Want to try it for yourself?
Static Application Security Testing (SAST) Tools
Pros, cons and implementation of SAST tools
Every developer's goal is to keep their source code secure without overthinking it. But developers often don't have the security background to avoid insecure programming patterns, know how to use secure APIs, or detect interfile issues that include several parts of an application not developed by a single team.
That's why it is perceived as best practice to have static application security testing (SAST) as part of an overall application security solution and strategy. SAST analyzes your source code for security vulnerabilities, so you don't have to.
Keep reading to discover:
What is Static Application Security Testing (SAST)?
Static application security testing (SAST), a subset of static code analysis, analyzes source code to identify vulnerabilities that could leave applications open to malicious attacks. SAST uses vulnerability scanning techniques that concentrate on the source code and bytecode to detect security issues like injection attacks or memory management issues. The scan is performed before the code is executable, which is why it is known as white box testing. By utilizing SAST tools, your applications are better protected from potential security threats.
Integrating SAST early in your continuous integration (CI) pipeline or into the integrated development environment (IDE) using a plugin while coding enables the tool to check your code in real-time and prevent security issues from entering the codebase.
5 benefits of static application security testing
SAST offers numerous benefits for the software development lifecycle (SDLC), like improved code quality and reduced overall cost and effort to ensure application security.
Here are five more benefits:
Scans early in development: Most SAST tools work solely on source code, checking it against best practices. This means SAST can be applied while writing your code. IDE plugins for SAST tools are common and catch problems before anything enters version control.
Indicates problematic code locations and explains the issue found: SAST shows you the exact location of every vulnerability and explains the data flow. This makes it simple to understand and remediate each one.
Requires no test cases: Some AppSec tools, like dynamic application security testing (DAST), require you to decide what to test, while SAST tools will simply apply all its rules to your codebase.
These rules can be manually implemented by the SAST tool creator or a community. These rules are often based on numerous projects and years of programming experience, meaning a rule developer must be knowledgeable in different fields. These rules allow you to catch vulnerabilities you didn't even know existed.Requires no app execution: SAST works on the source code before the application runs, therefore, SAST scans are much quicker than other application testing suites.
Easy to automate: Source code files can be scanned automatically at any point of the SDLC. This means SAST can be used as a security gateway at any point.
3 limitations of static application security testing
Despite the benefits, static application security testing also has limitations, including the inability to detect certain vulnerabilities. Other major limitations include:
False positives and false negatives: SAST tools interpret the source code and need to apply certain assumptions. This might lead to SAST tools finding issues that are not true which is called a false positive — a false finding. Legacy SAST tools could have a 50 to 80% false positive rate, making it hard to find the signal in the noise and the ROI on SAST questionable, so it's important to use a modern SAST with better accuracy.
Missing context: Unsanitized user input is a huge security risk and should be fixed whenever entering a software component. Unsanitized input on the front end is often fixed on the backend, mitigating the risk. This happens because frontend and backend code aren’t always in the same repository, meaning that a SAST tool won’t detect the sanitation and prompt the developer to fix a nonissue.
Language dependency: SAST has a strong code dependency. For prevalent programming languages (e.g., Java and C#), plenty of SAST tools are available, but for more niche languages (e.g., ReScript and Nim), there are very few SAST tools out there.
SAST vs. other AppSec tools
When it comes to application security, several tools are available, so it's critical to understand the differences between SAST and other application security testing tools to determine which is the best fit for your organization.
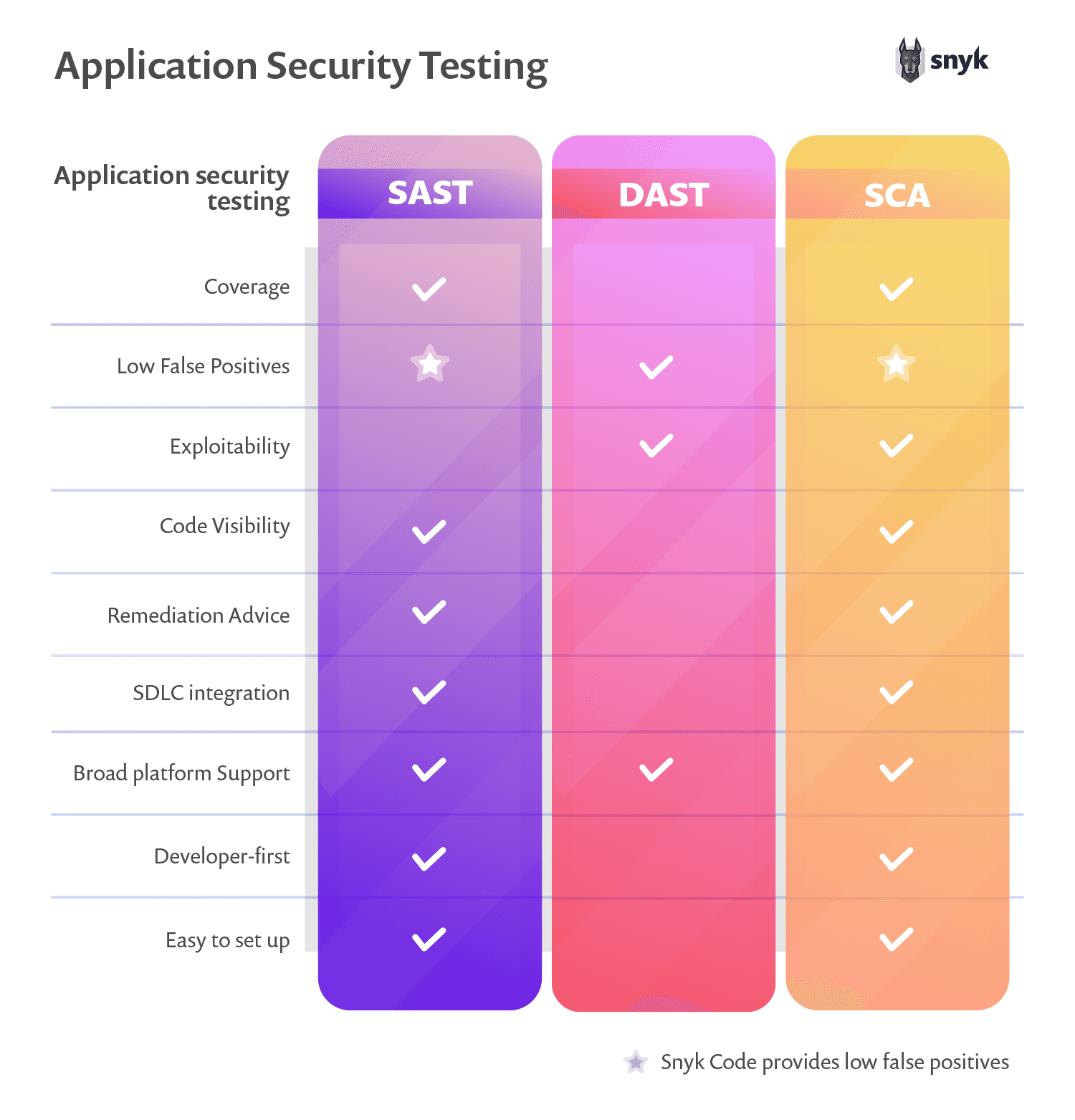
SAST vs. DAST
If SAST is white-box testing, then DAST is a black-box testing method. DAST tests applications in runtime and is applied later in the CI pipeline. DAST is a good method for preventing regressions, and unlike SAST, it is not programming language specific.
Fuzzing is a DAST method that stresses an application to cause unexpected behaviors, crashes, or resource leaks. This allows developers to understand the behavior and vulnerabilities of the application comprehensively.
Read more about SAST vs. DAST, the difference, and how to combine the two for optimal results.
SAST vs. interactive application security testing (IAST)
Interactive application security testing (IAST) is a newer approach to application security testing that provides real-time feedback on potential vulnerabilities in an application.
IAST is considered very accurate, as it combines elements of SAST and DAST and provides visibility into the code and the application runtime environment.
The interactive nature of IAST also allows for more efficient remediation of vulnerabilities, as developers are provided with specific details about the issue and can address it directly within their workflow.
SAST vs. software composition analysis (SCA)
Software composition analysis (SCA) focuses on third-party code dependencies in the application. It discovers more details about open source components than SAST can, such as licensing details and version history — making SCA a better fit for securing third-party dependencies.
SCA is very effective in applications that use many open source libraries, it’s common practice to use a lot of open source libraries during development, so SCA is becoming more important than ever, but this method is also programming language-dependent.
Read more about SAST vs. SCA and how to combine them to release secure software.
SAST and other AppSec tools
SAST, DAST, SCA, and IAST are all essential application security testing types that offer different perspectives on the security posture of the development lifecycle.
These tools complement each other, so employing them together will give you a comprehensive assessment of your application's security.
How do SAST tools work?
SAST is a technique used to evaluate source code without actually executing it. It involves examining the program's structure and syntax to identify potential issues and errors, such as coding mistakes, security vulnerabilities, and performance bottlenecks. The process involves parsing the source code, building an abstract syntax tree, and applying various analysis techniques to detect issues. By providing early feedback on potential issues in the code, SAST can help improve software quality and reduce the likelihood of errors and security vulnerabilities.
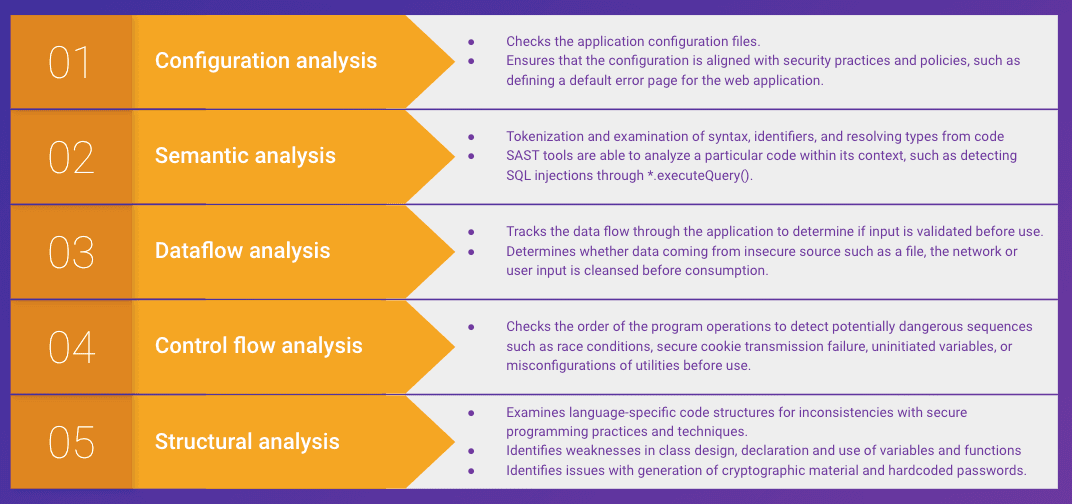
What vulnerabilities can SAST tools find?
SAST tools detect a range of security incidents and vulnerabilities in source code, including:
Dataflow issues
Semantic errors
Misconfigured settings
Control flow problems
Structural flaws
Memory issues
7 stages of a security application testing scan
The seven stages of a SAST scan are:
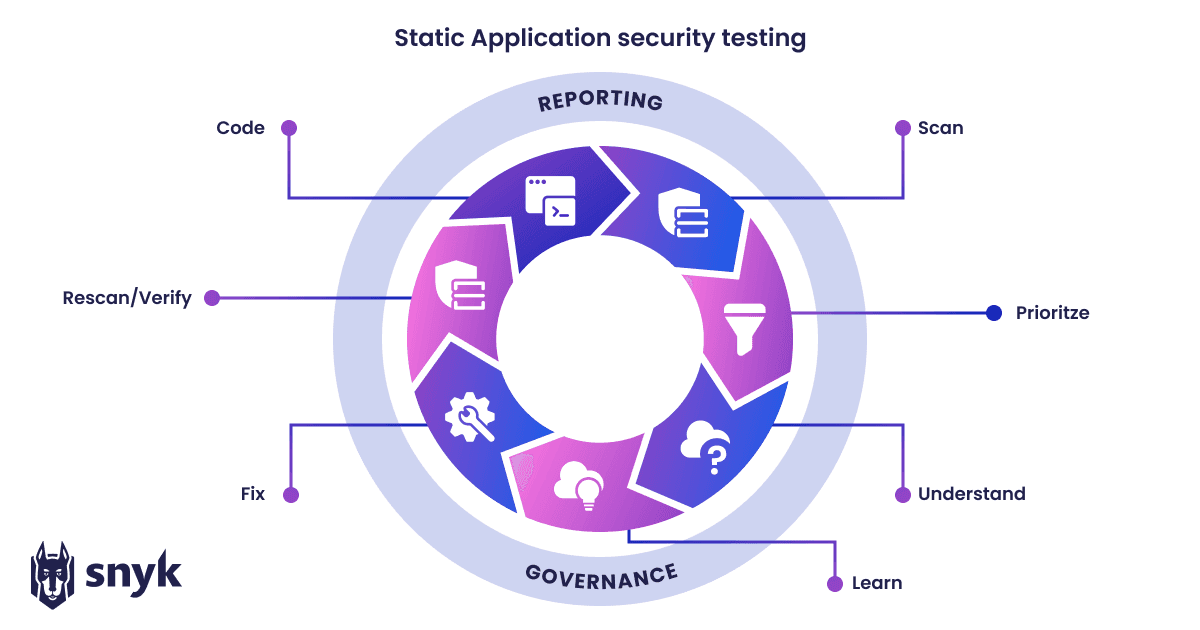
Scan your code as it’s being written.
Prioritize and triage based on the severity and impact of the vulnerabilities found
Understand the nature of the vulnerabilities found by reviewing scan data and assessing the associated risk level.
Learn from the scan findings to prevent similar vulnerabilities in the future. This includes improving code quality, adopting secure coding practices, and implementing developer security training.
Fix vulnerabilities found in the scan by patching the code or implementing other remediation measures.
Rescan to verify that the fix has worked.
Continue coding while integrating security into the development process to prevent vulnerabilities from being introduced in future code.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
How to find the right SAST tool to secure the software development lifecycle (SDLC)
SAST is a crucial part of securing the software development lifecycle, so it is essential to choose a tool with certain features, like:
Developer-friendly interface with a UI that is easy for non-security staff to use and understand.
Fast scanning capabilities to avoid slowing down the development process.
Low false positive rates, as this reduces the time and effort required for developers to review and verify results manually.
Simple integration into your existing CI/CD pipeline.
With these types of SAST tooling features, organizations can ensure that their software is developed with security in mind, reducing the risk of vulnerabilities and increasing the overall security of their applications.
Developer-first SAST with Snyk
The ability of SAST tools to catch security problems early in the development process means that even in deadline-driven environments, developers don’t need to constantly worry about following security best practices while coding. However, depending on how late in the software development life cycle you run a SAST, it takes a lot of effort to get it up to speed.
Conventional SAST tools will yield many false positives, which developers need to weed out. And if the system is coded in a niche programming language, there might not even be a SAST tool available to help with your security issues. Developer-first SAST tools successfully address these issues and offer a more seamless and efficient process, making it a tool every security-conscious developer and org should have in their toolbelt.
Snyk Code is a developer-first SAST that offers real-time scanning right from your IDE, industry-leading accuracy, actionable fix advice in-line with your code, and a cutting-edge knowledge base that's powered by human-in-the-loop AI. Start using it for free today.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
Up Next
Application Security Testing (AST) - Top Questions Answered
Application security testing is a key step in the SSDLC. Learn more about types of application security testing, app sec testing tools, and get started with building secure apps.
Keep reading



















