Using the Snyk Vulnerability Database to find projects for The Big Fix
DeveloperSteve Coochin
March 30, 2022
0 mins readAs developers, we all have our morning startup routine: make coffee, check Slack/Discord/email, read the latest news. One thing I do as part of my daily startup routine is check the Snyk Vulnerability Database for the latest open source vulnerabilities.
It's been especially interesting to see the types of exploits and vulnerabilities that appear in different ecosystems. I’ve been watching the emergence of vulnerabilities in Tensorflow libraries since May 2021, and at the time of this writing, they have appeared again (nearly two pages of them!). Vulnerabilities within ElectronJS, the ecosystem powering Slack, VS Code, Twitch, and many other popular apps have also surfaced multiple times in recent reports.
While the Snyk Vulnerability Database simplifies secure development day to day, it also helps make the internet more secure overall. Snyk’s month-long vulnerability sprint, The Big Fix, brought developers, DevOps, and security practitioners together to fix as many vulnerabilities as possible, culminating in the 24-hour Big Fix-A-Thon live stream. Many participants used the Snyk vulnerability database to find and fix malicious packages in a variety of open source projects.
The official event may be over, but The Big Fix community is active as ever. Today, I’ll show you how to find a project with the open source vulnerability database, so you can help keep users safe and grab a limited edition #thebigfix t-shirt along the way.
Getting started with The Big Fix
The first step is to sign up for a free Snyk account. If you don’t already have one, head over to the getting started page and provide all the usual details (no credit card required). After that, go to The Big Fix website and click Register now. Finally, fill out your name and email address, and you’re ready to start.
Once you're signed up, the next step is finding a project. There are a few ways to do this.
Connect an existing repository
If you already have a project repository in mind, you can connect it quickly and easily. Go to your Snyk dashboard and click Add Project. If your repository of choice is not listed in the quick menu, click Other, which will take you to a comprehensive list of integration options.
Select your repository of choice and follow the steps to connect and configure.
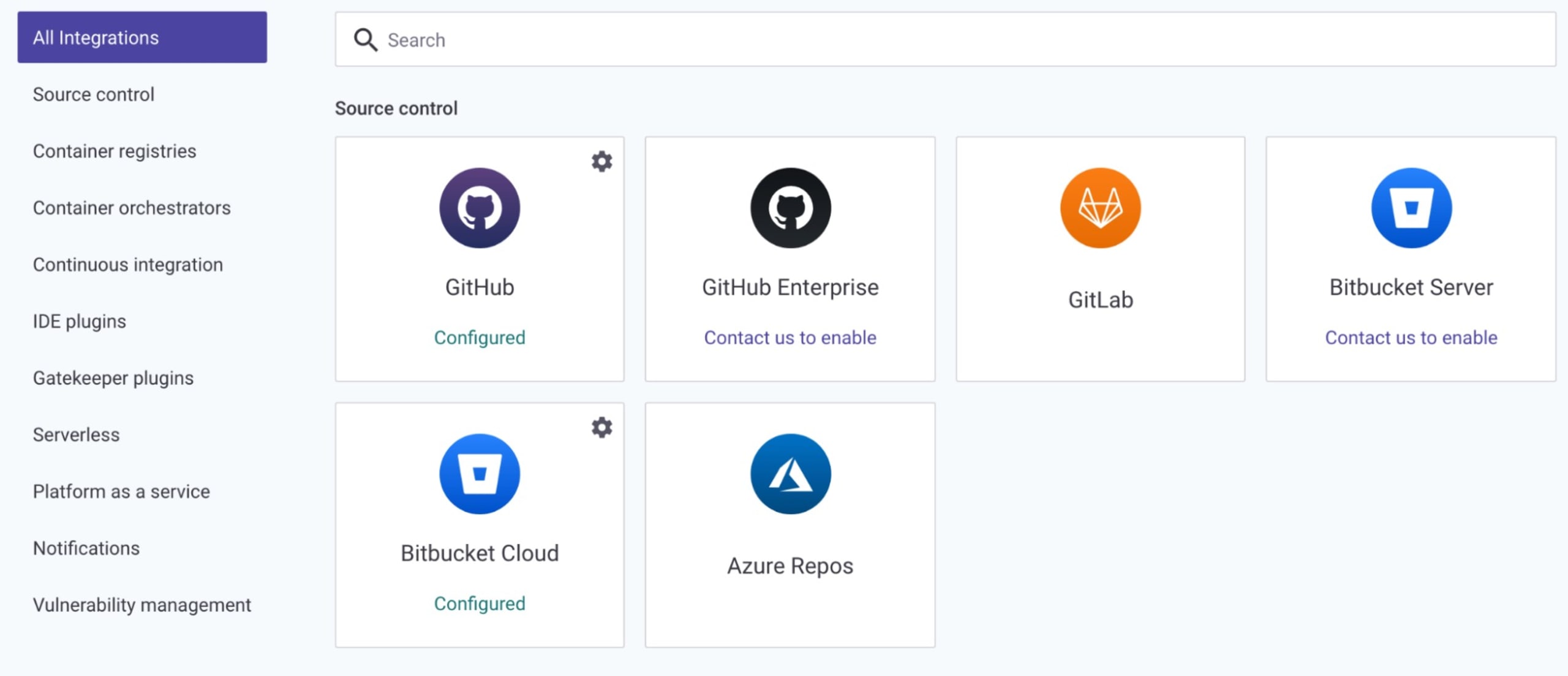
Once connected, click Add Project again and select the repository where you want to do an open source vulnerability scan. You can even scan private repositories.
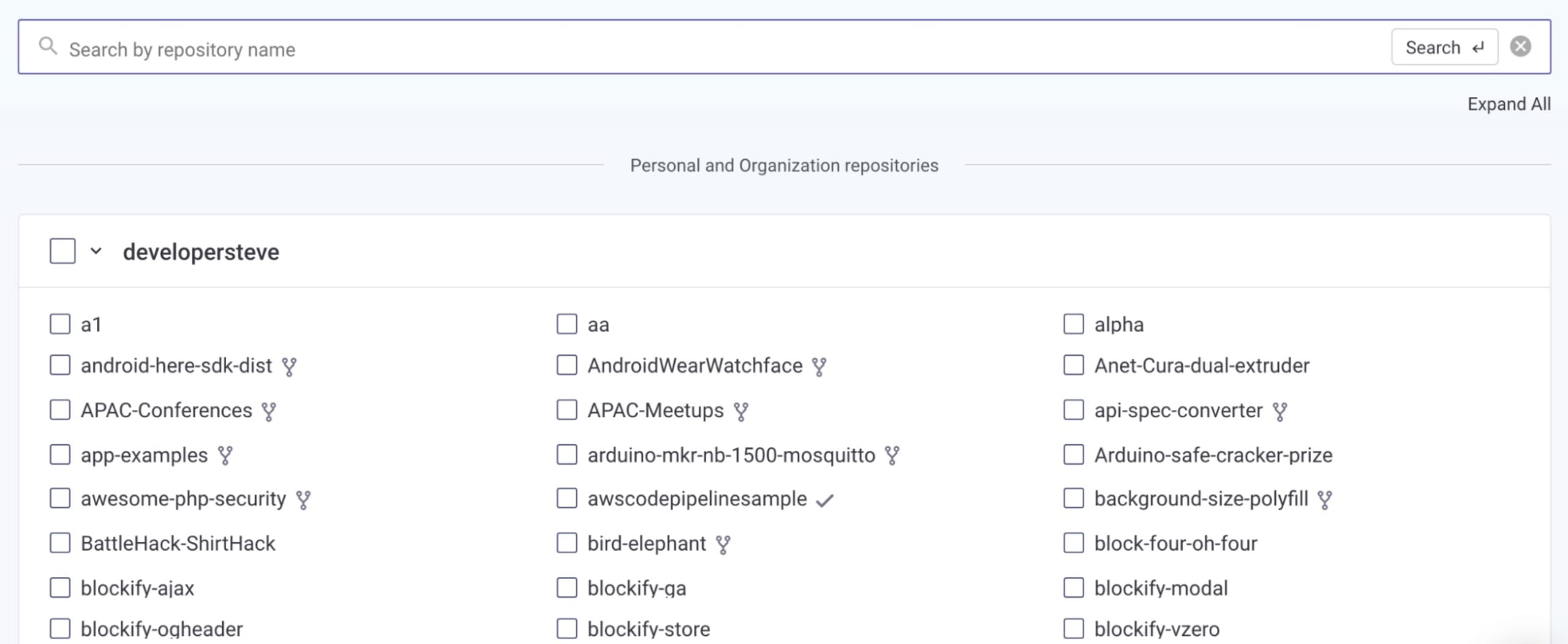
When connected to Snyk, the scan will identify vulnerable packages in the connected package manifest. You can then select these packages to see recommended fixes and potential remediation steps. Snyk also offers the ability to create an automatic pull request with recommended fixes — just remember to test the application to verify that everything in the project is working as expected.
Find a project
If you’re looking for a project where you can help fix a vulnerability, you can use the Snyk Vulnerability Database to search for projects in your package or ecosystem of choice.
During The Big Fix, I contributed to Invoice Ninja, one of my favorites from the PHP open source ecosystem. This open source project helps businesses all over the world with invoicing and accounting, by connecting to a variety of third-party business tools.
First, I forked the main repository into my own account. Then, using the method above, I connected the repository to Snyk.
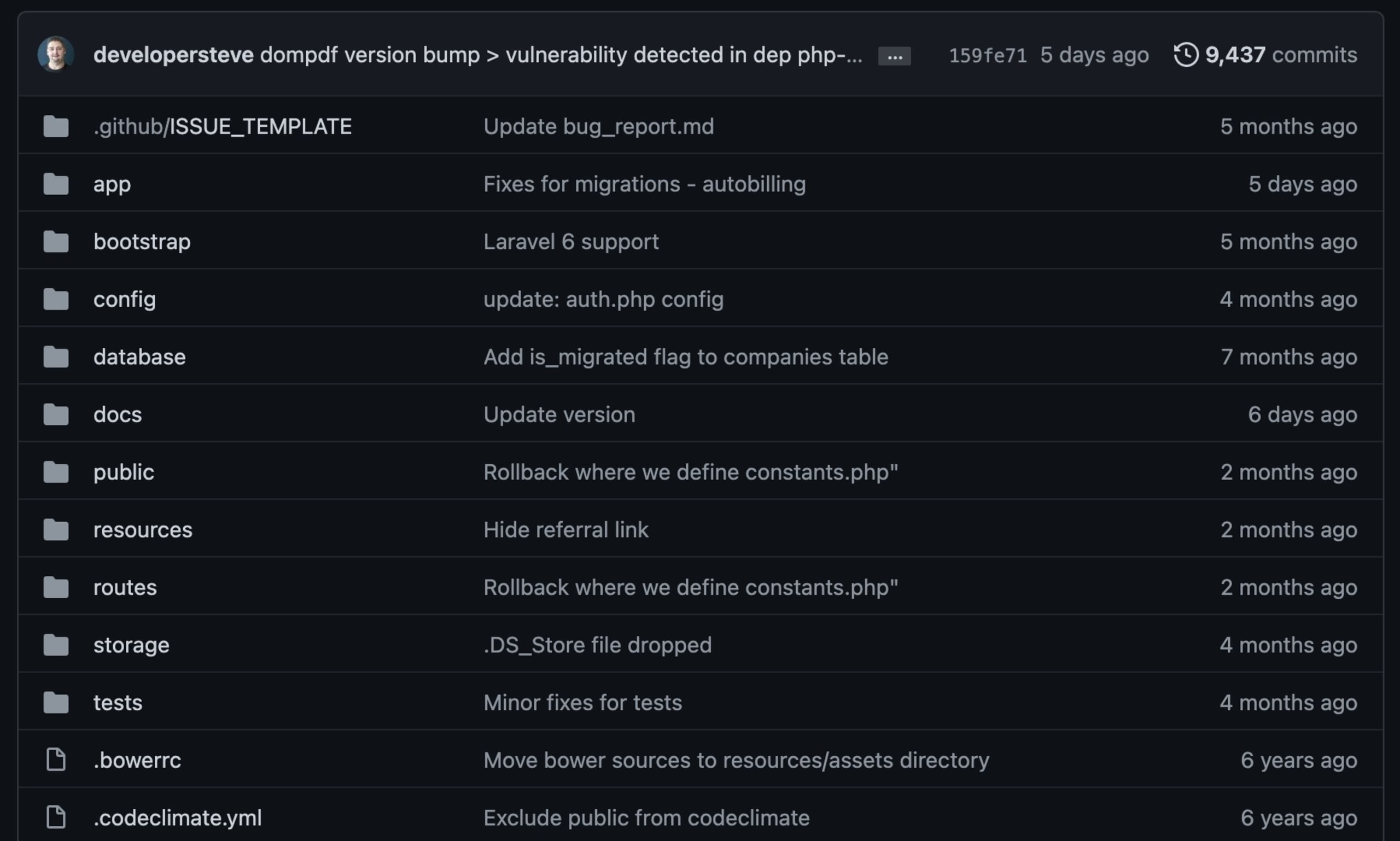
The scan identified a few vulnerabilities in the PHP composer package manifest, one of which was being introduced via DOMPDF 0.6.2 as a dependency library.
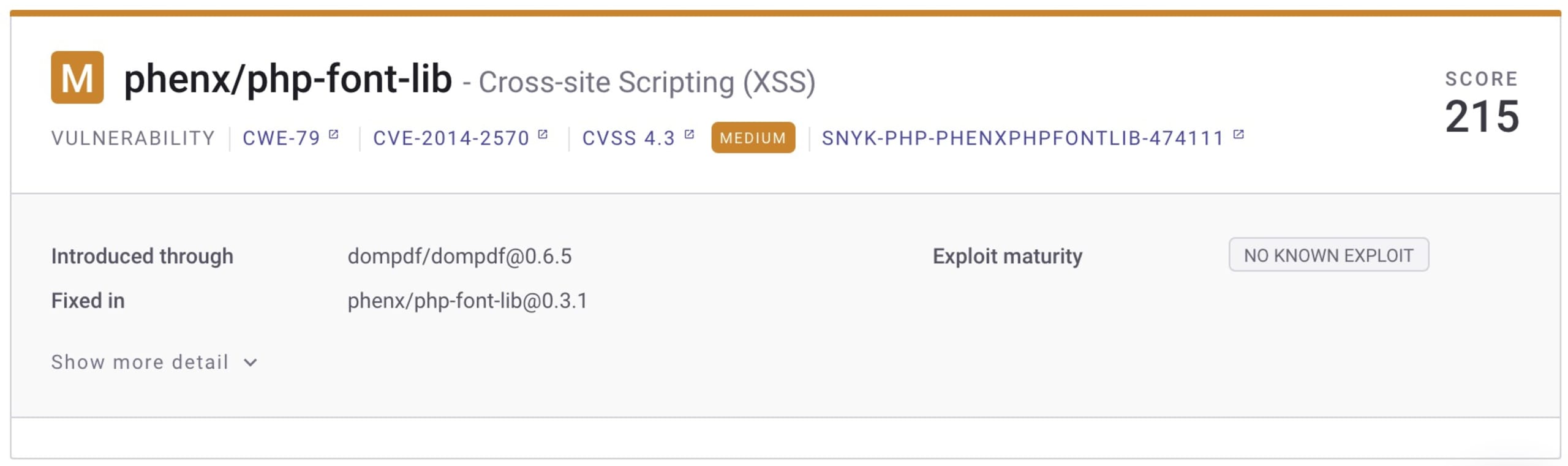
Digging a bit further into some of the findings, I identified a few issues, including a cross-site scripting (XSS) vulnerable path in PHP-Font-Lib — a vulnerability from 2014. Tracing it back through the project helped identify not only the issue itself, but also the necessary fix.
When deploying fixes, you need to keep a few things in mind. Foremost is making sure the overall project still works. This is especially important with library and dependency upgrades. Many people rely on these projects for their day-to-day business, and deploying a breaking change is not something any project wants to see.
I pulled the forked repo into my localhost using a Git pull request and launched VS Code. With the Snyk plugin installed, I was able to upgrade the affected packages and debug. Then, I ran the code for testing on my localhost using a localhost server (this can also be done using PHP’s built-in server).
Finally committing back to my forked repository, I submitted a Git pull request, which was verified by the community before being merged.
The elation of completing contributions
I love giving back, especially when I can help keep another community safe and vulnerability-free. As members of the open source community, it’s important to contribute and help protect all open source users. So, let's all work together to make the digital world a safer place.
