Patching Detected Vulnerabilities with Factory AI and Snyk Studio
Programming with Factory AI’s Droids feels great. It’s cohesive, it’s smooth, it’s juicy; it feels like playing a game. One can sense their commitment to this ideal not just in their UI, but also in their partnerships – one key integration being with Linear (which is Jira’s younger competitor with a reputation for enriched UX via reactive web app animations and keyboard shortcuts). If tools like Claude Code, OpenAI Codex, and Gemini CLI are an offline Word document, then Factory AI’s offering is an online Google Drive built from the start with collaborative teams in mind.
Their developer journey includes a well-made tutorial built into their website, which guides you step by step to:
Download the Factory CLI
Add the Droid IDE Extension to VS-Code or your fork of choice (i.e., Cursor or WindSurf)
Give your Droid (Factory AI’s specialized AI Agents) its first task, in the browser or in the IDE.
If you’re on Linux, you can install the Factory CLI like so:
The extension for VSCode is available here. Once installed, you can use `Ctrl-Shift-P` to open the Command Palette and select Run Factory Droid.

What’s in a Droid?
Factory AI offers specialized AI agents for a breadth of common software development tasks. These are referred to as Droids.
Code Droid: Go from idea to merge-ready code changes. Write new features or components with clear requirements, leveraging Code Droid's ability to understand your codebase and implement functionality that follows your project's patterns and best practices. Improve existing code by identifying complex or inefficient patterns and transforming them into cleaner, more maintainable solutions while preserving functionality and enhancing performance. Analyze error logs, identify root causes, and develop fixes for bugs in your codebase. Create comprehensive unit tests to ensure code reliability and prevent regressions in your applications.
Knowledge Droid: Engineering research, technical documentation, and onboarding guides. Generate comprehensive documentation for your codebase, including API references, architecture overviews, and component relationships to improve team understanding and onboarding. Get clear explanations of complex systems, architectural decisions, and implementation details within your projects to help team members understand how different components interact. Quickly find and extract specific information from your codebase and documentation, saving time when looking for implementation details or understanding particular features.
Reliability Droid: Investigate incidents, write RCAs, and debug complex multi-service systems. Analyze production incidents by examining error logs, metrics, and system behavior to quickly identify patterns and potential causes of outages or performance degradation. Create comprehensive Root Cause Analysis documents that include timeline, impact assessment, root cause identification, and preventative measures to share with stakeholders. Develop robust error handling mechanisms, including circuit breakers, retry logic, and graceful degradation patterns to improve system resilience and prevent cascading failures.
Product Droid: Plan features, create PRDs, and manage your projects. Generate detailed Product Requirements Documents with feature overviews, user stories, acceptance criteria, technical considerations, and implementation phases for new product features. Create comprehensive user stories with detailed acceptance criteria for different user types and scenarios, helping development teams understand feature requirements from the user perspective. Analyze feature requests and develop prioritization frameworks with impact vs. effort assessments to help product teams make informed decisions about implementation order.
This contemporary approach to AI agents – to offer a library of pre-built and specialized agents – allows users to make the most of their LLMs’ limited context windows. While the singular agent offered by tools like Claude Code, OpenAI Codex, and Gemini CLI “can” be versatilely applied to a similar breadth of tasks, Factory AI has put the time into providing developers with an agent that can do so with expert management of its context for its very particular purpose. That’s not to exclude the general-purpose Droid that is also included in their library, which you can of course rely on for any purpose not covered by the specially prepared set of Droids.
Happily, Factory AI does not lock you into any single LLM vendor. The most well-known vendors are readily available (see below). And for LLMs with unique variants for things like reasoning, you can easily make your choice in the same UI dialog.

MCP support
Similar to other AI agent CLIs, Droid CLI offers fantastic Model Context Protocol (MCP) support. Adding your favorite MCP server is easy.
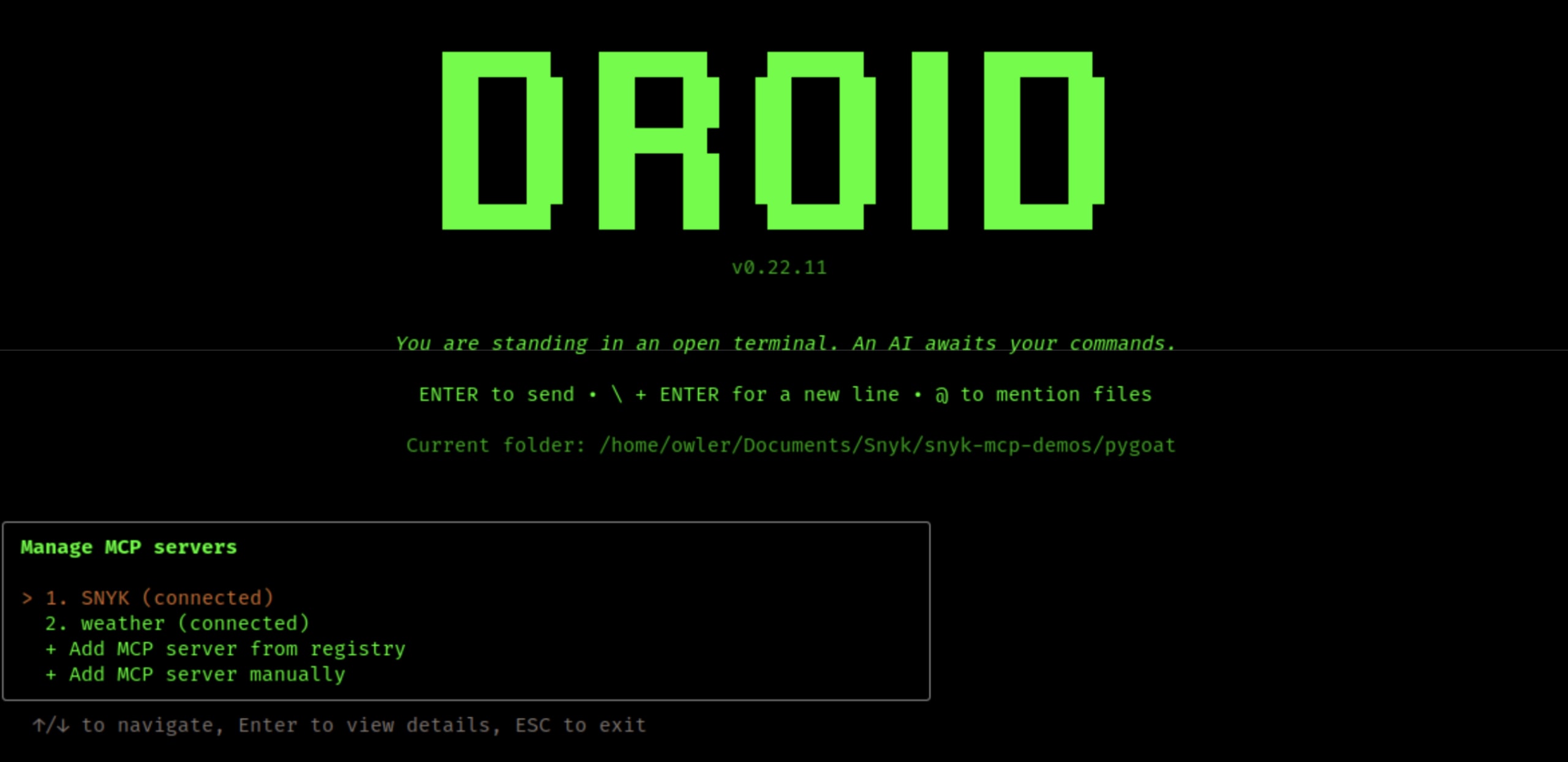
For example, the official Snyk MCP Server can be added like so :
But what can we do with this? What would be the benefit of extending the toolset available to an already-capable Droid? Support for running shell commands, reading, writing, and editing files is already built in.
Using AI agents (Droids) to automatically patch vulnerabilities
For this example, I’ve cloned OWASP Project Leader adeyosemanputra’s pyGoat repository. This project intentionally includes a series of well-documented vulnerabilities for educational purposes. Here are some of the vulnerabilities highlighted by Snyk’s own IDE extension:

We can also ask Droid to use the MCP server to list some of those same vulnerabilities. See:
Finally, with the Code Droid selected, we can ask the LLM to patch one of these high-priority vulnerabilities.
This demonstrates the potential for a new paradigm in DevSecOps workflows. Rather than security being a separate, often delayed concern, we can now integrate vulnerability detection and remediation directly into the development process. The combination of Factory AI's specialized agents with MCP servers like Snyk’s means that security issues can not only be identified but also swiftly fixed and re-verified for correctness—all within the same interface where developers are already working.
Next steps with Factory AI and Snyk Studio
As MCP adoption grows and more security tools develop MCP servers, we can envision Droids that not only patch vulnerabilities but also generate security tests, update documentation to reflect security fixes, and even create tickets for manual review of complex issues. The modular nature of both Factory's Droid system and the MCP protocol means these capabilities can evolve independently while remaining interoperable.
For teams looking to implement similar workflows, the setup is straightforward: install the Factory CLI, add your preferred MCP servers, and start patching vulnerabilities to build confidence in the automated patching process. The key is treating AI agents as force multipliers for your security team rather than replacements—they excel at handling the routine, well-understood fixes while humans focus on the novel security challenges that require creative problem-solving.
Want to learn more about securing the MCP Server ecosystem? Download our Ebook today.
EBOOK
Securing the MCP Servers Ecosystem
Explore emerging attack paths and unpack real-world incidents to show how to defend against them with practical, flow-aware strategies.