Snyk IaC scanning enhancements include Azure and AWS infrastructure as code
February 23, 2021
0 mins readRecently I wrote about Infrastructure as Code (IaC) and how Snyk’s IaC scanning can help catch issues in your templates before they make it to provisioning. Our engineering team continues to expand the breadth of our IaC scanning policies to better protect your platforms from vulnerabilities and issues.
In this post, we’ll review the IaC scanning tool, take a look at recent additions that have been made to it—including Azure, GCP, and AWS infrastructure as code—and how your teams can use it as an active part of your company’s DevSecOps efforts.
Why should I scan IaC?
IaC templates contain the declarative state you want your applications to run as in various deployment environments. I like to think of them—along with other artifacts like Dockerfiles—as automated run-books that capture all of the tribal knowledge and ceremony associated with manual deployments and distill it into standardized, repeatable steps that can be reviewed and tested before they are run. It also allows you to apply software development principles like code reviews and approvals to your infrastructure code. Snyk’s scanning tools provide an automated review that compares your existing IaC templates against our curated set of policies and best-practices resulting in a report showing any issues found along with detailed descriptions and remediation advice.
Most of the concerns with IaC aren't “vulnerabilities”, at least not in the classic sense of the word. Generally, IaC users don't worry about a zero-day vulnerability suddenly inflicting their IaC definitions but instead they focus more on compliance with policies and standards set by security and architecture teams. What that means in practice is that we generally want to test as changes are made to the code, which fits well with the pattern of running tests in pipelines when there is a push or a pull request.
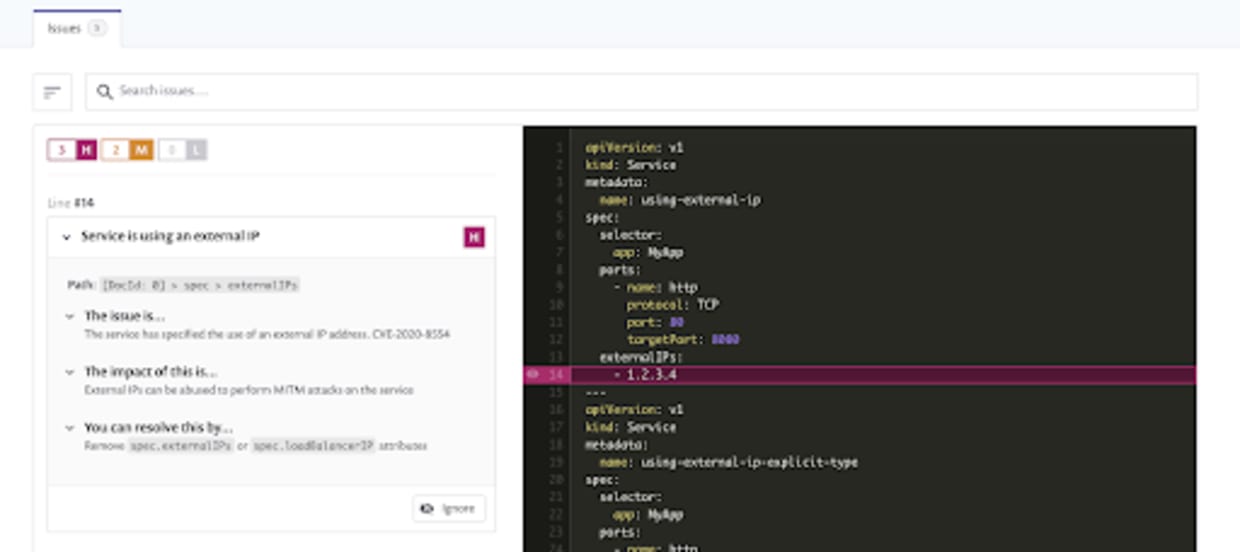
Kubernetes, however, has a way of fouling up the best laid plans. Take, for example, the Kubernetes Service man-in-the-middle attack vulnerability that was found to be exploitable in all versions of Kubernetes. Designated CVE-2020-8554, it was disclosed publicly on December 8th, 2020 and as I type this post no patch for this vulnerability exists yet. For those that had Snyk IaC monitoring in place, an updated policy was rapidly added and they started to receive alerts automatically as part of the continuous Snyk GitHub scanning feature, even though they hadn’t triggered a scan on their own.
If you are new to IaC and how Snyk scanning works, check out this Infrastructure as Code Tools post for a deeper dive.
Recent additions to infrastructure as code security scanning
The initial set of issues Snyk IaC scans for included Kubernetes, Helm Charts, and Terraform AWS resources. Since its initial release, Snyk engineers have continually added new policies, expanding the breadth of scanning; some of the enhancements recently added include:
Terraform AWS infrastructure as code
Over 100 policies covering areas such as:
S3 access control and logging
various checks related to sensitive data (i.e. hard-coded secrets, weak settings) in Lambda, EC2 and EKS
detection for lack of encryption at rest for various services
IAM privilege bad practices
Terraform Azure infrastructure as code
Now supporting Azure with coverage including:
logging best practices
app services best practices
MYSQL: SSL and alerting related issues
various PostgresSQL issues including:
SSL
connection throttling
logging
storage account access and encryption issues
Google Cloud Platform (GCP)
Also new are GCP resources including:
IAM user assignment
GCP Kubernetes related issues
Kubernetes
Coverage continues to mature for Kubernetes and Helm resources with new policies. More specificaly:
container checks including:
exposed ssh port
host device mounts
missing liveness probes
etc
services with external-IP (the CVE-2020-8554 scanning mentioned above)
PSP checks such as:
overly permissive volume mounting
Seccomp
AppArmor issues
allowing root GID in container processes
Scanning your own IaC code is simple
At Snyk we pride ourselves on making security simple to use and we believe that by empowering developers with tools that fit their workflows we can enable them to actively make a difference in squashing vulnerabilities and security issues at the source.
You start scanning your IaC templates right away by creating a free account at Snyk.io.
For more information on what Snyk has been up to this year be sure to check out the article my colleagues, Jim Armstrong and Daniel Berman recently posted going over all of the Cloud Native features and announcements Snyk has made during 2020.
Let’s make 2021 the most secure yet!
Secure infrastructure from the source
Snyk automates IaC security and compliance in workflows and detects drifted and missing resources.