Unique to the .NET ecosystem, 75% of the top twenty vulnerabilities have a high severity rating
July 25, 2019
0 mins readWelcome to our new security report: .NET open source security insights. This report is split into three posts:
Unique to the .NET ecosystem, 75% of the top twenty vulnerabilities have a high severity rating
Our lovely handcrafted pdf report contains all of this information and more in one place, and it's free to download.
Introduction
In the first part of this report, we learned about the .NET ecosystem and discussed what a typical project looks like in terms of direct and indirect dependencies. In this part of the report, we are going to examine the twenty known vulnerabilities found most often by Snyk project scans. We also take a look at those vulnerabilities' corresponding libraries. For an ecosystem level discussion of known vulnerability types and severities, please see the final section of the report.
The most commonly seen vulnerabilities in .NET projects
Now let’s look at the top ten libraries that currently are impacting our users most, because they most frequently appear in Snyk project scans.Let’s start by looking at the characteristics of the top 10, and then take a deeper look at three of these libraries that include particularly interesting vulnerabilities. Included in the table are the minimum version upgrades you need to make to move to a vuln- free version.
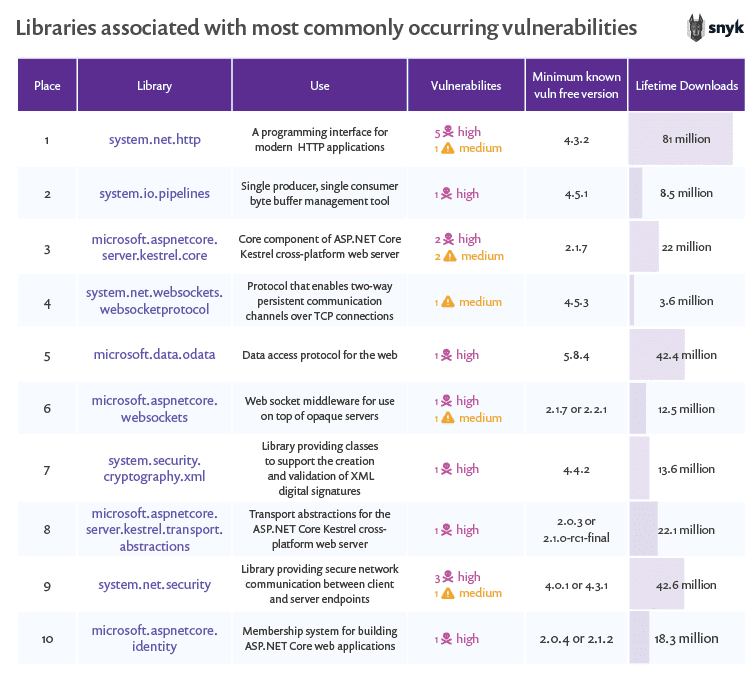
When reviewing this table, a few things stand out. First, the ASP.NET Core Kestrel cross-platform web server is both popular, and has seen a number of high severity vulnerabilities derived from several different related libraries.
Second, the total number of vulnerabilities for these libraries is generally low, but the severities are generally high. Using the Snyk vulnerability database and data from the NuGet registry, let’s dig into the top three of these libraries to learn how they are used, how popular they are, and what known vulnerabilities they contain.
system.net.http
system.net.http provides a programming interface for modern HTTP applications. This includes HTTP client components that allow applications to consume web services over HTTP, and HTTP components that can be used by both clients and servers for parsing HTTP headers.
Popularity
system.net.http has about 81 million lifetime downloads. The current version (4.3.4) accounts for around 3.4 million downloads. System.http.net averages around 31,000 downloads a day.
Vulnerabilities
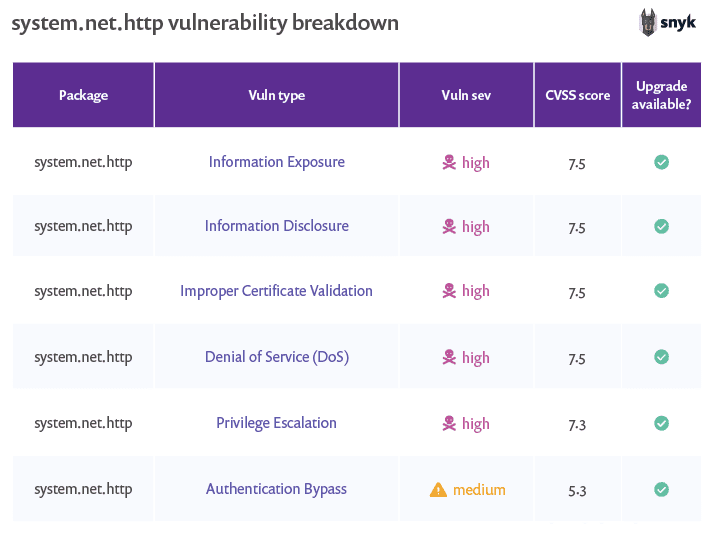
There is good and bad news with respect to vulnerabilities in system.net.http. First, the good news. The most recent version of this library (4.3.4) has no known vulnerabilities. If you use this library, upgrade to the most recent version!
But now for the bad news. This library includes a number of high severity vulnerabilities in its other versions. One of these vulnerabilities is only present in very old versions, but there are four high severity vulnerabilities and one medium severity vulnerability for versions below 4.1.2 and for versions 4.3 - 4.3.2 inclusive.
These vulnerabilities are of multiple types, including information disclosure, improper certificate validation, privilege escalation, authentication bypass, and denial of service. NuGet provides some interesting statistics for this library, including what versions have been downloaded and how often and even includes granular information from the last 6 weeks.
Unfortunately, these statistics show that only 16% of the downloads of this library in the past six weeks were for the most recent version (the only version completely free from known vulnerabilities). That means that over the last six weeks, 84% of package downloads were of versions that include multiple, known, high severity vulnerabilities.
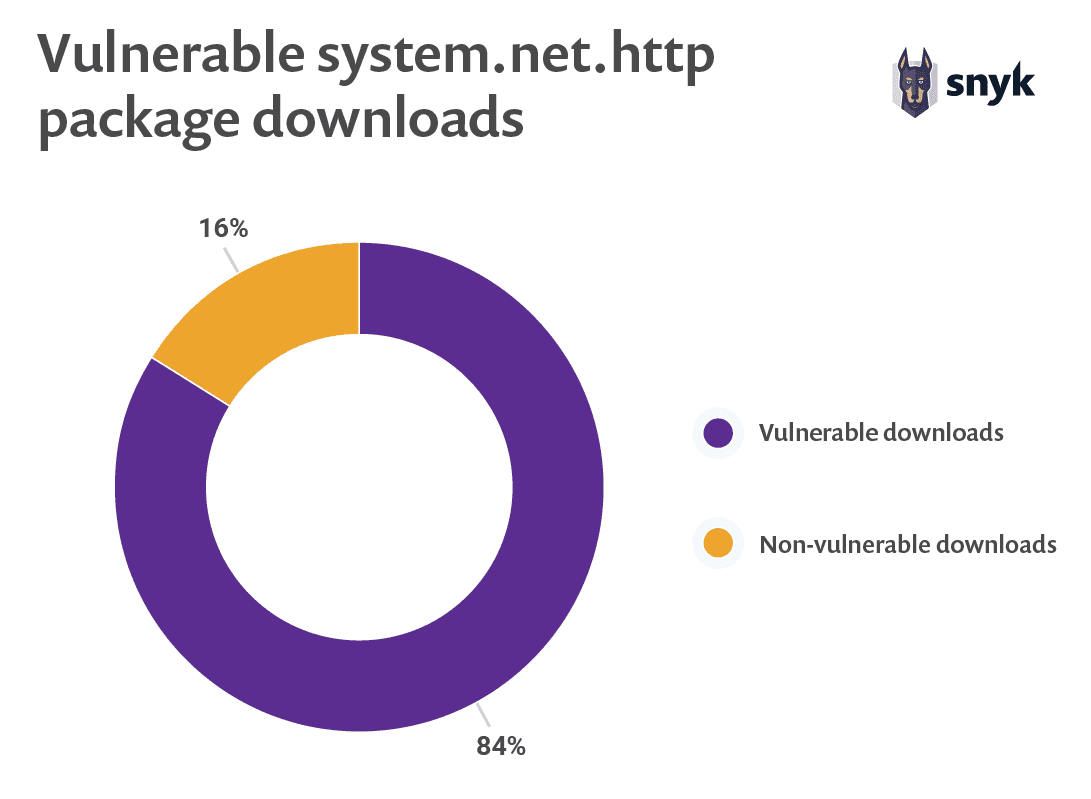
The numbers on NuGet do provide a ray of hope. The most recent version (4.3.4) has been out for 7 months, but it looks like the pace of adoption has been picking up recently. Version 4.3.4 has been downloaded approximately 3.3 million times, but 1.2 million of the downloads occurred in the last six weeks.
system.io.pipelines
The system.io.pipelines library is a single producer, single consumer byte buffer management tool. In short, this library makes it easier to do high performance I/O (input/output) in .NET.
Popularity
system.io.pipelines has been downloaded approximately 8.4 million times, including around 600k downloads of the most recent version (4.5.3). Version 4.6.0 is currently in preview.
Vulnerabilities
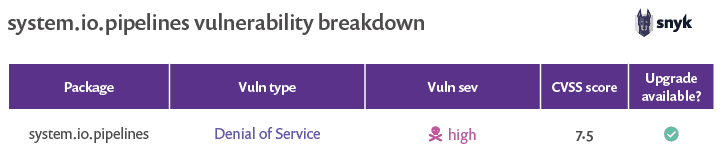
Currently, there is only a single known vulnerability associated with the system.io.pipelines library. Similar to the previously discussed system.net.http library, there is good and bad news with respect to the vulnerability in system.io.pipelines.
First the bad news. The single high severity vulnerability associated with this library is a denial of service vulnerability—which has the capacity to crash your website. The vulnerability in question has a high severity score, and if exploited can prevent legitimate users from accessing your website, run up your server costs, and cause you many headaches.
Now for the good news. The single high severity vulnerability associated with this library is a denial of service vulnerability.
Yes! This is good news as well. Unlike other vulnerabilities, denial of service attacks usually do not aim at breaching security. Despite the headaches that such a vulnerability can cause, it is reassuring that although it is likely to cost you your uptime rate, the vulnerability is not likely to lead to a loss of data or personal information.
Our recommendation? Upgrade system.io.pipelines to version 4.5.1 or higher and keep an eye on the security status of this new and useful library!
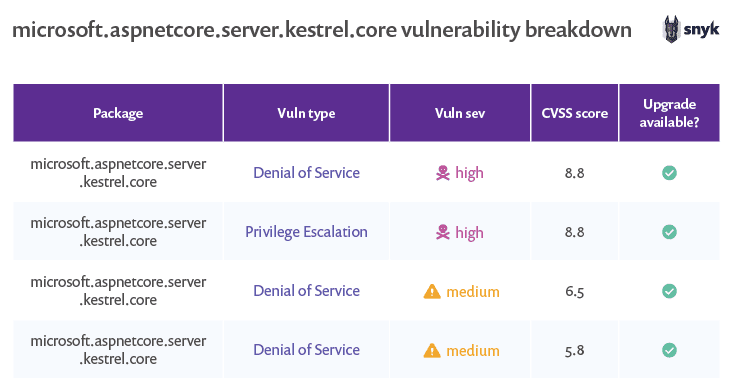
microsoft.aspnetcore.server.kestrel.core
The microsoft.aspnetcore.server.kestrel.core library is the core component of ASP. NET Core Kestrel cross-platform web server. Kestrel is an event-driven, asynchronous I/O-based server and is generally considered to be the favored web server for new asp.net applications.
Popularity
microsoft.aspnetcore.server.kestrel.core claims more than 22 million lifetime downloads. Around 630k of these downloads are for the most recent version (2.2.0), which was released in late 2018.
Vulnerabilities
This library currently has four known vulnerabilities, including two denial of service vulnerabilities of medium severity and a denial of service and a privilege escalation of high severity. The good news for this library is that the two most recent versions (2.1.7 and 2.2.0) are free from known vulnerabilities.
The bad news with respect to this library is that a related library ( microsoft.aspnetcore.server.kestrel.transport.abstractions) also appears on the list of libraries associated with the most commonly seen vulnerabilities. If you are using microsoft.aspnetcore.server.kestrel.core, you are also likely to be using other libraries with common vulnerabilities.
Additionally, it is important to remember that Kestrel is not a fully featured web server and is often run behind another library. Your choice to run Kestrel independently versus running it behind a library like NGINX or IIS is going to have an impact on how you approach your security.
The remainder of the 20 most popular libraries containing the most commonly seen are described in the following table.
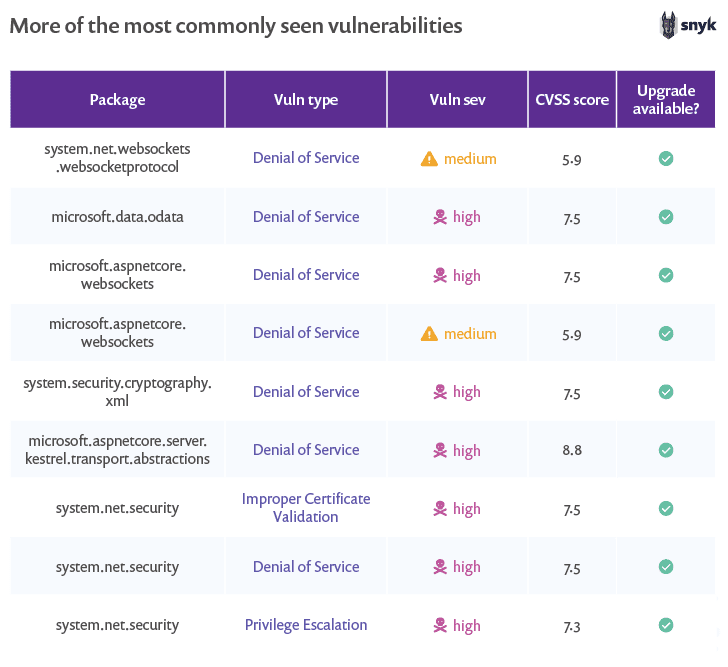
Now let’s look at vulnerability types, severities, and remediations related to these vulnerabilities.
The most commonly found .NET vulnerability types
Within the most commonly seen vulnerabilities, we see a variety of vulnerability types. More than half of the vulnerabilities in the top ten however, are denial of service vulnerabilities. Denial of service (DoS) describes a family of attacks, all aimed at making a system inaccessible to its intended and legitimate users.
More than half of the vulnerabilities in the top ten however, are denial of service vulnerabilities.
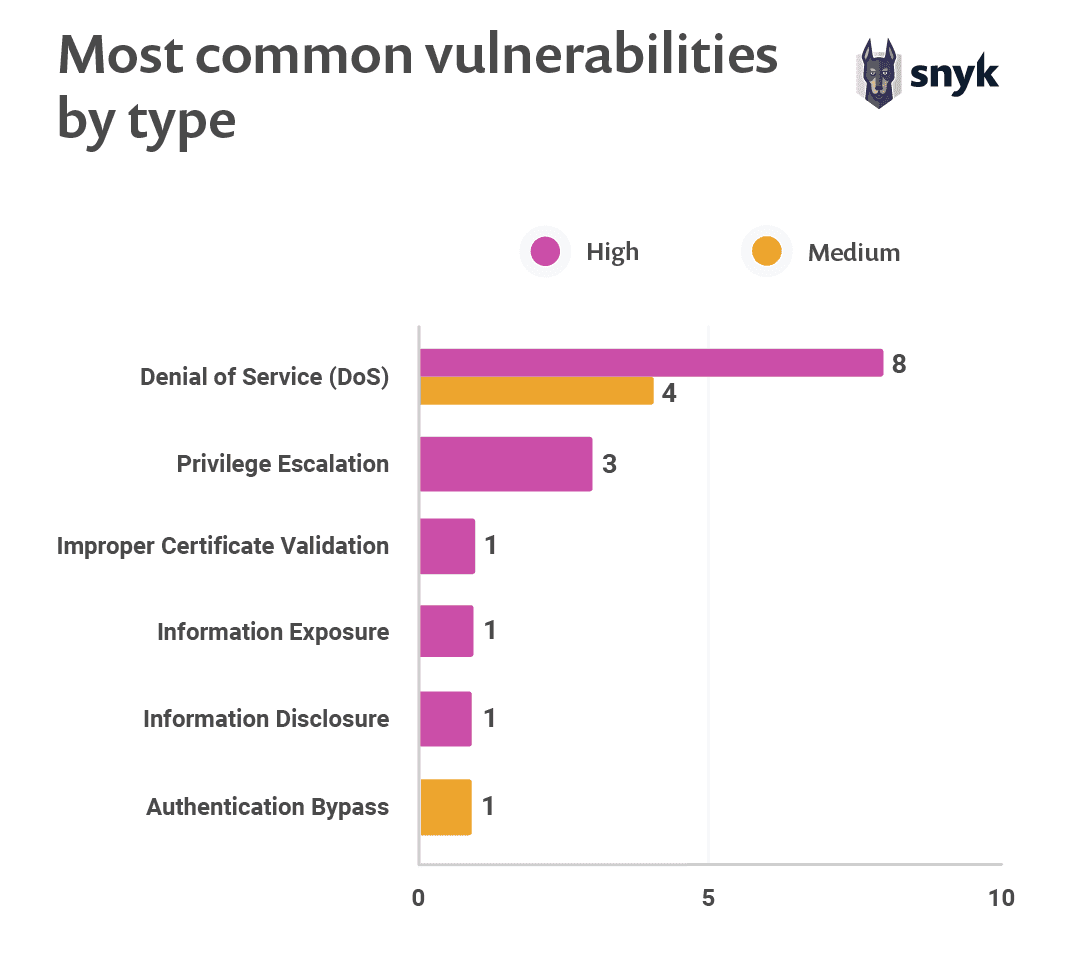
This has interesting security implications because unlike other vulnerabilities, DoS attacks usually do not aim at breaching security. Rather, they are focused on making websites and services unavailable to genuine users resulting in downtime.
One popular denial of service vulnerability is a DDoS (distributed denial of service), an attack that attempts to clog network pipes to the system by generating a large volume of traffic from many machines. When it comes to open source libraries, DoS vulnerabilities allow attackers to trigger such a crash or crippling of the service by using a flaw either in the application code or from the use of open source libraries.
Two common types of DoS vulnerabilities are:
High CPU/Memory Consumption- An attacker sending crafted requests that could cause the system to take a disproportionate amount of time to process.
Crash - An attacker sending crafted requests that could cause the system to crash.
Although no one wants a costly denial of service attack and the bad press, downtime, and lost revenue potentially associated with it, a breach of security that surfaces sensitive information could be much worse.
Vulnerability severity
The bad news that comes from this data is that three quarters of the most commonly seen vulnerabilities have a high severity rating. Medium severity vulnerabilities account for the remaining quarter of the top twenty vulnerabilities. We saw no low severity vulnerabilities. CVSS scores ranged from 5.3 through 8.8, with a median of 7.5.
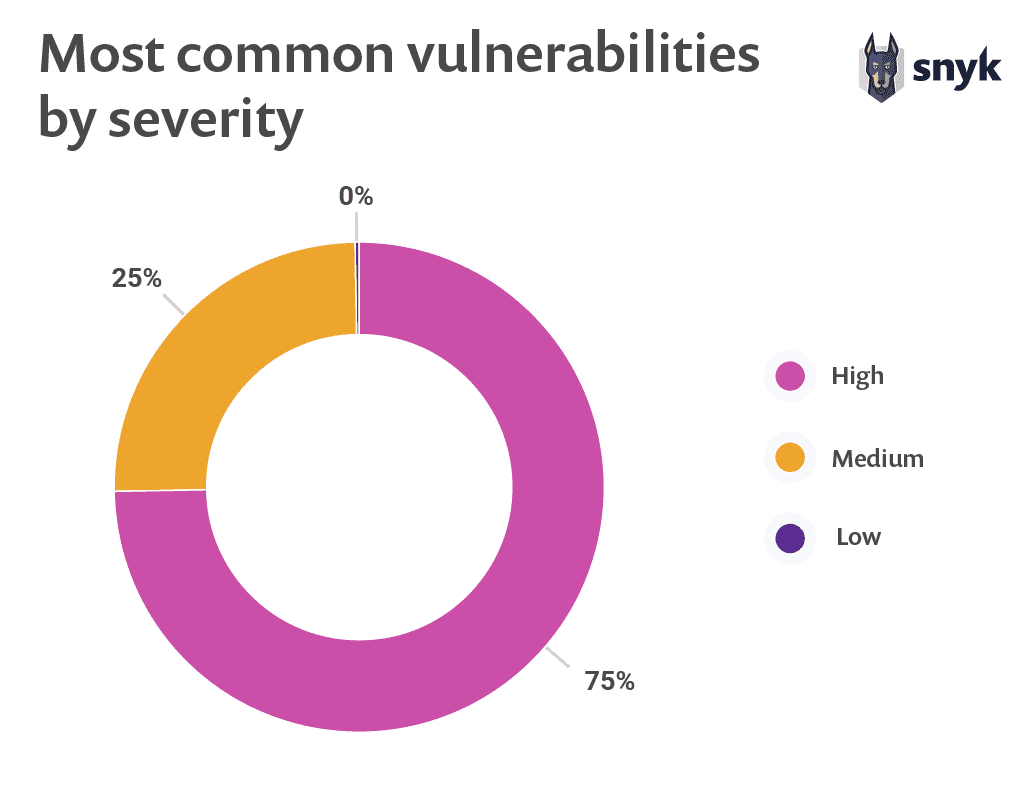
75% of the most commonly seen vulnerabilities have high severity ratings.
A general trend we have seen in the .NET ecosystem is that projects had tended not to have high numbers of vulnerabilities. This may lead people to think that they can put security on the back burner, but the statistics on severity ratings show why this is faulty thinking. Known vulnerabilities may not be as common within the .NET ecosystem, but the ones that are present can cause serious disruptions and damage if not addressed.
Every vulnerability can be fixed
Every single vulnerability within Snyk’s top 20 had available remediation.
The majority of the vulnerabilities in the top twenty may be rated as high severity, but there is good news as well. Every single vulnerability within Snyk’s top 20 had available remediation. This is excellent news. It is good to know about a security vulnerability, even if remediation is not available, but nothing beats actionable advice that leads to a more secure project.
Want to learn more?
Curious to see a bird's eye view of known vulnerabilities in the ecosystem? You can find the final portion of our report here.
And of course, you can download the entire report for free.





















