Announcing Insights: Helping you focus on top risks for your organization
Daniel Berman
June 7, 2023
0 mins readModern applications are built, deployed and, run in increasingly complex and dynamic environments. Assessing and prioritizing the security issues introduced by these applications without taking this context into account inevitably leads to focusing remediation efforts on the wrong set of issues. This not only results in real risk slipping under the radar but also wastes the valuable time of developers, increasing their frustration and eroding their trust in security.
This is why we’re excited to announce Insights, a unique capability providing organizations with code to cloud application intelligence that enables development and security teams to manage their application security posture more effectively by identifying, prioritizing, and fixing those issues posing the greater risk! In fact, Insights is already helping early adopters to dramatically reduce noise in their backlogs and focus on the top risks to their business!
“Understanding where to focus our fix efforts has always been a major challenge for us. With Insights, Snyk is providing the context we need to narrow down on just a handful of vulnerabilities, making prioritization much more effective.”
Alessandro Manno, Tech Lead Cloud Engineer at facile.it
Insights will be available in open beta starting July 12th.
Prioritizing vulnerabilities in siloes
Organizations face thousands — if not tens of thousands — of security issues in their backlogs. Understanding that it is impossible, and usually unnecessary, to fix each and every issue and maintain a fully secure posture, security teams repeatedly go through the process of deciding which issues are more urgent than others and asking developers to address these issues first.
Today, this process takes place within siloes.
Software composition analysis (SCA) tools are used to find, prioritize and fix open source and container vulnerabilities, static application security testing (SAST) tools do the same for code issues, and so forth. While CVSS-based severity levels provide a good starting point for prioritizing within each of these buckets, they only provide a siloed, static, and theoretical picture of the actual risk posed by a given issue.
Modern software risks require context
Today, however, security issues do not exist in silos. They exist within the highly complex and dynamic architecture of the modern application, which includes not only the application’s source code, but also containers and Kubernetes, the databases the application connects to, the cloud environment in which it runs, and plenty more.
These components, and the intricate relationships between them, have a direct impact on the practical risk posed by security issues. For example, a Log4j issue identified in a deployed container with public access to the internet likely poses more risk than the same issue identified in a staged container with no direct access to the internet.
Without this application context in hand, prioritizing issues effectively becomes an impossible task. Issues posing little or no risk to the business can get erroneously prioritized over issues actually posing a greater level of risk. As real risk gets ignored, and developers find themselves wasting time on irrelevant issues, frustration grows, and trust in security erodes.
This is exactly where Insights comes into the picture.
Helping you understand your application so you can prioritize based on risk
Insights is designed to provide you with the application context you need to gain a better understanding of the risk posed by security issues so you can make faster and more effective prioritization decisions.
It does this by aggregating and correlating data from across the Snyk platform to construct a 360° view of your application that includes all the components involved in producing it, together with the context of how it is deployed in production. This view enables Insights to help you better assess the risk a given security issue poses by answering questions such as whether the issue is applicable to your environment or not, whether the code introducing the issue is deployed or not, and so forth.
Let’s take a closer look at how Insights provides this information and how you can use it.
Exploring your security issues
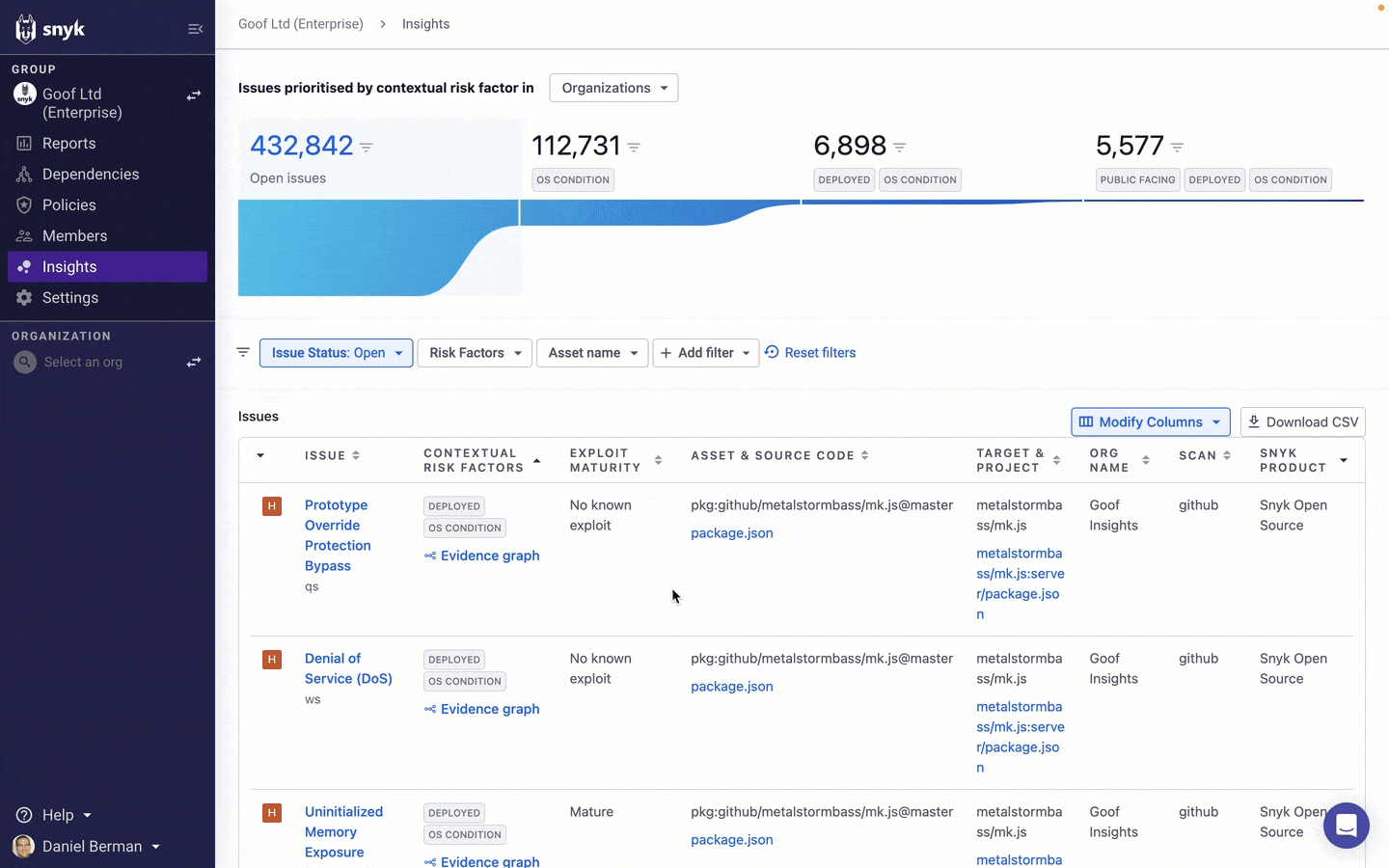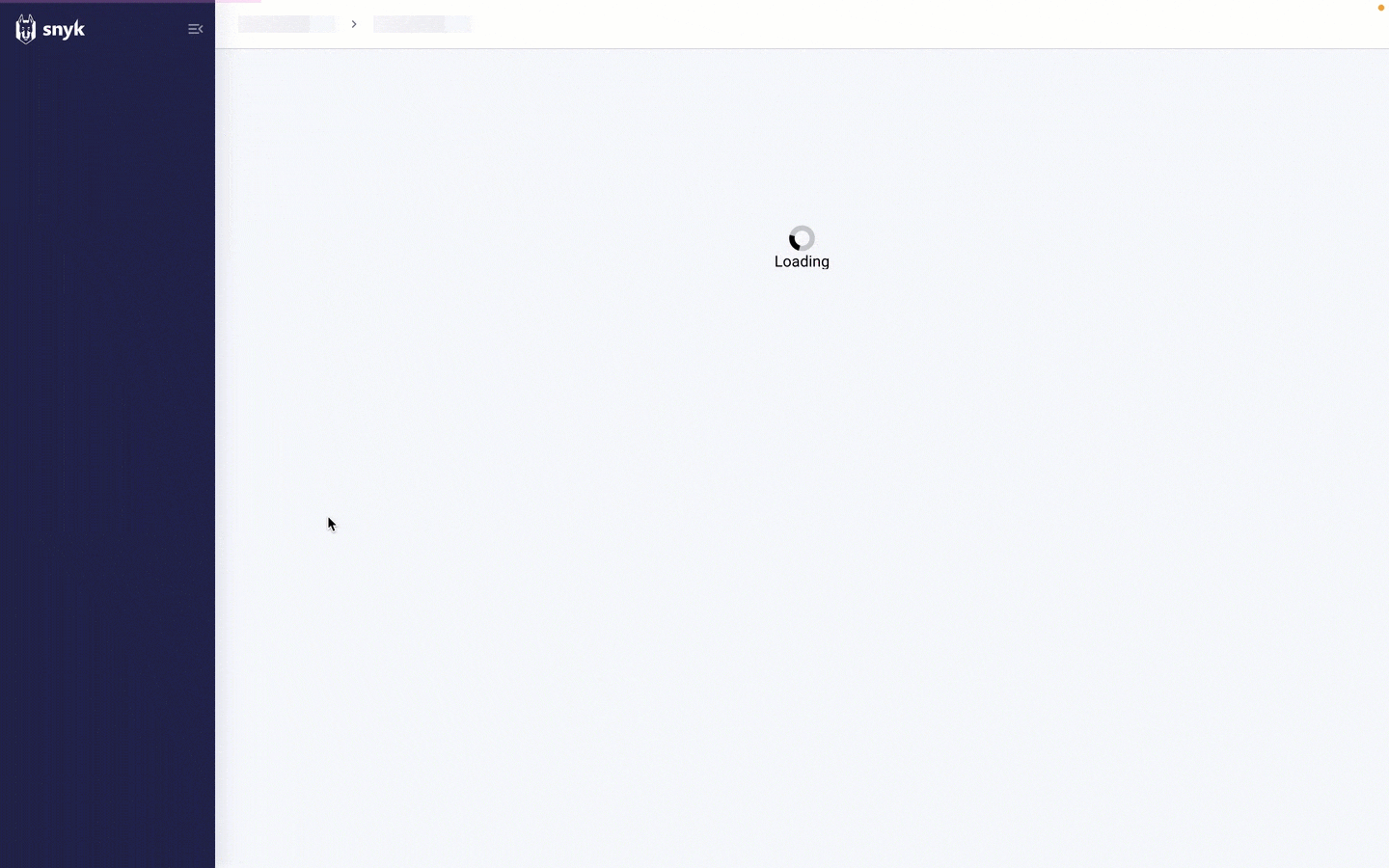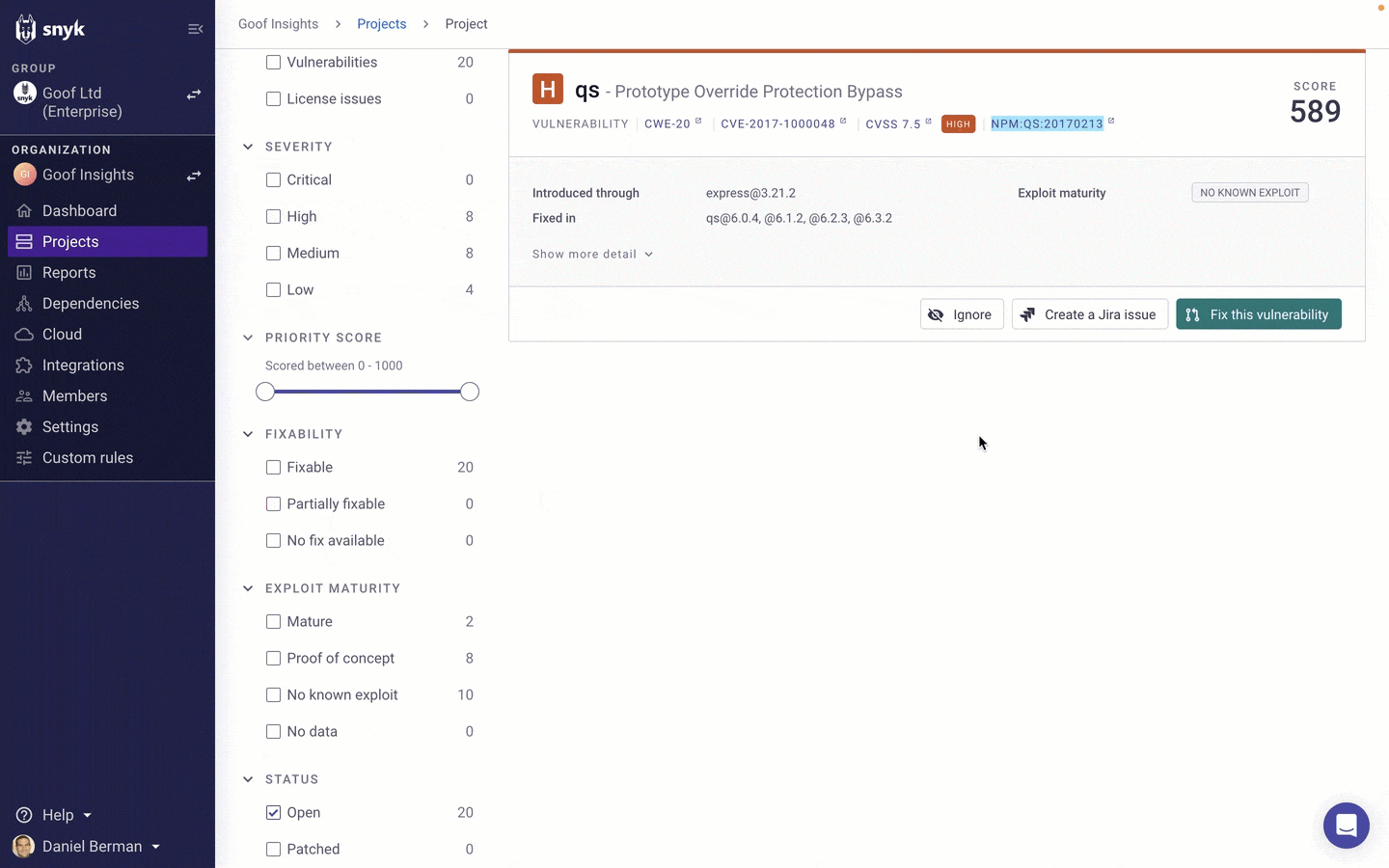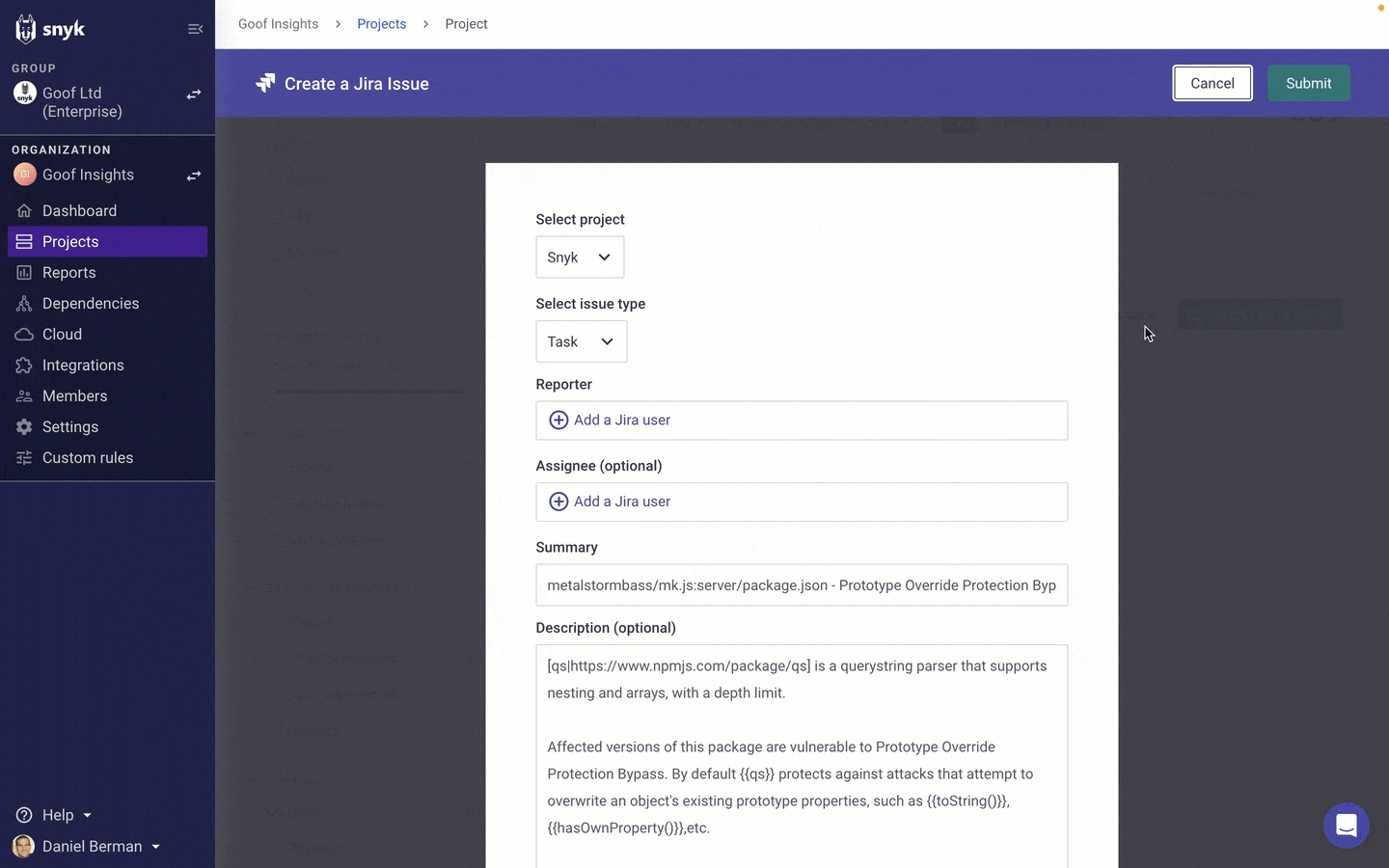
Once you've enabled Insights, your journey starts on a new Insights page which can be accessed via the main navigation within the Snyk App UI.
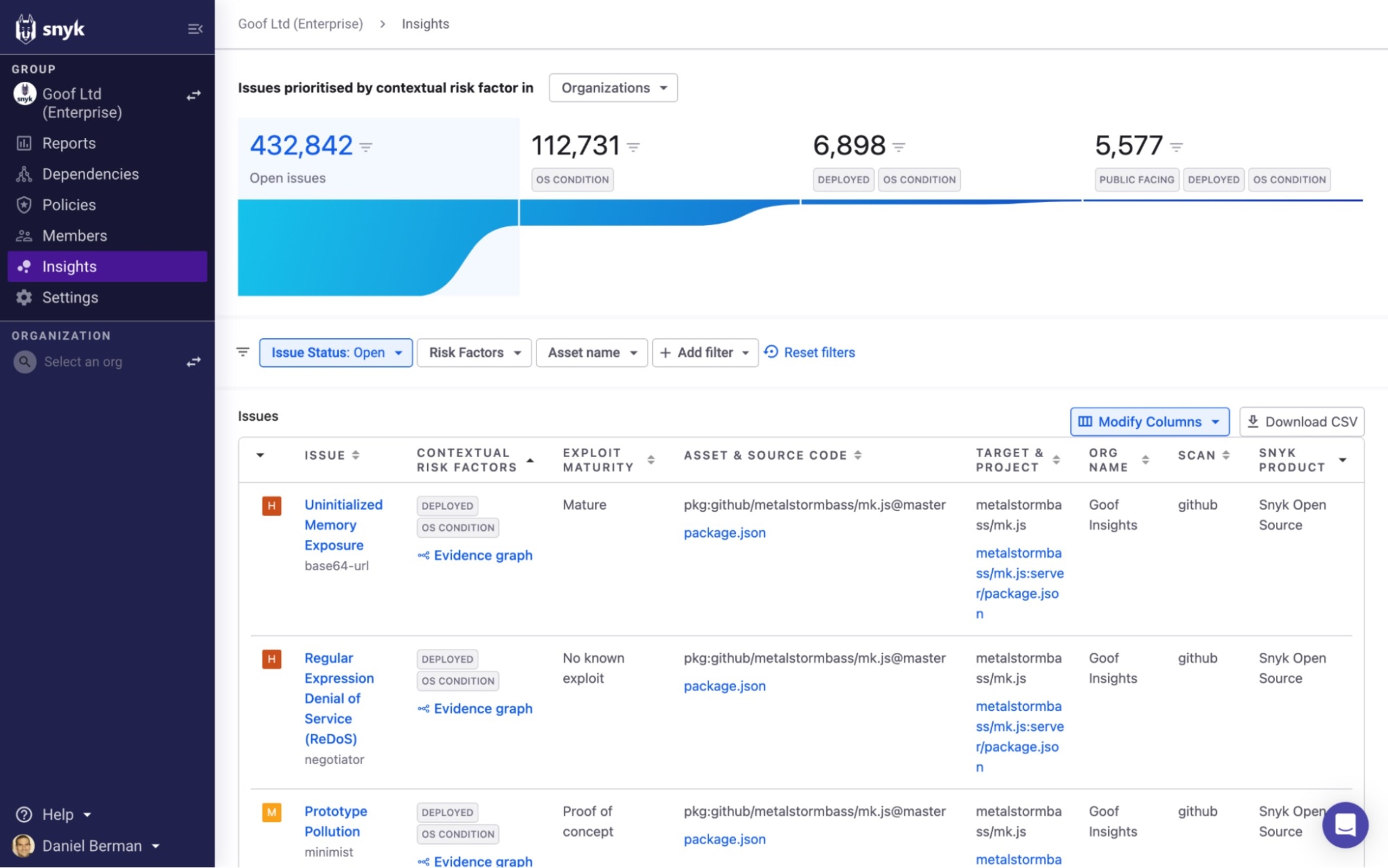
At the top of the page, a funnel view provides you with a quick breakdown of your issues, narrowing down based on the contextual risk factors that Insights supports. The funnel includes four segments:
Open issues: All open issues identified by Snyk.
OS Condition: All open issues identified by Snyk that apply to the operating system.
OS Condition & Deployed: All open issues identified by Snyk that apply to the operating system and that are associated with a deployed container.
OS Condition, Deployed & Public facing: All open issues identified by Snyk that apply to the operating system, are associated with a deployed container, and have a configured path to the internet.
Clicking on any of the segments in the funnel will automatically filter the list of issues based on the relevant risk factors.
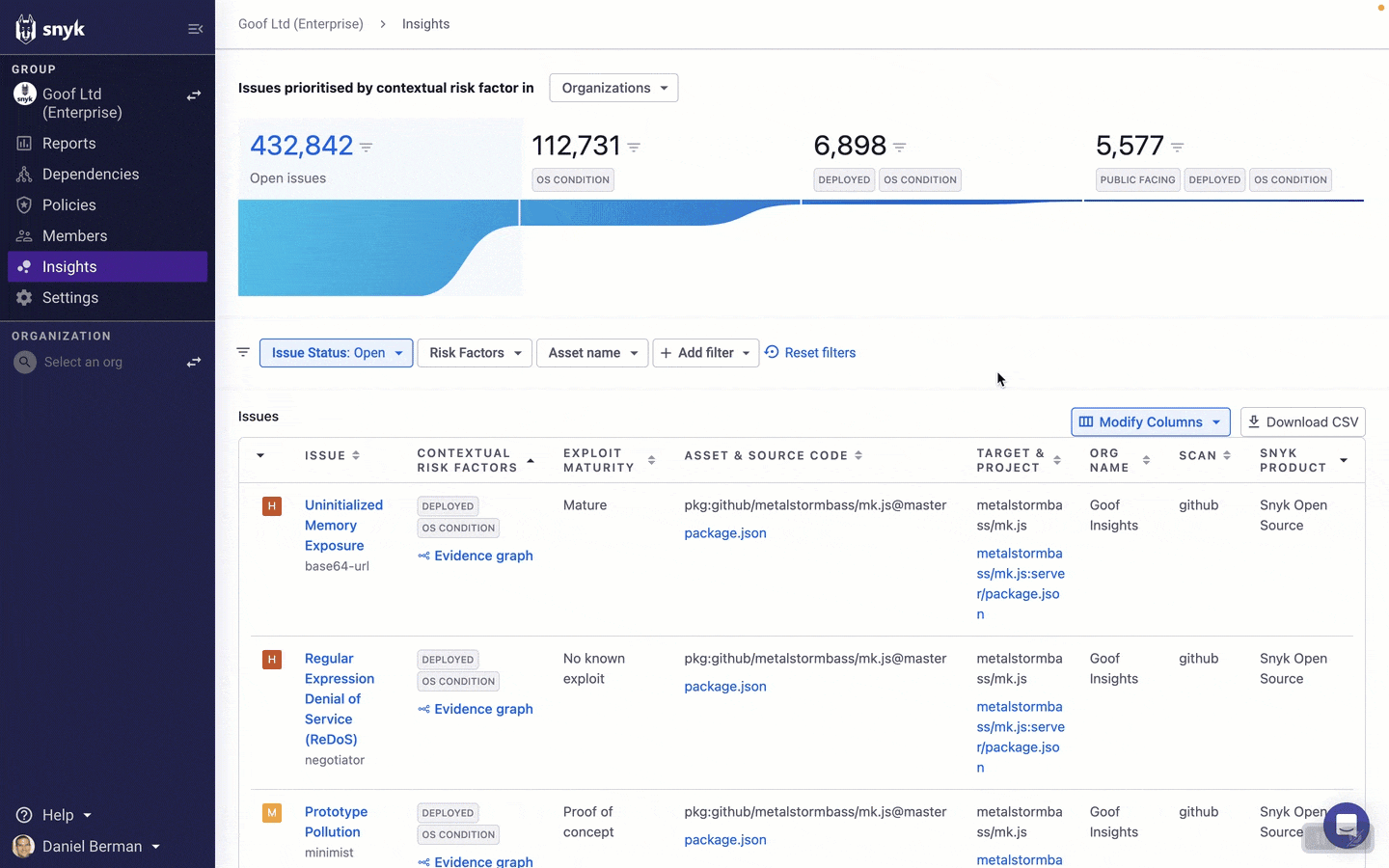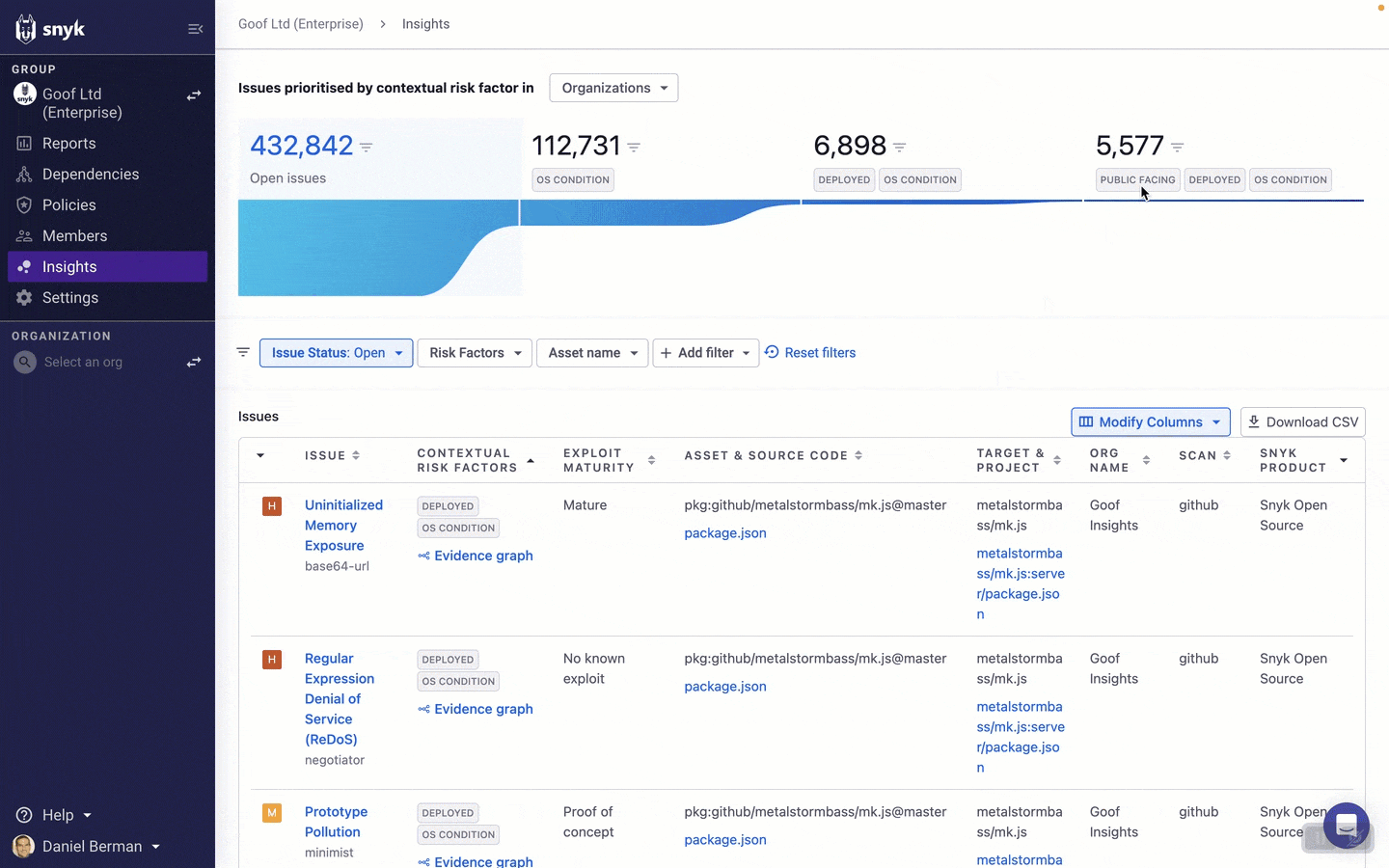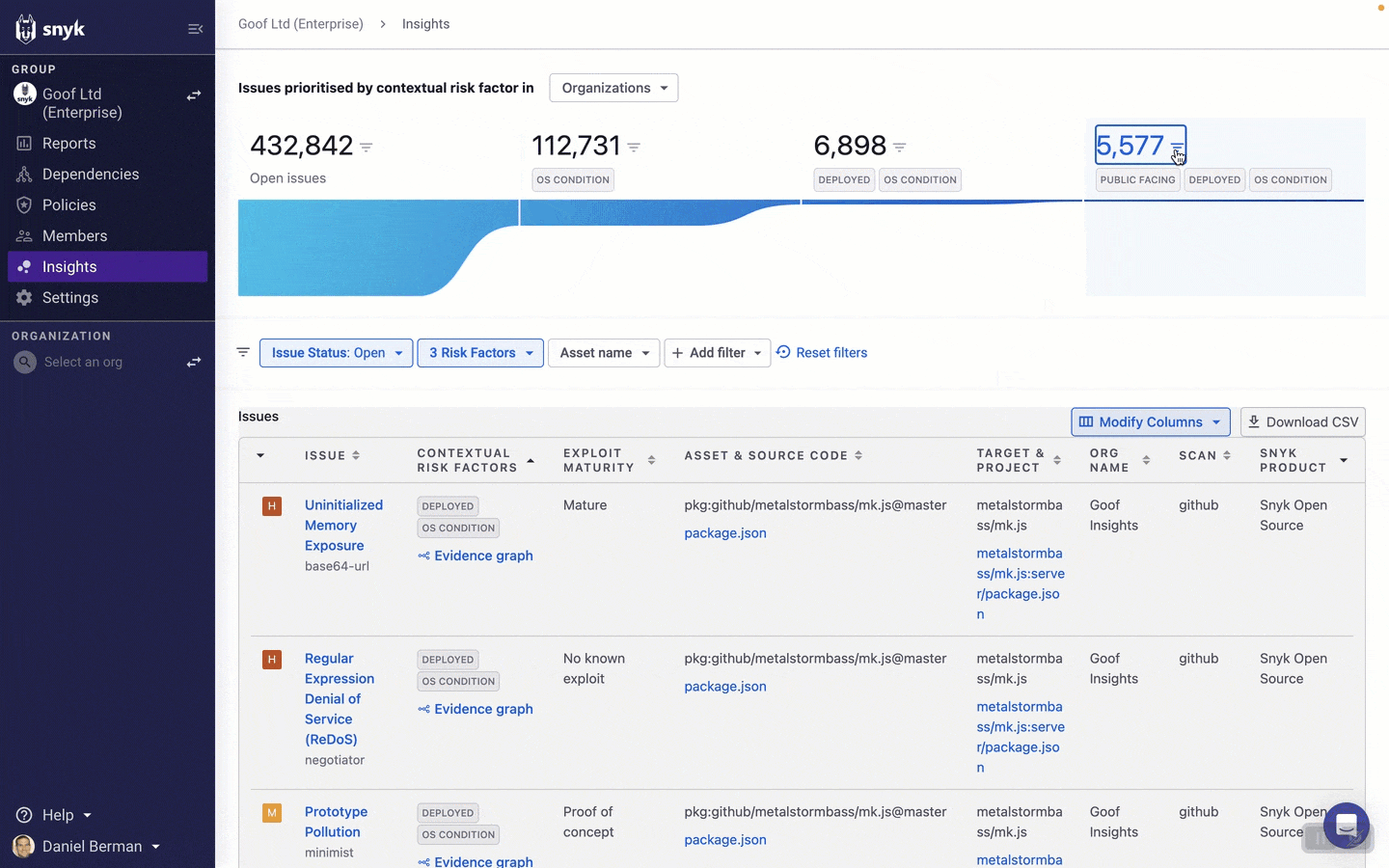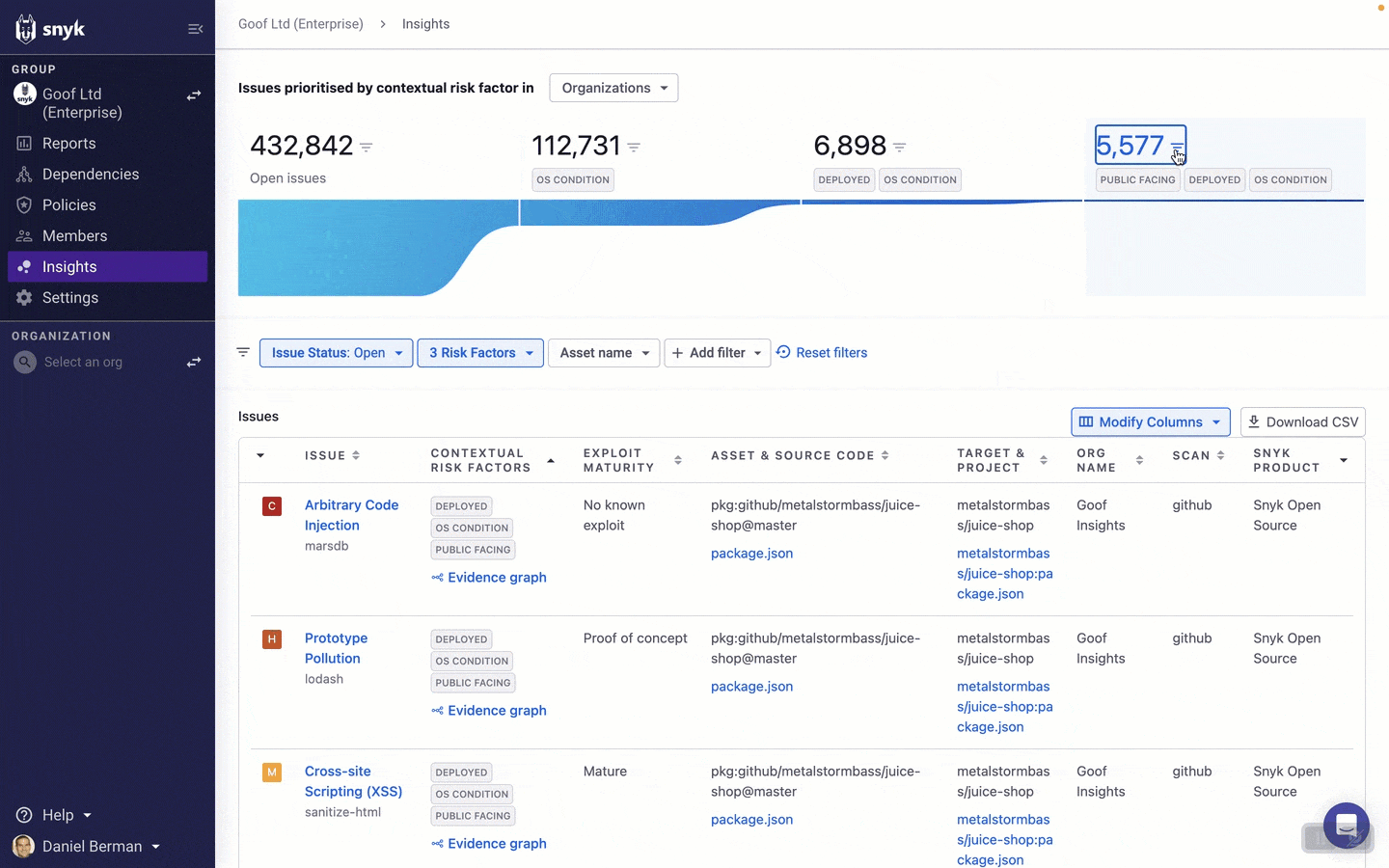
You can then continue to explore issues using an extensive list of filters that Snyk provides on the Insights page. This will help you further narrow the list of issues to focus your fix efforts on.
How you decide to filter the list of issues on the Insights page will depend on your issue management practices, internal policies, and specific circumstances, but let’s take a look at some useful examples.
Prioritizing your most important assets
Based on the model Insights builds of your application, Snyk now has a better understanding of the different assets it is comprised of. Filtering by Asset name, you can choose to narrow down the list of issues to those that pertain to a specific asset or resource. For example, if you would like to focus developers on a service that is business-critical because it is handling sensitive information, you could select the relevant container from the filter menu.
Prioritizing Critical and High severity issues
Critical and High severity issues that are applicable to your operating system, deployed, and public facing pose a high level of risk to your organization and so narrowing down on these issues using the risk factors that Insights provides and the severity filter is a powerful tool. For open source issues, further filtering based on whether there is a mature exploit for not will help you narrow your focus even further.
Prioritizing specific teams
A lot of large Snyk customers have their different business units or application development teams organized into different Snyk Organizations to help them better manage security at scale. Since Insights is available on the Snyk Group level, you can easily filter by Organization using the filter above the funnel view of from the filter bar above the list.
Once you’ve filtered down the list of issues using the available filters, you can share this view with others in your organization by clicking the Download CSV button.
Understanding risk with context
Narrowing down the list of issues using the risk factors Insights uncovers will help you zoom in on those issues posing a greater risk.
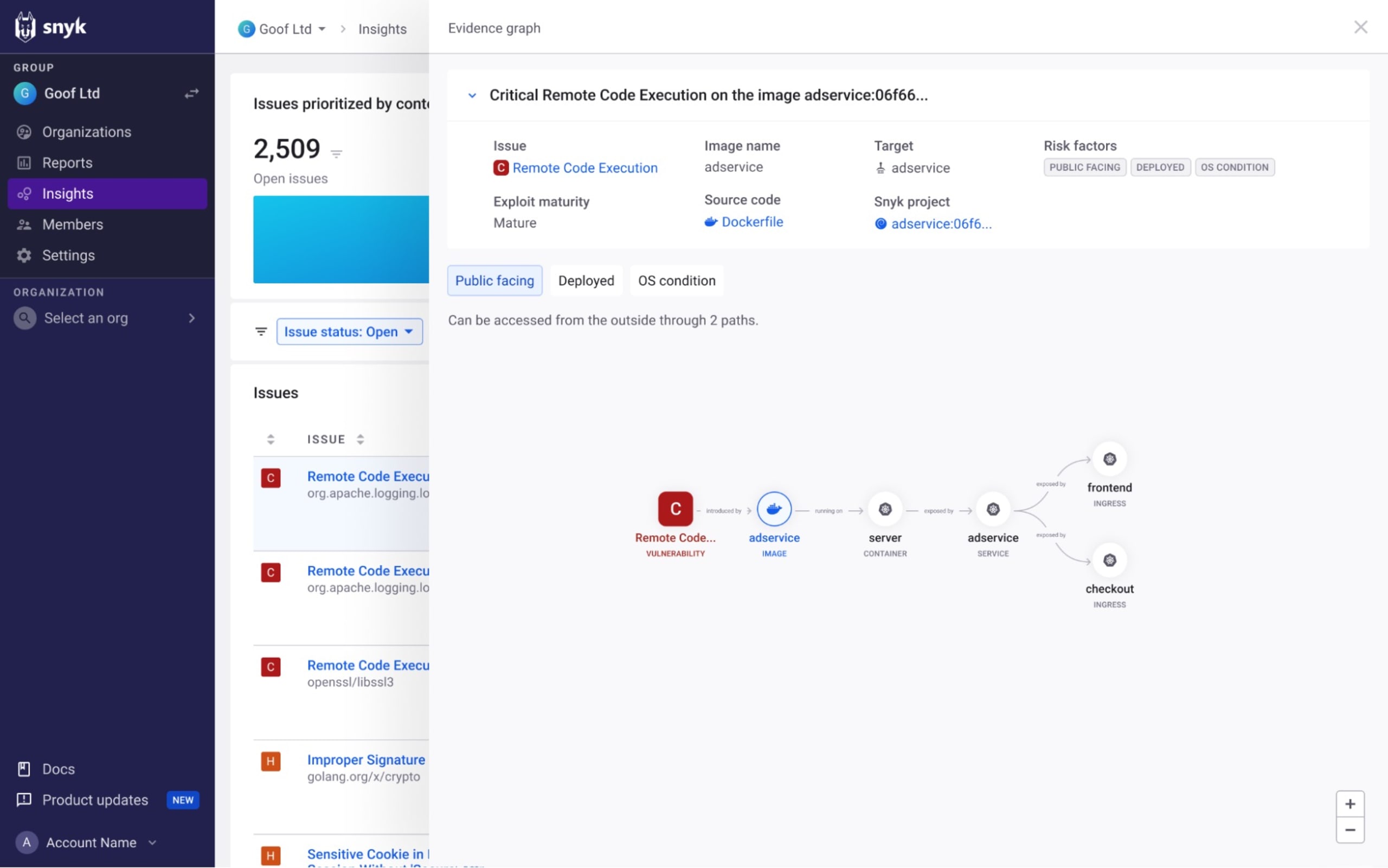
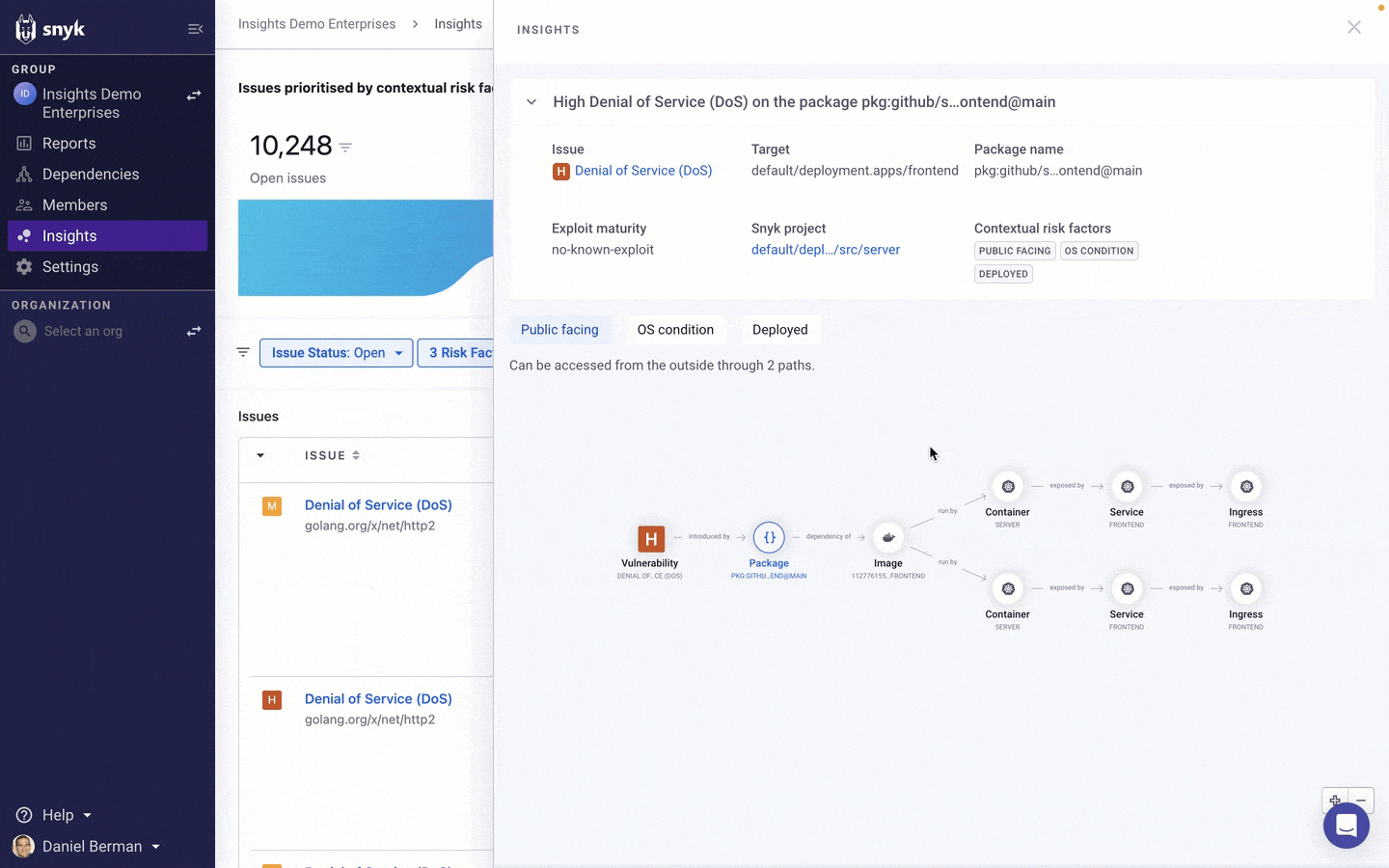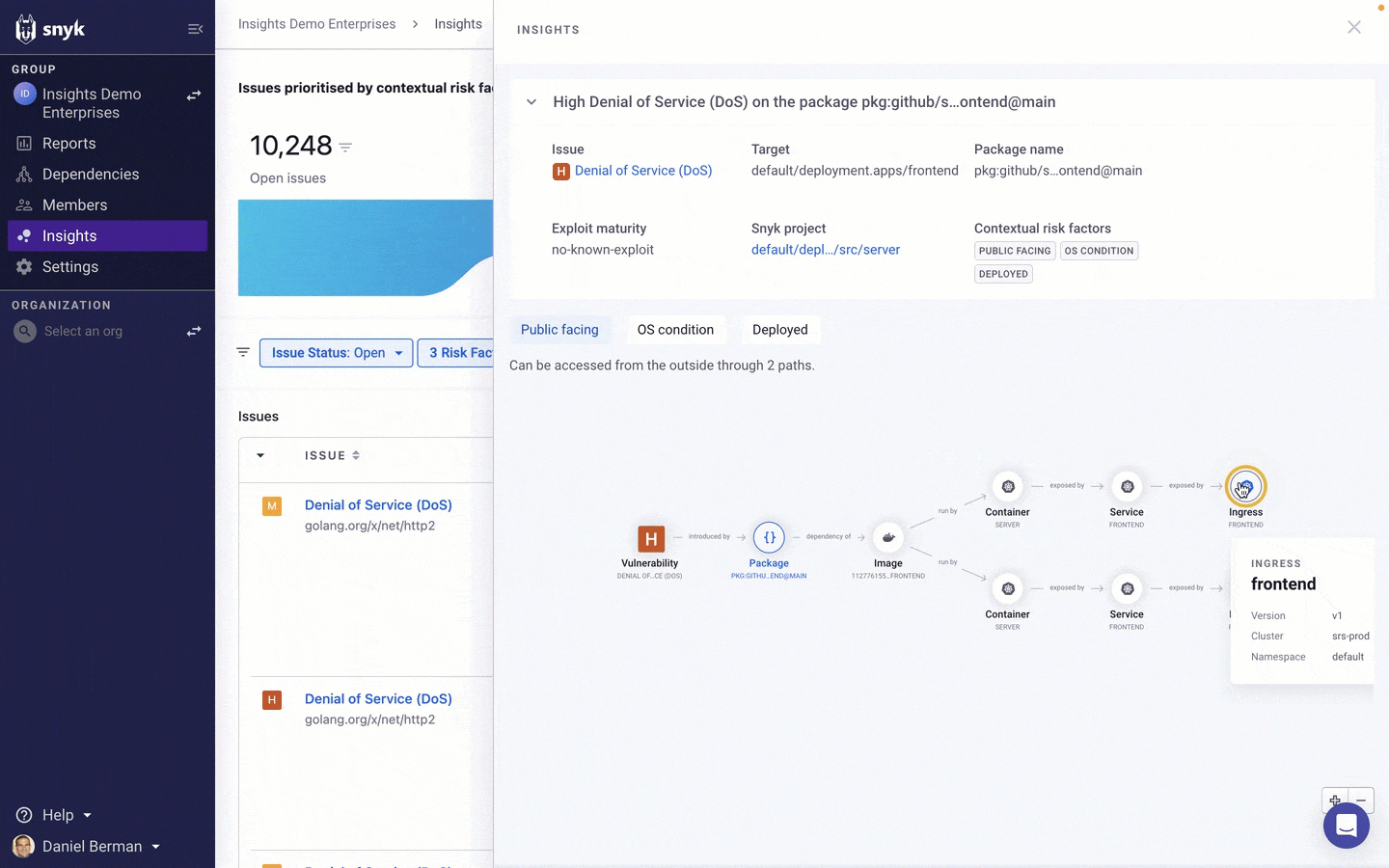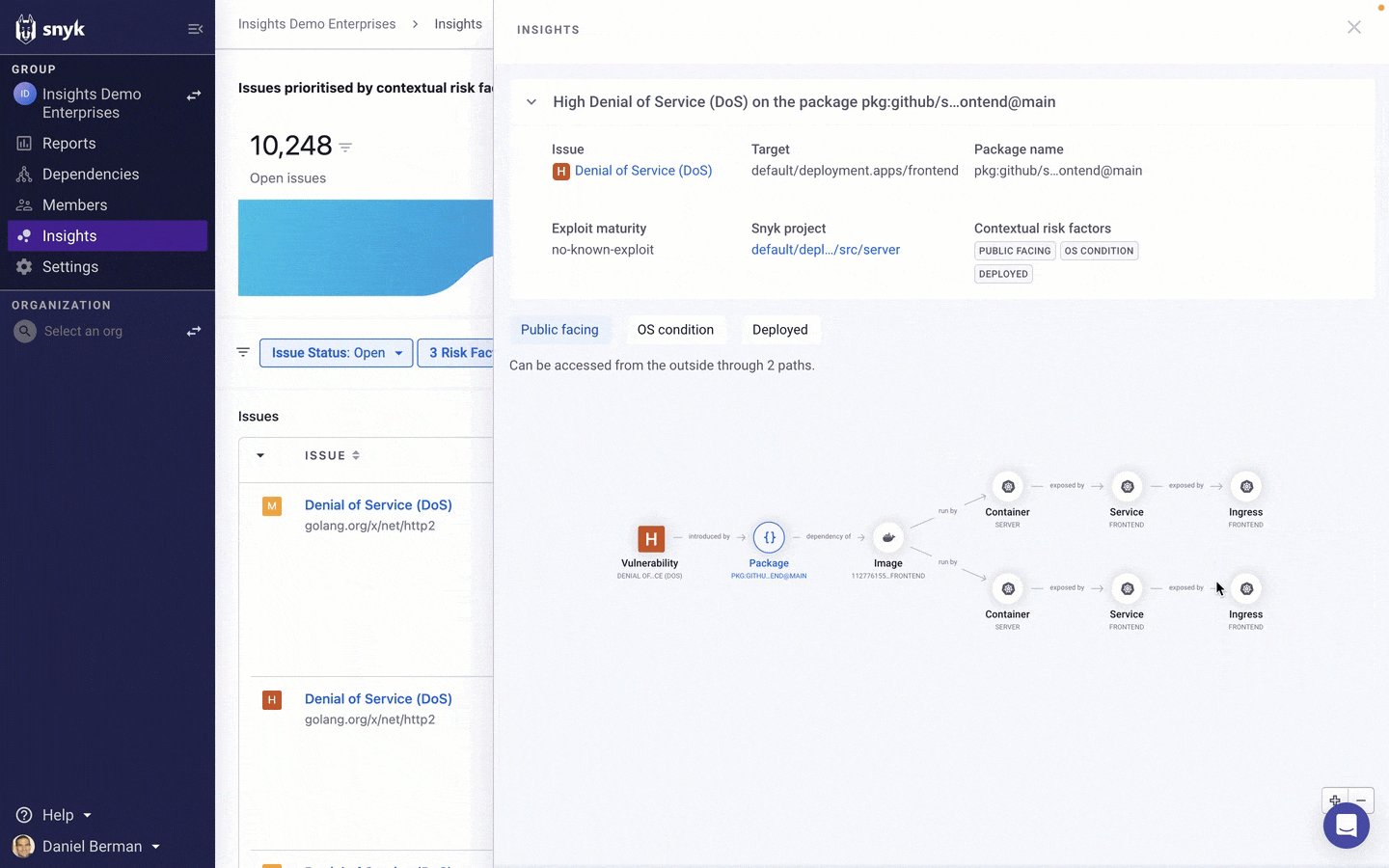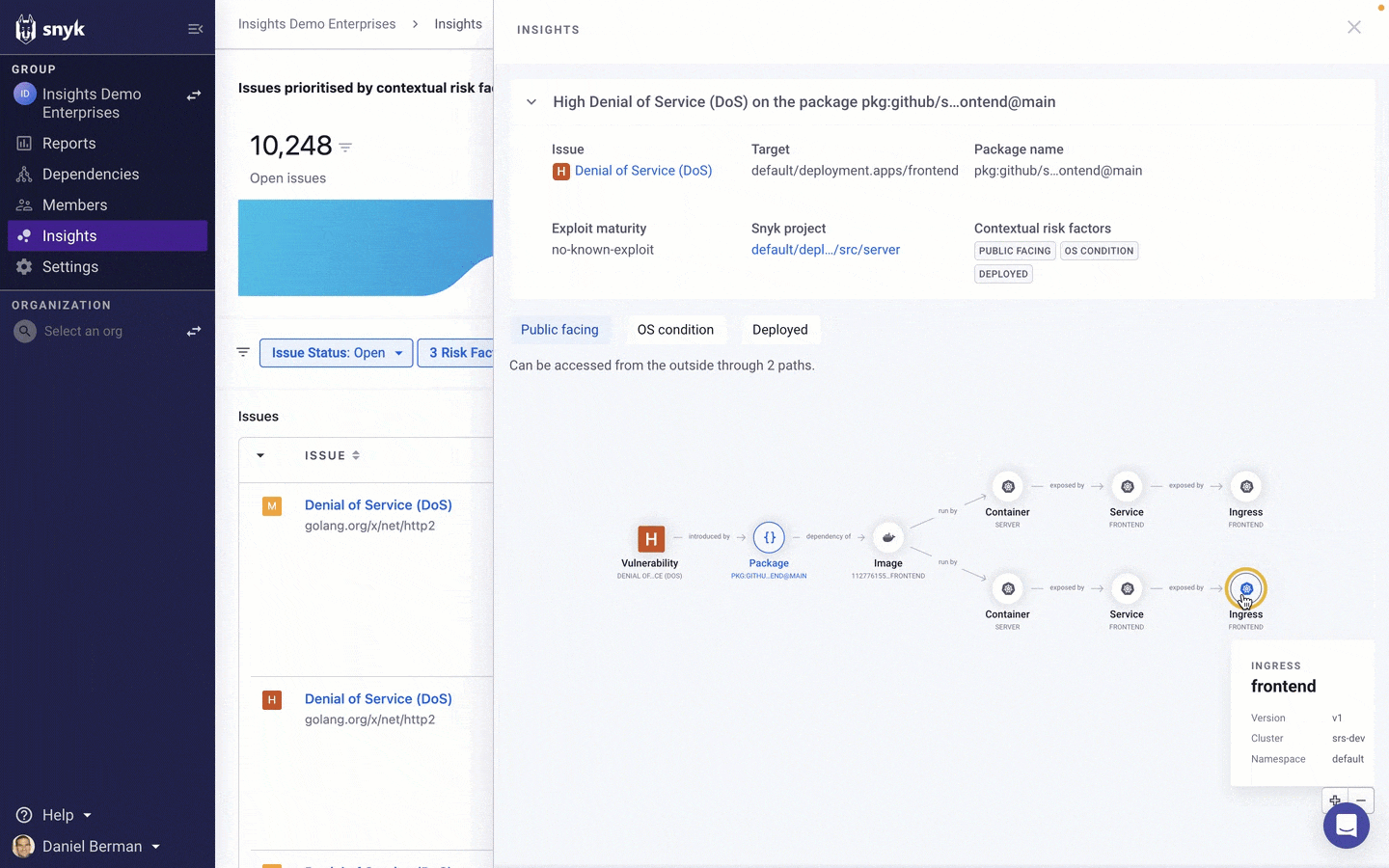
But to help you understand more about these issues and how the application configuration contributes to the increased likelihood of this issue being exploited, Insights provides an evidence graph that describes the different assets making up your application and how they relate to the issue in question.
Under the Contextual Risk Factors column, click the Evidence graph link:
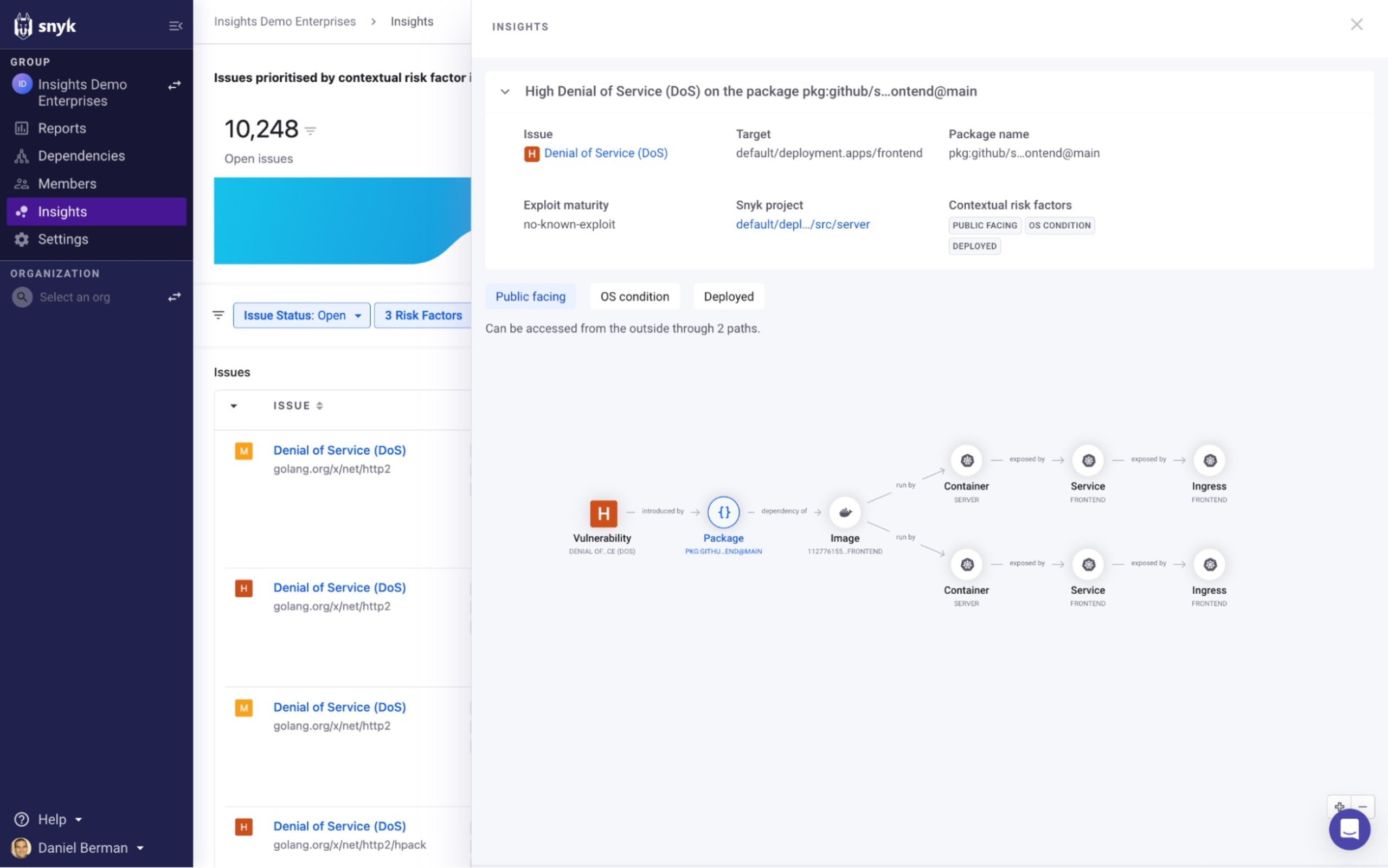
In the example above, Insights has found that a High severity vulnerability was identified in an source package that is associated with two deployed containers, each with a configured ingress path to the internet, which enables us to understand how the application configuration is contributing to the increased likelihood of this issue being exploited.
The graph itself is interactive — you can zoom in and out and drag the elements around to order them in a different way, and selecting them provides additional information. In this case, we can see that one of the containers is running in a development Kubernetes cluster while the other container is running in our production environment.
Insights also provides the link to the source code, helping you quickly understand who owns the code introducing the issue and how to fix it.
Together, all this context is a powerful tool to have when explaining the importance of fixing the issue to the development team - it explains the risk, how it is introduced, and more importantly - where the fix needs to be applied and by whom.
How to resolve the issue now that you understand the risk it poses is your next step. Clicking on the issue in the Issues list, the issue is opened on the Projects page, where you might decide to open a Jira ticket, open a fix pull request, or even ignore it if the context Insights provided you with suggested that the issue actually does not pose enough risk to warrant immediate action.
Building towards an easier way to manage application security
While continuous delivery and cloud native technologies enable organizations to deliver software faster and maintain their competitive edge, they are also making it increasingly difficult for them to manage their application security posture.
Leveraging CI/CD, developers are introducing new code with growing frequency and speed. Applications are more complex than ever before, comprised of a growing list of components with intricate relationships between them. Likewise, the number of security issues in backlogs continues to grow, obscuring visibility for security and creating frustration for developers.
To successfully overcome these challenges, a security program must be built upon an automated, continuous, and holistic understanding of the modern application. This understanding consists of not only the security issues an application introduces, but also the various assets it is comprised of, as well as the development processes involved in writing, building, and deploying it. Equipped with this understanding, development teams are able to make better secure design decisions early and throughout development, and security teams are able to better identify and prioritize the top risks for the organization.
Insights seeks to provide you with this understanding. Check out the on-demand recording from SnykLaunch for all the details.
Insights will be available in open beta for customers on the Enterprise plan starting July 12th. If you’re interested in trying Insights out, please reach out to your Snyk account representative to validate the requirements and then sign up for the beta.