Integrating actionable security in your CI/CD workflow and build systems with Snyk tests
December 13, 2019
0 mins readConnecting Snyk with the repositories you’ve stored in a source code management system such as GitHub or GitLab and then importing your projects to Snyk is a great way to leverage and benefit from security application testing throughout your core application development workflows. You immediately benefit from continuous security monitoring for any new vulnerabilities detected in your project’s library manifests, and even better, you can have Pull Requests created for you automatically to remediate those security issues.
Watch our video on how to get started with our CLI tool.
In addition to these basic Git integrations, Snyk also integrates from your CI/CD (continuous integration/continuous development) tools, based on our Snyk CLI, to run within a build or CI process such as Jenkins for example. The Snyk CLI proves to be a very flexible solution, helping developers easily start out scanning and fixing open source vulnerabilities for their applications and their containers as well. It’s no surprise that DevOps engineers are embedding this CLI tool into their pipelines more and more.
How can I provide valuable application security insight for my developers?
If you’re a DevOps or DevSecOps engineer I have no doubt you’ve probably asked yourself that at least once.
Application security testing in your CI/CD is a great step forward; but providing actionable remediation advice for developers to actually help them fix issues when a build fails is even better. This also helps reduce noise (such as breaking the build for issues that can’t be fixed, leaving developers to feel helpless).
To provide valuable advice your primary focus should be on actionability.
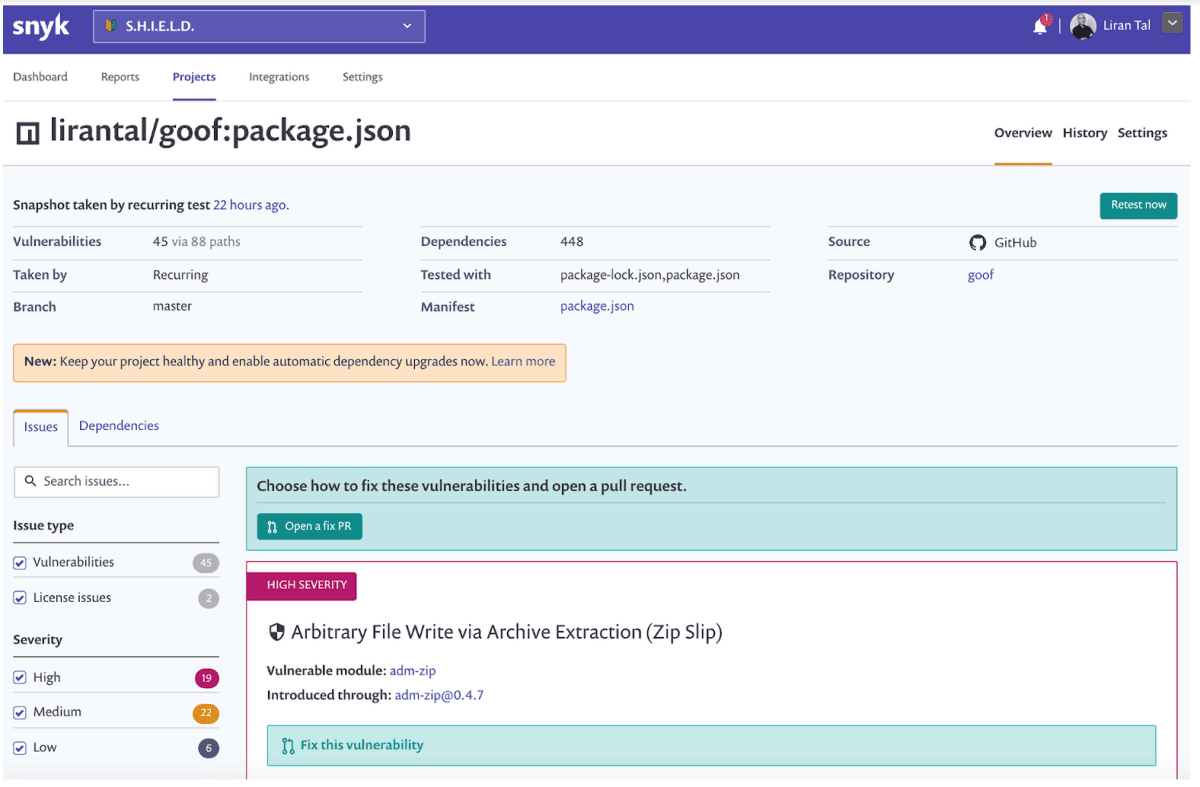
While this is easy to do when working directly from the Snyk UI and source code management integrations as is demonstrated in the image below, how do we do the same for developers working with the CLI tool?
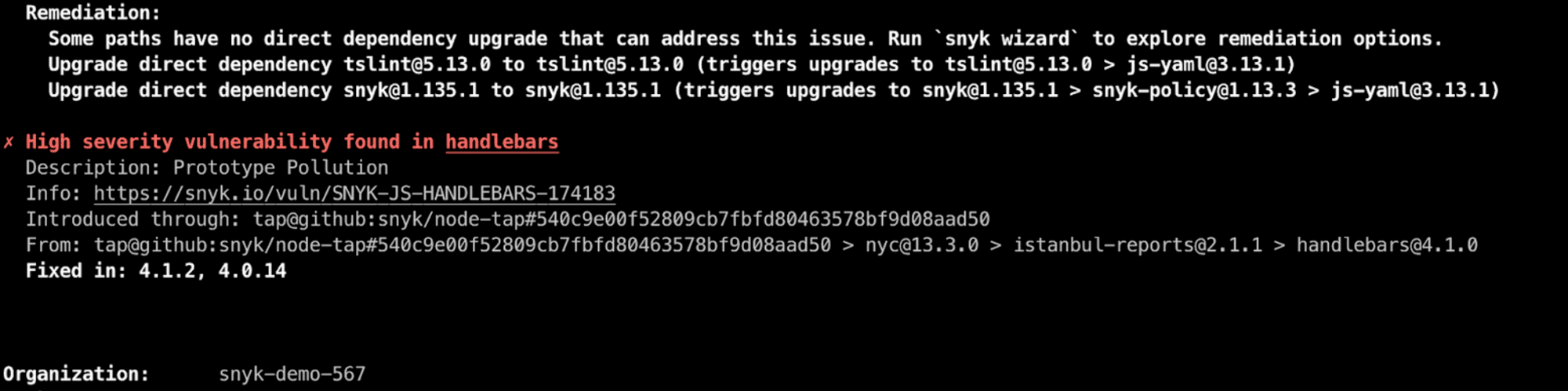
If you're running Snyk from the CLI to hunt down those security issues, you're probably used to the beautifully-displayed list of vulnerabilities, which is helpful when working with build results output, but did you know you can also get these results in JSON format as well? And, how does that help us to further increase actionability to resolve these security issues by developers?
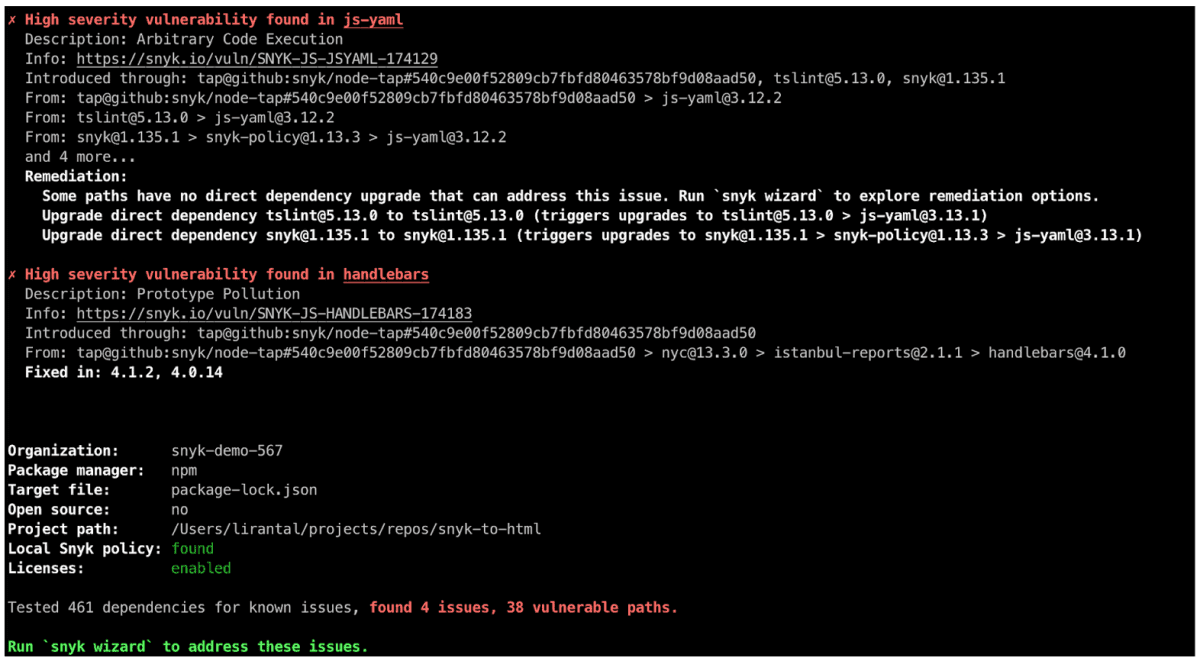
Filtering the Snyk CLI test JSON output
The Snyk CLI offers several very useful command line arguments to help get the desired information from a test, and we also offer a Snyk CLI cheat sheet as a reference.
One of those useful command line arguments is the --json option. The Snyk test JSON output, combined with the jq JSON parser command can prove highly useful for filtering and manipulating vulnerability results.
With this argument, you can easily filter results to only display issues that can be fixed by upgrading the vulnerable library or by applying a patch. That sounds pretty actionable to me!
snyk test --json | jq '.vulnerabilities |= map(select(.isUpgradable == true or .isPatchable == true))'
From machine-generated JSON output to visualization
Having a structured JSON format to manipulate is great but it would be even better if we could convert the results to a nice looking visual. We can then send the filtered version out to developers, team leads or other stakeholders to follow-up on actions and to mitigate the security vulnerabilities in our projects.
Luckily, we can make use of the snyk-to-htmlCLI. With this tool, you can export the JSON results into a static HTML webpage - packed into a single file that can be emailed or shared as you please.
First off, install the tool:
$ npm install --global snyk-to-html
Now, pipe the JSON output from the Snyk CLI test to jq for filtering, and lastly to snyk-to-html to convert the JSON into an HTML file:
$ snyk test —json | snyk-to-html -o results.html
This generates a nicely formatted, static HTML report that can then be sent out to relevant stakeholders - like this one:
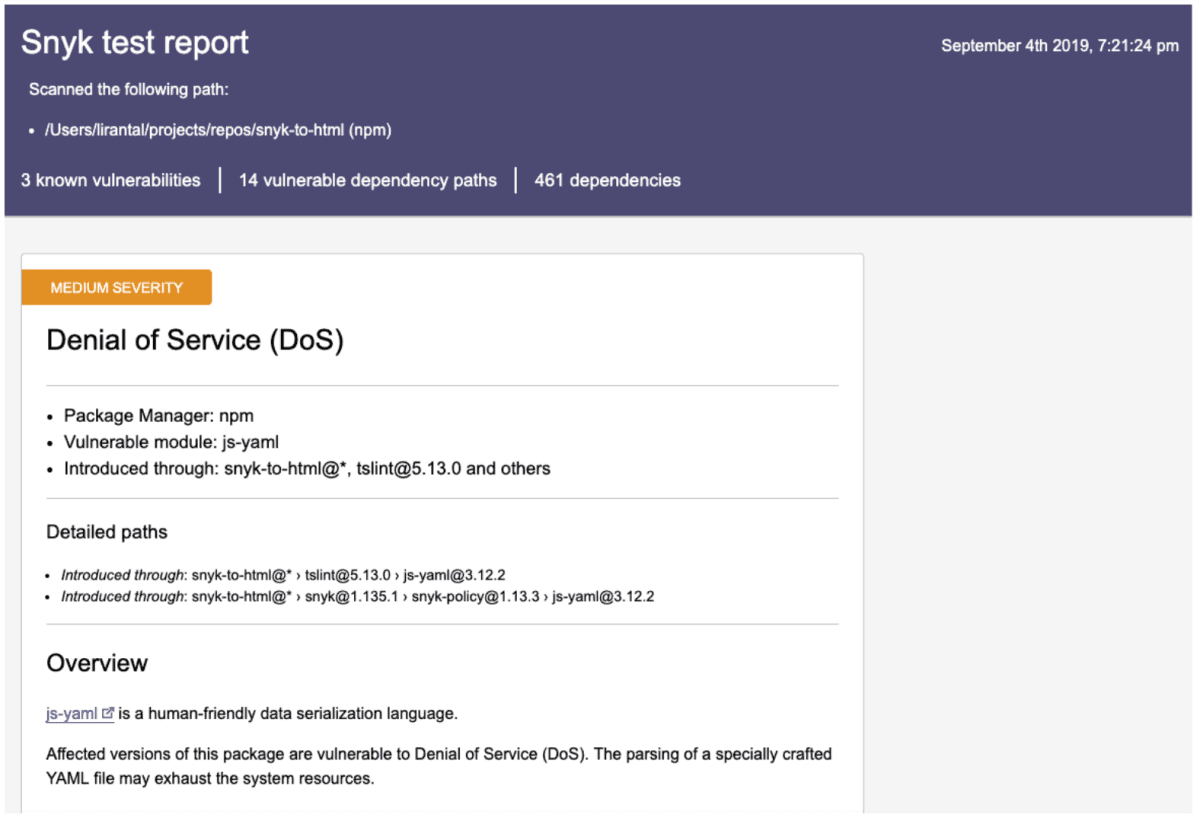
Summary
Knowing about security vulnerabilities is important but don’t forget that even more powerful is combining that with actionable advice that empowers your developers to take action and keep their applications safe.
Following are resources to further explore our Snyk CLI output:
Get started with our CLI tool by watching our quick video and check out our full CLI reference as well.
Learn even more about our command arguments with this handy Snyk CLI Cheat Sheet
For filters and other operators, refer to the jq documentation.
Lastly, you might want to read a more thorough post about getting the most out of Snyk test with JSON.
Live Hack: Exploiting AI-Generated Code
Gain insights into best practices for utilizing generative AI coding tools securely in our upcoming live hacking session.