Zero-day Extensive NPM Package Compromise - Shai Hulud Supply Chain Attack
September 15, 2025
0 mins readThis is an ongoing incident and updates will be provided as more information is confirmed.
Identify how you may have been impacted by this attack with Snyk's featured Zero Day report.
TL;DR (Sep 17, 2025)
The attack, which began around September 15, 2025, and came to be dubbed “Shai-Hulud,” is now known to be a worm-like malware that spreads over hundreds of compromised npm packages. The attack aims to steal and exfiltrate on-disk cloud credentials, API keys, and other secrets, transmitting them over a webhook and public GitHub repositories. It also targets CI/CD environments, relying on GitHub Actions to exfiltrate data and persist the attack.
Update (Sep 16, 2025)
The Snyk security research team is aware of this ongoing supply chain attack and is actively investigating, analyzing, and curating threats and risks resulting from this extended npm compromised packages attack. We recommend you refer to the Snyk product findings as an up-to-date resource.
Update initial (Sep 15, 2025)
On September 15, 2025, multiple malicious versions of the ngx-bootstrap and ng2-file-upload npm packages were published and then quickly pulled. Those releases embedded a postinstall script (bundle.js) that attempted to harvest developer tokens (e.g., npm, GitHub, cloud credentials) and exfiltrate secrets. Treat any system that installed these versions as fully compromised: remove the package, rotate all secrets from a separate, trusted machine, and investigate for lateral movement. GitHub has posted a malware advisory for ngx-bootstrap and ng2-file-upload; no patched version exists for the tampered builds because they were removed.
Since the initial ngx-bootstrap findings, malware signals have also extended to the @ctrl/tinycolor npm package downloaded at more than 2 million times a week and compromising more npm packages under the @ctrl, and @nativescript-community namespaces and other individual packages.
What is ngx-bootstrap and why this matters
ngx-bootstrap is a popular Angular component library that wraps Bootstrap UI components for Angular apps. It’s widely used in front-end projects, CI builds, and developer workstations, meaning a malicious install script can run during routine npm install, with access to developer machines and local credentials. The official repo is maintained by Valor Software.
What we know so far
Affected packages are likely 100s
The attack has further advanced to compromise other packages beyond ngx-bootstrap and @ctrl/tinycolor and includes more organization namespaces such as packages belonging to the cybersecurity company Crowdstrike under the npm package namespace @crowdstrike and others.
The following is not meant to be an exhaustive list but rather a reference. We always advise you to refer to the Snyk product, scan results, and reporting for an up-to-date and comprehensive list of all malicious packages and versions.
Broader affected packages can be found on our dedicated Vulnerability Database compromised packages page.
Affected ngx-bootstrap package and versions
Community reports documented that the following ngx-bootstrap versions contained the malicious postinstall hook invoking bundle.js:
20.0.4, 20.0.5, 20.0.619.0.318.1.4
Additionally, 20.0.3 reportedly contained bundle.js but without a postinstall declaration. The same report notes the affected versions were removed from npm shortly after discovery.
Note: At the time of writing, the npm package page shows only current, non-impacted versions; the malicious ones were unpublished.
Community reports also flagged ng2-file-upload as “looking affected,” but details are thinner; keep an eye on dependency trees that include Valor Software packages and validate installed versions.
Timeline (UTC)
2025-09-15 — Community report opens on
valor-software/ngx-bootstrapidentifying maliciouspostinstall/bundle.jsin new versions; notes token exfiltration attempts and that affected versions were pulled from npm.2025-09-15 — GitHub Advisory Database posts GHSA-6m4g-vm7c-f8w6 for
ngx-bootstrap(“Malware”), with guidance to treat installing hosts as compromised.
(We will update as new, verifiable facts emerge from maintainers/registries.)
Impact assessment
Who’s affected? Developers, CI agents, and endpoints that installed one of the listed versions, or pulled them via transitive deps during the window they were available.
What could be exposed? Developer environment secrets and tokens (npm, GitHub), and potentially cloud credentials (AWS/GCP/etc.) based on the behavior described in
bundle.js.Additionally, an indicator of compromise (IoC) is attributed to a new GitHub Actions workflow named
shai-hulud, created by the malware.Severity: Critical (malicious code execution at install time; credential theft/exfiltration). GitHub’s advisory explicitly instructs a full compromise response.
How to detect 0-day npm malware with Snyk?
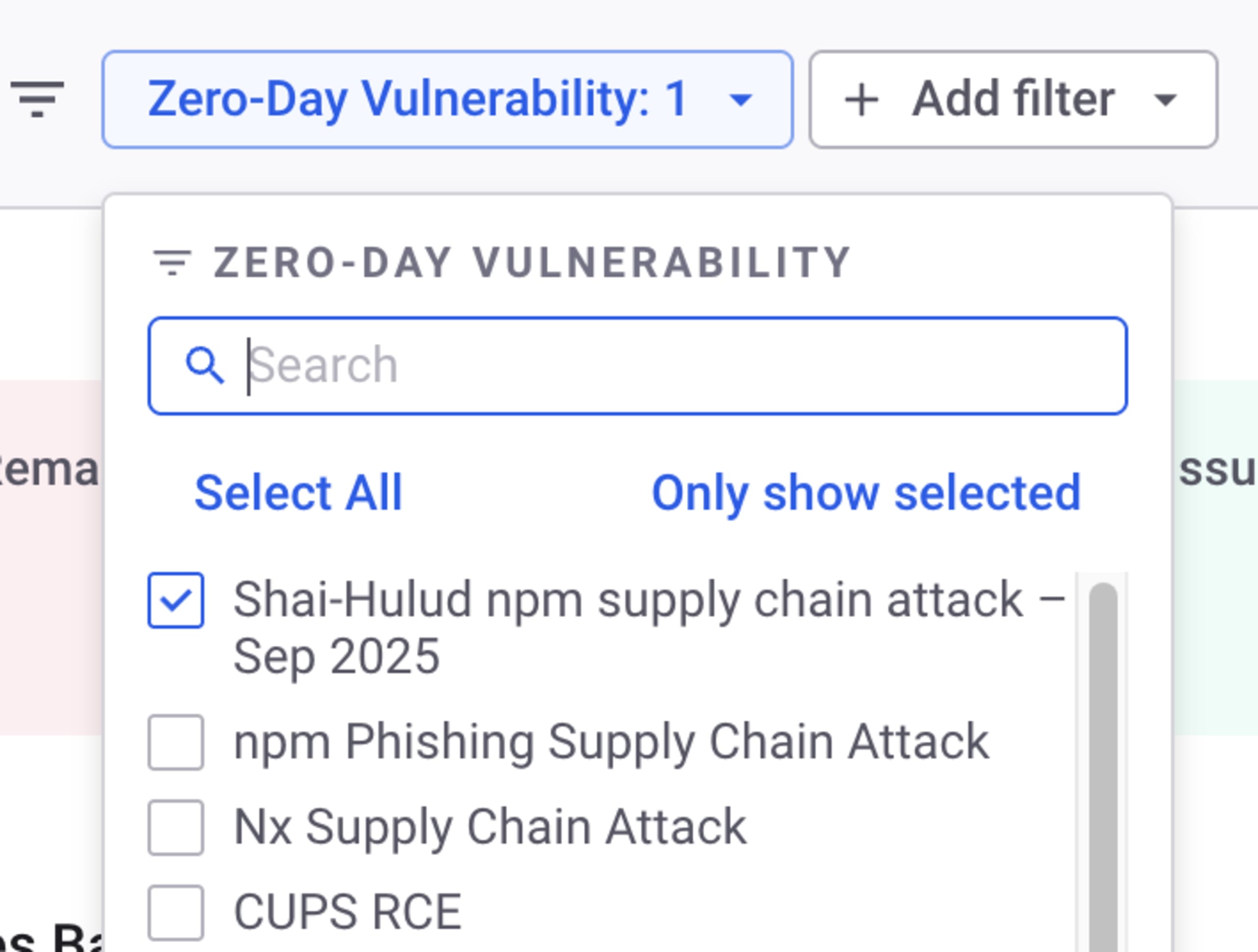
Snyk features a Zero-Day report as part of the dashboard in the Snyk app called Shai-Hulud npm supply chain attack - Sep 2025.
If you're on an Enterprise plan, you can use this view to filter the report and select the relevant zero-day for this npm malware attack or specific CVEs you wish to track and gain a system-wide view of the impact for this tinycolor / ngx-bootstrap or other dependencies across your applications and monitored code repositories.
Detection & triage playbook
Identify exposure quickly
Check whether your environment pulled impacted versions:
npm ls ngx-bootstrap(per project)Review lockfiles (
package-lock.json,pnpm-lock.yaml,yarn.lock) forngx-bootstrap@18.1.4,19.0.3,20.0.4–20.0.6, and note any installs performed on/after 2025-09-15.
Inspect
node_modules/ngx-bootstrap/package.jsonfor apostinstallentry, and look for abundle.jsfile in the package root if you maintain vendor archives/caches
Halt script execution during incident response
Reinstall with scripts disabled to prevent any remaining lifecycle hooks from running:
npm ci --ignore-scriptsornpm install --ignore-scriptsYou can also set
ignore-scripts=truein.npmrc
Forensic checks
Review outbound connections from build agents/developer hosts at install time windows.
Audit GitHub (access token lists, recent security logs), npm tokens, and cloud provider credential usage for anomalies. Audit GitHub Actions.
Treat any host that ran an impacted version install as compromised per GitHub Advisory guidance.
Immediate containment & remediation
Remove impacted versions
Delete
node_modulesand lockfiles referencing malicious versions; reinstall pinned, known-good versions.Clear any private registries/caches/artifacts that might still hold the bad tarballs.
Rotate secrets from a clean machine
GitHub: revoke personal access tokens/SSH keys; rotate fine-grained tokens; review OAuth app/device authorizations.
npm: revoke registry tokens.
Clouds (AWS/GCP/etc.): rotate access keys/service account keys and invalidate any long-lived credentials.
Rebuild/redeploy
After rotation, rebuild from clean environments with lifecycle scripts disabled initially, then re-enable as needed.
User/tenant communications
If you distribute software built during the window, notify downstreams and advise upgrades/rebuilds.
On supply chain security attacks
This comes along with a few other recent security incidents of this nature. We’ve seen CI and maintainer-account attacks allowing release hijacks before:
The ESLint/Prettier maintainers compromise (July 2025): Phishing + typosquatting (
npnjs.com) harvested npm credentials and pushed malware to popular packages, another reminder to harden maintainer accounts with 2FA.Weaponizing AI Coding Agents for Malware in the Nx Malicious Package Security Incident (August 2025)
npm Supply Chain Attack via Open Source maintainer compromise (September 2025)
Secure your supply chain with Snyk
87% of our respondents were impacted by supply chain security issues. Keep yours secure with Snyk.
