Snyk Maven plugin: Integrated security vulnerability scanning for developers
April 20, 2021
0 mins readMaven is the most commonly used build system in the Java ecosystem, and it has been for many years. Building your application with Maven is easy since it takes care of many things for you. In different phases of the Maven lifecycle, it handles things like:
Downloading dependencies
Compiling your Java code
Running unit tests
Creating a shippable artifact
Integration tests
And much more
With Maven, the development lifecycle happens the same way on every machine for every developer on the team, as well as within the CI pipeline. Since Maven already downloads the needed dependencies and runs tests, wouldn’t it be great to seamlessly integrate vulnerability scanning in this lifecycle? Well, the Snyk Maven plugin does just that.
Scanning the dependencies for known security vulnerabilities in your project is essential. The ideal time to start checking your dependencies is the very moment you import them! To that end, we created the Snyk Maven plugin so you can now scan your application for security vulnerabilities in third-party libraries as part of your build cycle — putting security expertise in the hands of developers.
If you want to see the plugin in action before you keep reading, have I got the video for you...

The Snyk Maven plugin
The Snyk plugin for Maven is generally available and published on Maven Central. You only need to configure it in your pom.xml file. Below you see the default configuration for the plugin.
<build>
<plugins>
<plugin>
<groupId>io.snyk</groupId>
<artifactId>snyk-maven-plugin</artifactId>
<version>2.0.0</version>
<inherited>false</inherited>
<executions>
<execution>
<id>snyk-test</id>
<goals>
<goal>test</goal>
</goals>
</execution>
<execution>
<id>snyk-monitor</id>
<goals>
<goal>monitor</goal>
</goals>
</execution>
</executions>
<configuration>
<apiToken>${env.SNYK_TOKEN}</apiToken>
<args>
<arg>--all-projects</arg>
</args>
</configuration>
</plugin>
</plugins>
</build>As you can see, we distinguish two different goals: test and monitor. After adding the plugin to your project, simply call mvn snyk:test or mvn snyk:monitor. By default, the snyk test goal connects to the Maven test phase in the lifecycle. This means that after the Maven test phase completes, the Snyk test goal executes automatically. The Snyk monitor goal connects to the install phase and works in the same way.
Just like every other Maven plugin, you can change this behavior. In the execution part, you just need to add a <phase> tag. It can be set to an existing phase like test, package or verify, or none. In the example below, I connected snyk-test to the verify phase and snyk-monitor to none. Now mvn snyk:monitor is still available manually, but will not execute automatically as part of a phase in the build lifecycle.
…
<executions>
<execution>
<phase>verify</phase>
<id>snyk-test</id>
<goals>
<goal>test</goal>
</goals>
</execution>
<execution>
<phase>none</phase>
<id>snyk-monitor</id>
<goals>
<goal>monitor</goal>
</goals>
</execution>
</executions>
... Note that if you want to skip the execution of the Snyk goal in your lifecycle, you only have to add -Dsnyk.skip to your command. Ex:
mvn package -Dsnyk.skip
How does the new Snyk Maven plugin work?
There already was a Snyk plugin for Maven, however, this plugin used custom logic to determine the dependency tree. As a result the output from the CLI and the old Maven plugin could be slightly different.
Similar to the Gradle plugin, the new Snyk Maven plugin now actually uses the Snyk CLI under the cover. It automatically downloads and updates the appropriate CLI binary, so the CLI doesn’t need to be preinstalled. The only thing you need is a free Snyk account to obtain the API token.
Configuring the Snyk Maven plugin
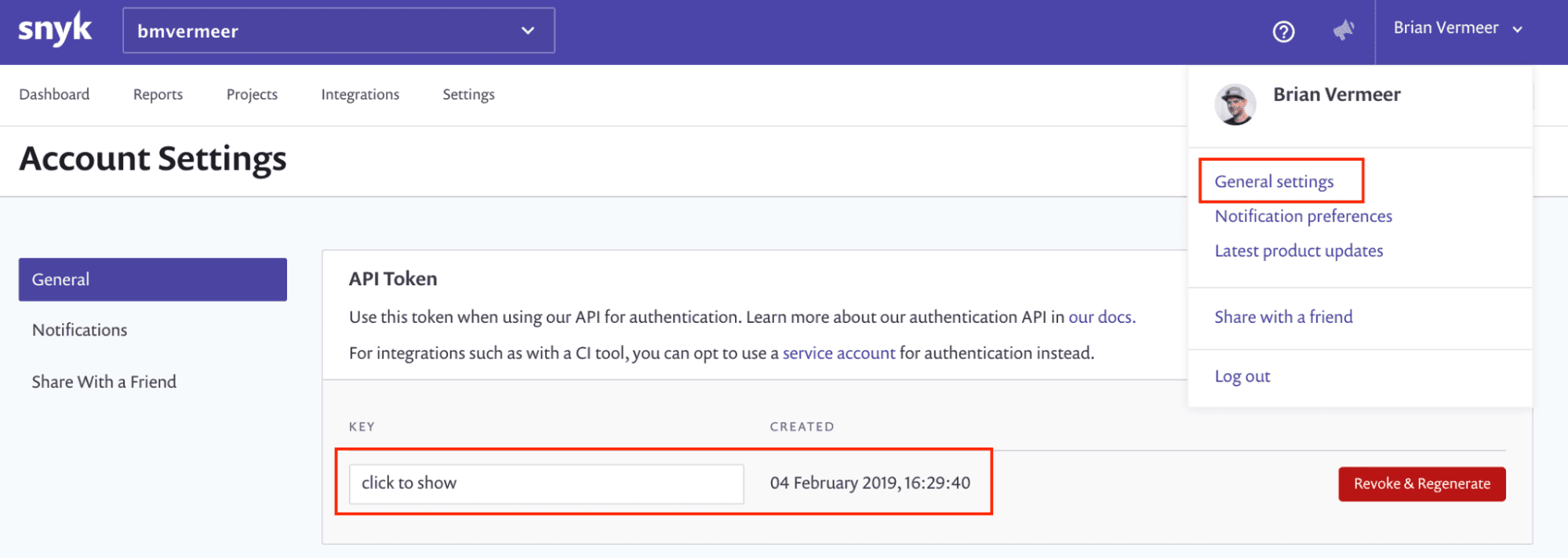
To configure the plugin, you’ll need to set the API token to enable dependency security scanning with Snyk. You can find the token in the General settings part inside your Snyk account. Alternatively, you can also create a specific token for a service account.
In the first example of the blog post, I did not put the token in the pom file. Instead, I created a global environment variable SNYK_TOKEN on my machine and referred to that.
This way, I do not have my secret token in the pom file, which is especially useful when you publish your code to an open source repository
apiToken>${env.SNYK_TOKEN}</apiToken>
In the <args> part of the configuration, you can provide any flag you normally provide to the CLI. Currently, in my example I provide the --all-projects flag. Now, all my projects, regardless of the ecosystem, will be scanned in one go. This is especially useful if you use multiple pom files in your project.
Furthermore, you can also configure some specific things on the CLI if you want. By default, the CLI automatically updates daily on the first execution. Still, if you want to use a specific binary, a specific version of the CLI or change the update strategy, you can add a <cli> object inside <configuration>. All possible settings are documented in the github repo. In the example below, I change the <updatePolicy> to always. As a result, the plugin checks for new CLI updates at every execution and not just once a day.
<configuration>
...
<cli>
<updatePolicy>always</updatePolicy>
</cli>
</configuration>Add security to your Maven lifecycle
Integrating Snyk Open Source scanning in your maven build lifecycle feels very fluent and natural. With the new Snyk plugin for Maven, this integration is seamless and can be run in the same fashion on every machine, including your CI pipeline. Now you don’t need to call the CLI manually anymore, and the configuration for running Snyk Open Source scanning is stored as part of the project. One less thing for a developer to worry about.
For more information on the plugin, please visit our Github repository. And don’t forget to signup for a free Snyk account before you use this great integration.
Follow-up resources that I highly encourage you to review:
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.