Automating Kubernetes workload security reporting
Rags Srinivas
March 2, 2020
0 mins readIntroduction
At Snyk, we work hard to continue improving container and cloud-native security solutions. As part of this effort, the Kubernetes integration from Snyk Container now enables you to import Kubernetes workloads and identify vulnerable container images and workload misconfigurations.
Automate your cloud workload security to seamlessly add security checks natively as part of your DevOps pipeline, without requiring further manual steps and centralize monitoring. You can implement mandatory site policies for example by sending cluster details to a centralized console: simply set up annotations in your configuration files and you’re done.
In this blog post, we will use our new product feature and enable new projects to be created in Snyk automatically.
Adding the annotation to automate workload security
Kubernetes annotations enable attaching metadata to objects, such as build release numbers, git branches, pointers to logging information, etc. Once installed, Snyk's Kubernetes controller looks for the annotation key `orgs.k8s.snyk.io/v1`. You'll set the value for that key to your Snyk Organization ID to automatically push essential information to Snyk. Your organization ID can be found in Snyk as follows:
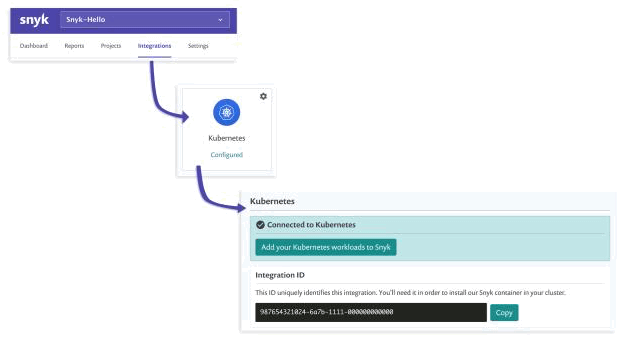
Now, for example, create the filealpine.yamland add anannotations:section. Next, add an annotation in the file starting with `orgs.k8s.snyk.io/v1`.
Make sure you substitute your organization ID as the value for the key `orgs.k8s.snyk.io/v1` in theannotations section. See the example below.
The following manifest file, for example, creates a workload with the annotation attached to it.
1apiVersion: apps/v1
2kind: Deployment
3metadata:
4 name: alpine
5 namespace: default
6 labels:
7 app.kubernetes.io/name: alpine
8 annotations:
9 orgs.k8s.snyk.io/v1: aaaaaaaa-bbbb-cccc-dddd-eeeeeeeeeeee
10spec:
11 selector:
12 matchLabels:
13 app.kubernetes.io/name: alpine
14 template:
15 metadata:
16 labels:
17 app.kubernetes.io/name: alpine
18 spec:
19 containers:
20 - name: alpine
21 image: alpine:3.9
22 command: ['sh', '-c', 'echo Hello from alpine pod! && sleep 360000']
23 resources:
24 requests:
25 cpu: '100m'
26 memory: '100Mi'
27 cpu: '100m'
28 securityContext: {}The added annotation tells the Snyk Kubernetes integration to import vulnerability information about the workload into Snyk automatically.
To create the workload with the annotation set, use the following command:
1kubectl create -f alpine.yamlMonitor the workload from the dashboard
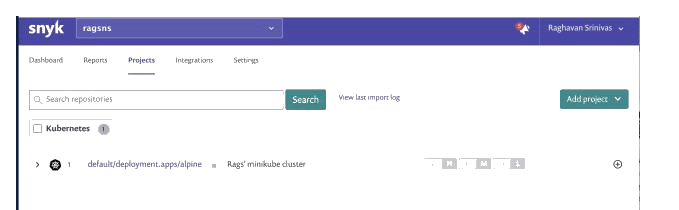
Refresh the browser and voila, you should see the workload information imported into Snyk.
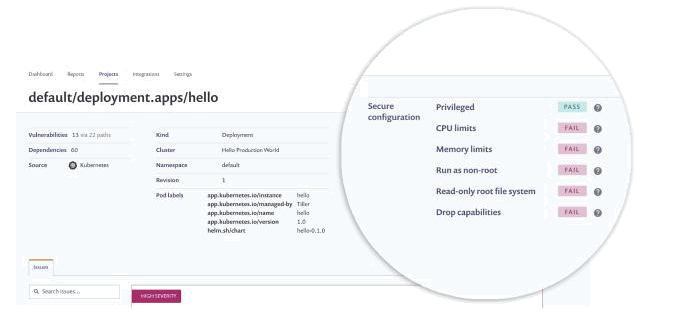
Drill down into the project, and you’ll notice the improper configuration parameters displayed at the top, in the details area. You merely need to modify theYAML file to remedy the configuration problems.
Running a second workload with the annotation attached pushes information on the second workload to Snyk as well, as shown below.
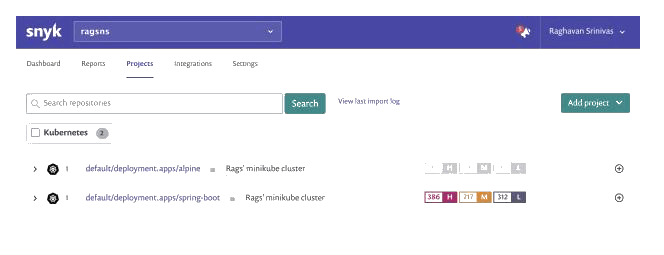
With this new feature, all of the workload information is available for reporting and fixing. Instead of manually adding the details, all you had to do was add annotations to the workloads. Now, you’ve reduced the amount of work you need to perform, and you can easily monitor your clusters as part of your regular workflow.
Summary and next steps
We’ve seen how to push specific Kubernetes workload information to Snyk with an annotation that includes the Snyk organization ID.
That's all that there is to pushing these details for centralized monitoring and increased security on your clusters.
Snyk supports the security of your application development for the entire software development lifecycle, including integrations with your image registry, Dockerfile repository and Kubernetes clusters. Start automating the reporting of workloads into Snyk today. Check out our docs for more detailed information on how to.
Secure infrastructure from the source
Snyk automates IaC security and compliance in workflows and detects drifted and missing resources.
