Snyk users don't have to worry about NVD delays
Hadas Bloom
March 13, 2024
0 mins readEditor's note: September 19, 2024
Update: NVD still has significant delays.
355 CVEs published in the Snyk Security Database in 2024 have yet to be analyzed by NVD.
You may have encountered recent discussions and the official notice from NVD (National Vulnerability Database) regarding delays in their analysis process. This message was posted on the February 13:

We want to assure you that these delays do not compromise the integrity or efficacy of Snyk's security intelligence, including the Snyk Vulnerability Database.
What powers Snyk's security intelligence?
Snyk Vulnerability Database (VulnDB) derives its strength from a dedicated team of security analysts, supported by advanced technologies. This interdisciplinary team of analysts, researchers, product managers, and engineers is at the forefront of all security-related endeavors at Snyk. From researching zero-day vulnerabilities to aggregating structured and unstructured vulnerability sources, their efforts are pivotal in maintaining the integrity and accuracy of the Snyk Vulnerability Database.
How does Snyk analysis and triage work?
On a daily basis, Snyk’s security analysts meticulously review numerous vulnerability-related events to publish new advisories with actionable and precise information.
The collection process includes multiple types of sources:
Structured community ecosystem databases, such as RubySec Advisory DB.
Official databases and advisories, such as NVD.
Unearthing unpublished vulnerabilities using machine learning algorithms to uncover uncataloged vulnerabilities from public forums or source control repositories.
Community and academic disclosures, including collaboration with independent researchers and academic institutions.
Proprietary research and vulnerability trend analysis to find zero-day vulnerabilities and identifying exploits, such as the recent Leaky Vessels research (Docker and runc container breakout vulnerabilities).
Human intelligence, augmented by AI, drives the decision-making process, which includes validating that the potential threat is an actual vulnerability and ensuring all actionable details are added. Our in-depth research is why organizations trust Snyk.
Snyk open source advisories are not dependent upon NVD
All of Snyk’s open source vulnerability advisories undergo rigorous assessment by Snyk security analysts, regardless of (and many times in advance of) the analysis applied by NVD. While NVD data is provided alongside Snyk's own analysis when available, the delivery of our vulnerability data and its quality are not directly impacted by external incidents (like delays in NVD analysis).
To be more exact, every open source advisory added to the Snyk Vulnerability Database is accompanied by precise package coordinates, vulnerable version ranges, CVSS vectors, and detailed insights, regardless of what other sources provide. In addition, while NVD only analyzes vulnerabilities with CVE IDs, the Snyk Security Team analyzes vulnerabilities regardless of their CVE ID assignment status.
Snyk container advisories
For container advisories, Snyk employs a semi-automated process that considers multiple sources for assessment. Container advisory details rely primarily on the Linux distributions’ own provided information and assessment because they have the most context when it comes to issues in their respective environments. Therefore, package coordinates and vulnerable version ranges for these advisories will also not be affected by delays in NVD.
Severities and CVSS scores are assigned using a combination of the best assessments available, taking into account the Linux distribution’s assessment and NVD’s. You can learn more about how that is done from our documentation. Advisories in which the Linux distribution does not provide their own CVSS assessment or severity level (“Relative Importance”), and relies on (or passes through) NVD’s instead, will see delays in CVSS assessment as a result of this incident.
Go beyond NVD with Snyk
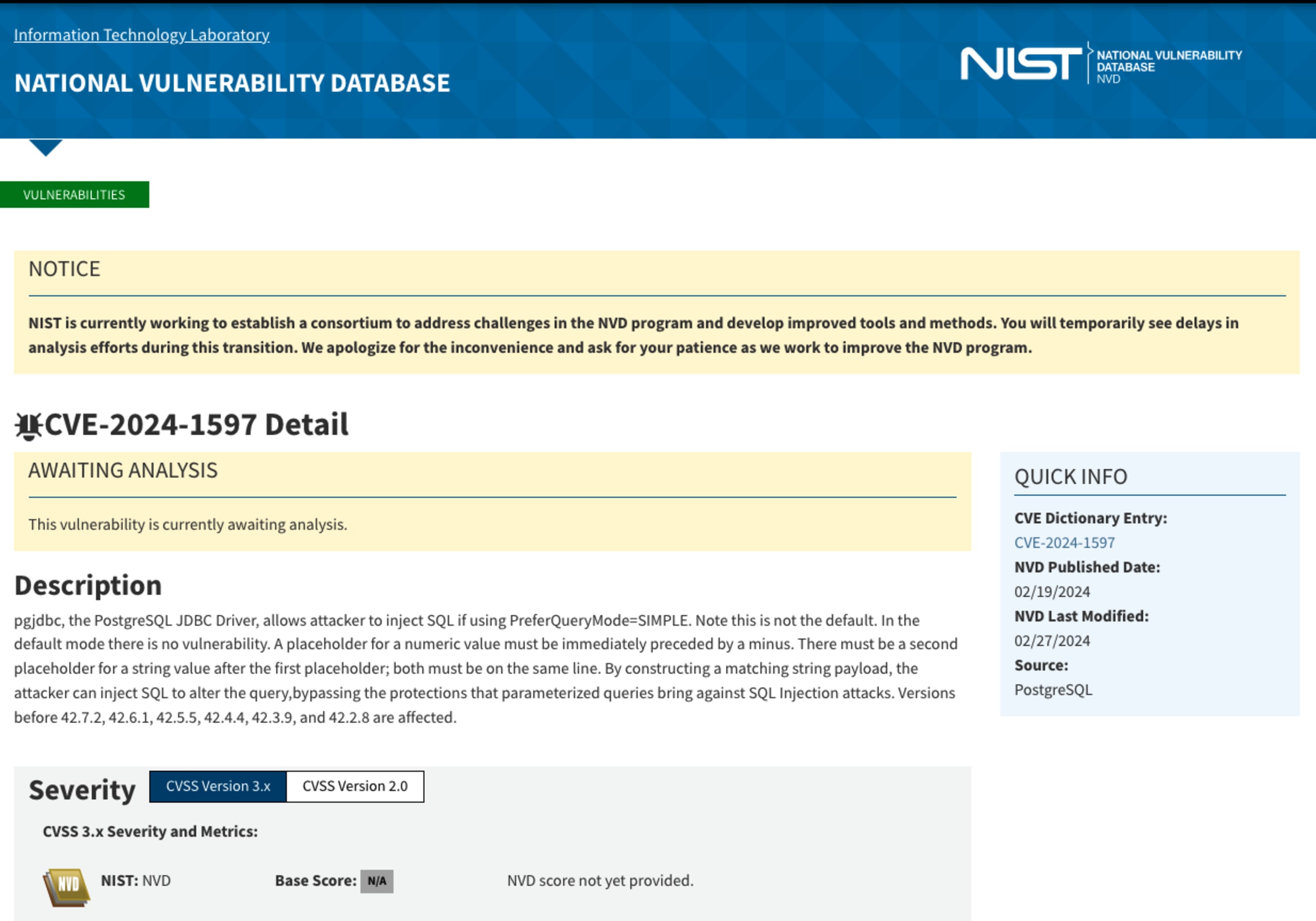
Snyk's vulnerability data goes well beyond NVD, and often comes out ahead of NVD for open source vulnerabilities, and as such, Snyk users should not be worried about delays from NVD. As of March 12, 2024, more than 500 unique CVEs published in the Snyk Vulnerability Database in 2023 and 2024 have not yet been analyzed by NVD. Some of these are high or critical severity vulnerabilities, as assessed by Snyk security analysts, for example, CVE-2024-22243 (High severity open redirect in Spring) and CVE-2024-1597 (Critical severity SQL injection in PostgreSQL), both of which were already published and analyzed 3 weeks ago in the Snyk Vulnerability Database.
Example of a critical severity advisory waiting for analysis:
Snyk’s mission is to make the world more secure — including the open source world — and help empower developers and AppSec teams to take an active role in securing their codebases. We aim to have the most timely, comprehensive, actionable, and accurate security intelligence, powering the whole of the Snyk platform, without relying solely on external sources for success. Book an expert demo today to learn more about our security intelligence.
