Snyk Open Source adds beta C/C++ security scanning for unmanaged OSS
Daniel Berman
December 8, 2021
0 mins readWe’re happy to announce the open beta of C/C++ security scanning in Snyk Open Source, enabling development and security teams to find and fix known security vulnerabilities in their C/C++ open source code and libraries!
Used across various industry verticals and prominent within the gaming, hardware/IoT, and communications industries, C/C++ continues to have a major impact on software development and the technology space as a whole. According to the November 2021 TIOBE index, C/C++ ranks among the top 5 programming languages at second and fourthpositions, respectively. Similar findings appear in the PYPL index and RedMonk rankings.
Just as with any other programming language, C/C++ developers rely on open source code and libraries to build their applications. This growing reliance introduces risk in the shape and form of known security vulnerabilities hiding within these libraries. This risk is exacerbated by the fact that, unlike more modern languages, the majority of C/C++ developers do not use a standardized process for managing these libraries (49% of C++ developers cite package management as a key pain point in the latest C++ community survey). Instead, the source code for the open source library is bundled together with the application code, making it more challenging to manage these libraries and identify vulnerabilities they might include.
With this announcement, Snyk Open Source users can mitigate this risk by testing their C/C++ projects from within the Snyk CLI, enabling manual testing in local development environments, or automated testing, as part of a CI/CD pipeline.
The following capabilities are supported in this beta version:
snyk unmanaged testin Snyk CLIsnyk unmanaged monitorin Snyk CLIVulnerability data based on National Vulnerability Database (NVD)
Let’s take a quick look at how this works.
Setting up the Snyk CLI
First thing first, make sure you’ve got the Snyk CLI installed. If you’re already familiar with the Snyk CLI and have it installed, make sure you are using version 1.775.0 and above.
Setting up the Snyk CLI is simple. You can use npm or Homebrew to quickly install it and then all that’s required is to authenticate with your Snyk account (if you haven’t already, sign up for free):
Your browser will open up with a request to authenticate the CLI. Go ahead and authenticate!
You’re now ready to start working with the Snyk CLI to scan your C/C++ projects for vulnerabilities.
Scanning for security vulnerabilities
Let’s give the Snyk CLI a first try and run a test.
To scan a project, the open source libraries need to be located within the directory being scanned. Within that directory, run the following CLI command:
Snyk now converts all the files in the folder into a list of digital signatures, or hashes, which is then correlated with Snyk’s databases to form a list of matching open source components. This list of components is then correlated with the National Vulnerability Database (NVD) to display results.
The vulnerability scanning process depends on the number of files in your project and can take between a few seconds to a few minutes. As soon as the scanning is completed, you will be presented with a list of vulnerabilities identified:
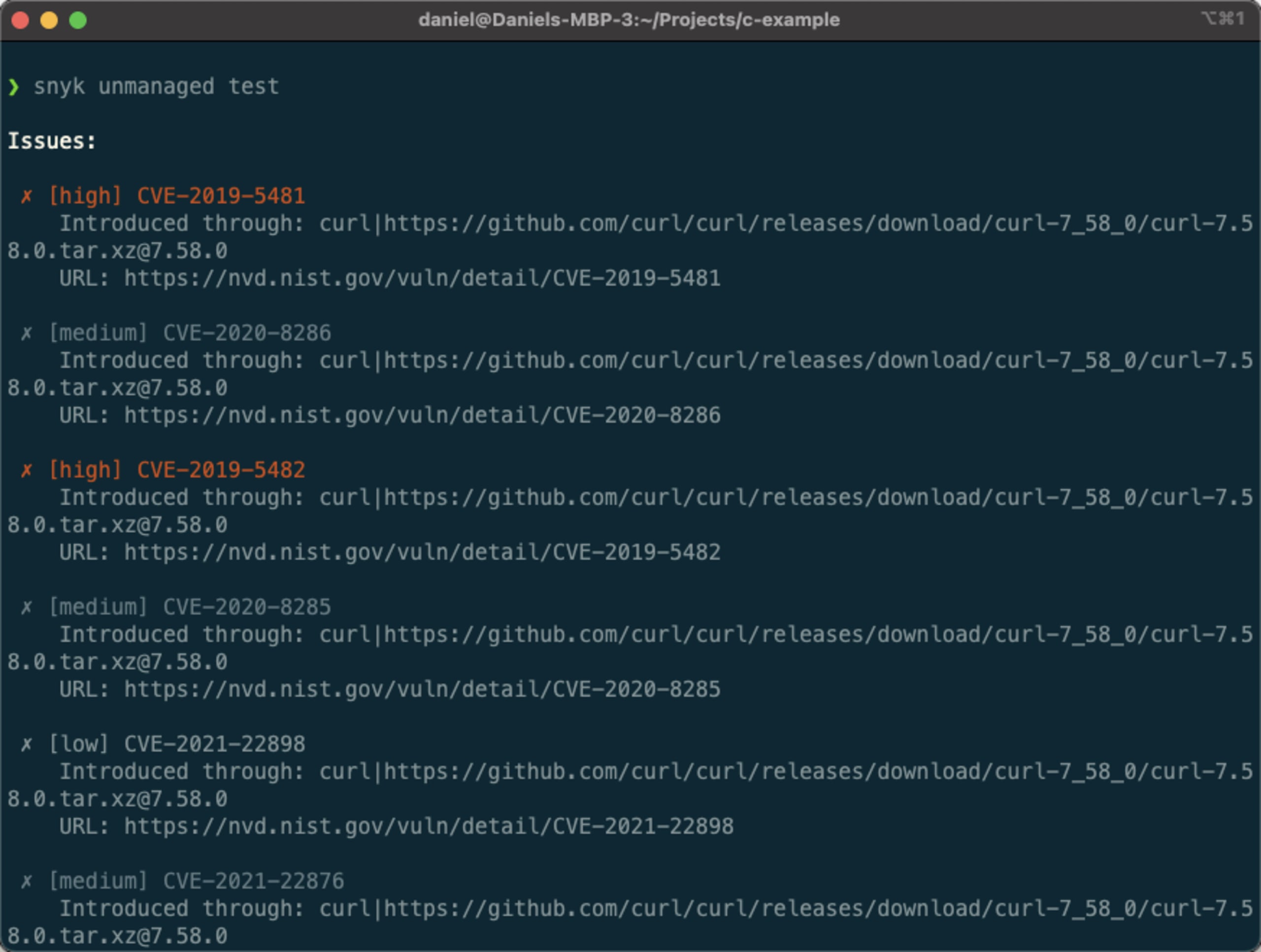
As seen in the example above, the list of issues contains the severity of the vulnerability, its CVE, information about the library introducing the vulnerability, and a link to the vulnerability itself within NVD.
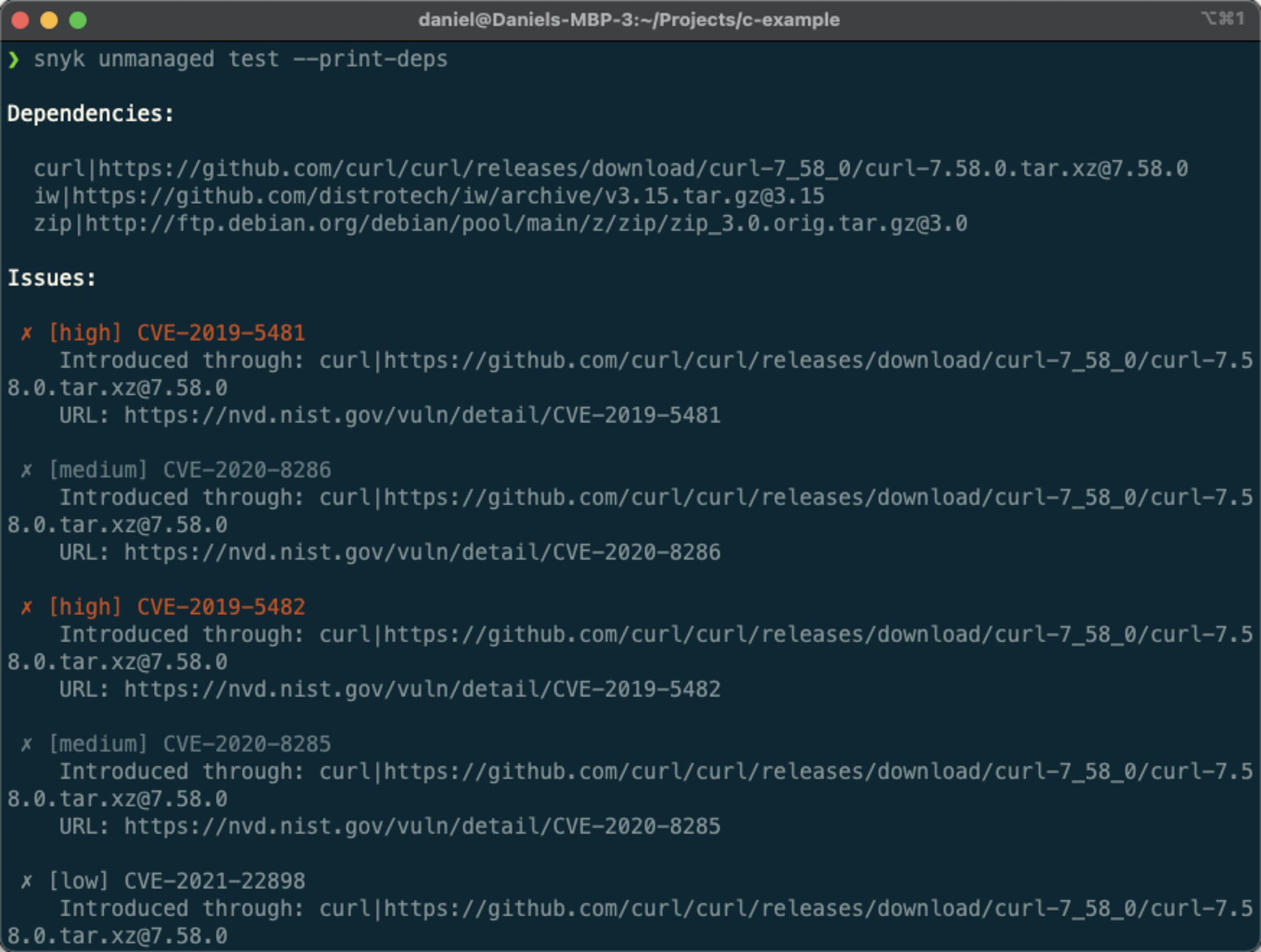
Another useful command displays the open source libraries included in the project, vulnerable or not:
The Snyk CLI will now provide a dependency list before the list of vulnerabilities. As seen in the example here, this specific project includes the curl, iw, and zip libraries.
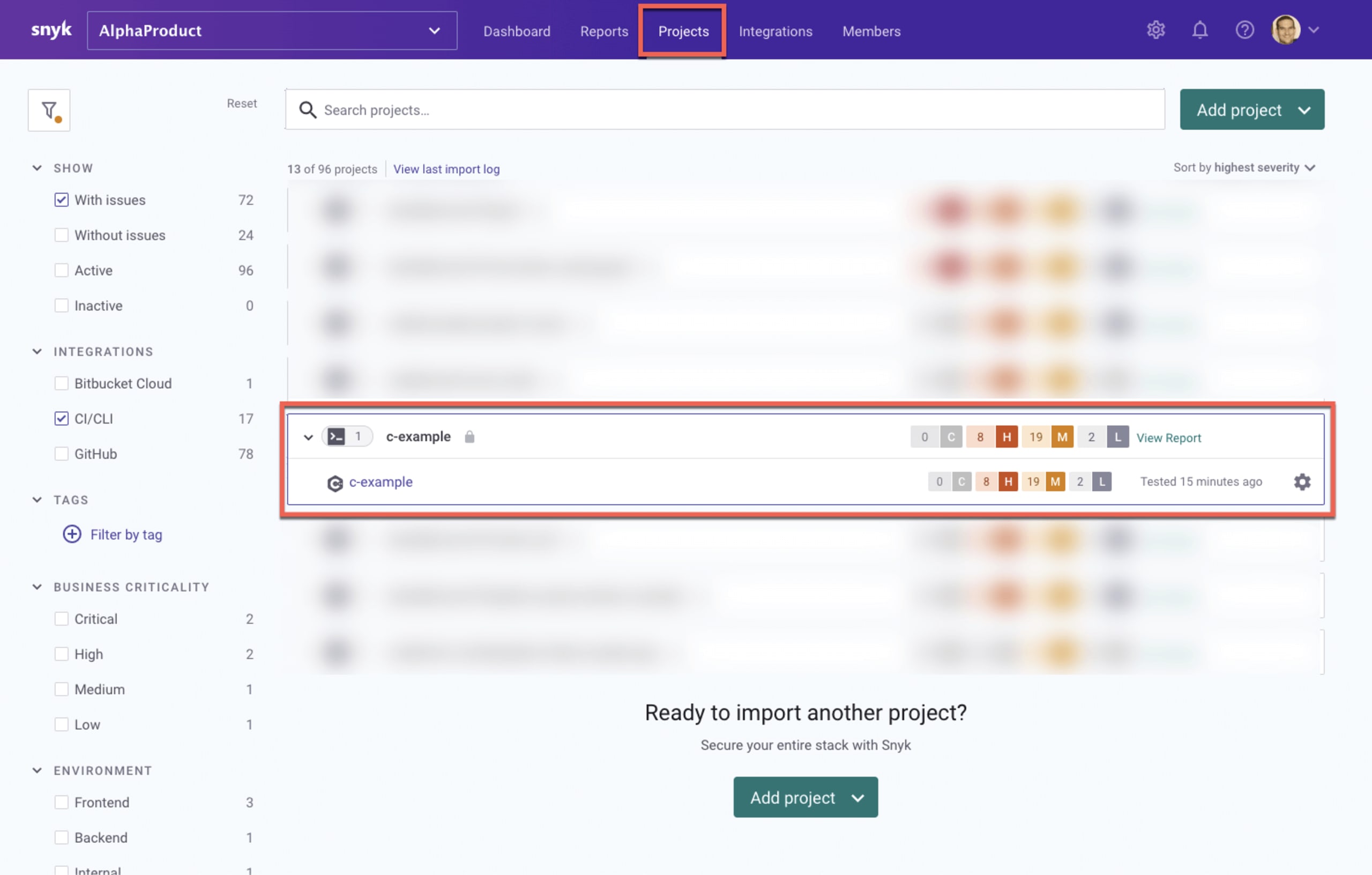
You can also import scan results into the Snyk application for better visibility and reporting. To do this, use the following command:
A snapshot of your C/C++ libraries is taken, together with the vulnerabilities they include, which is then imported into Snyk for further review and analysis. It will appear as a new project on the Projects page:
There are plenty of other ways of interacting with scan results, including filtering results and outputting them into JSON format. Please refer to our Snyk documentation for more CLI options!
Venturing into the world of unmanaged open source
C/C++ development teams trying to maintain a fast pace of development while also staying secure are faced with codebases that contain large amounts of legacy code. Most of the open source code in these codebases is undeclared, consumed directly by embedding code into the application which makes it extremely difficult to manage the risk being introduced.
This beta announcement is Snyk’s first step towards helping these teams overcome this challenge by fully extending our developer-first software composition analysis capabilities to secure unmanaged open source. Our next steps will include the full integration of C/C++ support in Snyk Open Source with the Snyk Intel vulnerability database, and further down the road, added support for unmanaged open source in additional ecosystems such as JavaScript and Java.
As we start implementing these next steps, we are counting on your feedback to ensure we are headed in the right direction. We want to verify that we are developing the right functionality and in the right order.
So please be our guest! These capabilities are available, in beta, across all of Snyk's paid plans: Team, Business, and Enterprise. To join the beta, please reach out to our team at ccpp-beta@snyk.io so we can verify your specific use case is supported.
For more information on how to scan your C/C++ projects and beta support, please visit our Snyk documentation.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
