Fetch the Flag CTF 2022 writeup: Potty Training
November 12, 2022
0 mins readThanks for playing Fetch with us! Congrats to the thousands of players who joined us for Fetch the Flag CTF. And a huge thanks to the Snykers that built, tested, and wrote up the challenges!
This post was written by Snyk Ambassador, Mohammad-Ali A’râbi (@MohammadAliEN). Sign up to become a Snyk Ambassador today and get inside access to Snyk, including access to CTFs before they go live.
The challenge (with some historical context)
If you attended Snyk's 2022 Fetch the Flag CTF, you know the Potty Training challenge. It was fast, simple challenge that I found quite interesting. It was also the first flag I ever fetched or captured in a security competition!
So, the challenge just contained a single PNG file called potty.png. When it’s an image, then it means most likely something is hidden in it. Concealing messages inside pages is so old, it has a Greek name: steganography, which means “concealing messages”. This is probably the oldest practice of sending secret messages, ages before cryptography was invented.
Back in 480 BC., Demaratus, a Greek who was expelled from his homeland, was living in the Persian city of Susa (aka Shush). He witnessed the Persian King, Xerxes, gathering an army to launch a surprise attack on Greece. So, he wrote a message, concealed it in a log, and let a messenger take it to Sparta. It takes the Spartans some time to find the right Python library to extract the concealed message, but they eventually do it. Ok, that part isn't true. Spartans didn't use Python, they uncovered the message by trying different things and including ideas from everyone.
Okay, enough with history. My point is, that “steganography” is the word of the day.
The solution
When I started the challenge, I first didn’t think of steganography and looked into the file with text editors like Vim, but it was all gibberish, as expected. The second hard part was to find the correct library to extract the concealed message. I was going to use Python anyway, so combining the two terms steganography and Python in my Google search led me to this nice Python package called stegano.
Opening the description up, it says after installing the package, one could also use it with CLI. So, let’s install it first:
1pip3 install steganoAnd then using the CLI:
1stegano-lsb reveal -i potty.pngThe output is the following:
1 import requests
2 r = requests.get('https://potty-training.c.ctf-snyk.io/')
3 print(r.text)So, some sneaky (or rather Snyky) Python code is hiding inside the PNG file. Now that we have extracted it, let’s put it into a Python file:
1stegano-lsb reveal -i potty.png > potty.pyFix the indentations a bit and run it:
1python3 potty.pyThe snippet runs, but throws an SSL certificate error, meaning that the HTTPS protocol won’t work. You might not remember HTTP in the wild, but being someone in their early 30s, I remember the times that you could find HTTP websites. So, let’s edit the code and turn the https URL into http for the old times' sake:
1import requests
2r = requests.get('http://potty-training.c.ctf-snyk.io/')
3print(r.text)And by running it, it shows this awesome message:
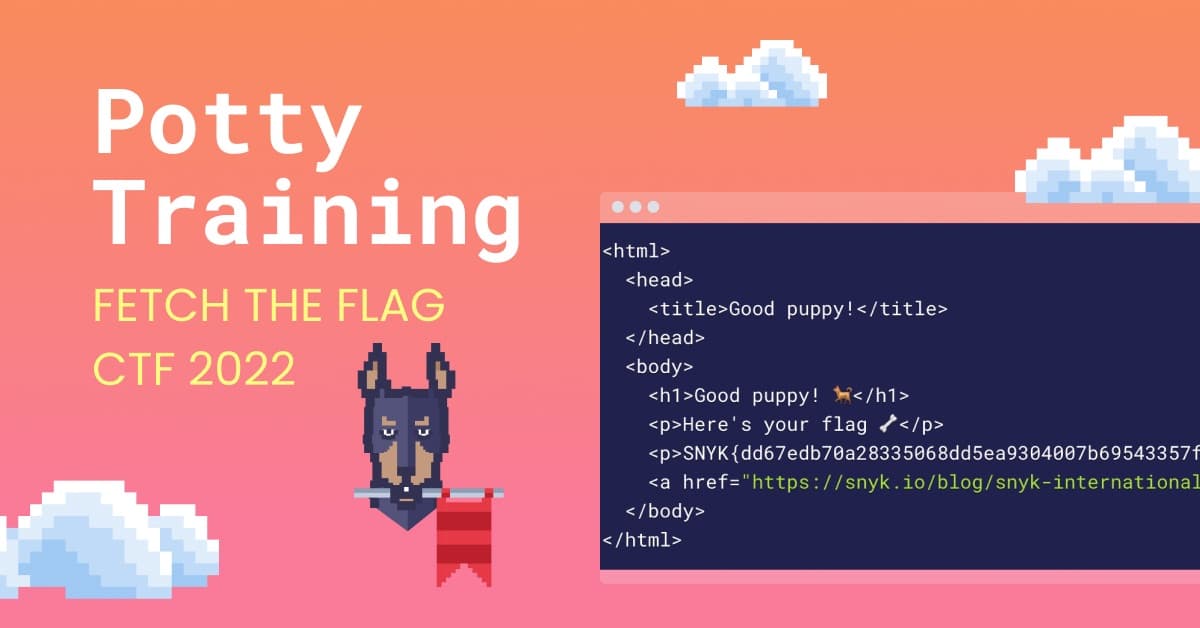
1<html>
2 <head>
3 <title>Good puppy!</title>
4 </head>
5 <body>
6 <h1>Good puppy! 🐕</h1>
7 <p>Here's your flag 🦴</p>
8 <p>SNYK{dd67edb70a28335068dd5ea9304007b69543357ff471b3144e3355bca34cb35d}</p>
9 <a href="https://snyk.io/blog/snyk-international-dog-day-recap/">Snyk + Dogs = 💜</a>
10 </body>
11</html>Tada! ? We get a good puppy and a nice flag to capture.
Final words
I really enjoyed solving this challenge in the CTF event. The last time I was in a capture the flag competition, I was playing Call of Duty 2 with my friends in a local game station. I would say capturing Snyk's flag was more fun than capturing the flags of WWII forces (the CoD 2 CTF maps are so unbalanced!). Already looking forward to next year's CTF!
The key takeaways for me were the following:
There is this protocol called HTTP. It's old, but not obsolete.
Steganography is very old, but not obsolete
If you're interested in learning more about the history of this kind of challenge, read The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography by Simon Singh.
If in doubt, use Python.
Want to learn how we found all the other flags? Check out our Fetch the Flag solutions page to see how they did it.