilities after deployment, but fall short of empowering cloud engineers to act on their results. This forces developers to backtrack to fix issues or leads to the "ClickOps" trap, where teams spend an immense amount of time managing tickets and making policy changes in administrative consoles, pulling them away from more strategic work.
The cloud is code. Therefore the ideal approach is to secure cloud infrastructure as code and to bring IaC and cloud security together with a unified policy-as-code engine. Organizations should proactively scan IaC for misconfigurations and compliance issues, preventing them from ever reaching production, while also fixing cloud issues in IaC code and redeploying to improve their security posture and achieve scale.
As platform teams become inundated with more and more security requests, alert fatigue and ticket overwhelm can lead to apathy and low adoption of critical security tools. There can be a lack of trust due to the lack of context and integration into development workflows. Hours of time is wasted trying to locate the owner and location where fixes need to be applied.

Fix cloud issues at the source
Fixes applied in production via cloud provider policy settings cause your IaC and cloud settings to drift out of sync — meaning your IaC is no longer the “source of truth”. This configuration drift can cause breaking changes to your IaC workflow and force you to redeploy the same issues over again from the original templates. Since most cloud security solutions aren’t built for developers, they operate only in pipelines or production environments. Promises of "automated" remediation workflows aim to patch issues in production using cloud provider APIs, which sounds like a great option, but really only contributes to the issue of configuration drift.
Visibility alone is not enough. A fix-focused approach with continuous testing and a holistic view of cloud applications is necessary to improve the security of your cloud infrastructure, but getting to that fix isn’t always that straightforward.
Remediate in code with Snyk IaC
Snyk IaC takes a different approach to cloud security by empowering engineering teams to secure the cloud from the start. This proactive approach finds and enables fixes for misconfigurations in IaC code pre-build and pre-production, improving the risk posture of deployed infrastructure and reducing developer and security rework. Also, by providing dev-centric context on issues found in running cloud environments with remediation paths in IaC, Snyk IaC enables developers to secure the entire cloud engineering lifecycle and codify security standards from IaC code, to cloud, and back to code.
Snyk IaC’s newest feature maps cloud issues to the IaC file that each was deployed from and will now include a link to the IaC source file in your SCM. This direct mapping to the IaC source will save your cloud engineers hours of wasted time tracing issues from your cloud environment back to the IaC source code in order to implement the fixes and redeploy changes.
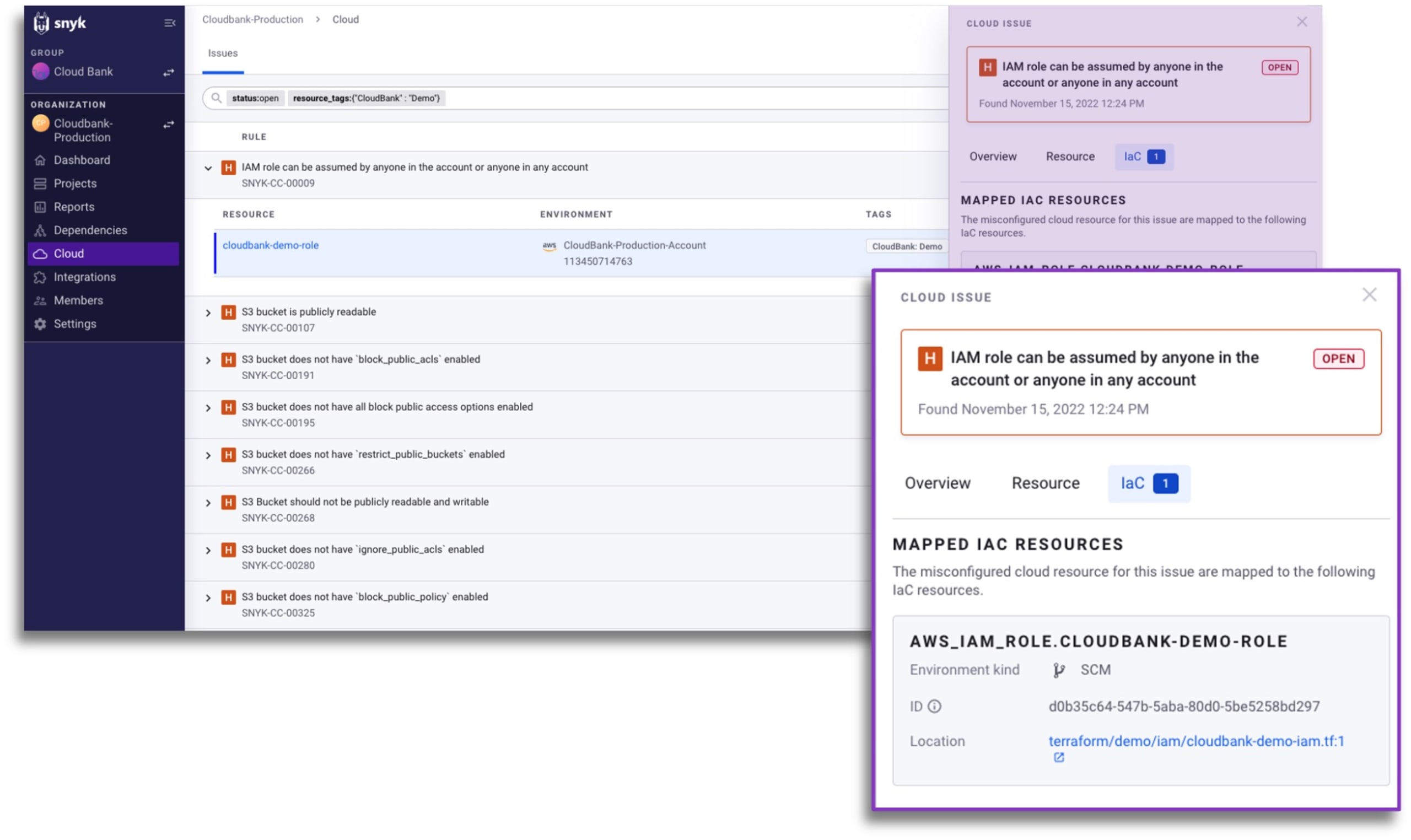
By unifying visibility and governance across IaC pipelines and running cloud environments security teams are equipped with more actionable results, while cloud and platform teams no longer waste time trying to locate fixes. The result is improved collaboration among security and development teams and a more secure cloud infrastructure.
IaC security designed for devs
Snyk secures your infrastructure as code from SDLC to runtime in the cloud with a unified policy as code engine so every team can develop, deploy, and operate safely.
