Want to try it for yourself?
Understanding Security Automation
Security automation explained
What Is Security Automation?
Security automation is the use of software that can integrate security processes, applications and infrastructure with less human input, allowing security and development teams to deliver secure software at scale.
Similar to the above, application security automation is the process of connecting tools and solutions to find and fix vulnerabilities within software. Again, automation is a vital part of effective application security. By automating identification, prioritization, and remediation, development and security teams can focus on more challenging aspects of ensuring deployed applications remain secure.
With hackers now targeting applications more frequently, manual threat response is often slow and labor intensive, but application security automation offers easy-to-execute and repeatable processes that help ensure your technology environment remains secure. To achieve automated security, application security best practices recommend using different automated tools in every stage of the build, test, and release cycle.
Why Is Application Security Automation Important?
As software development grows in speed and complexity, application security has followed pace. But with this increased complexity, it has become increasingly difficult to manually manage security and compliance. Often businesses find that manual security efforts cannot keep up with the speed of innovation needed to remain competitive.
Manual security can be slow to detect and remediate new threats or errors in production environments. This can leave your systems open to attack or create compliance issues. To greatly enhance detection and remediation, security automation systems can streamline daily operations by integrating with policies, processes, applications, and infrastructure throughout the development lifecycle.
The deep impacts of a security breach offer the strongest argument for security automation. For example, an Equifax breach resulted in a class-action lawsuit that cost the company $380.5 million, and recent reports indicate that 43% of data breaches are connected to application vulnerabilities. Aside from direct financial losses, customer trust is often another casualty of security breaches which can lead to future losses.
Application development has changed dramatically. To keep up with the rapid pace of change, businesses shifted to the open source development model, illustrated below. In this model, only 10% to 20% of code is developed in-house. Today, 80% to 90% of the codebase in software is open source. Up to 86% of vulnerabilities can be found in these indirect dependencies.
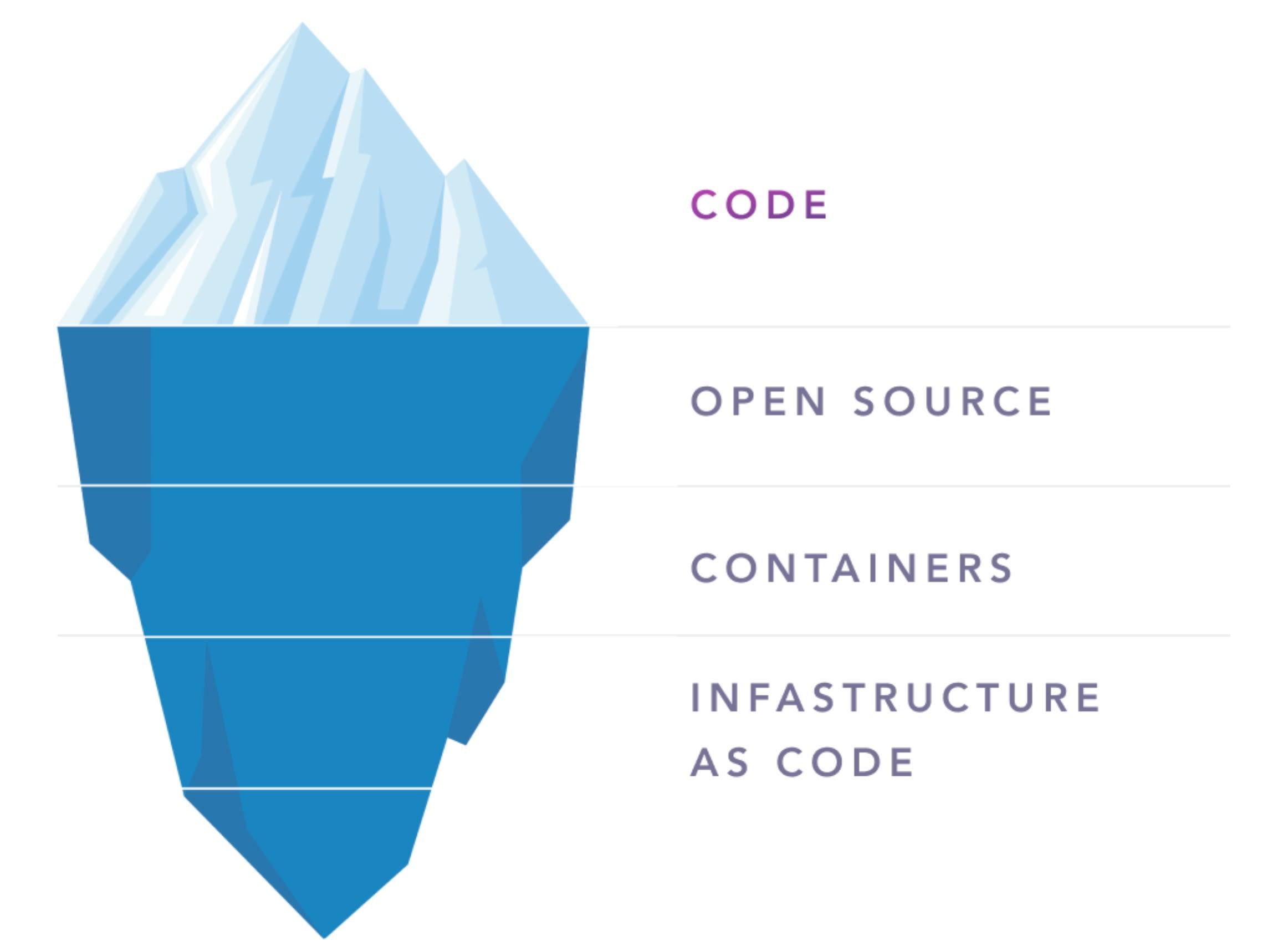
The increased use of containers and infrastructure as code (IaC) within application development also offers potential vulnerabilities. For example, infrastructure misconfigurations have led to some notable security breaches.
Effective application security automation empowers developers and security teams to react quickly and prevent costly breaches.
Benefits of Application Security Automation
"If we didn't have security automation and tooling in place, it would honestly be a nightmare. We would constantly be playing catch up on application dependencies or new containers. Lack of automation just doesn't scale."
Alfonso Cabrera, Director of Platform Engineering at Red Ventures
Automation frees up developers and security teams to focus on the more complex components of their jobs. Here are some other benefits of security automation:
Increased speed of detection: Security automation adds intelligence to threat detection across the entire IT environment, triggering security notifications based on recognized threats.
Improved incident response: AppSec teams can easily become overwhelmed with security alerts. Automated security systems help prioritize threat notifications for response. Additionally, some responses can be automated to remediate without manual intervention.
Enhanced visibility into security metrics: Security automation tools help you track and report on security incidents and threats. These reports allow AppSec teams to focus their efforts on critical areas and develop effective application security policies.
Live Hack: Exploiting AI-Generated Code
Gain insights into best practices for utilizing generative AI coding tools securely in our upcoming live hacking session.
Traditional security processes tend to offer manual incident response only as a postmortem after an incident has taken place. The illustration below shows a traditional plan, build, and deploy model as a time- and developer-intensive process.
It’s unrealistic to expect a pristine application deployment without vulnerabilities or incidents. However, incidents can be mitigated by automating security scanning early in the process with mechanisms that support proactive responses to potential issues.
Automated security scanning ensures confidence in software deployments by identifying known vulnerabilities during the build phase of development and suggesting code fixes that remediate the issue. Additionally, automated scanning can help you be fully aware of all your vulnerabilities, so you can properly lower the priority of those that are less likely to ever be exploited. This eliminates alerts and postmortems from the traditional process.
What Security Processes Can Be Automated?
Security automation can manage some of the more tedious and most critical aspects of your security framework. Here are five processes that can create the most benefit when combining automation and security.
Monitor and detect: Businesses must have visibility into every facet of their IT environment at all times. Security monitoring tools can provide this visibility at scale while integrating any detected vulnerabilities into a comprehensive view for ongoing monitoring. Additionally, some automation tools monitor open source code in applications in production against vulnerability databases, then notify security teams of any newly discovered vulnerabilities.
Threat investigation: Once a vulnerability has been identified, security teams need to discover which machines or nodes are affected, what damage was caused, and which vulnerabilities were exploited. Security automation can complete much of this forensic work in far less time than developers or engineers. For example, if there was a denial of service (DoS), an automated security tool can determine if the DoS was the result of misuse or a sudden HTTP-flood. This information helps determine what protection or remediation is needed.
Incident response: When a vulnerability or attack is identified, AppSec determines the appropriate response. Security automation can complete many responses quickly, such as removing malware, deactivating a service, or installing patches or upgrades to protect against new incidents. If a system is infected with malware, for example, automated tools can fetch forensic data, disable the infected network, run vulnerability scans to identify other at-risk systems, and isolate those until they are addressed.
Permission management: Managing users and their permissions is a critical security task. But when users number in the thousands, it can be challenging to keep up. Adding, modifying, or removing users and employees in this scenario can take hours or days. Automating the provisioning or deprovisioning of a user or investigating host escalations — among many other user-related tasks — will save effort, time, and ultimately resources.
Application and business continuity: Can AppSec teams ensure that systems and data remain operational during (or after) an attack? Or does the system need to be taken offline completely for some attacks to prevent critical damage or information breaches? Security automation can apply IP blocking rules during a brute force attack to prevent damage and allow the use of other IP addresses. Additionally, automation can replicate critical server instances, helping to ensure important data remains available.
What Security Processes Cannot Be Automated?
Even with improvements in automated security technology, there are still many elements that need human attention to verify or to accurately determine potential application security vulnerabilities. The question emerges: what parts of security can’t be automated?
The following processes require expertise that simply can’t be automated because they are highly nuanced and context-specific:
Threat modeling is an important part of building secure software. Because these models require context-specific planning that incorporates authorizations and business logic flaws, they require an experienced internal tester with comprehensive knowledge of the entire software environment. The models help developers and security teams understand the risks in an application before it is built. When done correctly by the team building the software, the value of this process is bigger than just the risks found. Threat modeling increases security awareness and promotes a culture of security ownership. Although there are tools to automate this process, we recommend it to remain a manual and expert-driven process.
Penetration testing, or pen testing, uses controlled cyber attacks to target a running system to determine vulnerabilities that could be exploited by attackers. Much like modeling, every software environment is different, offering specific areas of potential attack. So, pen tests require the business-specific knowledge and imagination of an in-house security engineer. While pen testing cannot be automated, it is more powerful if the person performing the test writes tests to reproduce the findings. Later on, those tests should run as part of the pipeline to prevent the issue from happening again.
Bug bounty programs invite independent security researchers to report bugs, security exploits, and vulnerabilities to an organization in exchange for rewards or compensation. These programs are an effective means of identifying unknown issues before they are discovered by bad actors. Bug bounties generally cannot be automated because many of the sites and applications offering the bounty have gone through automated systems prior to setting up a bug bounty offering.
An effective application security program goes beyond automation. Although the above processes cannot be automated, they can help secure your applications. Manual and automated application security testing complement each other.
Automated Remediation Processes
Automated application security tools look for known vulnerabilities and offer suggestions to developers for responding to these incidents. Because breaches often exploit vulnerabilities in the application layer to access systems, these automated security suggestions can be critical for improving application layer security. But security automation can go further. It’s possible to automate incident responses to further reduce the labor burden of AppSec teams.
Beyond proactively addressing vulnerabilities during the build, the following can be applied for the automated vulnerability remediation process in the software development lifecycle (SDLC):
Suggesting minimal fixes: Automated application security tools identify the minimal upgrade required to clear a vulnerability and alerts developers of any risk of breaking the code with the suggested fix.
Fix on pull request: When configured within pull request scanning, automated security tools can populate incident notifications within the pull request to offer automated fixes, giving the developers the opportunity to implement the required upgrades and patches with a single click.
Patch management: When upgrading for an incident would disrupt application systems, automated security pinpoints the patch needed and manages the rollbacks needed to ensure production environments remain stable.
Dependency upgrades: Automated security helps keep projects secure and current by finding and quickly fixing vulnerable and out-of-date dependencies.
Live Hack: Exploiting AI-Generated Code
Gain insights into best practices for utilizing generative AI coding tools securely in our upcoming live hacking session.
Gain Greater Success with Security Automation
Today’s development processes and the increasingly complex threat landscape have made security automation a practical necessity for any successful software operation. Application security automation helps drastically reduce incident response times and puts DevOps ahead of known threats. Automation means less exposure to fewer threats and greater assurance for customer information, which ensures business reputation and greater profits.
Learn more:
Try our free online code checker tool to see how the Snyk code engine analyses your code for security and quality issues.
Up Next
Key Components of the DevOps Pipeline
A DevOps pipeline helps teams build, test, and deploy software quickly and efficiently through a combination of tools and practices. Learn how it works and how to apply it.
Keep reading



















