Remove sensitive data in your files and Azure Repos history
Edward Thompson
May 6, 2019
0 mins readThis post highlights best practice #2 — removing sensitive data from your files and repository — from our series of 8 security best practices for Azure Repos.
Remove sensitive data in your files and Azure Repos history
If you find sensitive data in your Azure Repos repository, you need to do a number of things to recover. First of all you'll need to invalidate the tokens and passwords that were once public. Once a secret is public on the internet, you should assume it's in the hands of attackers and react accordingly.Of course you'll also need to remove the same sensitive data from your repository, but don't forget that Azure Repos is very good at keeping a full history of all your commits. Those tokens will remain in history and in other branches. So although you should remove that data, it's still critical to invalidate those secret tokens.
Continue reading the list of 8 Azure Repos security best practices:
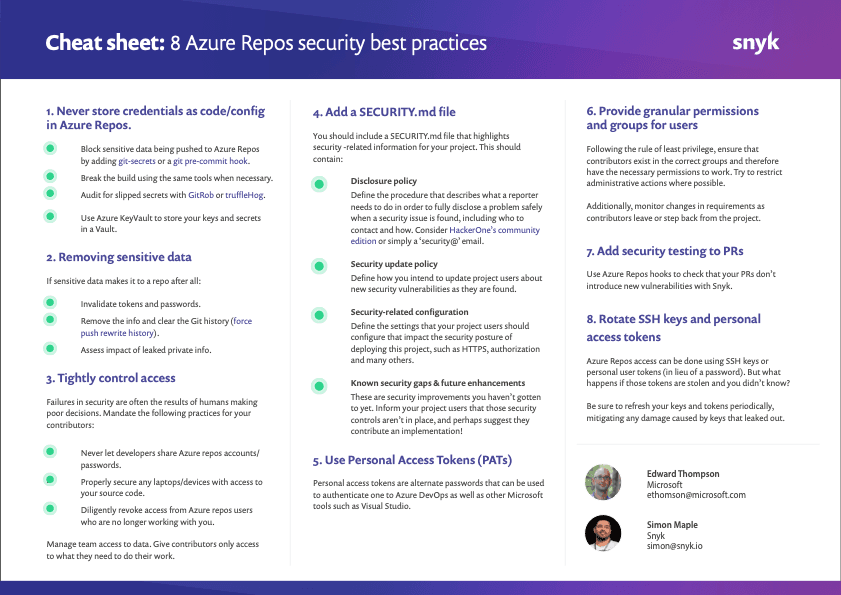
If you haven’t done so yet, make sure you download this cheat sheet now and pin it up, so your future decisions are secure decisions.