Announcing Snyk-Powered Linting in Sonar
Tim Kadlec
October 25, 2017
0 mins readWe’re proud to announce that Snyk now powers the vulnerable JavaScript libraries linter in Sonar — an open source linting tool for developers lead by a bunch of folks from Microsoft.
Earlier this year we ran a test on the top 5,000 URL’s on the web and found that 76.6% of them were running a JavaScript library with at least one known security vulnerability. It’s a frighteningly large number. Known vulnerabilities provide an easy attack vector—they’re well-documented and easy to discover at a mass scale. Keeping sites free of known vulnerabilities is critical to improving the overall state of security online.
That’s why we’re excited that some of the best auditing tools for developers have chosen to highlight this problem and, powered by Snyk’s vulnerability database, report on vulnerable libraries to all developers who use them! Embedding into these tools is key to raising developer awareness and making it seamless for developers to notice and understand the risk these vulnerabilities present.
Snyk and Sonar
Sonar started out as an internal project from inside the Microsoft Edge team, but they quickly realized they wanted it to be an open-source, community-driven project backed by the JS Foundation. Sonar lints your site against a number of different best practices and custom rules and gives you a report with the results so you know exactly what you need to improve.
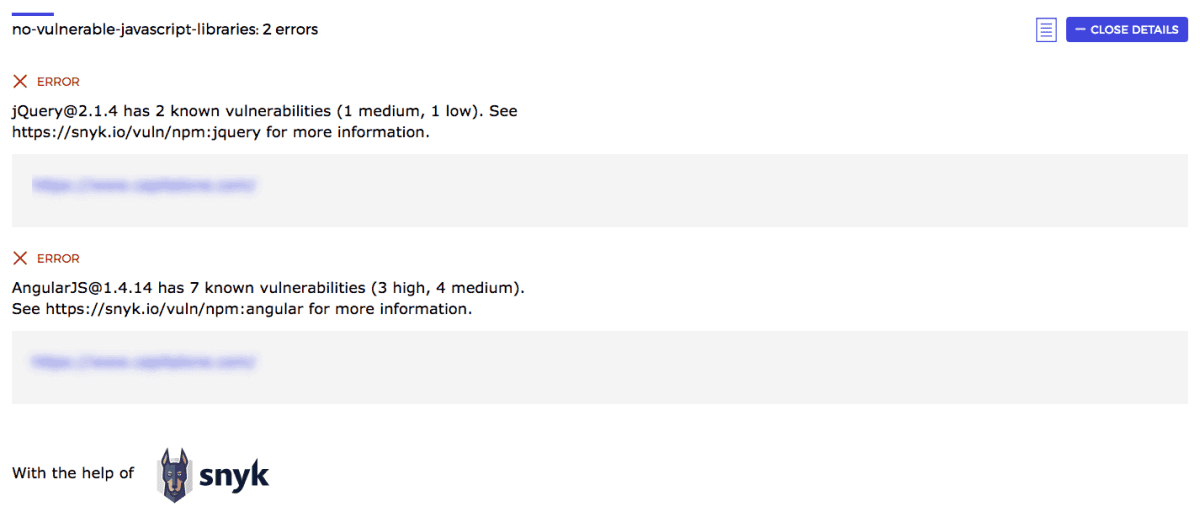
One of the default audits is to check for the presence of JavaScript libraries with known vulnerabilities. For this, Sonar sees what libraries it can detect, and what versions are being used. Then it looks at Snyk’s client-side JavaScript vulnerabilities to see what vulnerabilities might be lurking about. Finally, it outputs the results in your report with links to the issues on Snyk so that you can dig into remediation steps.
Sonar started off as a command-line tool using the sonar npm module, but they’ve just launched their brand new online site scanner as well, to make it even easier to get quick information about the overall health of your site or application.
Security and Developers, Together
Sonar is a fantastic resource for developers, and we’re very excited to help out. Having a default linting rule in place to look for vulnerable front-end JavaScript libraries provides much more visibility into potential security issues, making it easier for developers to address them. With the results in hand, you can quickly jump over to Snyk to find out remediation steps and even fix the issues with an automated pull-request.
You’ll still have to monitor your back-end code for similar vulnerabilities, but exposing front-end vulnerabilities in the tools developers already use and love is a key step to making it as seamless as possible for developers to discover and prevent known vulnerabilites from impacting their site, and their users. We’ll be shedding “light” on another way Snyk is going to make it easier for developers to discover vulnerable front-end JavaScript libraries tomorrow.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
