Rotate Azure Repos SSH keys and personal access tokens
May 6, 2019
0 mins readThis post highlights best practice #8 — rotating SSH keys and personal access tokens — from our series of 8 security best practices for Azure Repos.
Rotate Azure Repos SSH keys and personal access tokens
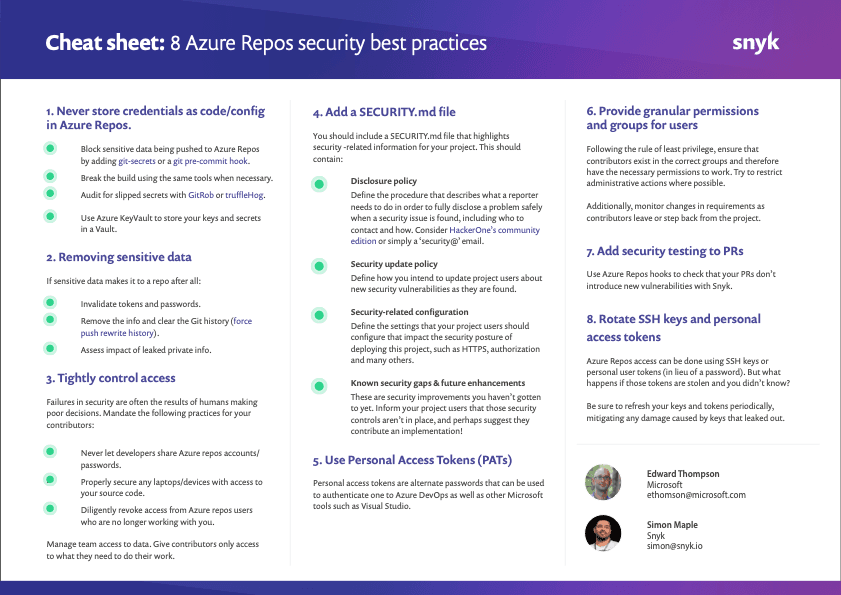
Azure Repos access is typically done using SSH keys or personal access tokens (in lieu of a password). But what happens if those tokens are stolen and you didn’t know? Be sure to refresh your keys and tokens periodically, mitigating any damage caused by keys that leaked out.
Continue reading the list of 8 Azure Repos security best practices:
If you haven’t done so yet, make sure you download this cheat sheet now and pin it up, so your future decisions are secure decisions.