XSS Attacks: The Next Wave
June 8, 2017
0 mins readHas the XSS threat died down? It’s been over 10 years since Cross Site Scripting (XSS) became big news, awareness has grown and defenses have become much more sophisticated. But recent data paints a different story:
XSS attacks grew 39% in Q1 of 2017, the biggest jump since Q4 of 2015
XSS vulnerabilities are expected to grow 166% in 2017, the biggest jump since 2012
XSS prevalence is consistently high — since 2012 around 50% of all website vulnerabilities are XSS
We recently surveyed the OWASP Top 10 security vulnerabilities in light of the top 50 data breaches of 2016. Compared to the dramatic stories of huge data breaches, XSS attacks appear to have a much smaller impact. In practice, however, XSS attacks are likely to affect many more users and websites, only instead of leaking data in one fell swoop, they compromise users one at at time — a “death by a thousand cuts”.
In this post we’ll show the latest data on XSS attacks, vulnerabilities and prevalence, which indicate we are in the midst of a “next wave” of XSS. Finally, we’ll offer our analysis of the reasons behind the persistence and renewed growth of XSS.
A Quick XSS Primer
XSS or Cross-Site Scripting attacks (see an official definition from OWASP) occur when an attacker tricks a user’s browser to execute malicious JavaScript code in the context of a victim’s domain. Such scripts can steal the user’s session cookies for the domain, scrape or modify its content, and perform or modify actions on the user’s behalf, actions typically blocked by the browser’s Same Origin Policy.
XSS vulnerabilities enable these attacks by echoing the attacker’s script on their page, thus executing it in the context of the victim domain. For instance, an attacker may post a comment that includes a malicious script on an article through an XSS vulnerability. The attacker’s script now compromises every visitor to the page.
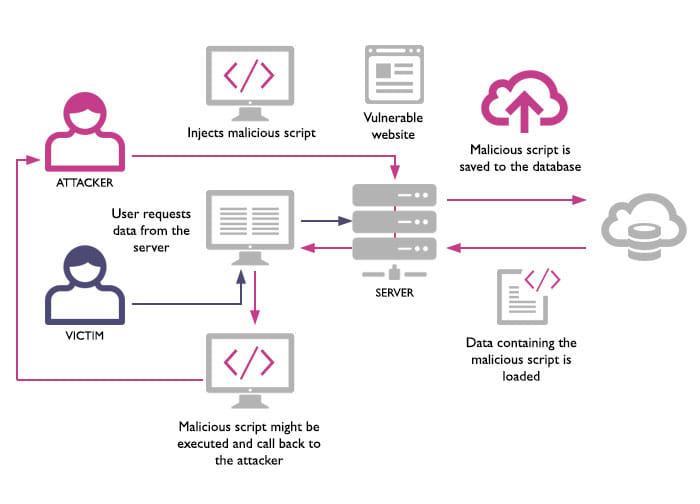
The example above describes a “Persistent XSS” vulnerability. Another common type of XSS is called “Reflected XSS”, in which the website echoes back a portion of the request. The attacker needs to trick the user into clicking a malicious link (for instance through a phishing email or malicious JS on another page), which triggers the XSS attack.
Lastly, “DOM-based XSS” attacks occur purely in the browser when client-side JavaScript echoes back a portion of the URL onto the page. DOM-Based XSS is notoriously hard to detect, as the server never gets a chance to see the attack taking place.
XSS Attacks on the Rise for a Year; Grew 39% in Q1
Akamai’s State of the Internet Security Report, published quarterly, shows that XSS attacks declined in early 2016, but are on the rise again and grew dramatically in the first quarter of this year. According to Akamai, XSS attacks now account for 10% of all attacks on web applications.
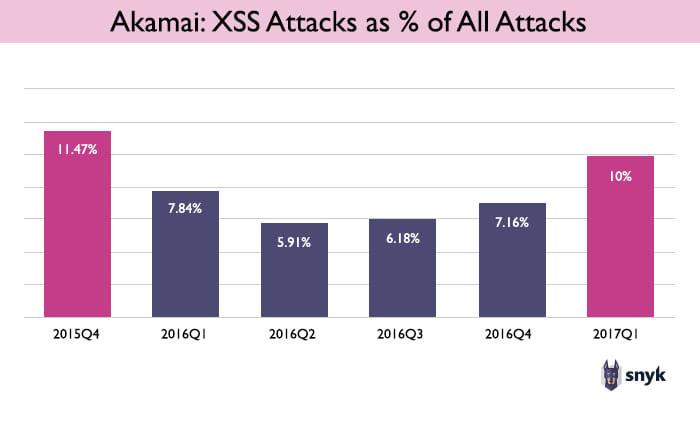
Before 2015, the Akamai report did not state the number of XSS attacks, making it difficult to extend this timeline backward. However, data from the Imperva Web Application Attack Report, a study of 297,954 attacks protected by Imperva WAF solutions, sheds some light on XSS attacks in preceding years.
Imperva reports that in the years 2013, 2014 and 2015, the average web application in their data set was attacked by XSS 8, 12, and 21 times respectively. Showing an increase of 110% in attacks from 2014 to 2015.
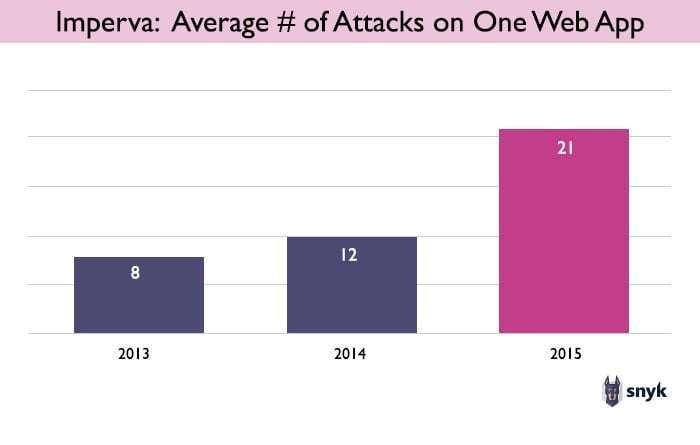
Although these are two very different data sets and methodologies, we could characterize 2015 as a “wave” of XSS attacks. And the 2017 data would suggest that we are now in the midst of the “next wave”.
XSS Vulnerabilities Expected to Grow 166% in 2017
The National Vulnerabilities Database, compiled by NIST, reports vulnerabilities in software products by CVEs, severity and many other criteria.
Looking at the gross number of XSS vulns, the past few years exhibit an uneven trend. 2014 stands out with 1,028 vulns, 66% higher than 2013. 2016 was a low year with only 472 vulns, 34% lower than 2015.
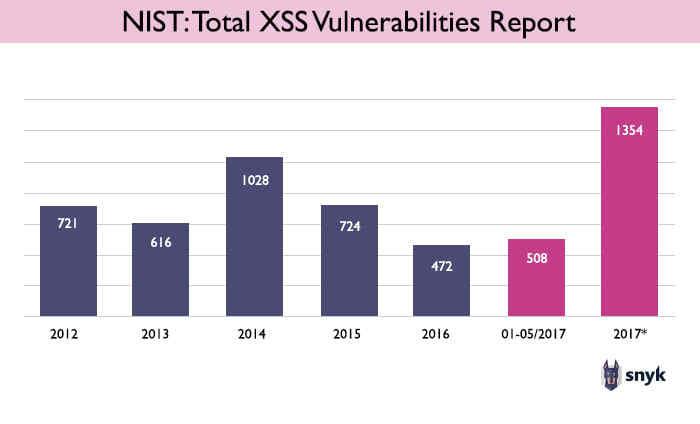
However in 2017 there is a dramatic upward trend — in the first 5.5 months of the year (up to the time of this writing), 508 vulns have been reported, more than in all of 2016. Extrapolating to the entire year yields an estimate of 1,354 vulns to be reported this year, representing unprecedented growth of 166%.
This is additional evidence of a “next wave” of XSS, leveraging unusual growth in the number of software systems reported to be vulnerable.
We should note that this data does not include DOM-based XSS attacks, which occur on the client side and are next-to-impossible to detect. In our experience, these types of attacks are growing in prevalence as single page apps become more popular and websites provide richer client-side functionality.
For example, we recently conducted a study of client-side JavaScript libraries and discovered that 77% of sites use at least one vulnerable JavaScript library. Many of those vulnerabilities are XSS, which would be difficult to detect by traditional monitoring tools.
High Profile XSS Vulnerabilities are Not a Thing of the Past
Cross-Site Scripting vulnerabilities and attacks have historically been reported at organizations such as MySpace (2005), American Express (2008), Barack Obama’s electoral campaign website (2008), McAfee, Semantec and Kaspersky (2009), Facebook (2011), the CIA and FBI (2011) and Ebay (2012).
But such “spectacular” reports are not a thing of the past. As recently as 2016, users of both eBay and Yahoo were exposed to XSS again. In July ‘16 Cisco announced an XSS vulnerability in its popular Webex platform, which was quickly fixed.
In 2017, only up to the month of May, the NIST database reported XSS vulnerabilities in certain versions of the following top-tier software systems:
IBM Rational Team Concert - CVE-2016-6037
Trend Micro OfficeScan - CVE-2017-8801
The ColdFusion programming language - 2017-3008
Cisco Prime Infrastructure - 2017-6611
IBM Financial Transaction Manager for ACH Services - 2017-1160
Atlassian JIRA - 2016-4318
This is just an anecdotal sample — many more of the 508 vulnerabilities reported in the past few months could be considered “high profile” vulnerabilities. Many may have been exploited by attackers (data which was not available to us at the time of this writing).
Prevalence of XSS Has Remained High Since 2012
Yet another study, the WhiteHat Security Statistics Report, tracked the prevalence of XSS in the years 2012-2015, by analyzing scanning and remediation data from the WhiteHat Sentinel service. The metric was XSS as a percentage of all vulnerabilities found on participating websites.
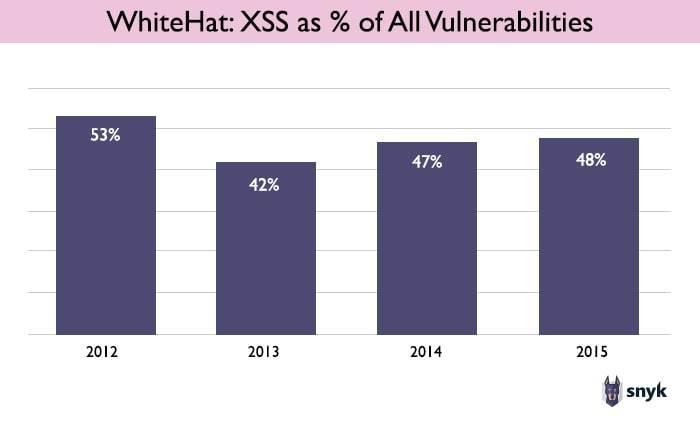
This data counters the argument that XSS is diminishing or disappearing. A full decade after the “Sami is My Hero” XSS attack on MySpace shocked the world, in 2015, almost 50% of vulnerabilities detected on websites are XSS vulnerabilities, with no significant change from previous years.
The WhiteHat study also underlines the significance of XSS compared to other vulnerabilities. Consistently, XSS is one of the top 3 vulnerabilities detected on websites, with a big gap in the prevalence percentage between the top 3 and the rest of the vulns.
Here are the numbers for 2015, with XSS at #3 with 48% of all vulns, compared to the next one down, Content Spoofing at only 25%.
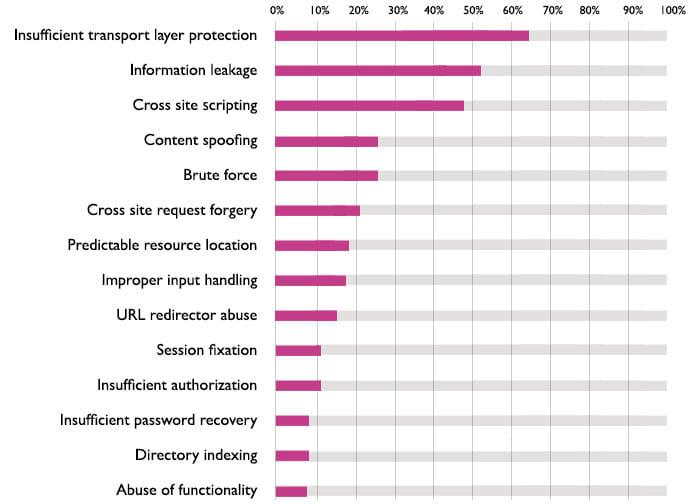
The EdgeScan Vulnerability Statistics Report supports this data with very similar numbers gathered with a similar methodology. EdgeScan reports XSS, as a percentage of all vulnerabilities, to be consistently over 50% between 2013-2015.
Our Take: XSS is a Growing and Intensifying Problem
The data show that XSS is still a very big deal, and is probably entering the next wave in terms of prevalence of vulnerabilities and number of attacks:
The proportion of XSS of all web application attacks has grown from 7% to 10% in the first quarter of 2017.
For the past four years (and more), XSS vulnerabilities have been present in around 50% of websites.
According to the NIST vulnerabilities database, XSS vulnerabilities are projected to grow 166% this year, from 508 vulnerable products and systems in 2016, to 1,354 vulns in all of 2017.
It’s important to remember that this prevalence has another multiplying factor — a single XSS vulnerability compromises the entire domain in which it occurs. As a result, one remote and rarely used page, which uses old JavaScript and is susceptible to DOM-based XSS, exposes and endangers all user data and actions for the domain it is hosted on.
At Snyk, we protect thousands of web apps from XSS and other vulnerabilities, found in the open source packages they use. Based on our experience, we can suggest five reasons why XSS is not going away (as many experts hoped) and why it might become a more difficult security problem in 2017:
Increasingly important data is transferred and actions taken via the web — making XSS attacks much more compelling for attackers to exploit.
Single Page Apps increase the amount of client side logic and user input processing. This makes them more likely to be vulnerable to DOM-based XSS, which, as previously mentioned, is very difficult for website owners to detect.
More persistence and caching of JavaScript in modern web applications, designed to support offline access and progressive web apps, lets attackers persist malicious JavaScript in a victim’s browser, keeping them compromised long after the vulnerability is fixed.
Mobile screens hide browser information, for instance by truncating URLs and query strings, making it harder for users to spot something unusual when surfing via their mobile.
Increased use of open source libraries, used by most websites and further encouraged by frameworks such as React and Angular, multiplies the reach of an XSS vulnerability in such libraries. Most websites don’t manage their dependencies and therefore remain unaware and vulnerable long after the library itself is fixed.
Application developers, website owners, and security officers should all take note — XSS attacks are a big red flag in 2017 and deserve careful attention. More than ever, applications should be developed, tested, scanned and updated with XSS flaws in mind, to reduce organizational risks and harm caused to customers and users.
Developer loved. Security trusted.
Snyk's dev-first tooling provides integrated and automated security that meets your governance and compliance needs.
