Application Security Testing (AST) - Top Questions Answered
Different types of application security testing, and software security testing tools.
The rapid rate at which developers build and release software requires a continuous cycle of testing during every stage of the development life cycle. Application security testing has thus become a vital step in the software build and release cycle. According to a 2020 Verizon report, 43% of data breaches were attacks on web applications. Building safe and secure applications requires testing applications regularly and patching known vulnerabilities as they arise. Application security solutions such as Snyk can help developers and security teams keep up with the speed of development, whilst staying secure.
What is application security testing?
Application security testing is a process that involves a set of tools and practices that help developers manage and fix all vulnerabilities in their codebase. Due to the complexity of today’s applications, developers require a variety of vulnerability detection tools that rely on different testing methodologies. Some of these tools scan the codebase to detect common problems, while others do dynamic testing with already running deployments.
Open-source components help speed up the development cycle, but can also lead to unsecured code if the security team doesn’t audit all code snippets. To help teams maintain a secure codebase, different types of application security testing are required throughout the many stages of the secure development life cycle. You should also consider specific web application security testing if your app will be available online.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
Types of Application Security Testing Tools
In each stage of the application life cycle, security teams can take advantage of specific tools to secure their application:
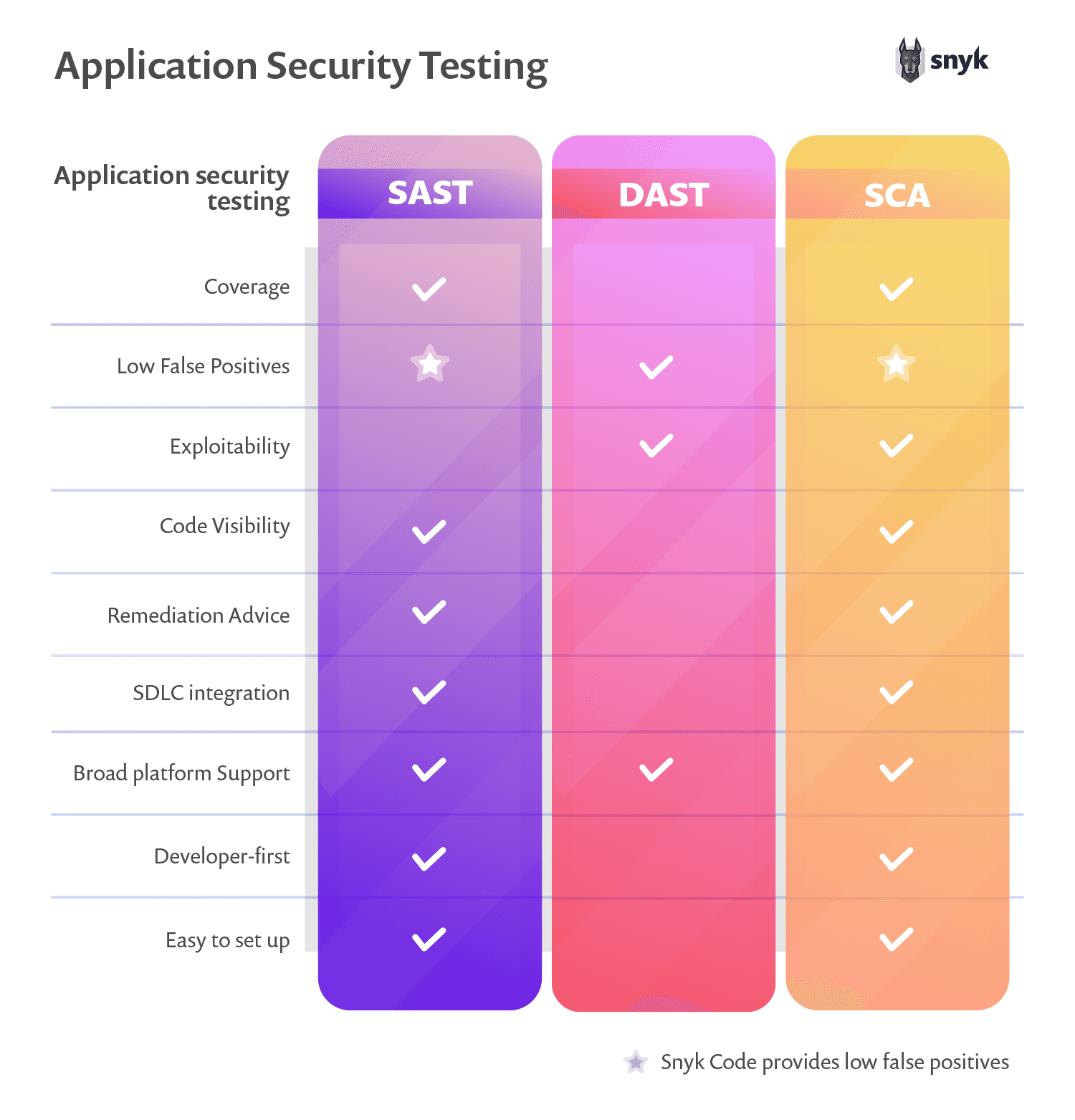
Static application security testing (SAST): Checks for vulnerabilities in the application source code (at rest), providing a real-time snapshot of the application’s security.
Dynamic application security testing (DAST): Verifies security during run time by testing different attack types against the running application. DAST does not require access to the application’s source code.
Application penetration testing: Penetration tester security professionals test the application against the latest cyberattacks where vulnerabilities may arise as a result of a user’s actions. Penetration testing tools can be used or the testing can be outsourced to a third-party organization.
Interactive application security testing (IAST): Searches for known vulnerabilities inside the application’s functions by simulating the various scenarios in which a user runs or interacts with the app.
Mobile application security testing (MAST): Combines other types of application security testing with mobile-specific attack vectors (e.g., malicious Wi-Fi hotspots or jail-broken mobile devices).
Software composition analysis (SCA): Analyzes the libraries in an application for their origin. Popular open-source software libraries often have public bug lists, which makes this technique very effective.
Database security scanning: Checks the used database for best practices, such as strong passwords and whether the latest security patches are installed.
Which Application Security Testing Tools should you use?
A variety of application security testing tools exist to assist teams with securing their software. Deciding which tool is right for you of course depends on the type of tests that need to be conducted. There are a number of good open-source SAST tools available, such as LGTM and Snyk CLI. If DAST is the preferred method, OWASP ZAP and the Arachni scanner are excellent choices. Arachni also offers commercial support. For IAST, most of the available tools are vendor-specific, but Contrast Community Edition (CE) is a fully featured, free IAST tool for Java and .NET applications.
Snyk offers a set of solid application security solutions, including an open source vulnerability scanner, that helps to automatically find, prioritize and fix vulnerabilities in the open source dependencies throughout your development process.
Depending on the development environment used for the build and release cycles, application security analysis tools can identify vulnerabilities early and ensure teams apply patches or replace components before releasing software into production.
Application security testing process
Depending on the type of application security testing that is needed, the application security testing process can differ greatly. SAST targets the code-base and as such, is best integrated into a CI/CD pipeline. DAST targets running systems; while it can be automated, a running deployment that resembles the production environment has to be provided. IAST differs from DAST in that it runs inside the system you want to test. Therefore, it has to be integrated into the code-base prior to deployment.
Teams need to ensure they test for new vulnerabilities, SQL injection, URL manipulation, spoofing, malicious code and cross-site Scripting (XSS). Testers must have experience with the HTTP protocols to prevent URL manipulation through the use of HTTP GET methods. If the application passes any important information with the string, it’s not secure.
To prevent XSS, testers should ensure the application rejects all external HTML and script requests. Testers must configure the operating system on the server running the application in accordance with security best practices. It’s also crucial to secure any other services running on the server, as every entry point is a potential attack vector. Private customer data must also be protected according to data protection laws.
It’s critical that developers review every aspect of their application security during each commit. The right tools can help teams automate the bulk of their testing during the development cycle. Failure to secure your applications prior to their release risks a breach with serious consequences, such as crashing the server or exposing user records.
Software security testing best practices
Continuous testing in every stage of the development life cycle is crucial, but these additional tips can help developers secure their applications at all times.
Identify business-critical systems: Frequent testing is essential for all your business-critical systems and may even be required by regulations.
Test all components early: The earlier your team starts the testing process, the less likely you are to encounter critical security issues and vulnerabilities in the future, and the more secure the application will be.
Prioritize remediation and fixes: Knowing about a vulnerability isn’t enough; teams need to work to fix them as soon as they arise.
Check out our application security checklist for more best practices.
Application security testing with Snyk
Snyk enables application security testing throughout every stage of the development lifecycle and integrates with your existing tools with our application security solution. Package vulnerabilities that remain unaddressed can lead to major breaches and compromised service.
Secure your applications with our developer first tool
Efficient and actionable application security advice across IDEs, repos, containers, and pipelines.
Check out our code checker tool to get a quick sense of your code's security and get started with building secure apps with Snyk.