Human + AI: The Next Era of Snyk's Vulnerability Curation
July 14, 2025
0 mins readYears ago, we published the blog post, “Why do organizations trust Snyk to win the open source security battle?” which laid out the methodology and practices for building the Snyk Vulnerability Database.
Since the original post was published, the security landscape has become exponentially more complex. The impact of major events like Log4Shell, the constant influx of malicious packages, and critical infrastructure challenges such as delays in NVD data and the near-funding crisis for MITRE CVE, have all contributed to an overwhelming volume and speed of threats. Traditional methods of addressing these issues are now reaching their limits. Amidst this turmoil, one transformation stands out as essential for navigating the future: the rise of artificial intelligence.
Our unwavering mission
In Snyk's Security R&D Group, our mission has remained constant since our inception a decade ago: to curate and organize every open source vulnerability on the planet. To achieve this, we measure our success against four key pillars:
Timeliness: Delivering information about vulnerabilities and exploits promptly, giving users a crucial head start to respond before a threat is widely known or exploited
Completeness: Providing a comprehensive view of all vulnerabilities, so users can be confident that no hidden threats are lurking in their codebase
Accuracy: Ensuring the data is precise to eliminate the noise of false positives from security scans
Actionability: Presenting data in a way that allows developers to triage the vulnerabilities that affect them and prioritize their work effectively, either by mitigating the vulnerability (for example, by removing one of the vulnerable conditions) or by remediating it by updating the affected package
EBOOK
AI Code Guardrails
Gain the tools needed to implement effective guardrails to ensure your AI-generated code is both efficient and secure.
The evolution of the security analyst
Initially, our team consisted of talented security analysts who manually curated vulnerabilities in a big JSON file. Over time, we developed internal tools to automate many aspects of this process. Still, the critical decisions remained with our human experts:
Is it a real vulnerability or a quality issue?
What is the affected package?
What is the affected version range?
Is a fix available?
What is the CVSS Vector?
Is there a known exploit?
What is the CVE ID (when applicable)?
What is the most accurate CWE?
Our analysts used a variety of data sources to back up these decisions. We consistently broadened our crawlers to collect information from both structured advisories and unstructured data, such as conversations on social media or talks about software flaws, to confirm if they were security concerns that warranted responsible disclosure and a CVE assignment.
Welcome to the team, AI agents!
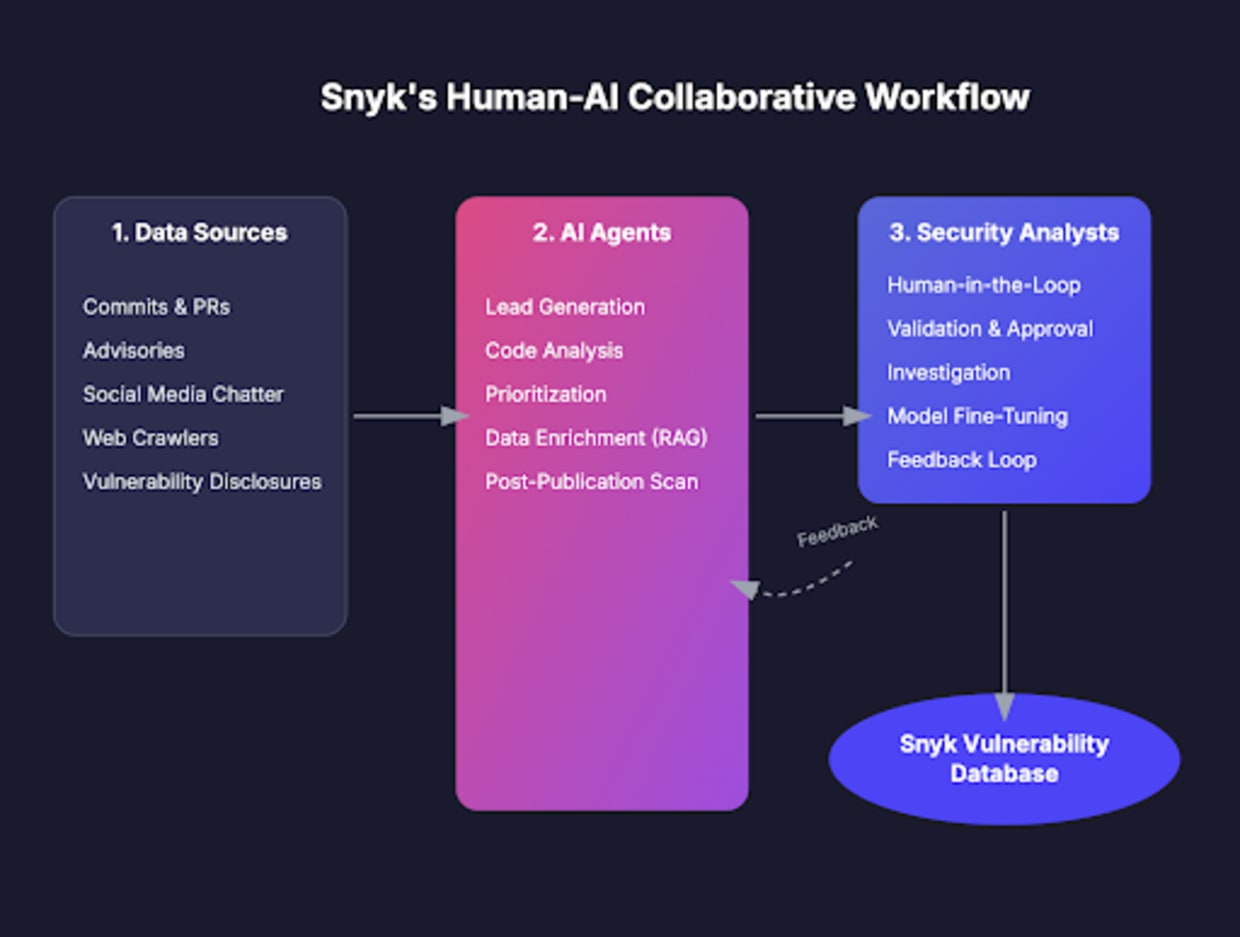
As we expand our coverage across more package registries and with new vulnerabilities being discovered every day, we are advancing our commitment to innovation by integrating AI Agents directly into our workflows.
Today, our AI Agents work alongside our human experts, taking on critical roles across the vulnerability analysis lifecycle:
Lead generation: Searching the web to find early signs and leads for new vulnerabilities
Code analysis: Monitoring commits and comparing code changes in repositories to identify potential issues using Snyk’s proprietary static analysis engine
Prioritization: Assisting analysts by prioritizing vulnerabilities, ensuring they focus not only on the most severe issues but also on those with the broadest impact
Data enrichment: Utilizing Retrieval-Augmented Generation (RAG) to learn from our existing, extensive, well-annotated, and human-verified database and suggest key vulnerability metadata to our analysts
Post-publication monitoring: Scanning for changes after a vulnerability has been published to identify fixes, backports, and new exploits in the wild
AI agent finds vulnerable code
The motivation for our work comes from real-world security findings. In past cases, seemingly routine bug fixes in popular open-source libraries have been known to introduce subtle, yet critical, security flaws. While a sharp human researcher might eventually spot such dangerous patterns (as ours routinely do), this manual discovery process isn't scalable. Learning from these incidents, we are now training an AI agent to perform this type of analysis at a massive scale. By creating this human-AI partnership, we aim to build a system that can flag suspicious commits and add vulnerabilities to our database before they are ever exploited.
The modern role of the security analyst: Human-in-the-loop
While Snyk firmly believes in the AI revolution, we are committed to implementing it responsibly. We maintain a Human-in-the-Loop (HITL) approach, where trained security analysts validate and approve AI-generated suggestions. This is especially critical for high-profile vulnerabilities, where the accuracy of an advisory is paramount. A false positive can waste precious developer time, while a false negative can put companies at significant risk.
Our analysts and AI systems operate in a powerful feedback loop, a process formally known as Reinforcement Learning from Human Feedback (RLHF). The analysts provide the critical context and oversight needed to train the AI, while the AI provides the scale and speed to augment our human expertise. This constant collaboration makes both humans and machines smarter and more effective over time.
This collaborative model has given rise to several key initiatives led by our analysts:
Eval-driven development & LLM-as-a-judge: Our analysts write evaluations (basically, unit tests) to test the various LLMs and prompts we are using, to ensure they fit our specific vulnerability analysis needs. We take this a step further by employing LLM-as-a-Judge, where we use models as an impartial referee to score and compare the outputs of our AI agents, for example, the accuracy and the hallucinations. This allows us to rapidly benchmark performance and ensure the quality of AI-generated suggestions at scale before they even reach a human analyst.
Exploring new models: In the constantly evolving world of LLMs, our analysts need to stay up-to-date with the latest LLM news, and that’s where public sources specifying Model System Cards and LMArena are becoming an important tool to learn about the latest developments, and help us to choose which to use in the various workflows.
Prompt/context engineering: While modern reasoning models require less specific prompting (no more need for ALL CAPS to get the point across, or to offer a 100$ tip to incentivize the LLM), crafting the right prompt for a specific use case still significantly impacts the results, and is a key part of our process
Model training and fine-tuning: Our team evaluates machine outputs, labels examples, and defines features to train and fine-tune specialized internal models, such as classification models that determine if a code commit contains a potential vulnerability
Building our internal MCP Server: To accelerate our research and response times, we are evolving beyond our traditional internal portal and fragmented CLI tools. We are now building a centralized MCP (Model Context Protocol) Server to act as a unified orchestration layer. This server wraps our entire suite of security tools, from code scanners to internal and external APIs and, through its deep integration with LLMs, empowers our analysts to conduct complex research using natural language. Instead of juggling multiple tools, an analyst can now issue a simple conversational command to cross-reference repository commits against our database or update a vulnerability record, allowing them to act on findings instantly.
What's next? The future of AI in security
Our journey with Agnetic AI is just beginning. We are actively exploring the next frontier of AI in security, using predictive analytics to not only identify existing vulnerabilities but also forecast which software projects are likely to develop weaknesses based on their historical vulnerabilities, development patterns, code complexity and their adoption of AI Agents, which can generate insecure code. We are also researching how AI can assist in automatically generating safe code suggestions and patches for vulnerabilities, even before an official fix is available.
Our commitment to a safer software world
The Snyk's Security R&D Group has taken a front-row seat on the AI journey, responsibly incorporating it into our workflows to continue delivering best-in-class security insights.
The future of security is not human-versus-machine; it is human-multiplied-by-machine. We're setting a new standard for security by combining the supervision of our expert analysts with the scalability and speed of AI. We are not only keeping up with the constantly evolving threat landscape, but also actively shaping it.
Own AI security with Snyk
Explore how Snyk’s helps secure your development teams’ AI-generated code while giving security teams complete visibility and controls.