Sequelize ORM npm library found vulnerable to SQL Injection attacks
September 11, 2019
0 mins readObject-Relational Mappers, also commonly referred to as ORMs, are a set of SQL libraries that help developers manage their database code by abstracting it into language constructs.
SQL ORM libraries have been found to be great for SQL Injection prevention, but unfortunately they themselves may have security bugs that open the door for application-level SQL injection attacks.
Why should I care about SQL Injection attacks?
A major benefit for using ORMs is that they make use of prepared statements, which is a technique to escape input in order to prevent SQL injection vulnerabilities. With that said, injection attacks are on the top list per the OWASP Top 10 and a State of The Internet report by Akamai found that SQL injection vulnerabilities now represent nearly two-thirds of all web application attacks (65.1%).
We’ve written about SQL Injection and ORMs in more detail in the past. In this post, I want to focus on the recent SQL injection example that the Snyk team discovered in the popular npm library sequelize.
Snyk discovers SQL injection in the npm Sequelize ORM library
In June 2019, Snyk discovered attack vectors that could lead to SQL injection attacks for applications that use Sequelize, a popular npm library for Node.js applications. In total, we found three SQL injection vulnerabilities affecting Sequelize identified as CVEs CVE-2019-10752 CVE-2019-10749, CVE-2019-10748.
Soon after confirming the issue we engaged with maintainers of sequelize Jan Aagaard Meier and Sushant Dhiman, to responsibly disclose our findings and provide an SQL injection example that demonstrates the security vulnerability and the vulnerable code paths that lead to it.
As a testament for Sequelize’s commitment to security and protecting their users as fast as possible, they promptly responded and released fixes in the 3.x and 5.x branches of the library, remediating the vulnerability and providing users with an upgrade path for SQL injection prevention.
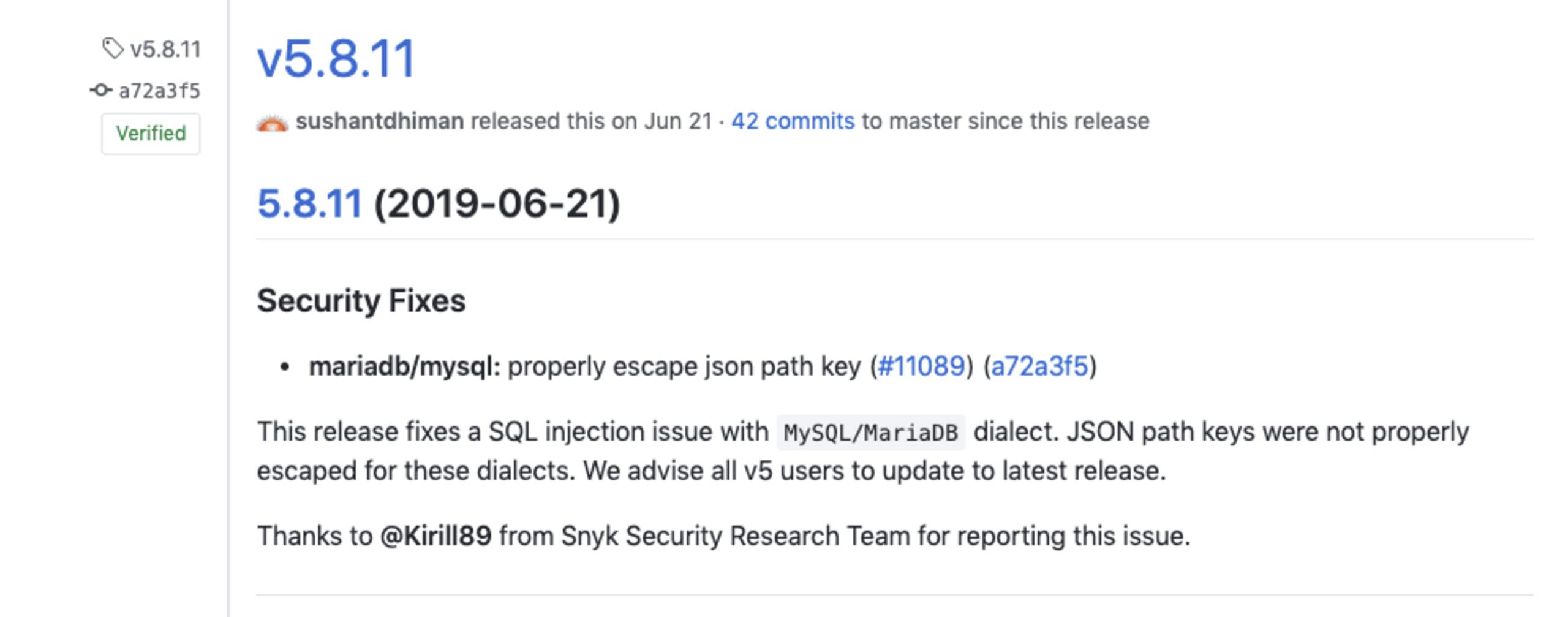
The Sequelize project released fixes in version 3.35.1 which addresses the security vulnerabilities affecting PostgreSQL as well as in 5.8.11 which fixed security vulnerabilities in MySQL and MariaDB dialects. We strongly recommend you to upgrade as soon as possibleto ensure you are using secure versions of sequelize.
The most recent SQL injection vulnerability of the three mentioned was fixed in Sequelize version 5.15.1 and includes an example as shown below in the official release notes:
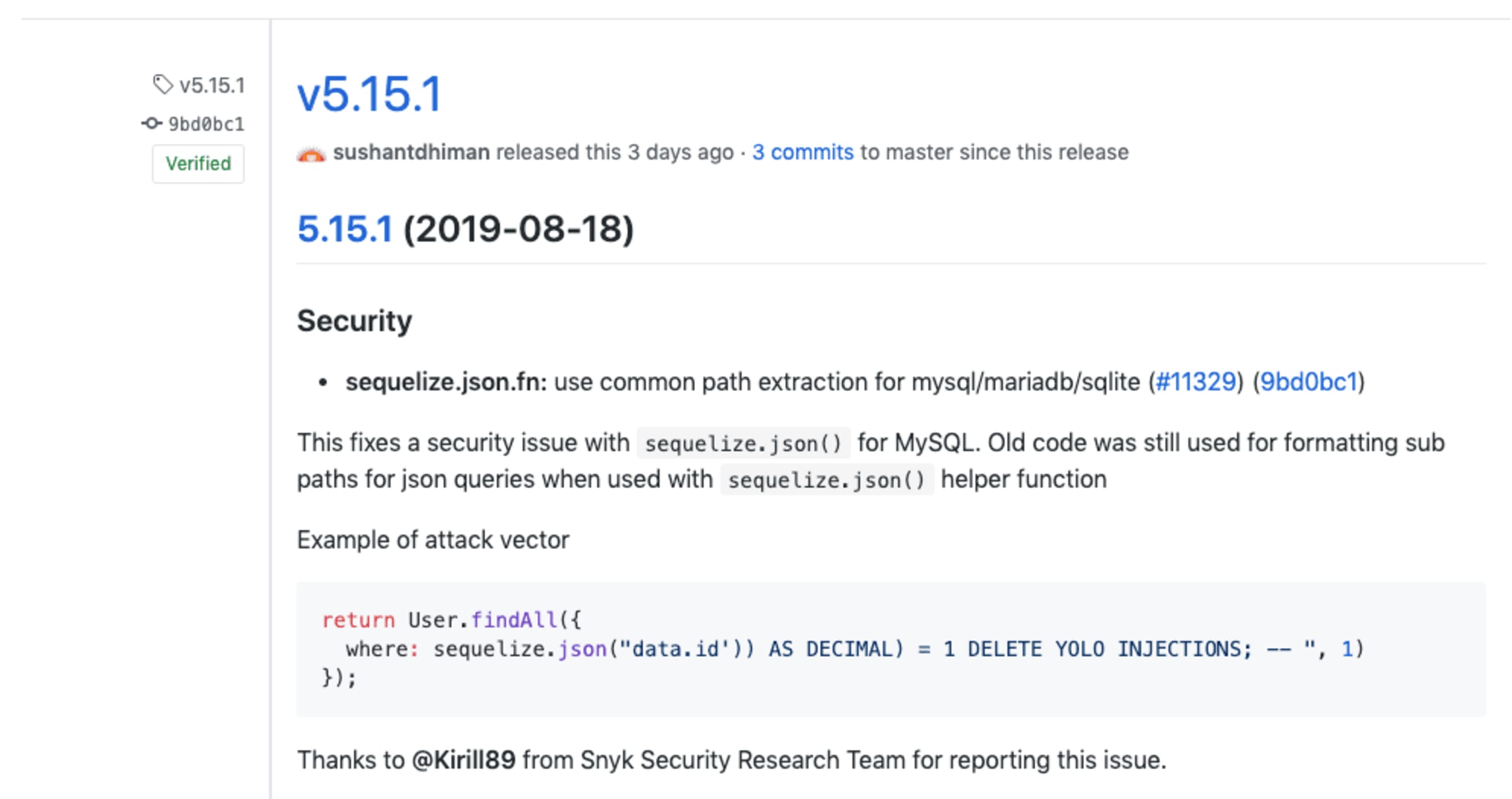
An SQL injection example for MySQL and MariaDB
All versions of sequelize lower than 5.8.11 are vulnerable to SQL Injection (CVE-2019-10748) because they contain JSON path keys that are not being properly escaped for the MySQL and MariaDB dialects.
Consider the following SQL injection example with sequelize:
The metadatabase field expects a JSON object, while the key provided for it isn’t properly sanitized to escape single quotes. If the single quote is passed with the )) AS DECIMAL) text which the query expects, then the code can be exploited.
The SQL injection example here shows how it is possible to further run SQL queries such as a UNION, or to completely terminate a query with a semicolon and add a postfix such as ; DROP TABLE USERS.
A similar SQL injection vulnerability affects all versions of sequelize lower than 3.35.1 for the PostgreSQL dialect.
Am I affected and what should I do?
If your project is being monitored by Snyk and we find vulnerable versions of sequelize you will be notified via Snyk’s routine alerts; on top of that if you connected your GitHub repository we automatically create a Pull Request for you to upgrade sequelize to its fixed version.
The Snyk security research team is constantly involved in work to uncover security vulnerabilities in many language ecosystems, some examples are the recent lodash npm library security vulnerability, as well as extensive research that yielded the Zip Slip vulnerability across many language ecosystems and affecting thousands of applications.
If your projects are not monitored by Snyk and you’d like to test them for the use of this package you can do so below, or by using our CLI to test your projects locally.
We also recommend that you practice secure coding conventions and follow best practices such as the one by OWASP for SQL Injection cheat sheet.
Think you found a vulnerability in Sequelize?We at Snyk value the security community and believe that a responsible disclosure of security vulnerabilities in open source packages helps us ensure the security and privacy of the users. If you think you found a vulnerability in Sequelize, you can submit to Snyk Open Source Package Vulnerability Disclosure program and we will take care of the rest!https://snyk.io/vulnerability-disclosure/
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
