In this section
Complete Guide to Application Security: Tools & Best Practice
This Application Security Guide will equip you with all the information you need to stay secure in 2025
Daniel Berman
What is Application Security (AppSec)?
Application security, or Appsec, is a critical aspect of software development, aimed at identifying, fixing, and preventing security vulnerabilities within applications. It involves implementing a secure software development life cycle, with the ultimate objective of enhancing security practices and ensuring the integrity, confidentiality, and availability of data.

Application Security (AppSec) is a key practice. It finds, stops, and fixes security flaws in software applications from start to finish. This goes beyond just the code and includes system settings, design, databases, APIs, and the networks they run on. The main goal of AppSec is to improve security and make sure the data handled by apps stays safe, private, and available. This protects them from new online threats.
Why is application security important?
Application security is crucial because applications, especially those that are cloud native, are a gateway to servers and networks and present an ideal attack vector for malicious actors. This makes them top targets for bad actors. By building in security from the start of development, AppSec finds weaknesses before they can be used.
Since malicious actors continue to refine their methods to penetrate software, security must be an ongoing activity that’s deeply embedded in the development process.
Application security best practices help uncover vulnerabilities before attackers can use them to breach networks and data. It's also important to consider application data security to ensure that sensitive data, such as customer information, is secure.
Vulnerabilities can originate from something as simple as a configuration error or using a software component that contains a known vulnerability. The issue is widespread: according to Snyk’s 2021 State of Cloud Native Application Security report, over 56% of organizations experienced a misconfiguration or known unpatched vulnerability incident involving their cloud native applications. While not all of these vulnerabilities present a major security risk, hackers evaluate vulnerabilities to find which ones present a plausible method for penetration.

Organizations of all sizes should also be aware of the risk that misconfigurations pose, particularly those working with highly sensitive data (such as financial institutions).
How to improve AppSec Security?
To improve application security, companies need to implement a two-pronged approach:
Process Enhancement
Shift-left security culture. Bring security into design, planning, and coding rather than leaving it for later stages.
Secure SDLC + threat modeling. Define security requirements upfront, conduct threat modeling, enforce secure coding standards, integrate testing, and continuously monitor and patch applications
Developer training & awareness. Provide regular, hands-on security training, reinforce awareness of OWASP Top 10 risks, and promote developer accountability from planning through deployment
Tools & Automation
Dev-integrated SAST, DAST, RASP tools. Use Static AppSec Testing (SAST), Dynamic AppSec Testing (DAST), Software Composition Analysis (SCA), and include them in IDEs, pull requests, and CI/CD pipelines to catch vulnerabilities early.
WAFs, dependency scanning, CI/CD checks. Deploy WAFs to filter and block malicious traffic before it reaches your application, serving as a frontline defense against common web attacks.
Ongoing Practices
Secure design & coding. Guard against injection, XSS, buffer overflows, broken access control, and misconfigurations by validating inputs, sanitizing outputs, and using secure libraries.
Patch management & configuration hygiene. Regularly patch third-party software, libraries, OS, and infrastructure to mitigate risks from known vulnerabilities and misconfigurations
Security testing, logging, and monitoring. Conduct continuous assessments—SAST, DAST, penetration tests, and audits—throughout development and after deployment to catch evolving issues.
Cloud & Community
Harden cloud-native pipelines. Misconfigurations and unpatched vulnerabilities are the top causes of cloud-native breaches—use automated scanning to continuously validate your infrastructure, IaC, and secrets
Leverage OWASP and Snyk for guidance and benchmarking. Check out Snyk Labs for all the latest vulnerabilities and AppSec experiments, and research.
Snyk AI Security Platform provides tools such as Snyk Code, Snyk Open Source, and Snyk IaC to monitor and fix security issues. These tools fit into a developer's existing work process, making security as automatic as possible for good application security.
How to Perform an Application Security Gap Analysis
In this guide we'll walk through the steps to run a Application Security Gap Analysis for asset visibility, AppSec coverage and prioritization.
Common Application Security Risks and Implications?
Modern application security is a wide and complex topic. We’ve boiled it down to five main challenges organizations commonly encounter:
Category | Associated OWASP Risks / Issues |
Inherited Vulnerabilities | Broken Access Control, Injection, Insecure Design, Misconfiguration, Authentication Failures, Integrity Failures |
Third-Party & Open-Source Risks | Vulnerable & Outdated Components; OSS-specific supply chain risks |
DevSecOps Approach | Insecure Design, Integrity Failures, Pipeline security, early detection tools |
Finding Qualified Experts | Skill gaps and staff shortages impacting security effectiveness |
Lack of Centralized Tooling | Disjointed operations, poor visibility, inefficient coverage across teams |
Let’s take a deeper look at each of these:
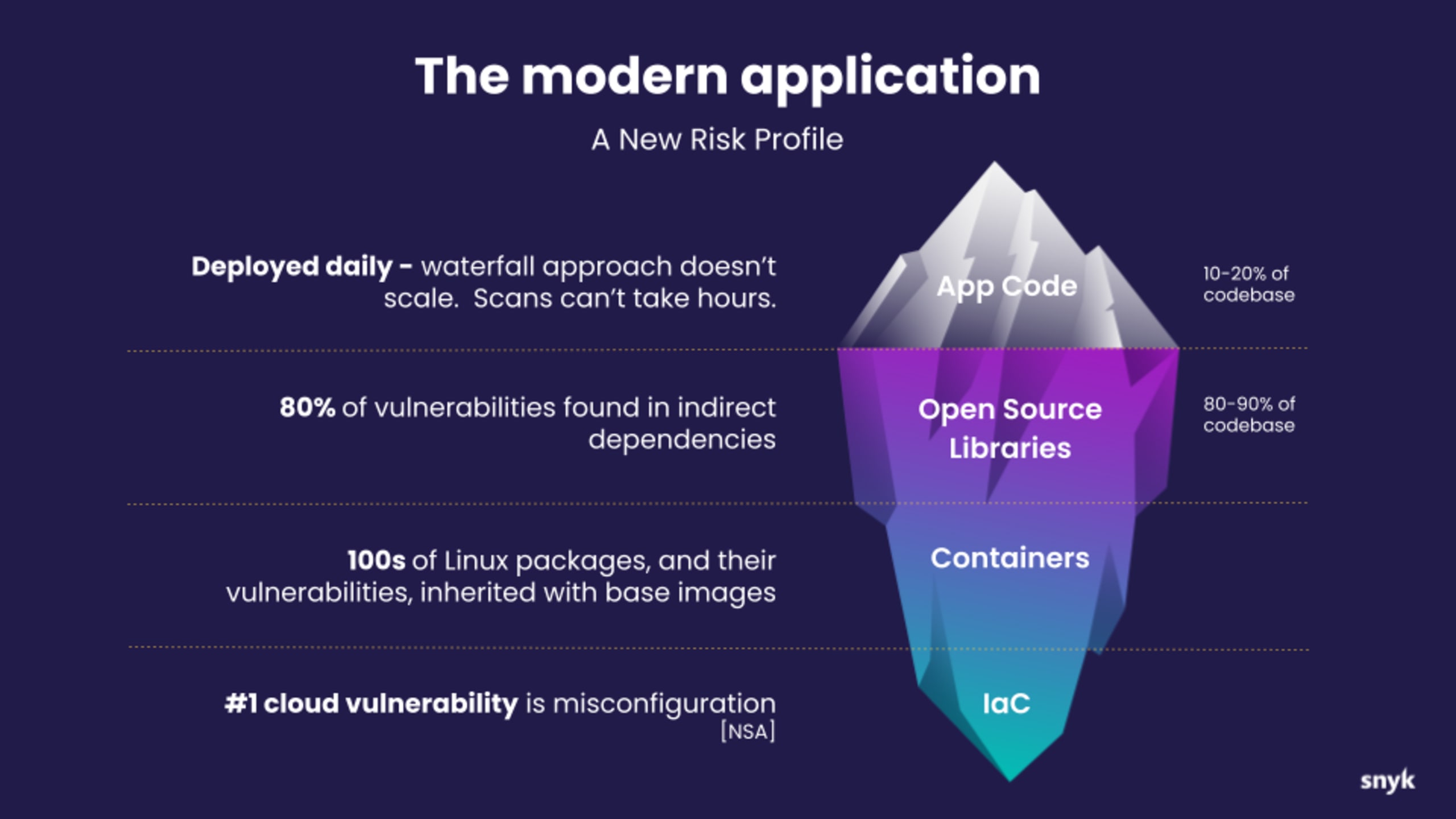
Inherited vulnerabilities
These are flaws originating from your own codebase—design or implementation choices.
Software systems experience entropy — they are constantly changing, increasing in complexity, and in need of updating and improvement.
Prioritizing vulnerabilities, which fixes, updates, and maintenance activities are most important is a vital and ongoing effort.
Legacy code continues to play an important role in many organizations’ environments, and security teams need to scan this code and prioritize the most important fixes. Older code is less exciting than shiny new application code, so fewer people are interested in working with it, but it still requires careful consideration pertaining to security.
The newest security tools are often not licensed to deal with legacy code. If the code isn’t maintained and secured, problems build up over time.
Third-party and open source vulnerabilities
These stem from external libraries or components beyond your direct control.
The widespread use of third-party and open source libraries makes them an attractive attack vector. Transitive (or indirect) dependencies are a particular concern since developers may be using vulnerable packages without realizing it.
However, external attackers aren’t the only concern with open source dependencies. Maintainers themselves could be releasing packages with malicious code or vulnerabilities.
It’s impossible to catch all these vulnerabilities manually, so to secure open source dependencies, you need tools to make you aware of what to update (and when) and detect new vulnerabilities as they arise. In addition to scanning tools, policy enforcement can help build security into projects from the start. Teams should develop policies that follow best practices and select tools that enforce those policies. The OpenSSF framework, for instance, sets rules for open source software projects to comply with. If everyone used this framework, security tools might not be as necessary, but this is unlikely to happen anytime soon.
Adopting a DevSecOps approach for AppSec
In addition to security tools, it’s critical to take a shift left approach and incorporate security throughout the development process. Traditionally, scanning has taken place late in the software development life cycle. The results would be sent back to development teams for fixes, meaning security teams became a bottleneck for other business areas. The tooling itself compounded this bottleneck with additional headaches for developers: The high number of false positives meant team members lost time triaging issues.
This legacy approach worked sufficiently well for organizations using a waterfall approach to software releases, but modern software development requires a tighter, more agile integration between security and development. Finding and fixing issues earlier in development makes the process more efficient for security teams and everyone else involved.

Shift left testing integrates testing best practices as early as possible in the CI/CD pipeline.
Finding qualified experts
In addition to shifting left, the human side of security is important. Finding qualified security experts is a top priority, and security teams themselves need to improve their training, develop efficient processes, and analyze their tooling. They can then equip themselves for a more integrated security approach, where scans happen in parallel with CI/CD pipelines so developers can easily apply fixes. Organizations are finding it difficult to hire experienced cybersecurity staff, as the ratio of developers to security practitioners is around 100:1, so more organizations are leaning more on developer security with education and automation.
Lack of a centralized management tool
Security professionals are tasked with managing the risk that an organization is willing to expose itself to. The idea that it’s possible to reduce this risk to zero is, in the best case, naive and, in the worst, counterproductive. A major aspect of risk management is to assess the vulnerabilities the applications contain and to prioritize which one to address, when, and how.
Application security teams need tools to support them. They need to constantly monitor and assess the security posture of an application, and ensure that they're using the correct application security metrics to track the impact of their work. Security posture means the combination of security knowledge at all levels of the application. Based on this knowledge, security teams need to triage and build a backlog of issues to address as part of the application security process.
Finally, the security team needs to monitor and ensure that issues from the backlog are correctly and timely addressed. The best tools will be able to centralize all of this necessary reporting and present it to stakeholders in a single dashboard.
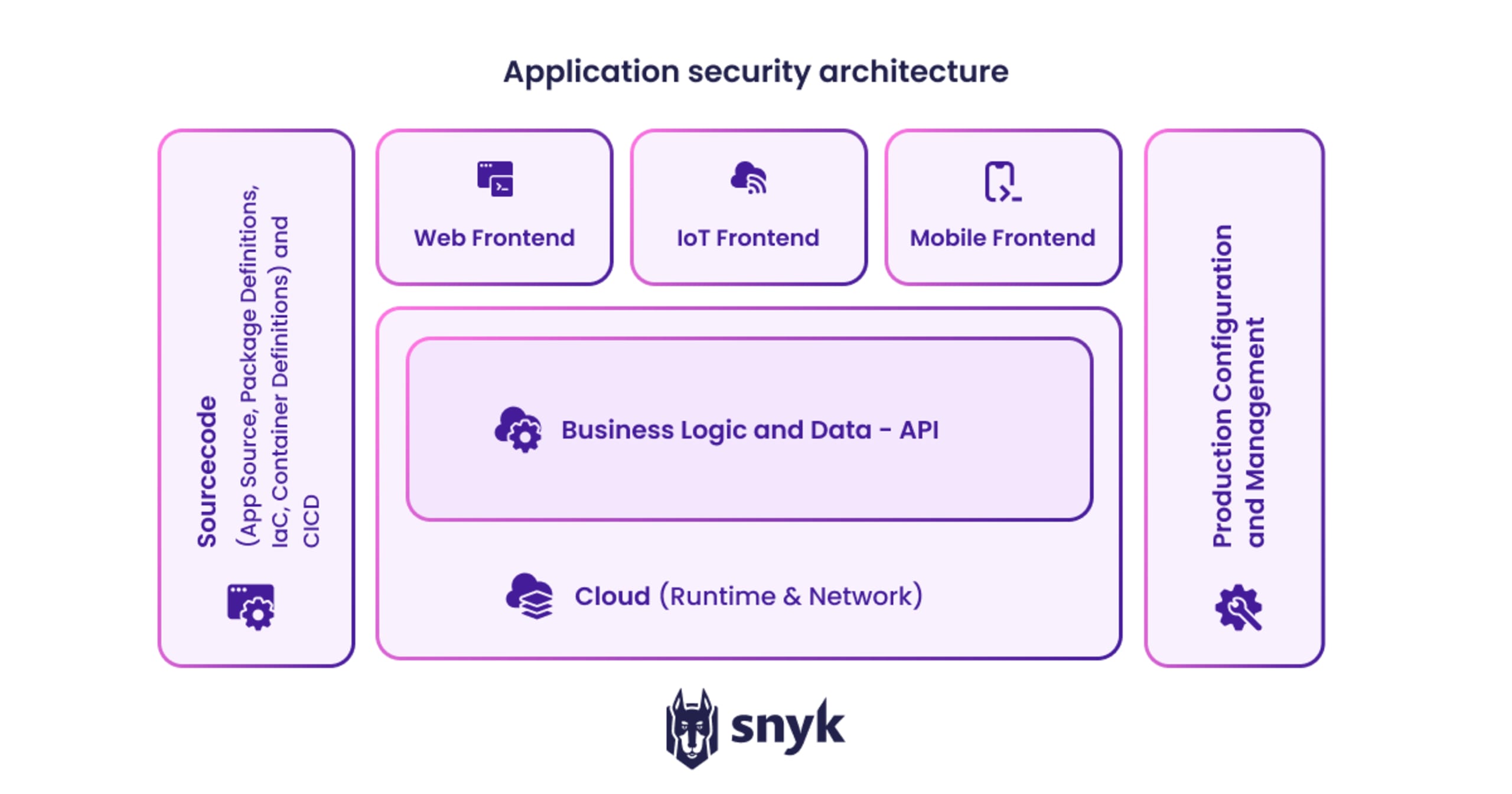
The three tiers of application security architecture
There are three tiers in the architecture of a modern application. Each tier has its own risks that need to be addressed. Here’s a look at each one, its makeup, and its potential risk profile.
1. The top tier: clients
This top tier, which may be a web front end, Internet of Things (IoT) front end, or mobile front end, is where users interact with an application. Front-end developers prioritize providing a high-performance, high-quality experience to the end user, but each type of front-end has its own threat profile, so security should not be overlooked. There are numerous ways to attack the front end, including injection and denial of service attacks.
2. The middle tier: the application
This is where data collected from users is processed. The tiered architecture itself helps protect against exploits by creating a kind of firewall between end users and data. Other tools, like fine-tuned access controls, can help secure this middle tier.
3. The bottom tier: the back end
This includes operating systems, cloud infrastructure, containers — everything used to run applications and store data. The goal of most attacks is to breach this tier, so it’s important to use secure configurations, properly configured networks, and robust data encryption to secure the back end.
A diagram of the architecture of a modern application
In the diagram below, we see the architecture of a modern application. Powering the front end is a business logic and data layer that exposes an API to the front end and runs inside the cloud (such as AWS, Azure, or Google Cloud).
On the left side, source code defines the client and logic, packages for your dependencies, cloud specifications (using IaC), and container files that give the configuration of containers your application will run in.
On the right side is the active production management. The cloud management consoles for production are especially valuable targets for hackers: if someone gains control of your cloud management console, they can use it to take control of machines to mine bitcoins, among other unauthorized uses.
It’s important to orchestrate security across the tiers to ensure it can be managed and operationalized. Doing so can have additional side benefits, such as the ability to detect click fraud, which can cause cloud oversubscription.
Application Security Best Practices
3 Key pillars of application security
There are three primary pillars of effective application security:
Technology, including process and training tools
Processes, including policies, principles, and controls
People who require education and training about security (such as to prevent phishing)
Here are the most important application security best practices:
Technology: review your toolset
Start by defining a comprehensive set of tools that can integrate with each other and that fit with your resource capabilities and budget. Remember that the best tools give recommendations — they require humans to action those recommendations to show the most value.
Explore the new tools that are available and review their capabilities.
Plan your tools roadmap. Where are they going? What is your vision around tooling? Will those tools keep up with your business needs?
Process: be clear
Start by defining your application security processes. Write them down to help gain clarity.
Test your processes. Do they actually work? It’s better to learn about any issues during testing rather than during an emergency.
Maintain a process repository. Keep your processes in one place. This helps during onboarding and can help you spot overlaps in processes.
Humans: embrace their role
Security teams and developers are knowledge workers. They need to be “upgraded” much like how software itself requires upgrades. The security field is constantly changing, but the development community is rich with information, training, and events. Educate and invest in your people so they know how threats and mitigation practices are evolving.
Invest in all layers of security. Everyone should be made aware of the importance and rules around security, from cleaners to CEOs.
Encourage an open culture for the smallest things. “SEE IT, SAY IT, SORT IT” should be the motto. An issue can’t be fixed if nobody mentions it.
What are the best tools and technologies used in Application Security?
Scanning tools are central to application security because they allow developers to test applications before running them in a production environment. These tools come in many different forms, including ones that scan source code directly and others that evaluate an application by running inputs through it. Here are six common types of scanning tools:
Static application security testing (SAST): SAST is a white-box testing method with access to source code, at rest, it identifies weaknesses that may lead to a vulnerability and then generates a report.
Interactive application security testing (IAST): This form of application security testing scans the source code for vulnerabilities while running the application and simulates the ways a user would commonly interact with it.
Software composition analysis (SCA): Also known as origin analysis, this method helps to analyze all sourced software components and libraries. These tools help identify known vulnerabilities and notify the user of any available patches or updates.
Dynamic application security testing (DAST): DAST tests an application’s security posture by applying different attack types to the running application. It does not require access to the application’s source code, making it a black box testing method.
Application security testing as a service (ASTaaS): In this scenario, the organization enlists an external company to perform all testing for their applications. ASTaaS usually combines static and dynamic security methods, including penetration testing and evaluating application programming interfaces (APIs).
Fuzzing: Fuzzing tests an application by inputting randomized data to uncover potential bugs. Fuzzing complements IAST, DAST, SAST, and other forms of testing.

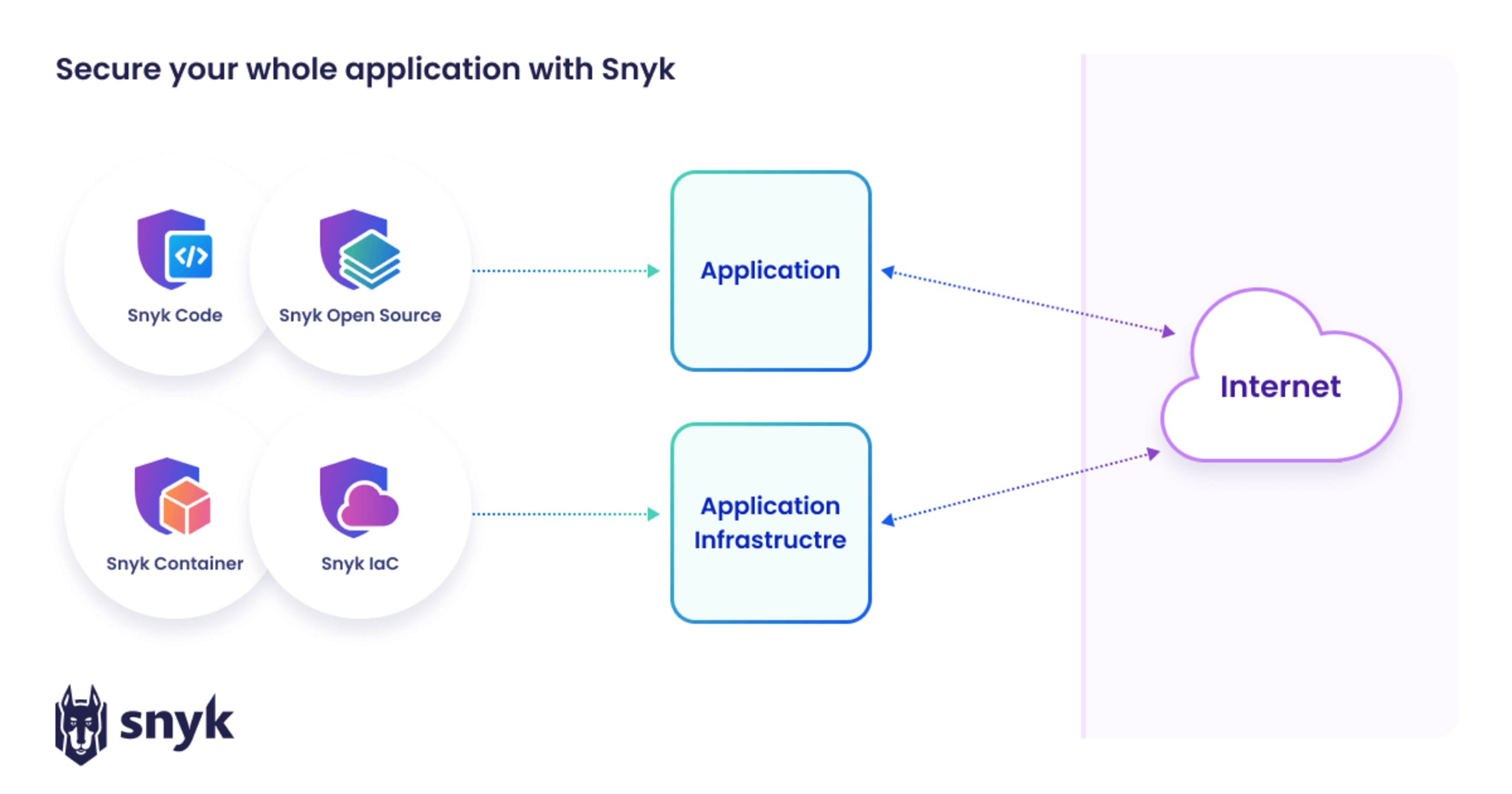
Application security with Snyk
Snyk is an essential application security technology because it provides end-to-end monitoring and mitigation steps that integrate into developers' existing workflows. Its tools include:
Snyk Code: A developer-first SAST tool aimed at making fixes easy and efficient.
Snyk Open Source: A software composition analysis (SCA) tool that uncovers and prioritizes open source vulnerabilities.
Snyk Container: A tool that helps secure containers from base image to runtime.
Snyk IaC: A tool that helps developers write secure IaC configurations.
Snyk AppRisk: An ASPM tool that helps to discover assets and ensure they're covered by security tools and free of vulnerabilities.
Here’s a visual display of how Snyk’s toolkit fits into application security:
Snyk’s tools are the natural next step towards automating developer security as much as possible. It’s continuing its evolution towards securing applications at runtime with its partnership with Sysdig and its recent Fugue acquisition. Together, these tools help developers ensure application security throughout the application life cycle.
Application Security Examples
Check out our case studies for examples of organizations that have used Snyk to improve their application security process and posture with developer-friendly workflows.
"The Glovo security team has reported a 78% reduction in critical vulnerabilities in its dependencies and code using Snyk. Furthermore, the team has achieved a 40% reduction in their mean time to fix, demonstrating overall that they’re able to ship more secure code faster."
Glovo
AppSec FAQs
What is the application security lifecycle?
The application security lifecycle runs parallel to the software development life cycle (SDLC). Traditional security methods involve waiting until an application is late in development — or even running in production — to secure it. Modern development practices move these practices earlier in the process, meaning that security and development teams need to incorporate security from the earliest stages of the SDLC all the way through to the runtime environment.
How do you secure an application?
Application security starts from the earliest stages of planning, where threat modeling and secure-by-design principles can ensure security is built into the application. It continues to the development and testing stages, where scanning tools can integrate into developer workflows to automate security testing. Since developers are increasingly responsible for the containers and infrastructure used to run the application, that environment also needs to be secured.
What are application security controls?
Application security controls are specific steps put in place to implement security standards. In the security hierarchy, policies are set to give organization-wide boundaries, while standards are specific rules based on those policies. Controls then put those standards into practice. For example, a company’s policy might be to only use specific encryption algorithms based on elliptic curve cryptography. Standards would then set rules for where to apply that policy in applications, and controls would then (ideally) automate their implementation
What is application data security?
Application data security is defined as the protection of sensitive business information and customer data that is processed and stored by software applications from threats like unauthorized access, modification, or deletion, making it a key part of your overall application security strategy.
What’s the difference between application security, cloud security, and network security?
Application security focuses on safeguarding the software itself—its code, logic, interfaces, and the data it processes—from vulnerabilities and attacks. It employs practices such as secure coding, static and dynamic testing, runtime protection, and ensuring third-party dependencies are safe. In contrast, network security protects the infrastructure layer—your data in transit, perimeter defenses, network segmentation, firewalls, VPNs, and intrusion detection systems—to prevent unauthorized access to systems and data.
Cloud security spans both domains but emphasizes the protection of cloud-based environments, including infrastructure, configurations, identity and access management, and compliance. It addresses risks unique to multi-tenancy, misconfigurations, and cloud-native APIs. Application security within the cloud operates at the app level, whereas network security in the cloud may extend to securing virtual networks or enforcing secure communication between service components.
What are the core principles of secure-by-design architecture?
Secure-by-design is an engineering philosophy that embeds security as a foundational attribute of systems from the earliest stages of design, rather than retrofitting it later. It emphasizes anticipating attacks and architecting systems to constrain compromises, applying principles such as least privilege, minimizing attack surfaces, defense in depth, and continuous assurance. Complementary practices—such as simplicity (KISS), open design (avoiding security by obscurity), separation of duties, and failsafe defaults—help reinforce system robustness by reducing complexity and enhancing oversight.
What role does zero trust play in application security?
Zero Trust is a security model that operates on the principle of “never trust, always verify”—requiring continuous authentication and authorization of every user, device, and application interaction, regardless of location or network boundary.. Applied to application security, Zero Trust ensures that access to applications and APIs is granted only through rigorous, context-aware controls, enforcing least-privilege policies and real-time monitoring to detect anomalous behavior.
This model also assumes breaches may occur and therefore supports architectural strategies—such as micro-segmentation, encrypted communication, IAM, and continuous behavioral analytics—that limit dwell time and lateral movement within systems, fundamentally enhancing application resilience and reducing potential attack impact.
How do you secure containers and Kubernetes workloads from an AppSec perspective?
Securing containerized applications and Kubernetes workloads requires a multi-layered strategy. First, scan container images for known vulnerabilities before deployment, enforce image signing, and integrate Infrastructure as Code (IaC) security checks early in the CI/CD pipeline. Use Kubernetes-native controls—such as admission controllers, Role-Based Access Control (RBAC), and network policies—to validate workloads, control access, and secure communication between pods and services.
Additionally, enforce best practices like using hardened host operating systems, running containers with the least required privileges, and continuously reassessing cluster configuration to avoid misconfigurations such as openly exposed namespaces or over-privileged roles.
What KPIs and metrics should CISOs track for application security maturity?
CISOs should monitor metrics that demonstrate both progress in risk reduction and the extent of AppSec integration across teams. Valuable AppSec KPIs include the number of exploitable vulnerabilities, average time to fix (MTTR), and alignment with compliance frameworks—all of which Snyk’s platform can help track and visualize.. Equally important are metrics reflecting team engagement and coverage—such as percentage of projects with integrated SAST/DAST, vulnerability remediation rates, and developer adoption of AppSec tools.
Unlock DevSecOps with Snyk
Overcome application complexities and AI hallucinations while fostering collaboration between dev and sec teams with insights from Snyk and Accenture.