Scanning Red Hat Quay registry images for vulnerabilities with Snyk
April 1, 2021
0 mins readWe’re excited to share that you can now scan container images stored in Red Hat’s Quay container registry and their hosted Quay.io service with Snyk Container. Snyk Container helps you find and fix vulnerabilities in your container images and integrates with Quay as a container registry to enable you to import your projects and monitor your containers for vulnerabilities, as is fully described in our Snyk Container documentation. Snyk tests the projects you’ve imported for any known security vulnerabilities found, testing at a frequency you control. Integration with Quay is available for all of our pricing plans, including free Snyk accounts (Note: if you have private Quay registries and require image scanning to occur inside your own environment, this capability requires the use of Snyk’s broker, which is only available on paid plans).
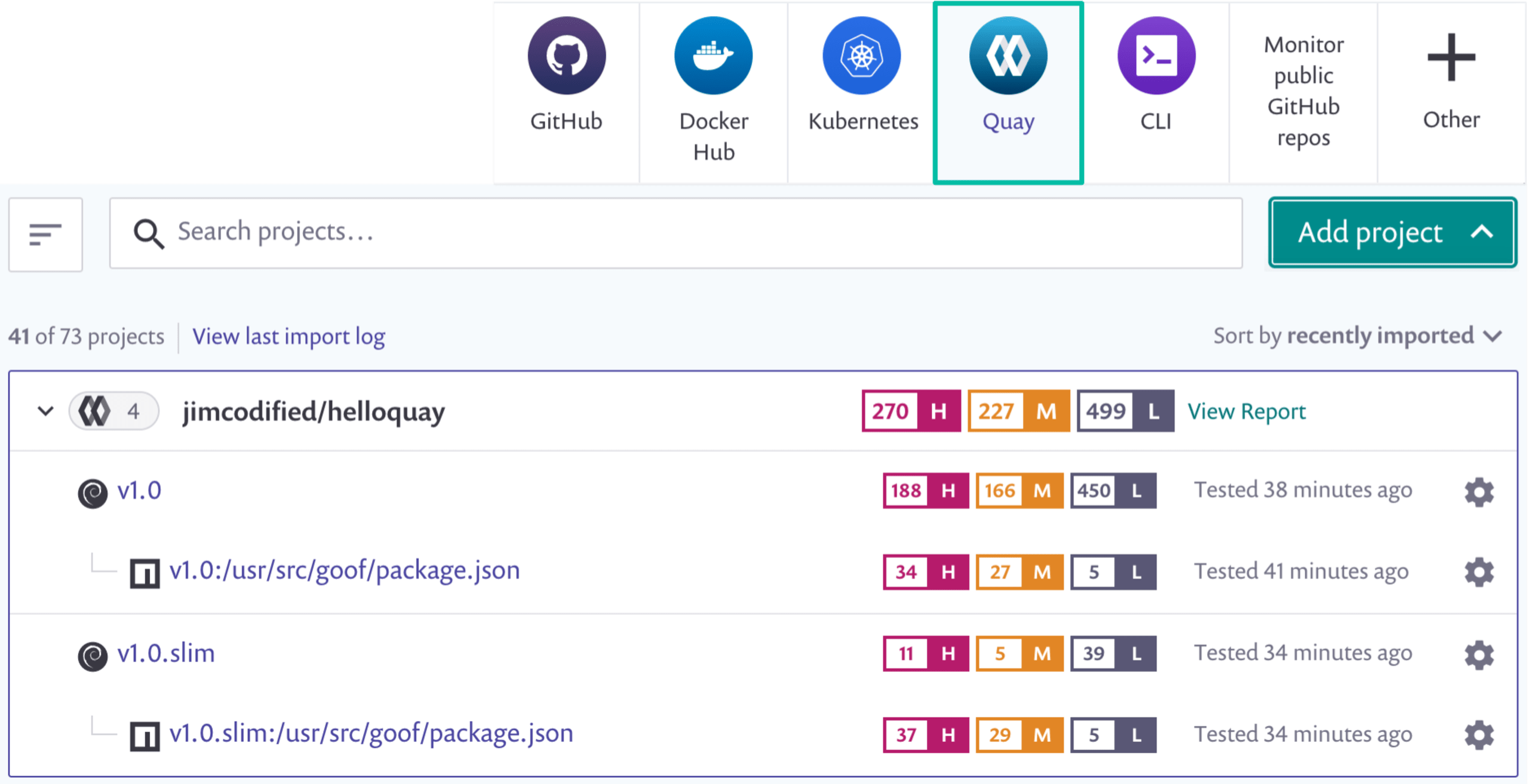
Once you’ve set up your connection to Quay and start adding images, Snyk Container provides base image upgrade recommendations, to help you quickly optimize how you build your containers, and includes built-in prioritization and dependency analysis features, enabling you to focus your efforts on the most problematic vulnerabilities in your images. We’ll take a look at each of these in action.
Using Snyk and Quay to reduce vulnerabilities
Snyk helps you identify and select alternate base images to help reduce the overall number of vulnerabilities in your container images. Often there are a number of base image alternatives available, especially for popular official Docker images. Snyk Container can determine the base image you’re currently using and provide recommendations for upgrades with fewer vulnerabilities.
The following shows base image recommendations for a container image built atop node:14.1:
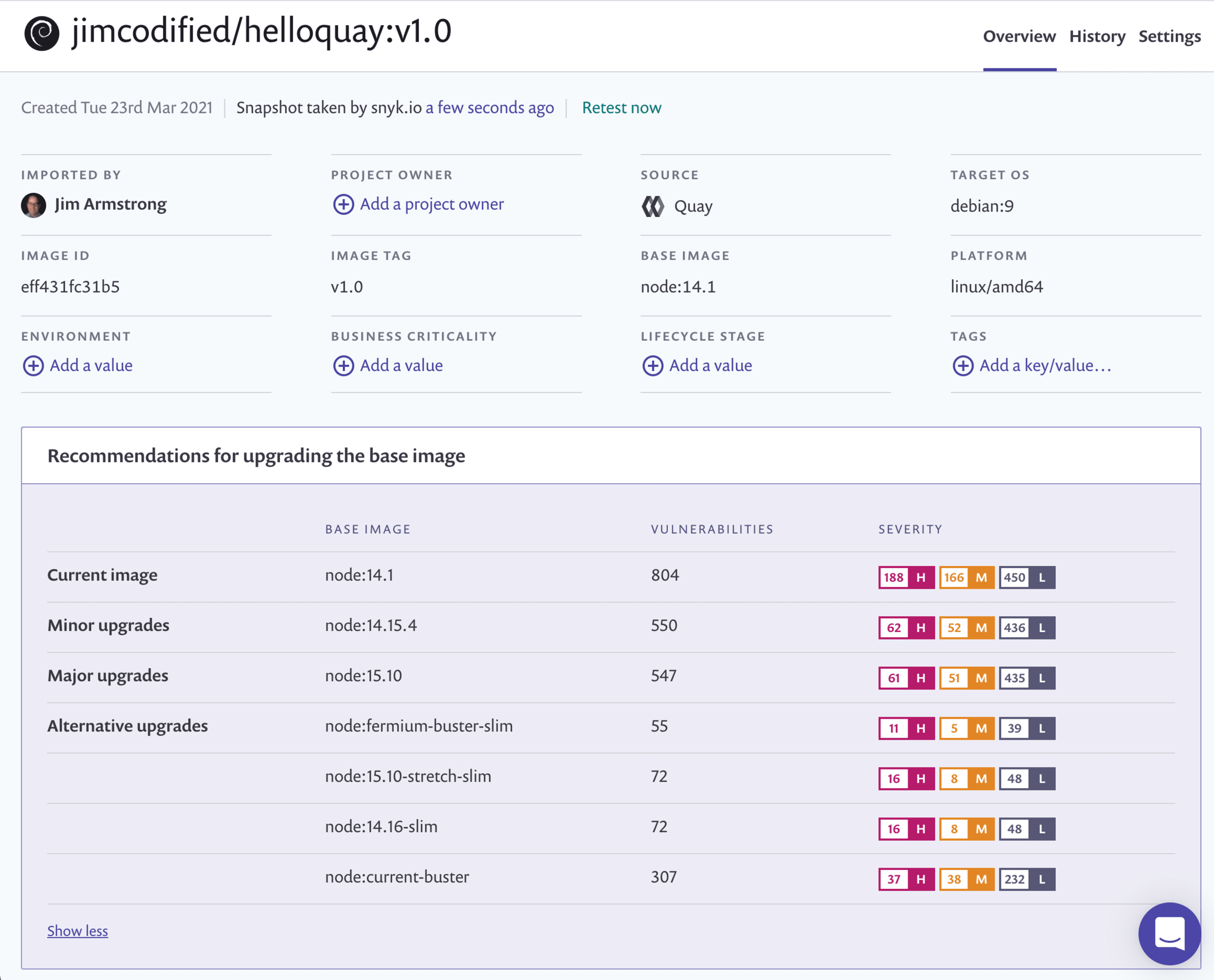
Snyk Container offers the different recommendations that are available based on your project, to enable you to control how you fix vulnerabilities:
Minor upgrades- with the general idea that smaller upgrades are faster and easier to use and less likely to break your build, these are minor upgrade recommendations, enabling you to keep the same major versions of the framework (node, in this example) and the same operating system distribution
Major upgrades - require a move to a newer major version of the framework or operating system distribution
Alternative upgrades - offer alternative suggestions for different images that can be used instead, but which may change both the framework and the distribution. While these alternative options may greatly reduce the number of vulnerabilities, as in the example above, they might also require more testing and consideration to ensure they don’t break your code.
Prioritizing container vulnerability fix efforts
After optimizing your base image, Snyk Container also helps you discover where you might be introducing additional vulnerabilities in your container images and prioritize which issues to focus your remediation efforts on. You can add your Dockerfile to Snyk, which provides the ability to match vulnerabilities up to the instructions that introduce them to the container, and Snyk has full dependency information to easily trace vulnerabilities back to their source. In addition, while it’s easy to be overwhelmed by the sheer volume of vulnerabilities in containers sometimes, Snyk helps focus on the most important or riskiest issues.
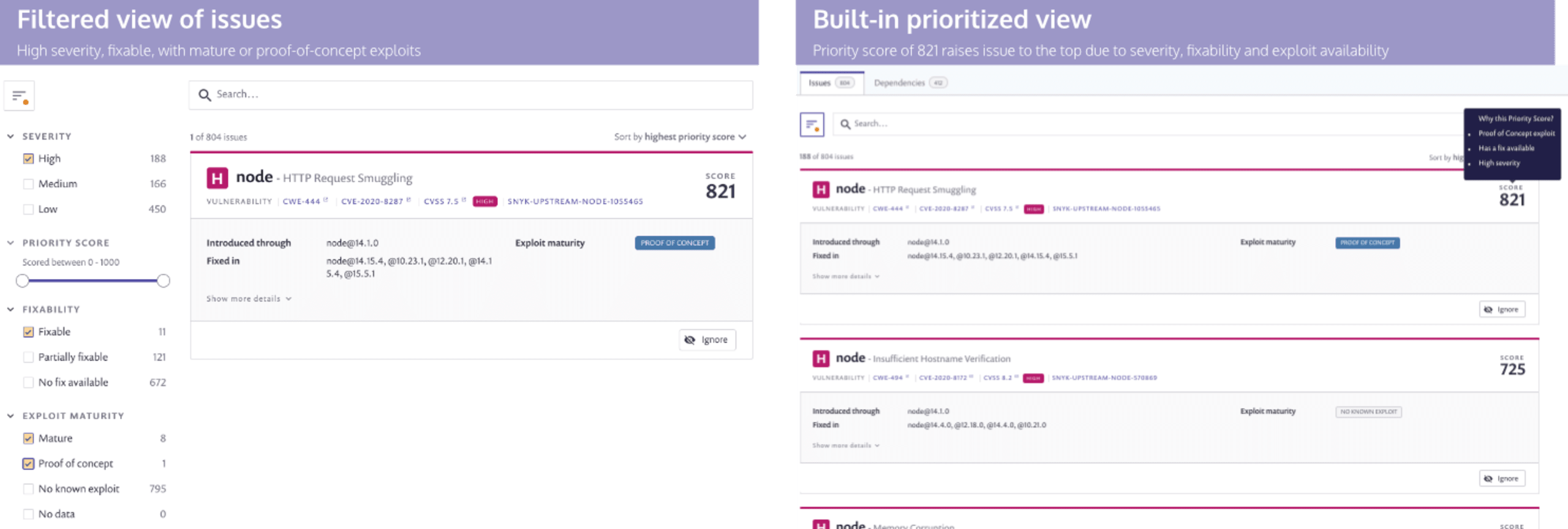
In the image below, for example, we have two ways of getting to the same basic view of the issues. Specifically, “show me all the fixable, high severity vulnerabilities for which an exploit is already available in some form.” In the view on the left, we use the Snyk filters to select for those details. In the view on the right, Snyk’s built-in Priority score causes the same issue to appear at the top of the issues list because all of those factors raise the potential risk of the vulnerability.
Getting started
Quay integration is available for all Snyk plans, and there are two different models:
Integrating directly with the Snyk Container service on Snyk.io [available for all Snyk plans]
Scanning on-premise for self-hosted registries that you do not want to connect directly to Snyk’s service [available only for Pro and Enterprise plans]
If you’re integrating directly with the Snyk.io it’s easy to get started. You’ll just need appropriate credentials (read access, at least) and you can be up and scanning in a matter of minutes.
If you’re self-hosting Quay on a private network you need to install the Snyk Broker and ensure your account is enabled for this feature. Your Snyk customer success team can make sure you’re ready to go, if you’ve not used the Snyk Broker before.
We’re excited about our ongoing work with Red Hat as we continue our efforts to make it easy for developers to fix issues as they work. Here are some more resources to get you started:
Snyk & Red Hat workshop materials with exercises to walk you through how to integrate Snyk into your Red Hat workflows.
If you don’t already have a Snyk account, it’s free to sign up and use Snyk to scan both container images and open source dependencies.
Find more information on how Snyk and Red Hat partner to empower developers to secure OpenShift applications here.
Want to see a demo or ask questions? We’d love to hear from you.
Stay secure!
Developer-first container security
Snyk finds and automatically fixes vulnerabilities in container images and Kubernetes workloads.
