AWS re:Inforce 2022 recap
Shilpi Bhattacharjee
August 8, 2022
0 mins readIf you're looking to catch up on what happened at this years AWS re:Inforce, this is the blog for you. There were many important announcements were this year, including some exciting updates on the cloud security front.
In this post, we'll quickly review the goals of the conference and who should attend, before diving into the keynote highlights, software updates, and helpful resources.
What is AWS re:Inforce?
Back in 2019, a few cool things were happening in cloud security. The Cloud Security Podcast kicked off, and AWS decided that they needed a dedicated AWS Cloud Security conference - AWS re:Inforce. This 2-day event brought security practitioners together to discuss AWS services, features, and tools and served as the platform where AWS released new security products, services and features. This conference was canceled in 2020 due to the pandemic, but ran virtually in 2021 and came back in person for 2022.
We attended AWS re:Inforce 2022 this week in Boston, and since AWS is one of the more prominent public cloud providers, we gained some helpful insights for the future of cloud security from the KeyNote highlights and updates.

Who should attend?
If you have been wondering if you should attend the next re:Inforce, the conference aims at Level 200 - 400 (intermediate to expert) and is a good opportunity to meet all sorts of cloud security practitioners. From engineers and architects, to CISOs who are currently using, or looking to use, AWS as part of their cloud strategy.
It's a great opportunity to connect with AWS experts, and learn what they are seeing in the industry, as well as the common trends and concerns their customers are bringing to them — which are sometimes presented as talks at the event. There will definitely be interesting moments that help you feel less alone in the security world.
So, if you have a passion for security, are currently working with AWS, or want to learn more about how it can help you solve security challenges, this is a valuable conference to attend. Though the talks are made available online right after the conference, the hallway conversations with experts and in-person chalk talks are reason enough to attend.
Additionally, fwd:cloudsec — one of the largest and most well-known, independent cloud security community conferences — usually happens the day before AWS re:Inforce, so it's a great week to soak up a lot of cloud security awesomeness (aka knowledge and insights). There may just be a cheeky Cloud Security Meetup around too.
So now that you know what AWS re:Inforce is, and we’ve potentially convinced you to attend, the key takeaways and updates you may have missed this year.
AWS re:Inforce keynote takeaways

Security should be baked in from the beginning
Amazon’s Chief Security Officer, Stephen Schmidt, shared the key message that security should be baked into products and services. Things like infrastructure as code (IaC) security, developer first security, software composition analysis, and secrets scanning are going to be top of mind for the cloud security space in the coming years. Comprehensive security isn’t bolted on after building something, it must be a priority from the very beginning of the process — which is why AWS recommends it to customers as a best practice.
He spoke about having software development engineers as Security Guardians who do not report the organization’s security teams.This would function a lot like the type of Security Champions program Snyk encourages, which is part of your company’s existing DevSecOps or developer-first application security programs.
In speaking to cloud security practitioners and experts at the event, and after on various forums like twitter space for AWS Re:Inforce 2022 Recap, it was clear that clickops, the move from decentralized to centralized security, is the natural evolution for the cloud space — alongside automation to mitigate the time consuming factors.
Leena Smart, from MongoDB, also shared their experience with running a successful security champions program for over two year and gave advice on steps other teams can take to reap the same benefits.
Identity based policies and appropriate permissions
The conversations about identity and access management (IAM) and least privilege, or generally knowing who has access to what and why, have always been important in the context of cloud..
Schmidt summarized the topic perfectly by saying, “overtly permissive environment guarantees you headaches”. Around the floor, there was interest in graph technology and the ability of cloud security solutions to provide clear, easy to digest visibility into complex identity permissions. AWS Vice President and Chief Information Security Officer, CJ Moses, mirrored Schmidt’s sentiments in his keynote address, sharing that baking security into the CI/CD pipeline and SDLC will make security reviews quicker and uneventful.
What’s my sensitive data and how do I find it?
After the breaches and vulnerabilities that surfaced this year (Log4J I am looking at you), many people are asking what their sensitive data is, as well as how to find it and make sure it's appropriately protected. Schmidt shared, and we agree, that stored data should be intentionally controlled and encrypted.
There is a strong need for context around vulnerabilities as the industry grapples with resource shortage and alert fatigue from an excess of alerts and dashboards. People are asking for more automation and prioritization to help them understand what’s critical right now, and what resources are at risk if they don’t comply with the organization's security policy.
Stronger together and layered defense
The theme of being stronger together — as an organization and community — came through strongly in the keynote. CJ Moses added that we win and lose together, and the culture of security should emphasize that everyone is an owner. He elaborated that security should not be the “office of no” but a partner that says “yes but”.
This probably extends to cloud security providers. But as someone once mentioned to me, shared responsibility without well-defined roles can mean no one takes responsibility.
There was also a callout for a truly holistic approach. Organizations need to have a layered defense strategy, since any single control can easily fail. Multiple layers of defense with a good understanding of shared responsibility is what organizations can expect as they adopt cloud security.
The updates and what they mean for cloud security practitioners
There are plenty of reasons to attend AWS re:Inforce, but it's also the place where new AWS security products and features get announced.
So, what was in store for us this year, and what do they actually mean? While there weren’t any major new service releases, some were rebranded and relaunched, alongside quite a few additions to existing services. Though some limitations have been pointed out (e.g. GuardDuty’s Malware Detection only scans once it has detected an issue but does not side scan), changes have been welcomed as they are steps towards democratizing security for organizations that may not have extensive cloud security expertise.
Amazon GuardDuty Malware Protection for EBS volume + integrations with Security Hub
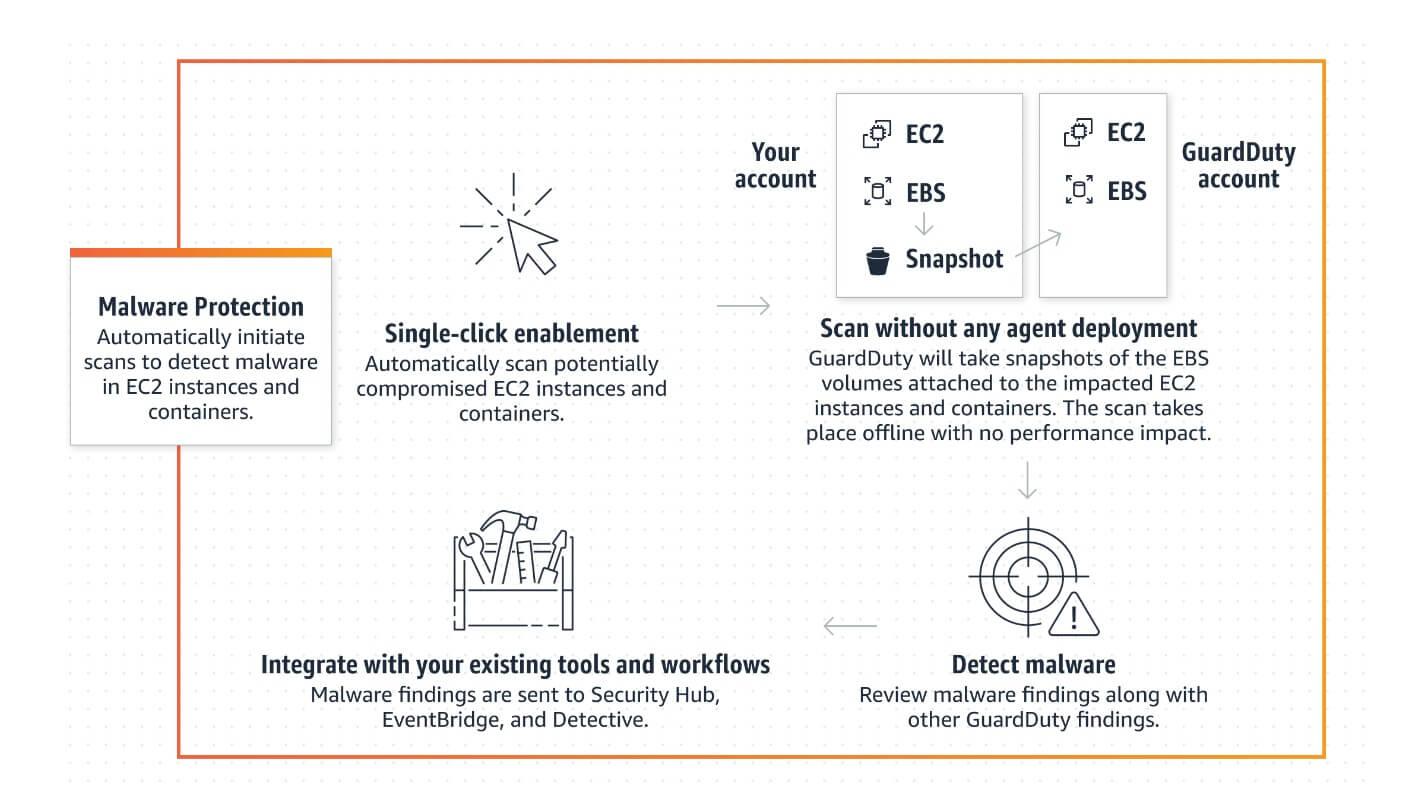
Amazon GuardDuty has been around in 2017, and is designed to intelligently detect threats in your AWS accounts. Its threat detection service continuously monitors your AWS accounts and workloads for malicious activity, and gives you security findings for visibility and remediation. Not to be confused with Amazon Inspector, which is their vulnerability scanning tool to identify potential security issues in your EC2 instances.Amazon announced the addition of agentless Malware protection to Amazon GuardDuty. Amazon GuardDuty was already monitoring for malicious activity, but now it can also detect if any of your EC2 instances or container workloads running on EC2 are doing something malicious. These findings are automatically sent to your GuardDuty console, and then sent, via Amazon EventBridge (serverless event), to AWS Security Hub (cloud security posture management service) and AWS Detective for incident investigation.
If you are wondering how this is different to AWS inspector, you aren't alone. They are intended to complement each other and offer protection at different layers. With AWS inspector offering protection against vulnerabilities as an entry point for attackers, and the Amazon GuardDuty Malware Protection protecting against malware on actively running workloads.
Practitioner's Perspective:
In some organizations, developers are often tasked with security items to fulfill compliance requirements. The announcement of updates like this may assist with wider adoption of services like AWS GuardDuty
Amazon Detective for Elastic Kubernetes Service (EKS)
For those following along, preview mode for Amazon Detective was launched at the very 1st re:Inforce in 2019,and later made generally available in March 2020. It’s a fully managed AWS service that brings together AWS CloudTrail, VPC Flow Logs, and Amazon GuardDuty.
These 3 services log what's happening in your AWS account, but when a security issue arises, you still need to translate these logs to understand what actually happened — that’s where Amazon Detective comes in. It combines the logs from these 3 services, applies a sprinkle (or maybe more) of machine learning, a dash of statistical analysis, and some graph theory to give you a meaningful answer.
AWS Cloud Trail basically tells you who did what in your environment by logging account activity, API usage, and actions across your infrastructure.
VPC Flow logs captures information about the IP traffic going to and from network interfaces in your Virtual Private Cloud
Now, they’ve expanded this service to EKS. Meaning that you can use these same tools to inding root cause of security issues and suspicious activity in your EKS clusters — even with the increasing adoption of Kubernetes when deploying workloads in AWS
Practitioner's Perspective:
Now, EKS consumer’s don’t have to rely on hacks to start inspecting logs from their kubernetes environments. They can also leverage AWS Detective for their EKS instances for additional metrics.
AWS SSO (Single Sign-On) rebranded as IAM Identity Center
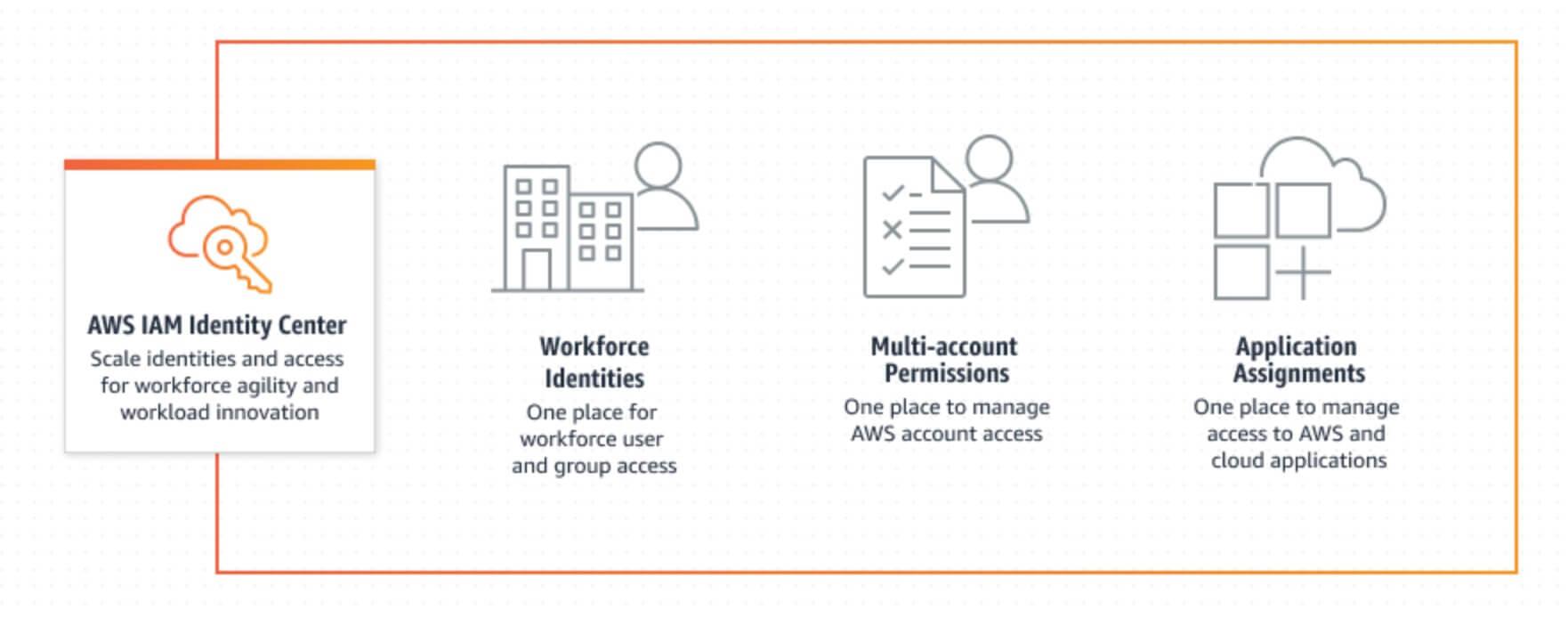
When considering the importance of least privilege, this makes sense. IAM best practice suggests that we should segment workloads and environments into separate AWS accounts. However, we’ve lacked access to the tools required to do this, and some users have turned to AWS SSO to achieve it.
With this rebranding, AWS is steering more users in this direction, and ensuring the rebranded IAM Identity Center becomes the central place to manage access across AWS.
Identity Center now also supports permissions, boundaries, and customer-managed IAM policies, and AWS Lambda now supports authorization based on tags. Meaning that access can be tailored to specific accounts and improve permission management at scale
Practitioner's Perspective:
This is a small, yet significant, change in building the Identity and Access Management. Using Single Sign On as the driver of identity reduces the use of AWS IAM users and leaked access keys, which are often behind security breaches.
New Amazon S3 objects Validation capability for Amazon Macie
Amazon Macie is Amazon’s fully managed data security and data privacy service. It uses machine learning and pattern matching to discover and protect your sensitive data in AWS. It now allows for one-click, temporary retrieval of up to 10 examples of sensitive data found in Amazon Simple Storage Service.
Practitioner's Perspective:
Previously you could only see the location of the sensitive data. Now, you can see the location and content of your S3 objects that were identified as sensitive
AWS Config now supports compliance scores
AWS also announced that AWS Config now supports compliance scores as an enhancement to conformance packs. This will tell you which of your resources are compliant with a set of requirements in the scope of a conformance pack. Compliance scores are emitted to Amazon CloudWatch metrics, allowing for tracking over time.
Practitioner's Perspective:
If you already use AWS Config, and not CSPM or similar tool for measuring compliance scores, this is a welcome change.
AWS Control Tower adopts AWS CloudTrail Organization logging
AWS Control Tower now includes AWS CloudTrail organization logging as part of landing zone version 3.0. The previous version, released at the re:Inforce in 2019, provided you with a landing zone to set up and govern a secure, multi-account AWS environment. Now, AWS CloudTrail trail will be deployed in your management account to automatically log the actions of all member accounts in your organization.
Practitioner's Perspective:
Many still believe that Control Tower has not kept up with the security best practices. However for some organizations, especially in the small to medium spaces where resources and expertise may be limited, it allows you to control your own accounts and guardrails.
AWS Wickr (in Preview)
Amazon acquired Wickr in June of last year and announced the availability of AWS Wickr in preview. It is an end-to-end encrypted enterprise communication service that allows secure collaboration across messaging, voice and video calling, file sharing, and screen sharing.
Practitioner's Perspective:
This could be an interesting play in the fast evolving world of remote work. Looking at their landing page, wickr is being targeted at military, government agencies, enterprise, and individuals — possibly in that order
AWS Marketplace Vendor Insights (In Preview)
In an effort to streamline the complex third-party software risk assessment process, sellers can now make security and compliance information available through AWS Marketplace. On the security front, AWS Marketplace Vendor Insights will check for 150 security credentials in total, and display security certifications and other information on a real-time basis.
Practitioner's Perspective:
The security certifications of Marketplace vendors would be refreshed every 7 days, and are a welcome addition to address the ever growing risk of a broken digital supply chain.
Relaunch of AWS Security Competency for partners
AWS Security Competency for partners has existed for a long time, but AWS just relaunched the program with eight new consolidated categories. These new categories align with the common security problems businesses encounter, so it’s no surprise to see things like IAM, data protection, threat response, and application security there.
Practitioner's Perspective:
Practitioners will be able to identify potential work partners with specific skill sets instead of the broad competency, which used to confuse a lot of AWS customers.
re:Inforce wrap-up
AWS re:Inforce 2022 was a long time coming for AWS security enthusiasts, and practitioners looking to connect with others using AWS to solve security challenges.
Implementing security in the beginning of the cycle, prioritizing least privilege, IAM, data visibility, and security were the key takeaways from the conference — and these themes were emphasized with the rebranding, relaunching, and addition of new features. There weren’t any major announcements, but those following closely believe there were steps in the right direction. The path of democratizing and re-emphasizing that security must be owned by more than just a few people in an organization.
If you want more of AWS Security, you can check out the AWS Series on Cloud Security Podcast or our episode AWS ReInforce 2022 Recap & Highlights
Did you know? Snyk has partnered closely with AWS to leverage seamless integrations with AWS services like AWS CodePipeline, Amazon ECR, and Amazon EKS to apply scalable security solutions across your development workflow. Find out more here.