CVE-2022-24086 Vulnerability alert for websites using Magento Ecommerce
February 17, 2022
0 mins readMagento has been a much used and loved e-commerce platform since its initial release in 2008. One of the things I've always loved about Magento is its ability to grow as ecommerce businesses grow. Starting as a self-hosted version (which I've used extensively as a developer over the years), Magento now has clear support and management options available via Adobe or third party ecosystem partners.
According to Wappalyzer, there are currently 158,000 websites using Magento to power their ecommerce solutions. Global brands such as Coca-Cola and Olympus, and iconic car companies like Land Rover, use Magento to facilitate their online shopping experiences.
Distributed under an OSL (Open Software License) 3.0 license, and currently in its version 2.0 SDLC, Magento has two main offering types.
Magento Open Source, previously known as CE (Community Edition). While backed by Adobe and Magento, this version is largely supported by the community and Magento ecosystem.
Magento Enterprise, now called Adobe Commerce. This is the Adobe-managed offering, which includes different levels of Adobe support and management.
Magento has seen its share of vulnerabilities over the years with a very proactive approach to security alerts, patches, and fixes when new vulnerabilities are discovered. A critical severity for CVE-2022-24086 emerged on February 14 for an improper input validation, affecting Magento Open Source and Adobe Commerce versions greater than 2.3.4 and less than 2.4.3-p1 or 2.3.7-p2.
Understanding the CVE-2022-24086 Magento vulnerability
This vulnerability is brought about by an improper validation method during the checkout process, allowing attackers to bypass input validation methods normally used to sanitize unwanted input types.
The attack vector from CVE-2022-24086 opens up the ability for SQL and PHP object injection attacks within Magento, which can add unwanted database entries or enable remote code execution.
In application security, we’ve seen improper input validation have serious consequences. Because of the inability for the platform to recognize a combination of character types during the time of form validation, harmful sequences are allowed to wreak havoc unabated.
To get hands-on with improper PHP validation and try it for yourself, check out the Snyk-Labs PHP-Goof app on GitHub.
Deploying the fix
Magento is one of those platforms/frameworks that has a really strong community and ecosystem built around it. Time and time again, we’ve seen that community rallying together to help deploy fixes in situations like this.
The patch available from Magento updates the Filter.php sanitization method in the transDirective public function in the /Email/Model/Template directory by adding a new regex catch pattern.
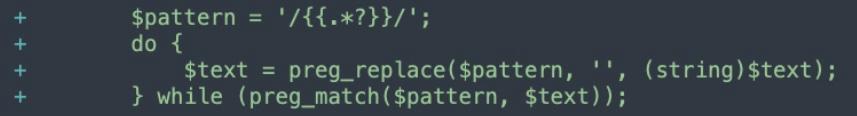
Additionally, the patch also amends the VarDirective.php file in the core framework with the same regex catch.
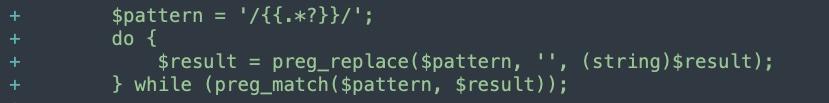
The Adobe official patch can be added into the PHP Composer package manifest, or can be applied directly to the forked codebase. Always remember to test any patches you’re looking to deploy in a staging or development environment before going to production, and remember to always have secured backups.
Detect issues automatically using Snyk
Security is always important, especially when it pertains to sensitive customer data and financial transactions. Snyk provides a few ways to get started with scanning Magento, depending on how you have Magento installed.
The most recommended and more widely adopted approach is to use the PHP Composer method. This is also a great way to update any Magento ecosystem add-ons or plugins as they are added. The PHP Composer package manifest can be easily scanned by Snyk to detect ongoing library and dependency vulnerabilities like CVE-2022-24086.
Magento can also be cloned or forked from the git repository. This is particularly useful if you’re looking to contribute back (always recommended!), or have a deployment method that requires deployment from a repo.
Snyk can connect to several different repository platforms, and can also be built into many CI/CD services that scan for IAC vulnerabilities.
Using a scanning service alerts you to any vulnerabilities that might appear, and helps protect your platform, infrastructure, and customers from attacks.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.





















