Introducing open source security runtime monitoring
November 12, 2018
0 mins readSnyk has now released the first capability in its application security runtime monitoring solution, allowing developers to monitor the actual behavior of their open source components at runtime!
At the moment, Snyk’s integration with the project’s repository or into a project’s CI cycle allows analysis of open source dependencies, flagging vulnerable dependencies and suggesting remediation actions. Snyk invests heavily in making fixing vulnerabilities an easy task that’s baked into the development workflow, such as opening fix PRs, providing patches where upgrades aren’t possible, and more.
However, even with the fix being relatively easy, many developers and organizations could still have a large backlog of vulnerabilities they need to handle. Any prioritization advice we can offer here is helpful, and we believe a key part of prioritizing vulnerabilities is determining whether a vulnerable dependency is indeed being used at runtime in a way that can be exploited. There are some approaches in the market that try to achieve that via static code analysis. The main problem with that is the high rate of false positives and negatives it generates (for example, if code is being called dynamically, or if it’s only reached based on a specific input, etc.)
Snyk provides a solution that monitors the actual application runtime behavior, and presents accurate indication of the invocation of vulnerable functions in a project’s dependencies.
Rest assured, we have been putting a lot of effort into making sure the performance impact on the application is minimal, and we'll keep testing that. We're currently offering early access to our runtime solution as a closed beta. If you’d like to try it out, please email us at runtime@snyk.io!
Prioritize vulnerabilities based on runtime invocation data
Once the agent is properly installed and is instrumenting running instances of the monitored application, you'll see an indicator on the issue details card that will tell you whether vulnerable functions were recently invoked in a monitored application instance. The vulnerabilities will be sorted primarily by whether they were called at runtime, and then by severity level. Additionally, the names and paths of any vulnerable functions will be shown. This will simplify triaging by helping you understand which part of your application is using them. We'll also show you how long it has been since one of the vulnerable functions was last called.
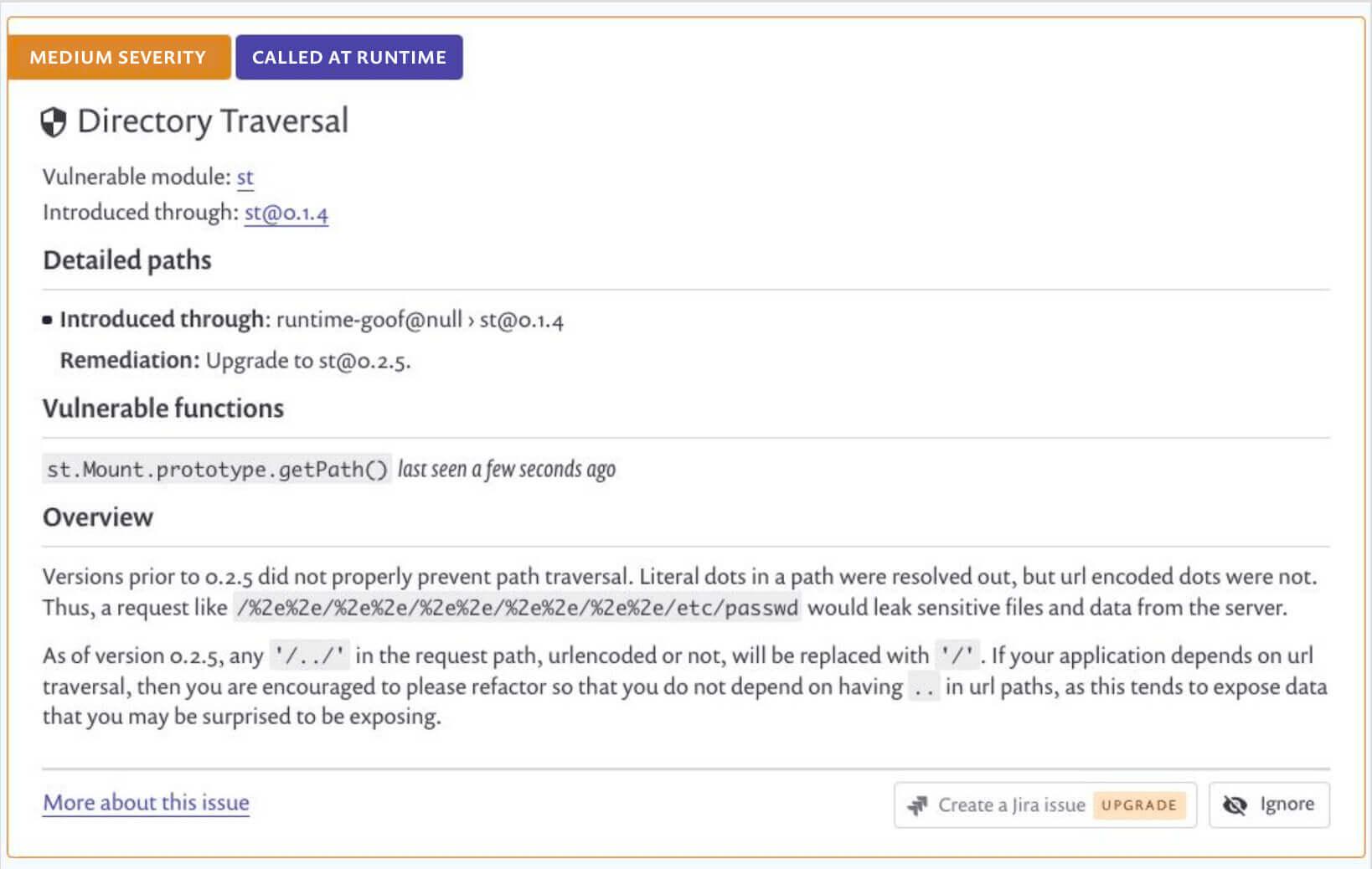
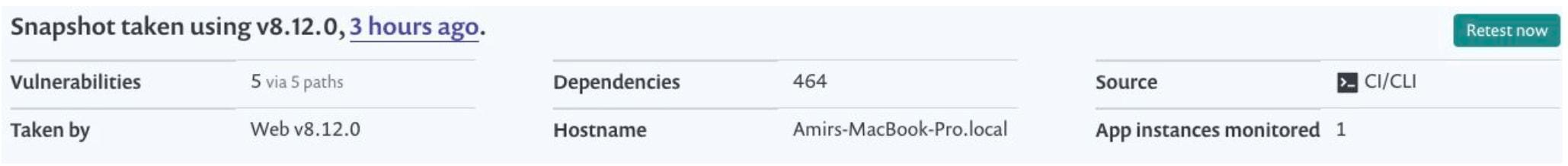
As there may be multiple monitored application instances running, you’ll be able to see the number of instances monitored in the bottom right section of the project metadata.
Getting started with Node.js
To start monitoring your Node.js applications you will need to add the @snyk/nodejs-runtime-agent dependency to your project by running: npm install @snyk/nodejs-runtime-agent in your project folder, and configure it as soon as possible in your application’s start sequence.Here’s an example of such a flow:
require('@snyk/nodejs-runtime-agent')({
projectId: '0462e42b-c92f-4b48-bac8-81eb3ff7f43e',
});
const express = require('express');In the snippet above, the @snyk/nodejs-runtime-agent dependency is required prior to any other require statement. This allows the agent to inspect each and every required dependency in order to create an execution hook that will signal to the agent when vulnerable functions are being invoked by the application.
The agent is configured with an ID of a project monitored on snyk.io. You can obtain your project’s ID via the API, or by inspecting the settings page of the project on snyk.io.
For more details, refer to our documentation on installing runtime protection.
Getting started with Java
To start monitoring your Java applications, download our runtime agent for Java (.ZIP) and unzip the archive.
Copy
snyk-java-runtime-agent.jaralongside your application.Create a
snyk-agent.propertiesfile at the location of the agent jar file, containing the project ID of your Snyk project like so:projectId=0462e42b-c92f-4b48-bac8-81eb3ff7f43e.Add the agent as a command-line argument to the Java command used to start your application, for example:
java -javaagent:path/to/snyk-java-runtime-agent.jar -jar my-app.jar.- If you're using Apache Maven, add-javaagent:path/to/snyk-java-runtime-agent.jarto yourMAVEN_OPTSenvironment variable.
- If you're using JavaEE containers such as GlassFish, locate theJVM Optionsand add-javaagent:path/to/snyk-java-runtime-agent.jaras an option.
Coming Soon
We plan to release our runtime offering out of Closed Beta in the next couple of weeks, after gathering your feedback.
What's next? Monitoring open source components for malicious behavior at runtime and connecting that with the scan results of the source code is what enables developers to own open source security throughout the application lifecycle, for both known and unknown vulnerabilities.The instrumentation of the application at runtime enables creating many more capabilities on top of the runtime-based vulnerability prioritization released today, which will be available in the coming months. Stay tuned!
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.





















