Software Security Explained
Definitions, issues, and guidance on how to secure your code
What Is software security?
Software security is a specific concept within the overall domain of information security that deals with securing the foundational programmatic logic of the underlying software. Critically distinct from application security, software security focuses on the early stages of the software development life cycle (SDLC) and the underlying code of a given application.
It's crucial for security-minded organizations to evaluate their software security stance. Are you focusing more on application security? Are you adopting a reactive posture that mainly focuses on already deployed infrastructure, artifacts, and binaries? Can you measurably improve your overall security by bringing more resources to bear on being proactive with software security? Are you following basic cybersecurity hygiene practices? A closer look into software security, application security, and the modern SDLC will hopefully provide some clarity and a path forward.
Software security risks
Software security deals with the foundational programmatic logic. Put simply: It's about the code. Insecure, poorly engineered code can result in software security issues like buffer overflows, improperly handled exceptions, memory leaks, and unsanitized input. Left unmitigated, these bugs can turn into full-blown application vulnerabilities, which can—and often are—utilized by malicious actors to exploit and attack software infrastructure. Organizations that want to have a secure SDLC (SSDLC) should ensure they're enabling engineering teams to get it right when it comes to the crucially important early stages of software development. Modern software is complex; consequently, so is any effort to secure it. The supply chain of dependencies for even basic applications can rapidly become a convoluted mosaic of third-party libraries and modules, all with their own bugs and potential vulnerabilities lurking beneath the surface.
What are software security requirements?
Software security requirements are the stated security goals of a particular system or application. A clear list of well-thought-out security requirements is incredibly important in the buildout of a modern software application. Good requirements are clear, can be tested, and are achievable.
What is hardware and software security?
Software security deals with the security of the code of an application. Hardware security, naturally, deals with security of the hardware. Hardware security can mean actual physical security, such as access control and intrusion prevention. It can also imply lower level concerns, related to the security of firmware and ROM.
Software security processes and tools
Having the proper tools and processes to identify and remediate software bugs is key. Even more important is for organizations to ensure that their software engineers have ownership and agency in dealing with bugs. The DevOps principle of the fast-feedback loop plays an important role: Immediate and actionable feedback means a lower overall incidence of bugs and vulnerabilities, particularly in the later stages of the development life cycle.
Conversely, organizations whose development and security teams operate in silos, with long remediation and reporting cycles, will inevitably find their software plagued by bugs and vulnerabilities, making the difficult task of application security exponentially harder.
Software and application security
Once the underlying software has reached the stage where it becomes a deployable artifact, such as a JAR or container image, it has entered the realm of application security. At these stages of the SDLC, the focus becomes more holistic: It's not just the software, but a variety of interconnected systems, infrastructure, and network paths. Most commonly, operationally focused staff, such as DevOps engineers, take a more active role in securing the application.
However, it should be clear that investment in the earlier stages of the SDLC, in software security, pays dividends for application security efforts. It's much easier to secure an application with fewer defects and vulnerabilities than one with several. Vulnerable applications put operations teams and security engineers on their heels, and often require costly infrastructure and security workarounds to mitigate.
Is it more cost-effective to buy a new firewall, capable of blocking traffic aimed at a specific vulnerability, or simply ensure the bug that causes the vulnerability never leaves the early stages of development? Newer paradigms, like DevSecOps, can help faster iteration and mitigation of vulnerabilities by tightening the feedback loop between operations and software engineers, but the ultimate goal should still be to prevent the vulnerabilities in the first place.
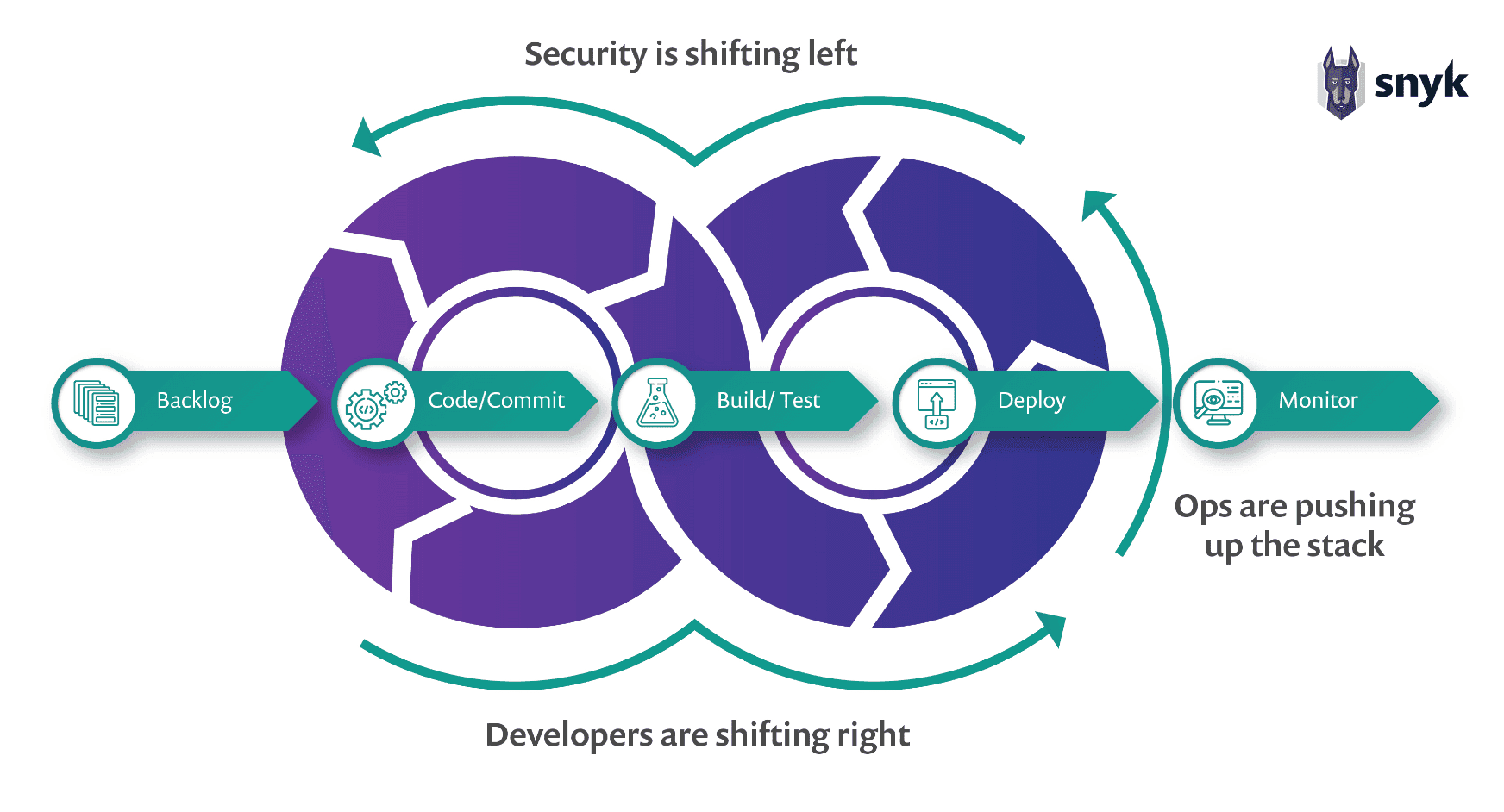
What does a secure SDLC look like?
Software security should always be a top priority for any organization, as it reduces the need for excess investment in application security bandaids. However, by no means should application security fall by the wayside. To provide a truly secure SDLC, organizations need to have a strong investment in both software security and application security.
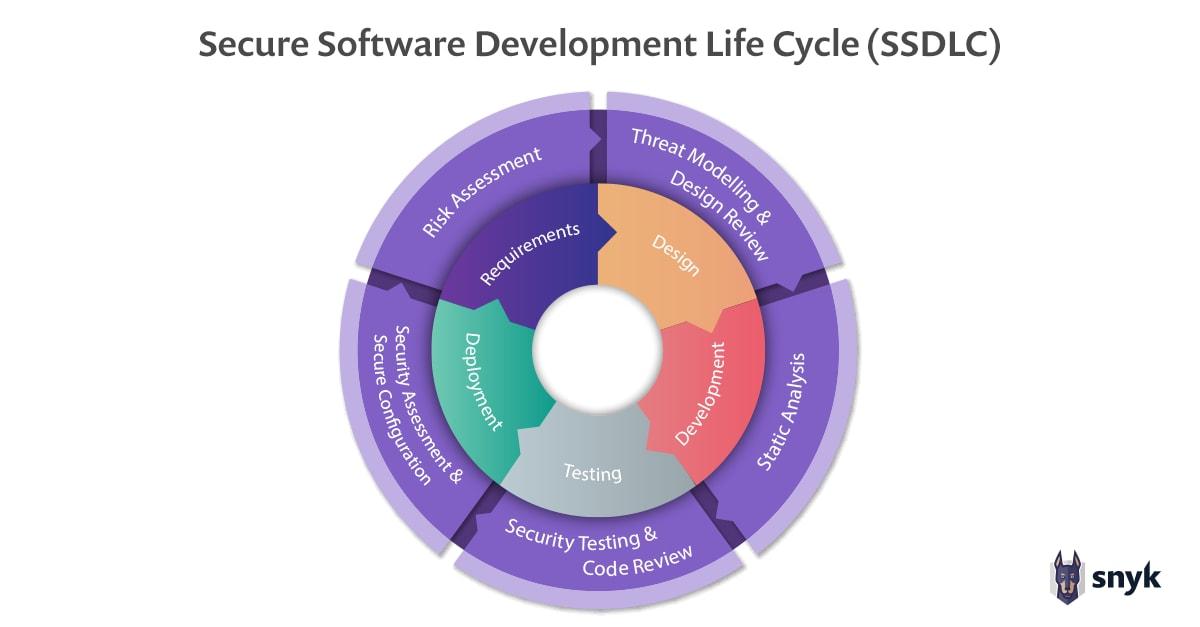
Breaking it down, this can be thought of as "stages": proactive/early, middle, and late.
Proactive/early security phase
In the early stages of software design and development, the first few sketches and customer requirements start to become functioning logic and features. Engineering teams should work closely with security/DevSecOps engineers to develop a detailed inventory of their software supply chain. Subscribe to news, analysis, and CVE feeds for the critical dependencies and modules.
As features are added and more code is written, a fast feedback loop is essential. Integrating application security testing with tools that can perform static analysis will enable the ever-critical identification of bugs and vulnerabilities prior to deployment.
Middle security phase
Now the code has likely become a deployable artifact. Operations teams are starting to get more involved in supporting and running the infrastructure. Having security tools and testing integrated into the CI/CD pipeline will help maintain a solid feedback loop from application security to software security.
Late security phase
At these stages of the SDLC, the application is likely being deployed into some form of the production environment. It is absolutely critical for organizations to have a robust monitoring and alerting infrastructure. A large percentage of organizations run container-based workloads, either standalone or using an orchestration platform like Kubernetes. Container security and Kubernetes security have therefore become more of a niche focus.
It should be emphasized that these stages are not exclusive, or isolated. For example, container security is an actionable goal at the very early stages of the SDLC owing to static container and image analysis tools. Static analysis testing is ongoing, and each new feature software engineers write should bear the scrutiny of the same rigorous testing methodologies that were applied at the beginning of the design.
Software security Is proactive security
Organizations that take steps to address security issues earlier in the SDLC, by focusing on core software security, have applications that are not only more secure, but cost less to keep secure once the application launches to production.
However, perfect software security is an anti-goal. Understanding that there will always be new and highly sophisticated attacks means understanding that application security is augmented, not replaced by software security.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
Improved software security with Snyk Cybersecurity Platform
Snyk's developer-first software security capabilities were designed to help you organize, govern, and prioritize projects more easily, and ultimately – manage the security vulnerabilities and license issues they introduce more efficiently.
Snyk Open Source: Enabling developers to easily find and automatically fix open source vulnerabilities. Get started with Snyk Open Source.Snyk Open Source also includes Snyk license compliance to help manage your open source license usage. Get started with Snyk License Compliance.
Snyk Code: Find and fix vulnerabilities in your application code in real time during the development process. Get started with Snyk Code.
Snyk Container: Find and fix vulnerabilities in container images and Kubernetes applications. Get started with Snyk Container.
Snyk Infrastructure as Code (IaC): Find and fix insecure configurations in Terraform and Kubernetes code. Get started with Snyk IaC.
Snyk Intel Vulnerability Database: Comprehensive and actionable open source and container vulnerability data.