Announcing Social Trends: Use social media for security intelligence
Daniel Berman
July 28, 2021
0 mins readWe are excited to announce the availability of Social Trends, adding social media intelligence (SOCMINT) to Snyk’s vulnerability data to help development and security teams prioritize vulnerabilities more effectively.
Given the size of vulnerability backlogs facing organizations today, finding and fixing security vulnerabilities in a timely manner is a monumental task. There simply are not enough hands on deck to triage and tackle all the vulnerabilities on the list. That’s where prioritization comes into the picture. Assess the risk, prioritize where to focus your resources, and fix those vulnerabilities posing the greatest risk. Rinse and repeat.
But to be effective, prioritization requires top-notch security intelligence. Is a vulnerability fixable or not? Does a vulnerability have an exploit in the wild and how mature is that exploit? Is the vulnerability reachable or not? When was the vulnerability first introduced? Not being able to answer these questions, either at all or in an accurate enough manner, can lead you to make the wrong prioritization decision, and in turn, result in a greater security risk for your organization.
Snyk’s security intelligence — curated, cultivated, and developed by Snyk’s Security Research team — provides you with the security expertise and context needed to not only find security issues in your applications but also to easily and quickly prioritize fixing them. With Social Trends, this intelligence just got a whole lot more powerful, providing an additional signal to help Snyk users focus their efforts on those vulnerabilities posing the greatest risk.
Social media’s role
Just here to drop a Chrome 0day. Yes you read that right.
@r4j0x00
This is how security researcher Rajvardhan Agarwal shared an exploit for a zero-day remote code execution (RCE) vulnerability on Twitter in April this year that affected Chrome and other popular web browsers.
Agarwal is not alone. A simple search for hashtags like #0day, #zerodaytoday, #CVE, and #exploit reveals that discussions over security vulnerabilities on Twitter are a common enough practice among security actors. Social media platforms like Twitter and Reddit are increasingly being used to share information about vulnerabilities, exploits, and malware. Many of these discussions take place early in the vulnerability’s lifecycle, sometimes before they are publicly disclosed.
A 2020 research report examined CVEs discussed in social media between 2015 and 2017 and found that, on average, they were discussed on Twitter, Reddit, and GitHub 87 days before being added to NVD. As an example, the CVE-2017-0144 vulnerability that was exploited during WannaCry and NotPetya attacks in 2017 was discussed on Twitter three days before being added to NVD.
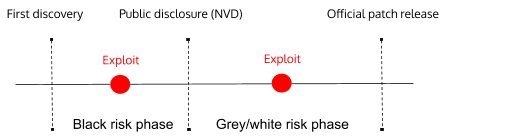
Other vulnerabilities are discussed on social media a bit later in the vulnerability’s lifecycle, after being publicly disclosed but before an exploit is available. Proof of concept exploits, as well as mature exploits, are also frequently a topic for discussion. For obvious reasons, the more severe the vulnerability, the more attention received: more discussions, more interactions, more engagement.
While these discussions contain valuable information to help security analysts and practitioners better protect their respective organizations, they also attract malicious actors, and the same information can aid their activity. Snyk's Security Research team has found a strong correlation between activity around vulnerabilities in social media and the likelihood that those vulnerabilities will be exploited — 80% of the trending vulnerabilities identified by Snyk have been found to have an exploit or PoC in the wild. In fact, 85% of these exploits were not officially published on known exploit databases either before or during the period of time they were trending.
Early awareness of these social media signals, often referred to as social media intelligence, can therefore go a long way in helping organizations prioritize which vulnerabilities to address first.
How to use Snyk’s Social Trends
Snyk’s Social Trends was designed to enable users to identify whether a specific vulnerability is trending on Twitter.
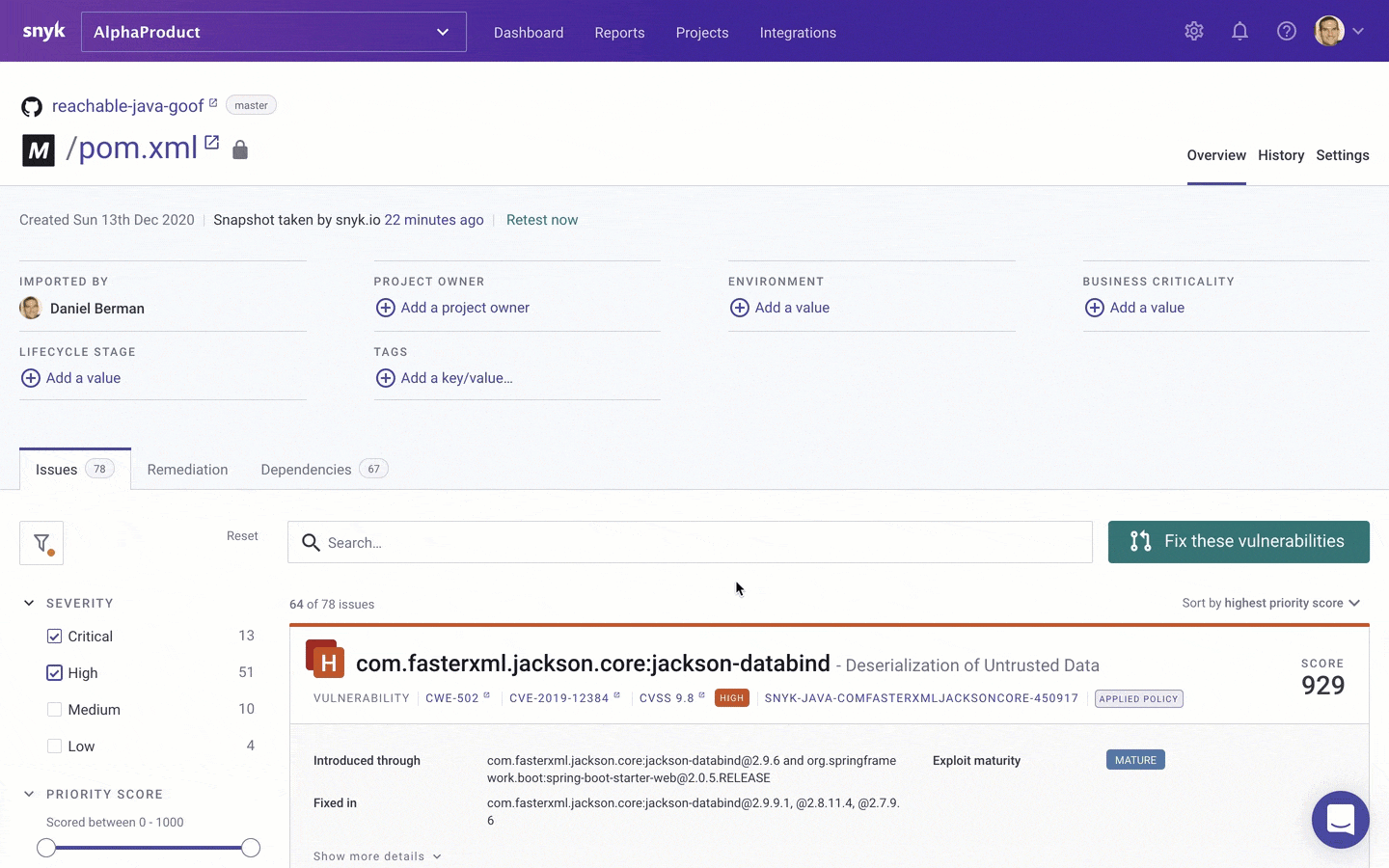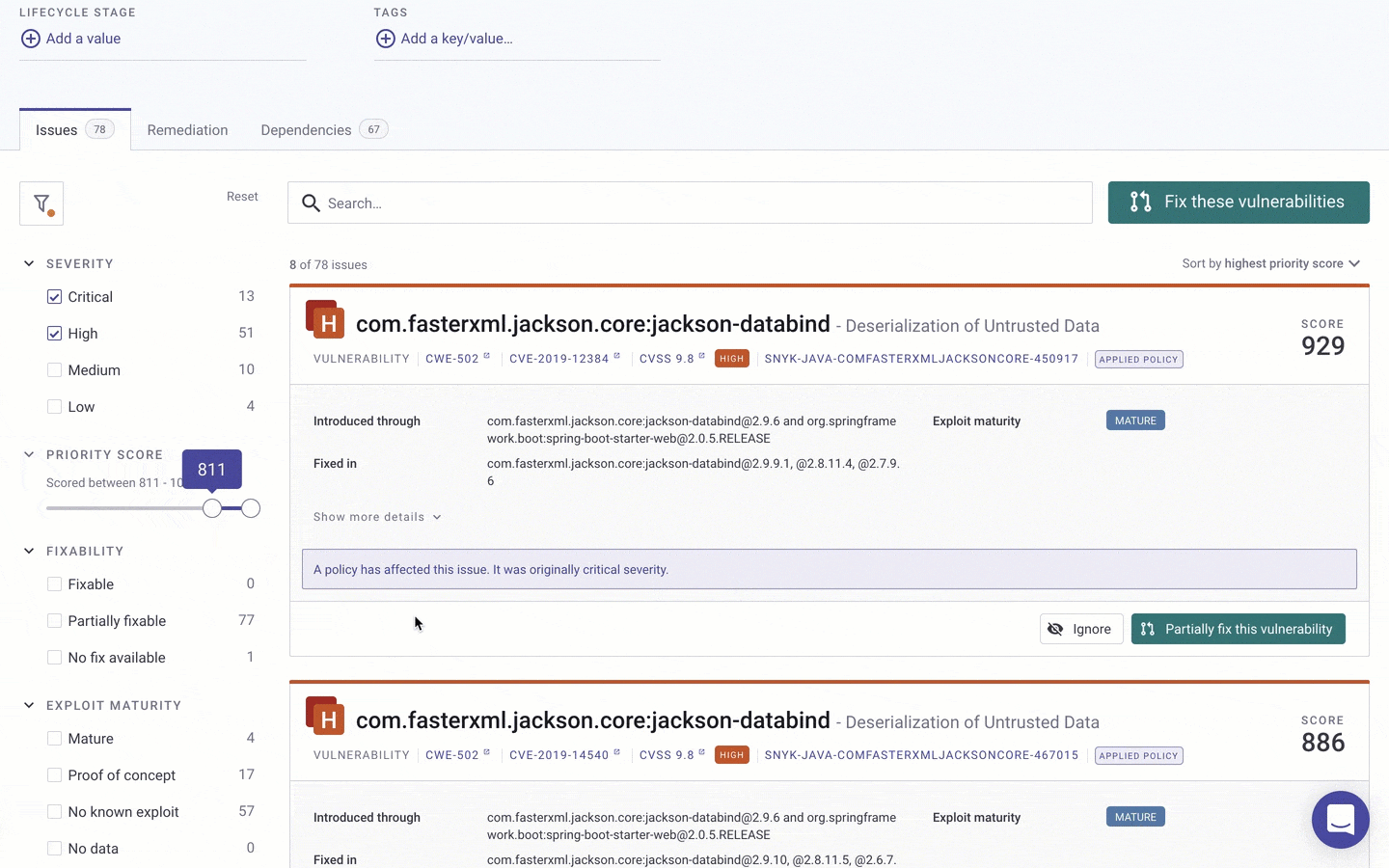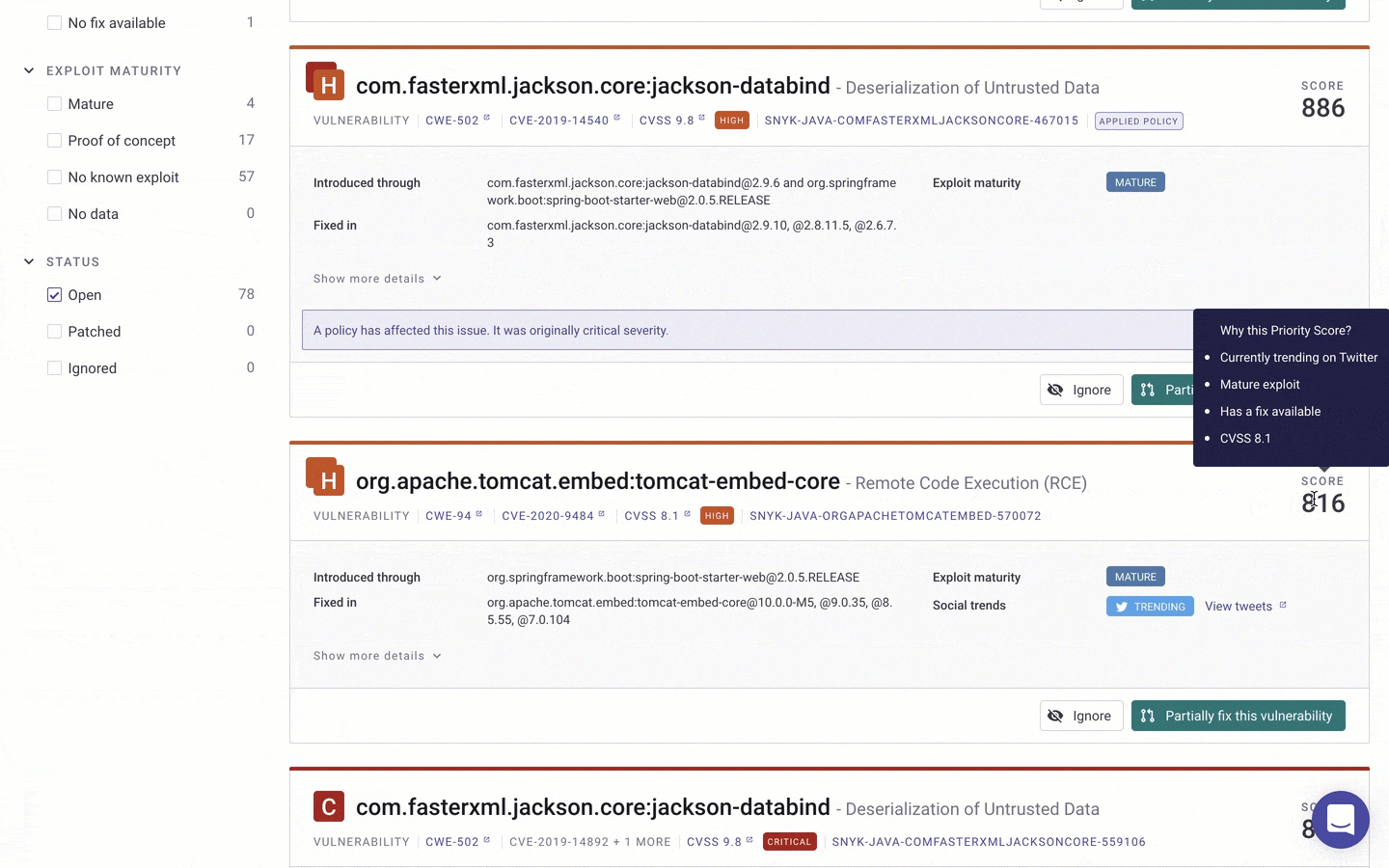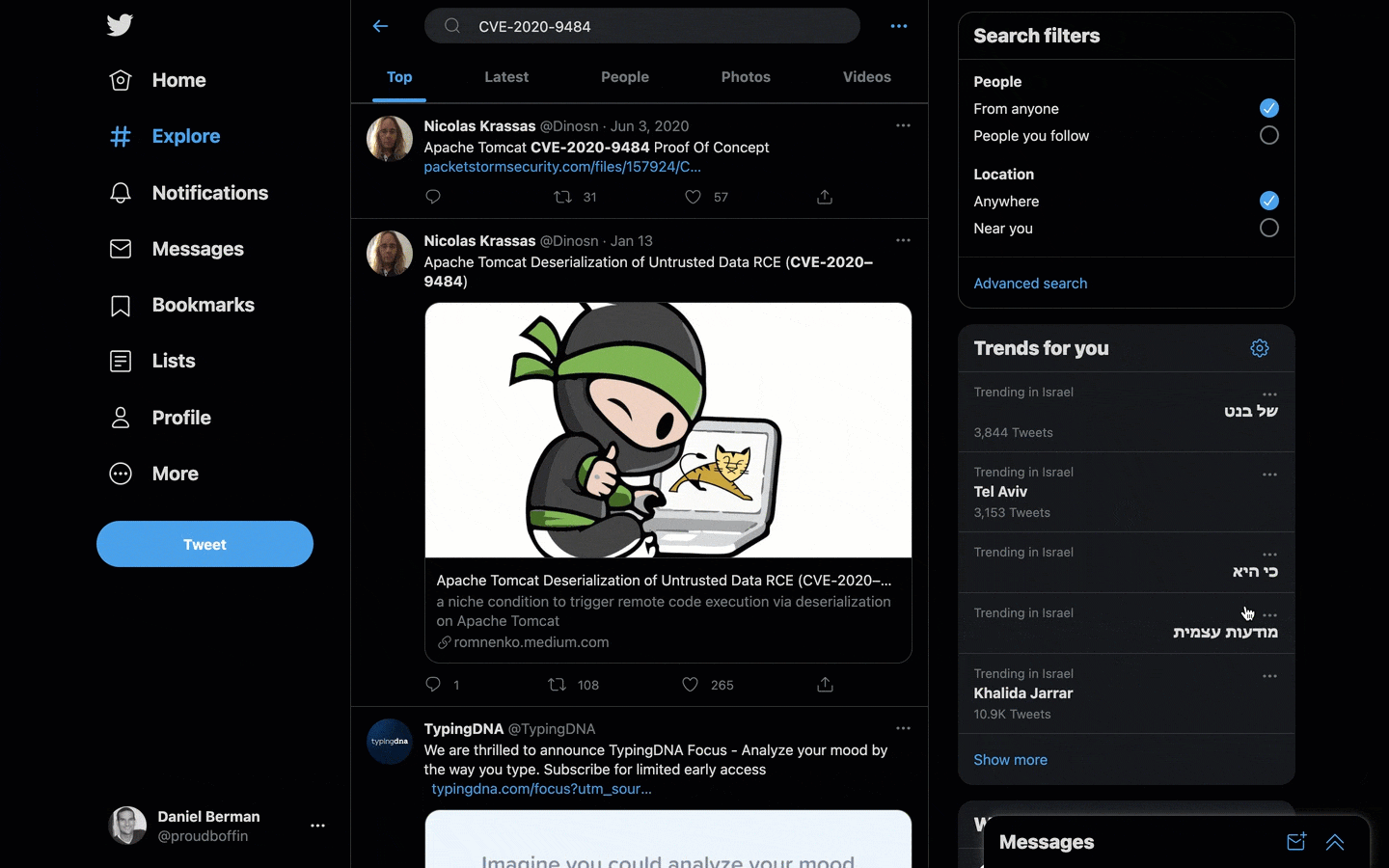
So how does Snyk determine if a vulnerability is trending in the first place? Data is pulled via Twitter’s public API and narrowed down by filtering for discussions that include mentions of CVEs. Using statistical models that were built and tested against Snyk’s vulnerability database, Snyk then measures the level of human engagement for a specific discussion, factoring in the number of likes, retweets, and levels of interaction. This process is crucial to guarantee accurate results; there is a lot of “noise” on Twitter, including bot activity, which could lead to an erroneous signal.
Once a trending vulnerability is identified, it is added as a factor in Snyk’s Priority Score — a scoring system that processes a vulnerability’s CVSS score, the availability of a fix, known exploits, how new the vulnerability is, whether it is reachable or not, and now also whether the vulnerability is trending. The score, ranging from 1–1000, is calculated for both security vulnerabilities and license issues and is displayed at the top-right corner of each issue within the Snyk UI.
When triaging, you can use the Priority Score filter on the left to quickly whittle down the list of vulnerabilities and focus on those with the highest score. A Social Trends field is displayed on the vulnerability card itself, alongside the other security intelligence that Snyk provides for vulnerabilities, with a link to the relevant discussion on Twitter:
If you are using the Snyk API to integrate with Snyk’s vulnerability data, you will be able to use Social Trends as well, pulling the information into your reports and dashboards for better visibility into vulnerabilities from within the tools and workflows already in place.
Trends being trends, at some stage, they die down. Snyk will identify when this happens and will remove the Social Trends field from the Snyk UI.
Proper prioritization made easy
The quality of the security intelligence you have at your disposal directly impacts prioritization. If this intelligence is not accurate enough, it might lead you to prioritize the wrong set of vulnerabilities. If this intelligence is not accessible in a user-friendly way, it will be difficult for you to leverage it to take action. And if this intelligence is not timely or comprehensive enough, you will not be able to quickly prioritize vulnerabilities.
Snyk’s Security Research team, together with our technology and contributions from the community, ensure that our security intelligence helps you easily and quickly prioritize and fix the vulnerabilities identified in your application. Social Trends is the latest signal added to this intelligence, but it is definitely not the last. We are continuously researching new ways to help you drive more effective prioritization decisions in your organization.
As always, we would love to get your feedback. Twitter is the first data source currently being used to power Social Trends but we are also considering additional social media platforms such as Reddit and Discord. Your input would be helpful for understanding how we develop this capability in the future so if you haven’t already, sign up to Snyk to try it out. Obviously, since not every vulnerability is trending, you may not see Social Trends appear as a signal in your projects.
Social Trends is fully available in all Snyk plans — including our Free plan — for vulnerabilities across all the supported programming languages in Snyk Open Source as well as Linux vulnerabilities in Snyk Container.
Developer loved. Security trusted.
Snyk's dev-first tooling provides integrated and automated security that meets your governance and compliance needs.
