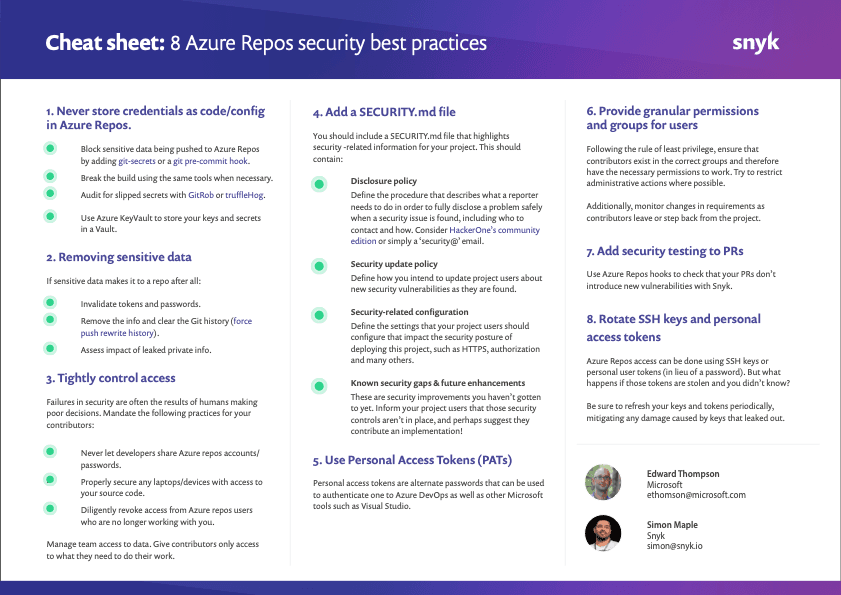
Never store credentials as code/config in Azure Repos
Edward Thompson
May 6, 2019
0 mins readThis post highlights best practice #1 — never store credentials as code — from our series of 8 security best practices for Azure Repos.
Never store credentials as code/config in Azure Repos
There are a bunch of great tools available, like git-secrets, that can statically analyze your commits, via a pre-commit Git Hook to ensure you're not trying to push any passwords or sensitive information into your Azure Repos repository. Commits are rejected if the tool matches any of the configured regular expression patterns that indicate that sensitive information has been stored improperly. This may slow down pushes a tiny bit, but it’s well worth it. Additionally, CredScan, a plugin to Azure Pipelines, can detect credentials that are being introduced into pull requests during the PR validation build process. Note, this tool is currently in preview.
Having team-wide rules that prevent credentials from being stored as code is a great way to police bad actions in the existing developer workflow. There are internal tools like Azure KeyVault that allow you to store your keys in a Vault. If you’d like to use a secure variable storage in Azure Pipelines and inject your secrets into your pipeline securely during deployment.
There are many ways to avoid putting credentials into your repository in the first place, and you should try to implement as many as you can; however there’s always the chance some sensitive information may sneak in. You should also consider regularly auditing your repos, making use of tools like GitRob or truffleHog, both of which scan through your codebase, searching for sensitive information via pattern matching.
Continue reading the list of 8 Azure Repos security best practices:
If you haven’t done so yet, make sure you download this cheat sheet now and pin it up, so your future decisions are secure decisions.