The rising trend of malicious packages in open source ecosystems
March 23, 2023
0 mins readEditor's note: March 5, 2025
The landscape of malicious open-source packages continues to evolve.
In 2024, Snyk identified over 3,600 malicious packages, with npm (3,000+) and PyPI (600+) as the primary targets. So far in 2025, we've flagged more than 1,000 new cases, with JavaScript remaining the most affected ecosystem.
Snyk is prioritizing the addition of malicious packages to its database that have active users and potential customer impact, rather than those with no real-world effect.
Since the beginning of 2023, Snyk has documented around 6800 malicious packages across PyPI and the npm registry, which requires little to no interaction, almost 860 of which were discovered by us.
Starting in the middle of 2022, we observed a surge in the number of malicious packages published into the ecosystems. These newly added 6800 malicious packages follow the massive phishing campaign from a few months ago — as discovered by Checkmarx in December 2022, more than 144,000 malicious packages were published to open source software registries and have typosquatted and polluted these ecosystems with phishing attempts. This incident follows yet another familiar phishing event that targeted the npm ecosystem specifically, wherewith more than 17,000 malicious npm packages were uploaded to trick developers with phishing attempts. Python developers were also targeted through a security incident that targeted PyPI, the Python libraries registry, as more than 1130 malicious packages were published.
In this article, we want to share a broader picture of how the Snyk security team is monitoring and disclosing security incidents concerning malicious packages. With so many reports surrounding malicious packages, we would like to provide more insights as to the actual risk and impact we observed at Snyk regarding these security incidents and how to lower the risk to the point of mitigation.
The recent growth of published malicious packages is clearly an increasing trend. During 2021, Snyk added 82 new malicious packages, but in 2022 and 2023 the scale is totally different. Snyk added more than 9900 impactful malicious packages, which is an increase of 11,973% in comparison to 2021.
This growth is largely due to our increased investment in identifying and neutralizing the effects of malicious packages in response to the increasing awareness of the malicious package phenomenon.
At Snyk, we’ve developed dynamic analysis tools that allow us to detect and obtain source code of malicious packages across the different ecosystems (such as PyPI and npm), analyze and publish them in a timely manner. Additionally, due to the partnership and collaboration of the open source community, we are able to track more resources that publish malicious packages and stay up to date.
The following graph emphasizes the change in the amount of malicious packages added to Snyk’s security intelligence since 2021:
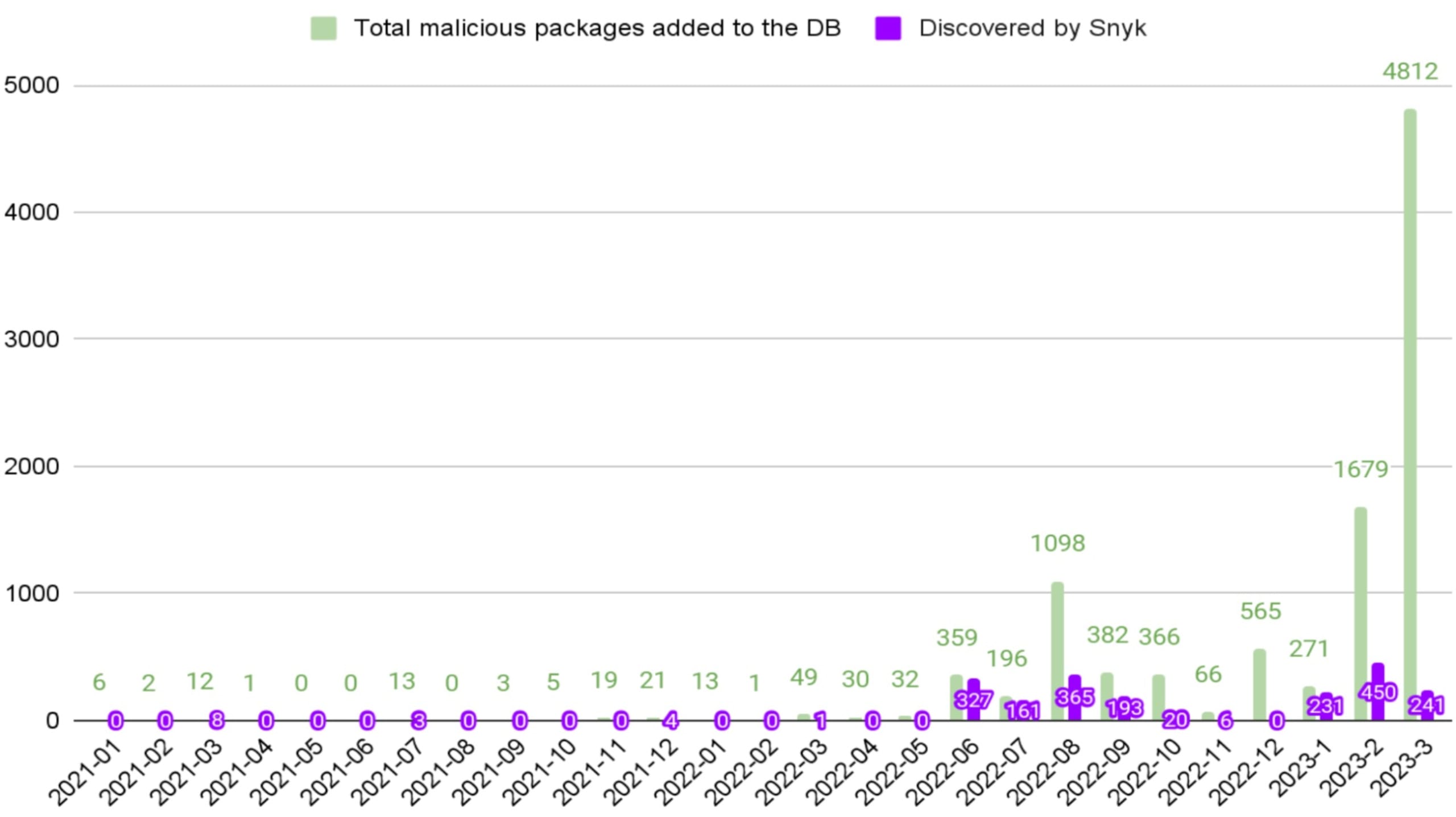
While the number of published malicious packages is massively increasing, it’s also important to assess whether all malicious packages present the same risk for developers — which, in reality, is not the case.
Many of the publicly known malicious packages are targeted phishing attempts. These packages require user interaction to be exploited — in addition to the action of downloading the package, the target must also proactively click the links to be redirected to the phishing websites. On the other hand, many impactful malicious packages, including those that make use of lifecycle hooks such as preinstall or postinstall scripts, can download malware or steal sensitive information from the target’s machine. These types of malicious packages don’t require user interaction beyond installing the package. Therefore, they post a more significant risk than packages that require proactive user interaction to be exploited.
Since 2023, Snyk found 681 malicious packages that require no user interaction except downloading the package. One such malicious package is the JavaScript npm package called django-yauth.
By investigating its source code, we discovered it contains a preinstall script named ./pre.sh, that includes the following code:
This preinstall script will execute when the user installs the package using the command npm install django-yauth.
In this specific case, the malware is simple to understand. It collects sensitive information, including the hostname value of the machine, the username, and the current directory. A POST request to an attacker-controlled endpoint will allow these details to be shared.
This package was uploaded to npm by a user named ypvpctpbamdhxtkzdu who published additional malicious packages with similar code, such as:
How to avoid falling victim to malicious packages
Before installing a package, you should verify that the package name is exactly the one you intended to install.
Additionally, you should aim to scan your projects and applications on a regular basis to avoid having unknown malicious packages in your system.
As a developer, you need to pay attention to suspicious indicators — such as a release with a very high version number in comparison to all other versions of the package or typosquatting naming attempts — and inspect the source code of packages you download.
For more tips and techniques to secure your projects, check out our previous post on preventing malicious packages and supply chain attacks with Snyk.
Security for the future
Even though the number of malicious packages is increasing, the abilities of open source security organizations and the open source community as a whole won’t fall behind. There are more automation and ML tools being developed to catch those packages on time, and the OS community has found that cooperation is vital to the “malicious packages battle”. Sharing information with peers and subject matter experts helps cast a wider net and makes everyone to be more aware of malicious packages they may encounter.
Finally, although the latest events included the massive publication of malicious packages, all of them were removed quickly from the ecosystem and had a shallow impact on Snyk customers.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
