Safely handling containers
June 22, 2022
0 mins readThis post was written by Tales Casagrande, a Snyk Ambassador. Snyk Ambassadors are passionate about sharing their security expertise. Become one today by signing up!
In the shipping industry, the container format follows ISO 668, a standard format that regulates the safe stacking of containers.
Imagine your applications with multiple containers, running different applications, serving different purposes for people all over the world.
Container safety for software
Modern software is not much different from a ship. We “stack” several microservices within projects, there are teams responsible for the development and security of the environment, and if someone makes a critical mistake, everything can be lost. Let’s think about containers from a development and security point of view.
Do you trust the image you’re putting into production? Is the origin reliable?
Do you conduct security tests to see if there are any security issues?
How do you prioritize fixes?
Does your base image have just the bare minimum needed to run your application?
Does the development team keep up to date on best practices?
Does your security team help during development, or just place blame when a vulnerability is detected?
If you can’t answer every question, no problem! Stick around and I’ll give you some tips.
Starting your analysis with Snyk Container
The point here is to break down barriers between security and development teams, helping both with information on how to prioritize vulnerabilities in containers using criteria instead of generating giant reports.
As an example, let’s use the snyk-goof repo, which contains a purposely vulnerable application used for testing (it is not recommended for use in production environments). We’ll analyze this application using Snyk Container, which provides a simple and effective way to automate vulnerability fixes and helps developers focus on problems.
First, create an account (it’s free!). If you already have one, just log in. Navigate to Projects > Add project.
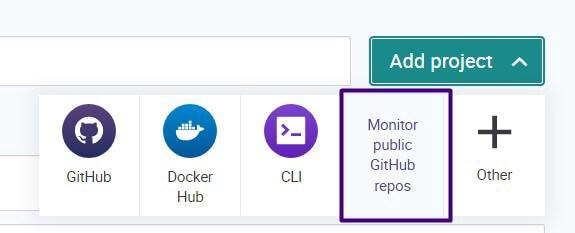
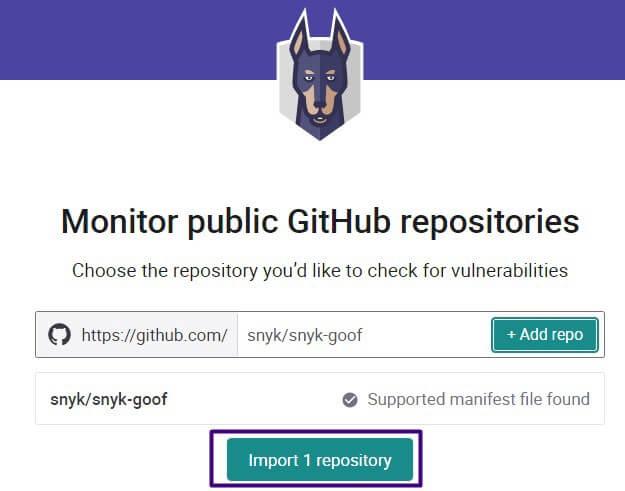
Be aware that it may take a few minutes for the analysis results to appear under your newly imported project. Snyk has the ability to analyze code, libraries and containers. Today we’ll focus on containers.
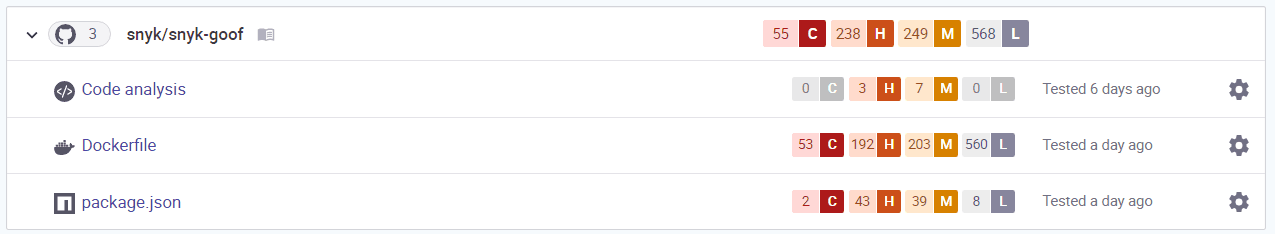
Take a look at the Dockerfile. Would you transport a container with critical infrastructure issues offshore? I don't think so! Let’s ask some questions:
Where can we start?
What is the priority of each of these problems?
Now, to create your plan, consider the following:
Could anyone take advantage of these flaws?
Is there already any malicious code (an existing exploit) on the internet that could exploit this flaw?
Is anyone on social media talking about the flaw?
Is there a fix?
Every vulnerability has a score assigned by the Common Vulnerability Scoring System (CVSS). The basis of this calculation score includes criteria such as attack surface, attack complexity, user interaction, and privileges required.
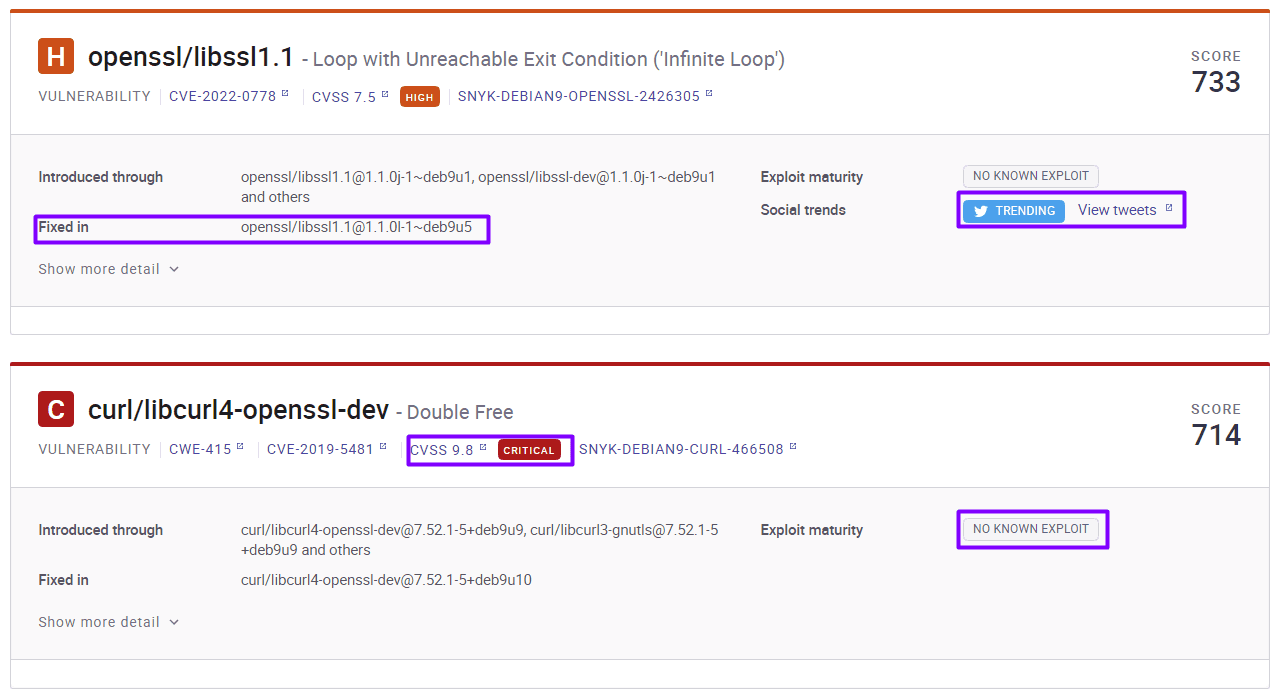
Snyk Container provides lots of helpful information about each vulnerability.
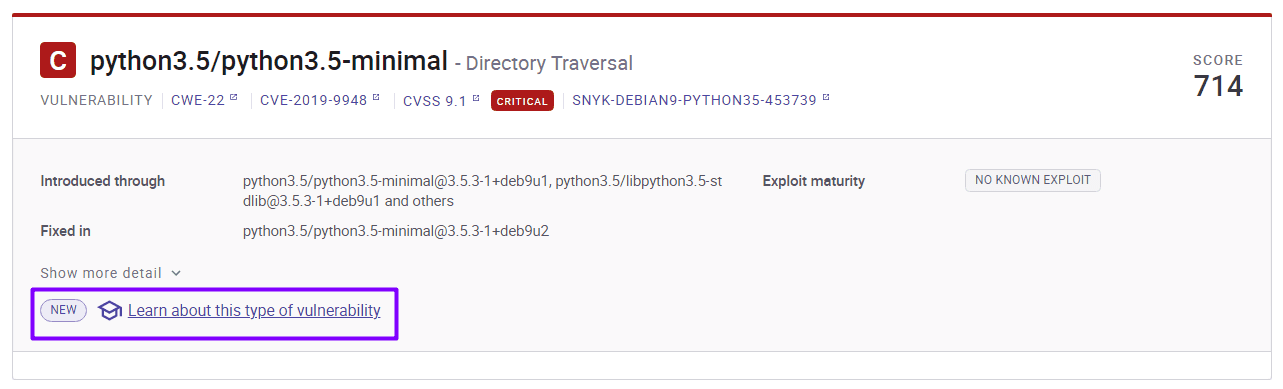
In this example, we’re talking about a simple image, but imagine on a large scale. What would it look like? We can create a baseline based on the questions above.
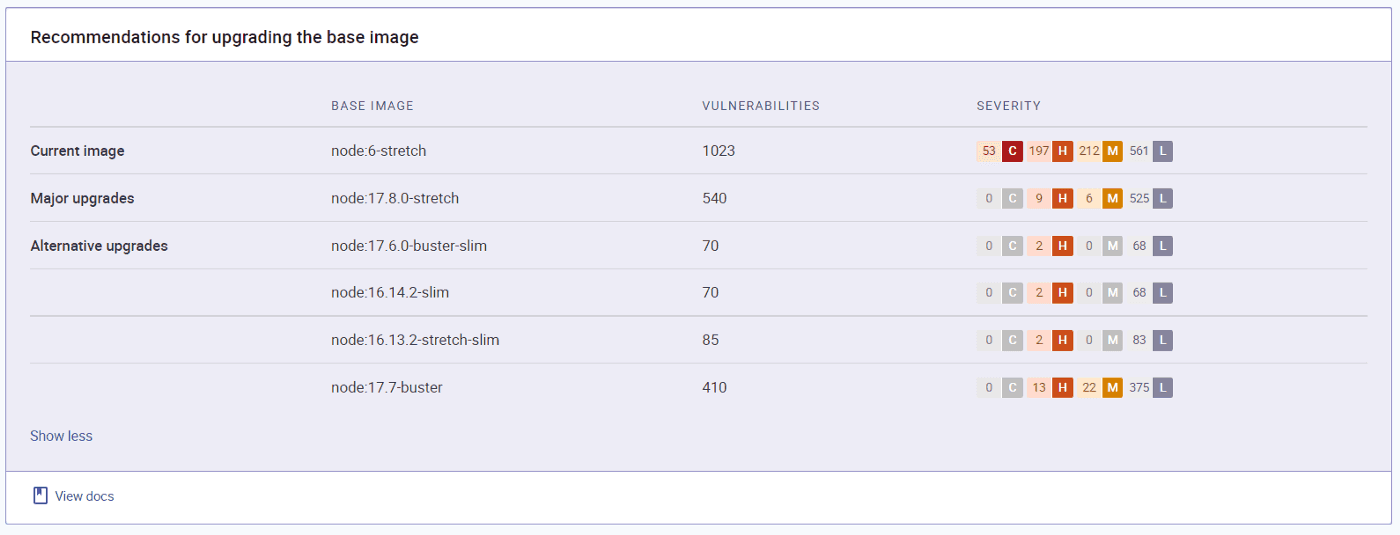
This image shows Snyk Code’s base image upgrade recommendations. These upgrades reduce risk, enabling us to save the time we might spend looking for another base image (or trying to upgrade).
Running the same analysis with the Snyk CLI
I did my analysis using the graphical user interface. But development teams often live on the command line, or in their IDE, so let’s remove the barrier of another login and do the same analysis using the Snyk CLI.
In the Snyk console, go to Integrations > CLI and follow the steps for your environment. Let’s use the same project: snyk-goof.
Now let’s build the image.
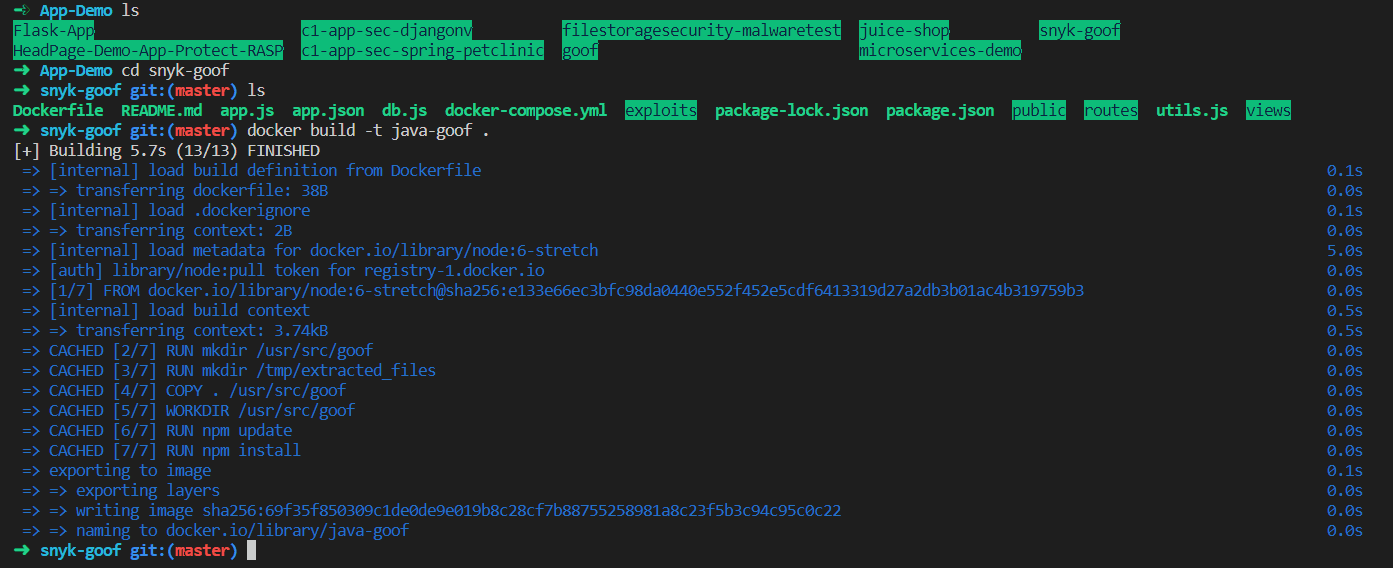
Now the fun part! Let’s start the analysis using the CLI.

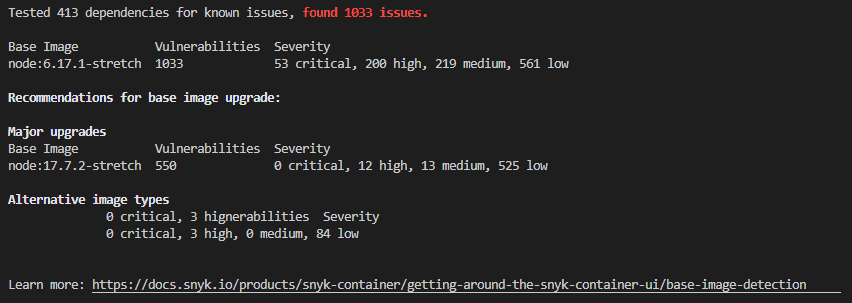
The test results in the console and the CLI are a little bit different because I tested on different days, but the analysis run using the Snyk CLI still provides the same base image upgrade recommendations.
The advantage of metrics-based analysis
New vulnerabilities emerge all the time. We can’t stop to fix every problem. We need to prioritize, automate and focus our efforts where the impact could be most severe. A metrics-based analysis eliminates the noise between teams and helps you quickly find ways to maneuver your containers safely.
Developer-first container security
Snyk finds and automatically fixes vulnerabilities in container images and Kubernetes workloads.





















