Prototype pollution in express-fileupload
24. August 2020
0 Min. LesezeitWelcome to the Snyk Monthly Vulnerability Profile. In this series, Snyk looks back on the vulnerabilities discovered by or reported to our Security Research Team. We choose one noteworthy vulnerability from the past month and tell the story behind the discovery, research, and disclosure of the vulnerability. We highlight the researchers, developers, and users who are helping identify and remediate vulnerabilities across the open source community.
This month we’re looking at a prototype pollution vulnerability discovered in express-fileupload.
Vulnerability: prototype pollution in express-fileupload
CVEs assigned: CVE-2020-7699
Snyk Analyst: Sam Sanoop
Discovered by: a researcher who operates under the handle po6ix
A prototype pollution vulnerability was recently discovered in the popular express-fileupload package and logged as an issue in the GitHub repository.
The issues feature can be a handy way for developers and security researchers to notify package maintainers of bug or security vulnerabilities they uncover. However, while this information is publicly viewable, it is not widely distributed to the security or development communities who may need to be aware of the problem.
So, how can we ensure serious security vulnerabilities logged as issues in the repository are communicated more widely? This story about prototype pollution in express-fileupload is a demonstration of how Snyk’s research team is helping to address this concern.
Digging into the specifics of the prototype pollution vulnerability
On the 25th of July, 2020, a researcher who operates under the handle po6ix, logged an issue to the GitHub repository for the express-fileupload package. The issue describes a prototype pollution vulnerability that the researcher discovered in the package. It additionally demonstrates how the vulnerability could be used to achieve remote code execution through a function designed to parse file path information. The researcher also published a blog post on their website that details the vulnerability along with providing proof-of-concept (POC) demonstrations.
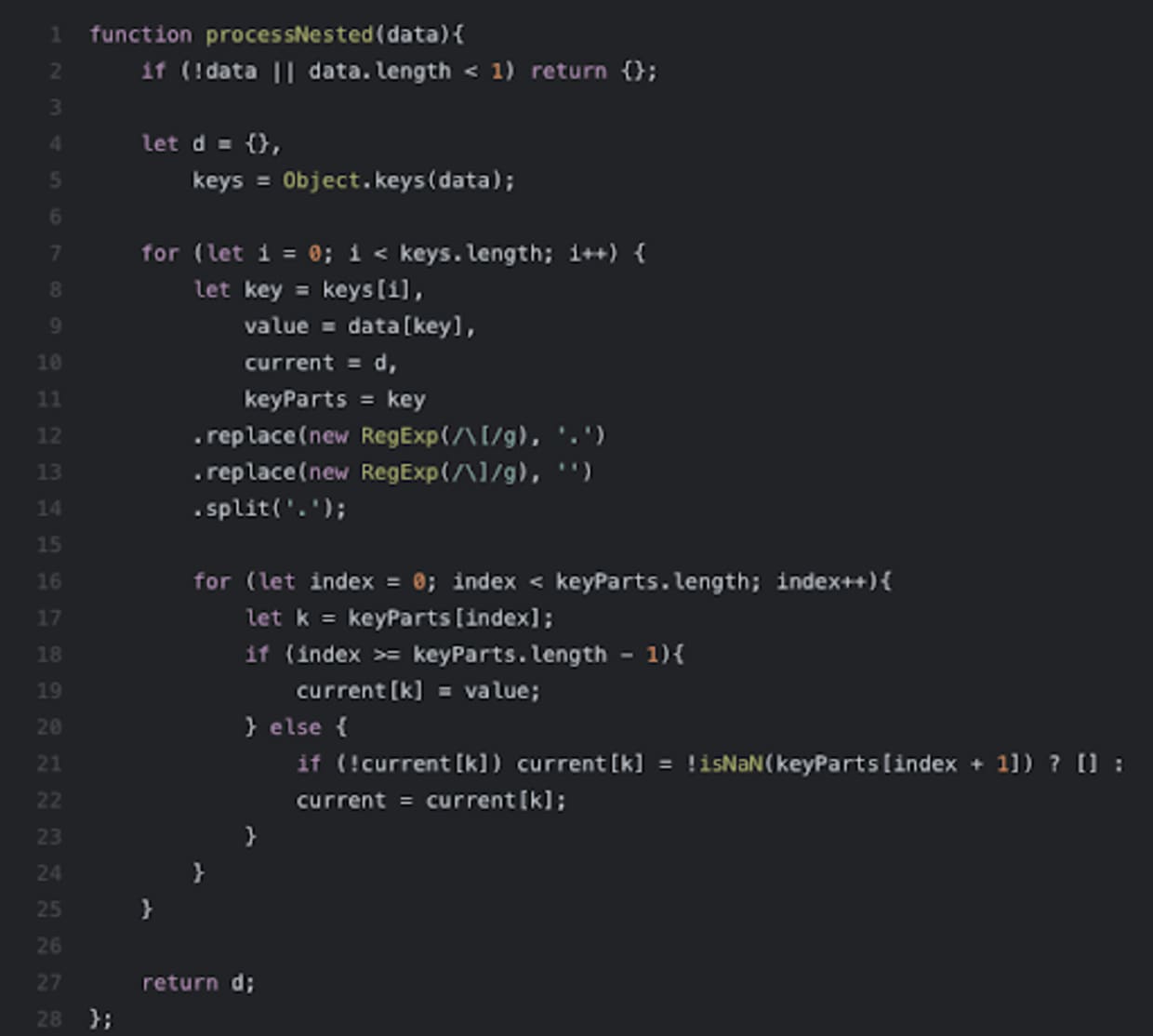
Snyk’s Security Research Team regularly searches for issues in public GitHub repositories that describe potential security flaws. The research team’s attention was drawn to a series of issues that po6ix had logged in a very short time which included the vulnerability in the express-fileupload package. Snyk security analyst, Sam Sanoop, reached out to the po6ix to gain additional insight into the vulnerability and to offer Snyk’s assistance in assigning CVEs to the multiple vulnerabilities the researcher had discovered.
After a discussion with po6ix about the vulnerabilities, Sam took the proof-of-concepts that were listed in the blog post and used them to reconstruct the attacks. In this way, Snyk was able to confirm the depth and applicability of the vulnerability.
After confirming the vulnerability details, Sam calculated a CVSS score of 7.5 for the vulnerability—in part because of the remote nature of the attacks. According to po6ix’s blog post—as of the end of July, 2020—the express-fileupload package has nearly 8 million downloads. The combination of the severity of the vulnerability and the vulnerable package’s popularity meant this was a particularly concerning discovery.
Sam assigned CVE-2020-7699 for the vulnerability and created a detailed report, adding it to the Snyk Vulnerability Database. The original researcher, po6ix, is appropriately credited with the discovery in the Snyk Vulnerability DB as well.
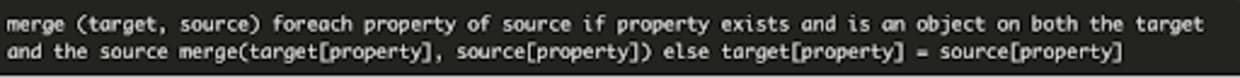
In the meantime, the package maintainer did implement a fix for the security vulnerability in version 1.1.8 of the package. However, the issue wasn’t fully remediated and another GitHub user opened a follow-up issue. In the follow-up, they noted that a Denial-of-Service vulnerability still existed within the package using elements of the same attack. On the 6th of August, 2020, the maintainer released version 1.1.10 of the package which Snyk has confirmed successfully remediates the vulnerability.
This story is just one example of how the Snyk research team works with the developer and security communities. Our goal isn’t only to make sure vulnerabilities get fixed in the packages, but rather to also ensure open communication of vulnerability information so everyone can more easily secure their software.
Did you miss our previous MVP posts? Check them out below: