Cloud native security guide for building secure applications
Modern, cloud-native architecture utilizes cutting edge software technology to provide enterprises with the means to deploy their applications securely, and at scale, with an emphasis on cloud-first infrastructure. Cloud native security is the same paradigm applied to securing these applications: a modern, pragmatic approach that includes concepts like zero trust and defense in depth (DiD). Cloud native application security demands the same approach, using purpose built tools and services.
What Is Cloud Native Security?
Cloud native security is the practice of securing cloud-based platforms, infrastructure and applications. Security is built in from the start of the development process through to production, ensuring multiple layers of security and continuous monitoring for new vulnerabilities.

What Is Cloud Native?
Cloud native is a collection of design principles, software, and services that focuses on building system architecture, with the cloud as the designed primary hosting platform. The overarching objective of a cloud-native application is to be highly scalable, resilient, and secure by taking advantage of the capabilities of modern cloud-based infrastructure, and leveraging continuous integration methodologies to enable faster development and deployment.
Cloud native also enables the simplification of operations, removing much of the burdensome overhead involved in managing and deploying traditional server infrastructure, leveraging high levels of automation by utilizing software driven infrastructure models.
While the above definition provides a solid foundation for a general understanding of cloud native, there are more specific takes on the subject from places like the Cloud Native Computing Foundation (CNCF).
In most cases, it's sufficient to think of cloud native as "cloud first," but the CNCF emphasizes a more vendor-neutral approach, championing projects and software that can be ported between cloud providers with minimal additional configuration. There is also a heavy emphasis on containers, which the largest CNCF project (Kubernetes) focuses on. It becomes immediately apparent that an enterprise could fit the general definition of cloud native while using hosted services that fall outside the scope of what the CNCF defines. It's up to individual teams to decide which definition is best suited to their designs.
What Are Cloud Native Applications?
Cloud-native applications are software programs and services that are built and designed in the context of cloud-native architectures. Cloud-native app is a specific and distinct unit, encompassing the necessary design principles, deployment paradigms, and operational processes to function in a way that takes advantage of the benefits of cloud native.
In contrast to the general principles of cloud native, specific applications require making definite implementation decisions, choosing tools and patterns, such as immutable artifacts, which help reinforce the cloud-native functionality of the larger system.
Although it's obvious there is a broad variety of ways to design and deploy software that will fall under the definition of cloud native, there are some generalized features that are shared by all cloud-native applications.
Most cloud-native applications rely heavily on automation in various forms. From automated testing and building of the core application code to automated deployment and scaling of the underlying infrastructure. Some of the most successful enterprises perform thousands of deployments per day, utilizing a robust, cloud-native CI/CD system that is heavily automated. Our state of cloud native security report shows that companies with higher levels of cloud native automation have a greater adoption of security testing techniques. Organizations with fully automated deployment pipelines are twice as likely to adopt SAST and SCA tooling into their SDLC to secure their cloud-native applications.
Cloud-native apps also typically employ microservice architecture patterns, with decoupled components that can be individually scaled to adapt to rising service demands. More generally, applications built utilizing DevOps principles will almost always implicitly depend on being cloud native to be successful.
Cloud native applications are able to be built faster and scale more effectively than previous application models, enabling more rapid innovation and faster time to market for technology-driven companies. However, the cloud native model brings about a fundamental change that must be considered by those responsible for securing and operating cloud native applications - what used to be infrastructure is now a part of the application. Specifically when it comes to security, cloud native applications require a new way of thinking about the security model, re-defining the notions of application security and operations.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
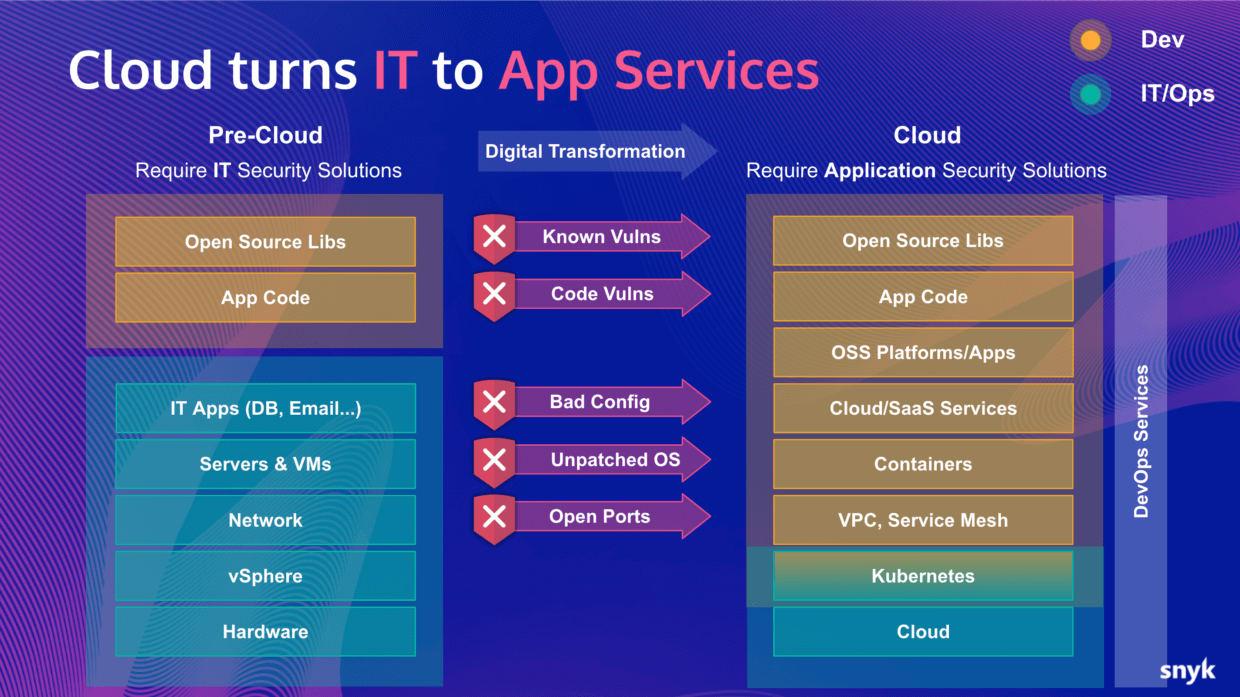
Cloud Native Security Tools vs Legacy Tools
Security tools and processes that were originally designed to handle the traditional, legacy software hosting infrastructure do not have the feature set required to sufficiently cope with the dynamic, highly exposed "borderless" paradigm of cloud-native architecture.
Put simply: Legacy security tools aren't built to handle the demands of the modern cloud. Many of the tools and design patterns that are second nature in a modern software stack may not have even existed when some security tools were originally designed.
A perfect example is the now widespread use of infrastructure as code (IaC) tools like Terraform. While they are technically "code," they typically represent a domain specific language (DSL) with unique functionality, making traditional validation using tools like static analysis difficult and ineffective. Given that IaC tools can provision large amounts of infrastructure with comparably little effort, it is critically important that they are secured. Auditing IaC code and configuration requires implementing best practices and tools that are only a recent development in the history of software and infrastructure engineering.
While IaC tools present a critical gap in legacy security tooling, they represent just one of the many challenges in securing cloud-native applications at scale. Fundamentally, securing cloud native applications requires an approach that migrates concepts that used to live in the IT/Operational security responsibility into the application security model, and securing these components needs to start with the developers that build the applications rather than being left entirely to IT/Ops security teams.
Securing Cloud-Native Applications
Cloud native security necessitates a re-focusing on security that operates in step with the overall cloud native strategy of an organization. Cloud native applications must be secured in an application context, and the approach needs to address the changes in the teams, processes, and infrastructure model that build and operate cloud native applications. Thus a key emphasis of cloud native security needs to be cloud native application security - ensuring that vulnerabilities are identified and remediated during development. The approach must be holistic, and security should be baked in throughout the software development life cycle.
Developers should be empowered by a security platform to focus on delivering a design that meets the business goals and utilizes cloud native principles, whilst at the same time recognising that as more and more of our infrastructure is defined during application development, the development team acquires responsibility for ensuring that code is secure. If cloud architecture isn't a first-class consideration in every discussion and design decision, then the goal of building a truly cloud-native application may fall short.
Once the foundation of the design has been laid, application and infrastructure coding is likely to begin. At this stage, it's critical to begin testing the code as early as possible in the secure software development life cycle (SSDLC). As alluded to earlier in the article, the legacy, single-pronged approach of static analysis is no longer sufficient. Static application testing (SAST), dynamic application testing (DAST), interactive application testing (IAST), and mobile application security testing (MAST) comprise just some of the array of tests that should be performed against cloud native application code.
Securing Cloud Native Infrastructure
Securing the cloud-native infrastructure of an application presents unique challenges as well. IaC configurations result in live infrastructure being deployed, with developers often writing infrastructure and application code in tandem. Security tools that can address this unique challenge are needed, and should seamlessly integrate with existing workflows, providing insights and remediation advice directly to the developer. This typically means surfacing security information directly into IDE’s and enabling local testing through CLI tools.
In addition to providing security insights to the local developer environment, cloud native security tooling should also be integrated into each phase of the software lifecycle. Automated scanning in source code management systems, and scanning of derived artefacts such as container images through CI/CD systems should be a priority. The results of these integration scans should also provide remediation advice to enable developers to easily make prioritisation decisions.
Legacy, on-premise infrastructure could often depend on a logical network perimeter, which would function to prevent unauthorized traffic into a distinct set of internal resources, which typically employed lax security controls. In cloud native, the notion of a perimeter ceases to be of any real value. Nearly any resource on most cloud providers can be made to be publicly accessible with a few lines of configuration or a UI change. Data that appears to remain the same logical domain may actually cross the boundaries of several networks and physical locations before it reaches its destination. In light of this knowledge, enterprises must adopt a "zero-trust" model, in which every component or service is assumed to be a potential target for compromise. Authentication occurs between all nodes or resources in a system, regardless of network location.
With the increased emphasis on cloud native application security in the development process, it is important to note that the need for cloud native security solutions continues into the live production environments. Legacy architecture typically had one type of computing resource available: the hardware server. Traditional security tools worked to secure the perimeter around these resources, employing static network configurations and firewalls to control access and traffic flow. Cloud native infrastructure is designed from the ground up to be highly dynamic, with rapid deployment of new applications and reconfiguration of resources.
What is Cloud Native Security Architecture?
A Cloud native security architecture is a strategy used to ensure visibility of everything deployed and running within the cloud that enables security teams to monitor and secure applications, infrastructure, and platforms on the cloud. Learn more about Cloud Security Architecture.
Cloud-native applications could potentially employ a bevy of different computing resources and runtimes, including virtual machines, containers, and serverless functions. Containers, another product of the cloud-native ecosystem, call for purpose-built security tools to help monitor and secure their runtime environments. Scanning artefacts and configuration at runtime is critical to maintaining a strong security posture when dealing with cloud native environments.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
Cloud Native Apps Need Cloud Native Security Platforms
Although it's constantly changing, the cloud as a whole is here to stay. As the pace of innovation continues to pick up speed, new technologies and tools will need to be developed to help enterprises keep up. Too often, enterprise organizations will port their existing, on-premises software infrastructure into the cloud, forcing dated abstractions and security models, and missing out on the advantages offered by cloud-native applications.
Security models and tools built for the days of on-premise hosting are a particularly severe liability. Most of these tools were designed before the proliferation of the cloud as a first-tier hosting platform and are insufficient in the task of providing adequate security. Being able to scale, and more importantly secure your applications is of paramount concern in an incredibly fast-paced and competitive space. Enterprises that want to remain competitive in the modern cloud age should focus on building cloud-native applications and using cloud-native security platforms to help protect them.
“There are a lot of moving pieces when you deploy software,”... “If you do it all manually, it’s time-consuming, tedious, error-prone, and you won’t want to do it very often. That’s why we knew we had to automate everything, including security, with Snyk.”
Secure every component of your cloud-native apps in a single platform with Snyk.