Announcing customized role-based access controls for Snyk
Daniel Berman
June 29, 2022
0 mins readWe’re pleased to announce Snyk’s new role-based access management capabilities, providing admins with greater flexibility in managing Snyk access in your organization!
As your development and security teams grow, it becomes critical that each of your team members using Snyk has only the required permissions to do their job. You need to ensure everyone can perform their jobs with ease, while also avoiding security and compliance issues. A developer, for example, needs the ability to find and fix vulnerabilities in his code but should not be able to change Snyk billing details.
Snyk already provides out-of-the-box user roles that determine the type of actions users assigned these roles can perform within the Snyk platform: Group Admin, Group Member, Org Admin, and Org Collaborator. These roles are predefined and cannot be modified. Because each organization is structured differently, this model might be too rigid. Some customers might find a particular role a bit too permissive while another customer might be interested in actually expanding permissions for that same role.
So, what’s new?
Following popular demand and building upon the principle of least privileges, Snyk is moving to a more customizable role-based access control (RBAC) model. Snyk Group admins can now grant users the permissions they need to do their jobs across the Snyk platform — and only those permissions — by creating their own customized roles and assigning specific permissions to them. This ensures the right people have the right access to the right resources at the right time, all in alignment with the internal structure and access policies within the organization.
Key features currently supported:
Easy to use- Group Admins can self-serve and use the Snyk UI to create their own custom roles in just a few clicks.
Flexible - Restrict privileges for custom roles using a comprehensive list of pre-defined, organization-level permissions.
Service account support - Group Admins can assign custom roles to an org service account as well as the org members.
Customized SSO support - New custom roles can be used together with your customized SSO setup without further configuration.
Important!This version allows customizing roles for organizations and assigning those roles to organization members and service accounts. In the next phase, Snyk will support group-level access (e.g. policies, group member management, reporting, etc.).
Create custom roles based on your needs
Creating a new role in Snyk is simple.
As a Group Admin, you will have the ability to open up a new Member Roles page under Group Settings.
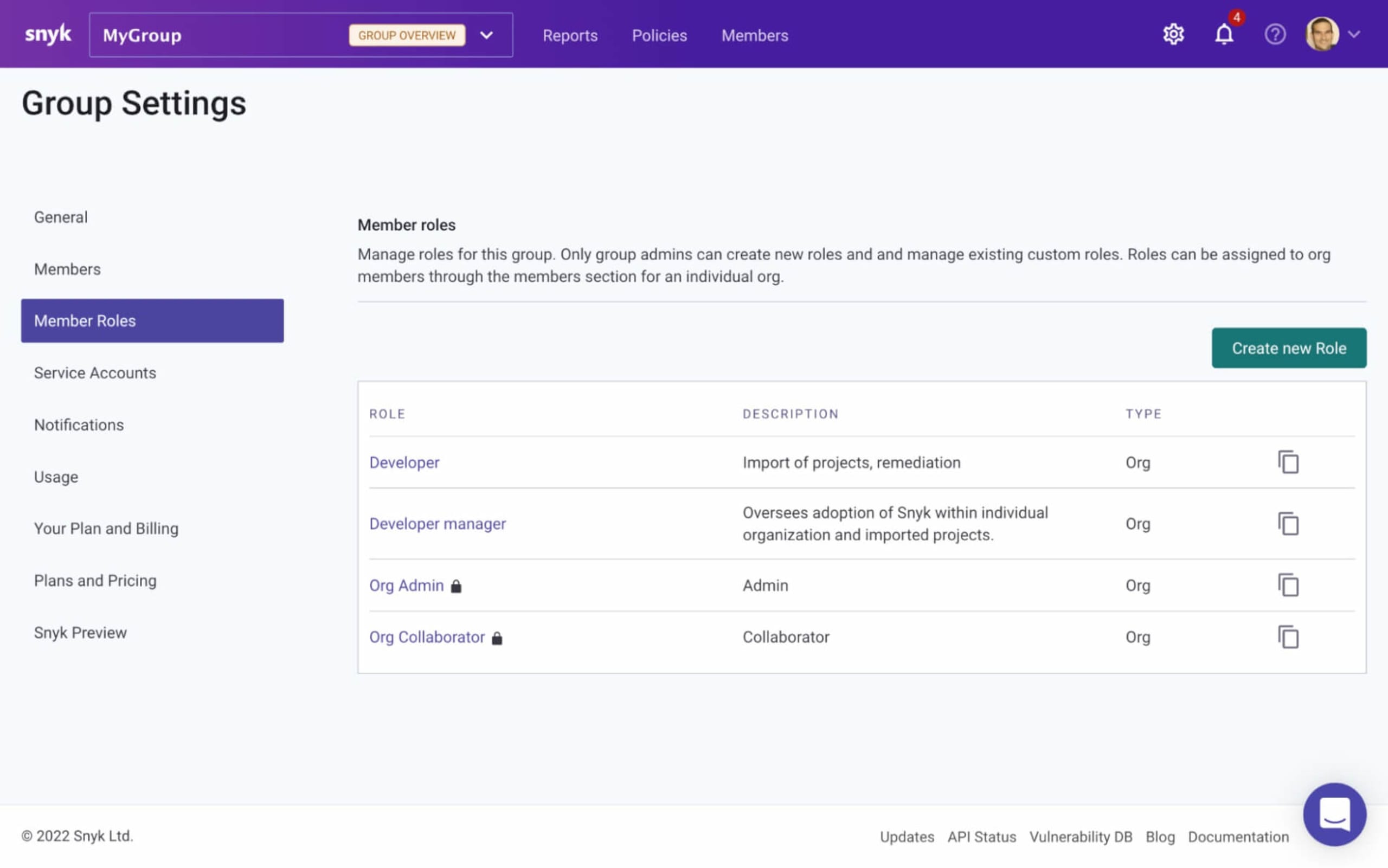
You will see a list of Snyk’s default roles — Org Admin and Org Collaborator. Clicking on either of these roles will open up another page containing a list of the assigned permissions which cannot be modified.
To create your own role, simply click the Create new role button, and in the window that pops up, give your role a name and a description (role names need to be unique):
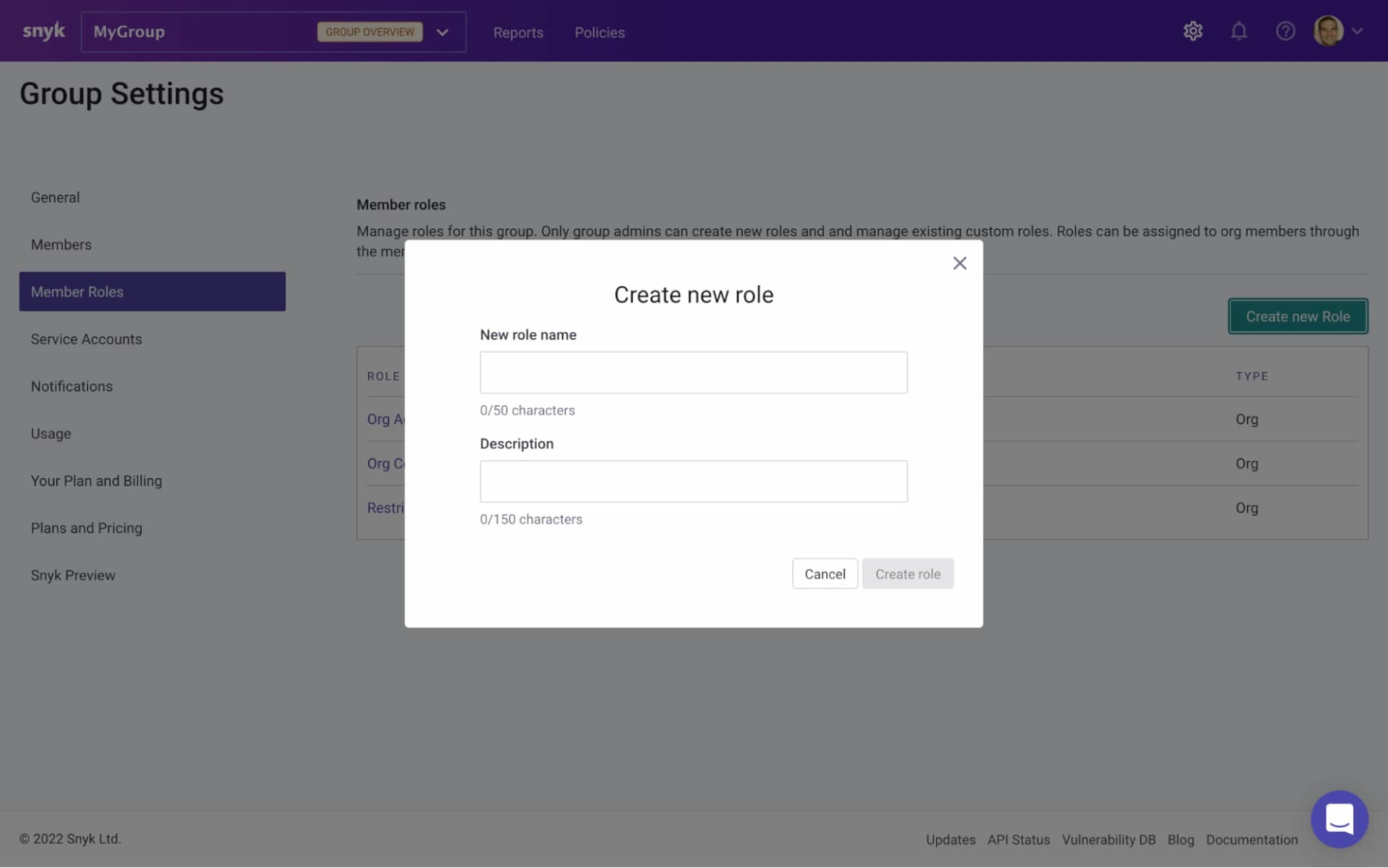
Next, select which permissions you want to assign to the role.
Permissions are grouped together in categories, so for example, under the Organization Management category, you will see permissions to create, edit, and remove an organization. And under the Project Ignore Management category, you will see permissions granting access to Snyk’s ignoring capabilities.
By default, and following the principle of least privilege, all categories and any of their nested permissions are unselected. To associate specific permissions with your new role, simply select them:
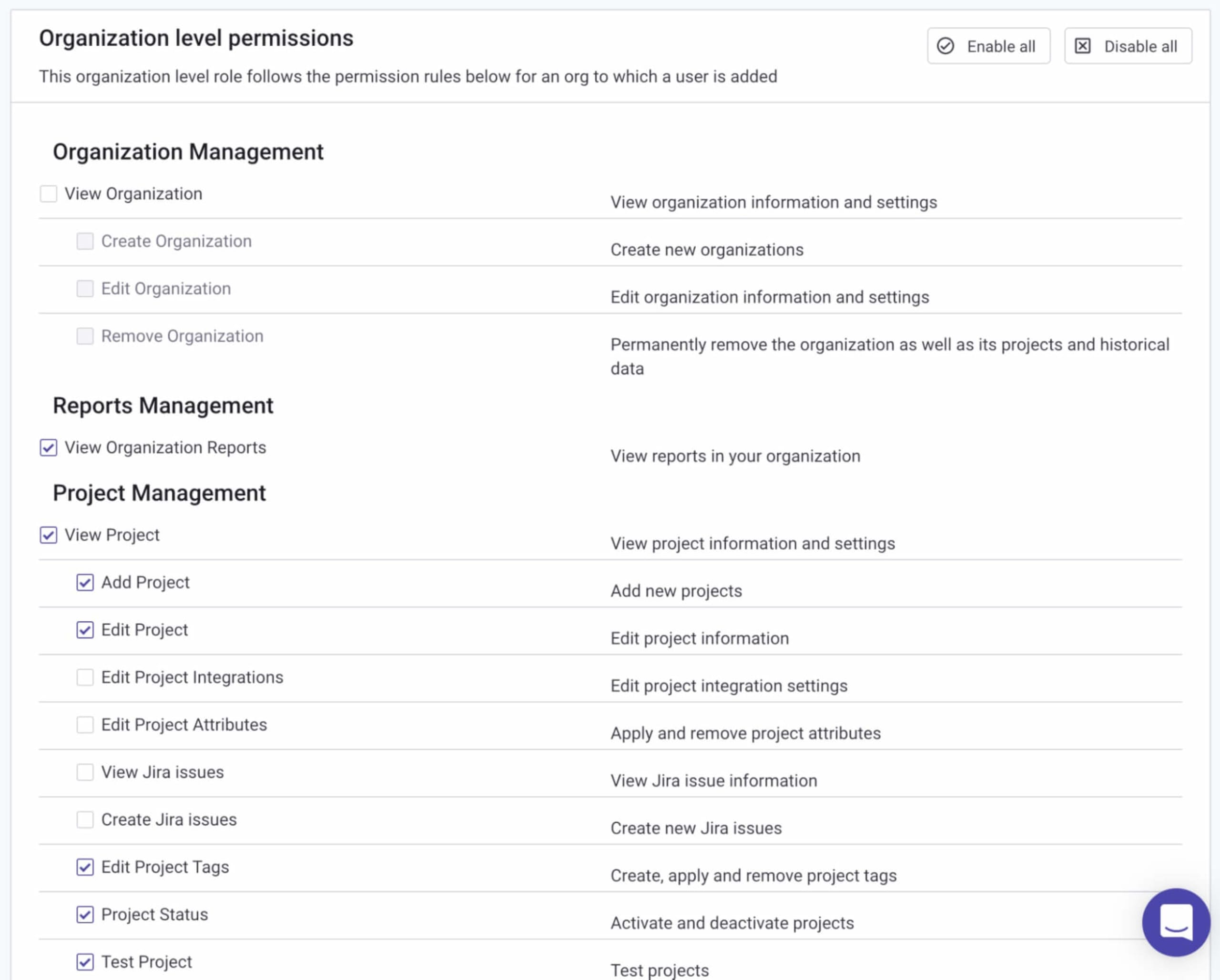
All that’s left to do is click Update role permissions at the bottom of the page. The new role is created with the selected permissions assigned to it, and listed on the Member Roles page.
You can edit this role at any time to assign new permissions to it or rescind any permissions already assigned.
Assigning custom roles to users
Once created, there are a number of ways to assign your customized role to a member in a Snyk organization.
Within the Snyk UI, select the organization you want to assign roles in and open the Members tab.
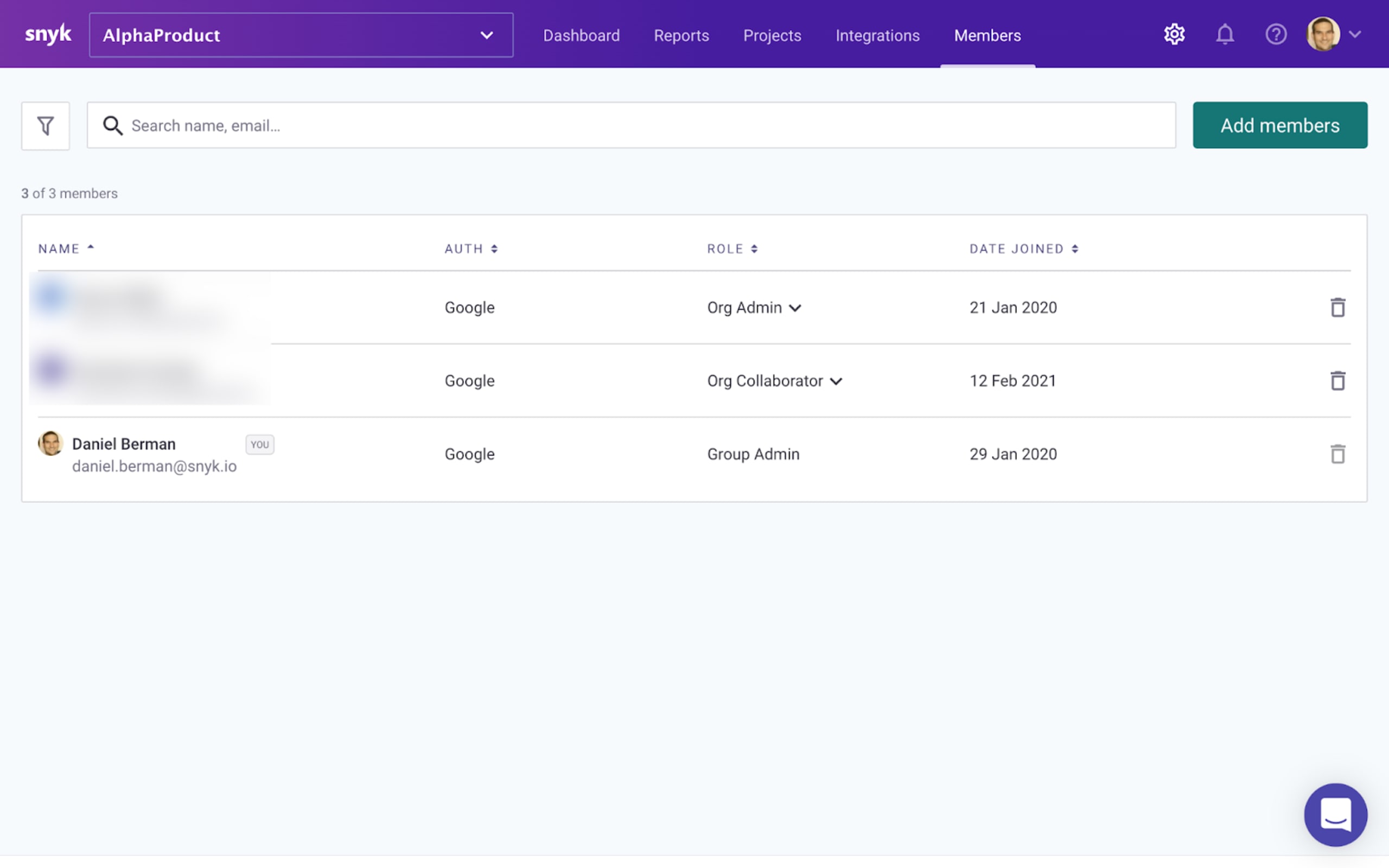
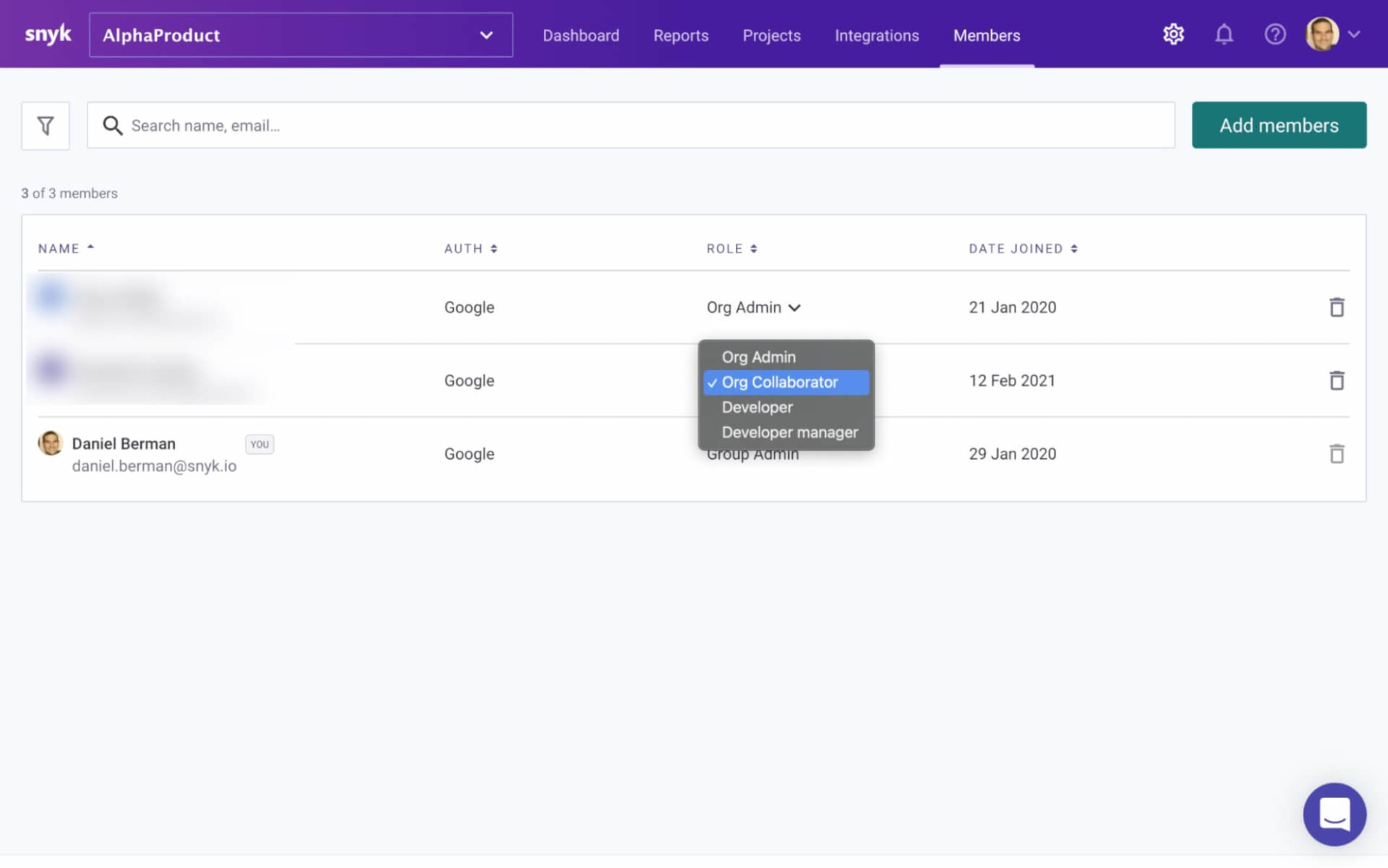
If you want to update the role of an existing member, simply click the role currently assigned to the member under the Role column and select your custom role from the dropdown menu.
You can also update the role of an existing member via the Snyk API.
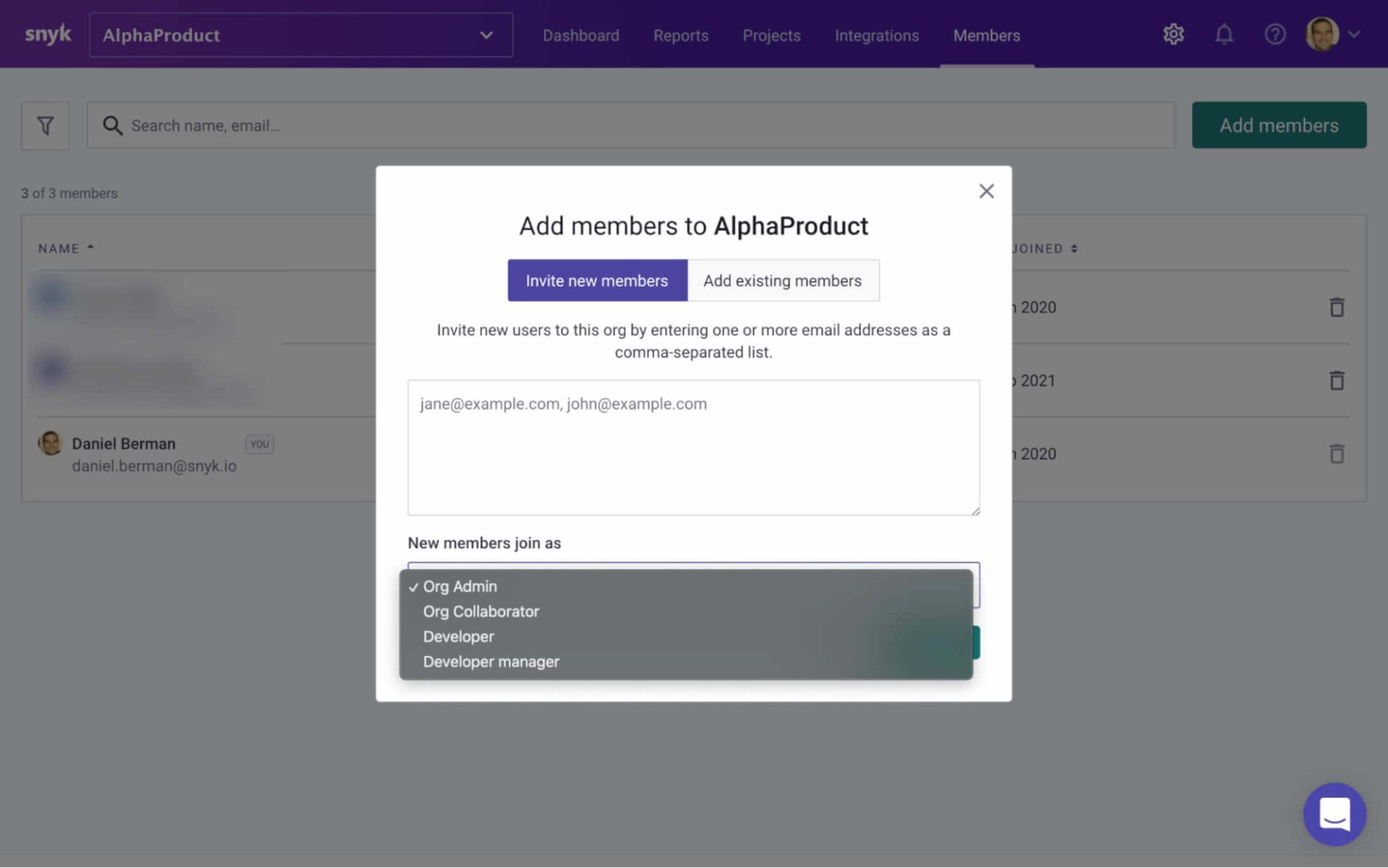
What about new members? Your new custom role can be easily assigned to any new member as they are added to an organization.
Click Add members and use the New members join as dropdown menu to assign your custom role.
Examples of customized user roles
Every organization is structured differently with different types of teams, different types of users, and different types of responsibilities. This is what makes this new ability to create custom roles so powerful — as a Group Admin, you can customize user roles based on how your specific organization is built. Below are a few examples but remember: these are just examples. Ultimately, how you define these roles and assign permissions is entirely up to you!
The developer role
To enable developers to actually find, prioritize, and fix issues, they need full access to their projects and the issues identified by Snyk’s testing. Though, in some organizations, developers would not be allowed to ignore issues. But they definitely don’t need to view Snyk billing information, right? A developer role could therefore be created that maps out these specific permissions, ensuring developers have the right degree of access to the Snyk platform to do their job.
The development manager role
For a manager of a team of developers, the scope of associated permissions will likely be wider. This of course varies from company to company, and will depend on the maturity and structure of an application security program, but more granular project management permissions will likely be required. The ability to edit projects and create Jira issues, for example, while not expected necessarily from an individual developer, are likely to be part of the development manager’s role.
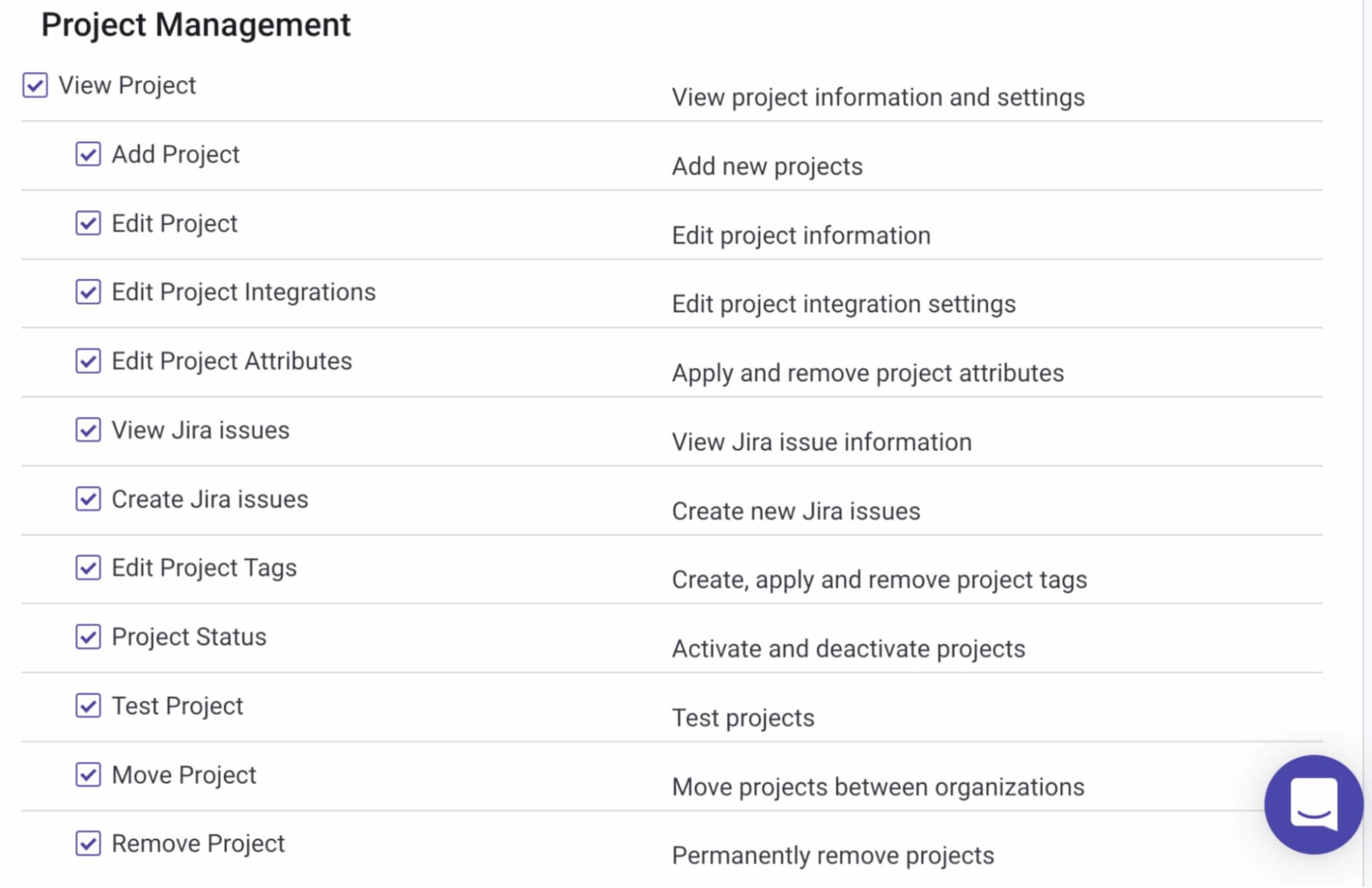
The application security role
In organizations where the application security team oversees the deployment of Snyk, permissions pertaining to organization, project, and user management could be required. Additionally, this role would need the ability to overview the way development teams are using Snyk and track the progress of the application security program in general. Permissions related to reporting and applying ignores to issues identified by Snyk would be likely assigned to this role.
Supporting governance at scale
From day one, Snyk’s vision has been to empower developers to take more responsibility for securing their applications, while enabling security teams to guide them through the process.
Features like policies, reporting, and now also the ability to customize user roles, together provide security teams with the control and visibility necessary to ensure developers can use the Snyk platform to find and fix issues in their applications effectively, all within accepted boundaries, and according to the organization’s internal requirements.
It’s a fine balance to strike, but it’s precisely this balance that Snyk’s developer security platform was designed to help you find.
As usual, we rely on your feedback. Future improvements to be introduced include support for group-level permissions, multi-group support, and API support, but if there is a particular capability you need, please let us know via the regular Snyk communication channels.
Snyk’s new customized RBAC capabilities are available for customers on our Enterprise plan. Try it out now!