Want to try it for yourself?
Open Source Security Explained
Open source software security defined
Open-source software security is essential to manage open source components and dependencies to mitigate the risks and vulnerabilities that come with third-party software.
Open source software has become widely used over the past few years due to its collaborative and public nature, simultaneously making it convenient for both developers and malicious actors. Once adversaries discover that an application is exposed to a publicly known vulnerability, they can attack any application developed using that open source code. Cases like the Log4j and Apache Struts vulnerabilities show that this represents a real and sometimes serious risk to organizations.
It’s essential to manage open source components and dependencies to mitigate this risk. Yet, it's difficult to maintain visibility over all the open source components used within an application, and tedious to manually check open source components against databases of known vulnerabilities. Nested dependencies further complicate the matter, since it’s necessary to secure not only the code developers write, but any open source code they consume and any dependencies inside that code.
In this post we’ll define open source security, dive into the risks around open source software, and introduce tools and processes that mitigate the risk organizations face when consuming open source software.
What is open source security?
Open source security is the risks and vulnerabilities that come with third-party software, along with the tools and processes taken to secure open source software. Security tools can automate the discovery of open source libraries and dependencies in code, analyze how those components are used in applications, and trigger alerts or remediation steps whenever vulnerabilities are detected. Practices such as two-factor authentication add another security layer to protect against breaches.
Snyk Report
State of Open Source Security 2022
A look at software supply chain complexity and risk in collaboration with The Linux Foundation.
4 Benefits of open source software
Business demands are driving faster software development and release cycles. To address these demands, developers are increasingly turning to open source software to augment internally developed code.
Its popularity comes down to a few factors:
Cost: Software developers can freely use, modify, and share public domain open source software while a worldwide community of developers and volunteers work to maintain it. Even commercial open source software packages are relatively inexpensive compared to the cost of custom-developing code from scratch.
Ease of use: The pre-built and open nature of open source software means developers can use previously written code to address their specific needs. Leaving more time to work on higher-value tasks.
Quality: Since a community of developers build, utilize, and inspect open source code, there are, theoretically, fewer bugs as vulnerabilities are quickly uncovered and addressed.
Speed: By using open source software, developers can get valuable business applications to market faster.
Open source software adoption has doubled or more in some cases, bringing developers the benefits of economies-of-scale since there are more tools available and better-trained developers entering the market. At the same time, there are tradeoffs between openness and vulnerability, agility and quality.
Using open source software means you’re relying on strangers to maintain the code your applications rely on, so it’s critical to use systems and tools to minimize the potential downside.
3 Open Source software security risks
Almost all cloud-native apps rely on open source components. However, since no one is responsible for their maintenance or security, open source software is laden with risks, including:
1. Vulnerabilities in open source dependencies
These span both known and unknown vulnerabilities. Known vulnerabilities include those assigned a common vulnerabilities and exposures (CVE) number, those disclosed on the Internet, those shared in public vulnerability databases, and ones within private vulnerability databases. In general, the more well-known a vulnerability is, the more urgent is the need to address it.
On top of tracking vulnerabilities, it’s also key to track every open source dependency within an application. Transitive dependencies — where dependencies rely on other dependencies — are a special area of concern because they are less visible to security tools and audits, so it’s helpful to use tools or processes that can identify and audit all the dependencies in an application.
2. License compliance risks
Developers need to understand each type of software license in the open source packages they consume so they can use the code in a compliant way. This requires awareness of the licensing stipulations and enforcement throughout projects. To enforce open source licenses, organizations need deep visibility into how open source components are used. It’s also important to continuously monitor licenses in case the copyright owner changes the license for a library.
3. Unmaintained open source packages
Open source packages are typically maintained by a single developer or a small team, if they’re maintained at all. Developers of community open source projects have no commitment to maintain the software, and it comes “as is.” Hence it’s users’ responsibility to devote the time and resources to ensure that code is safe. Fortunately there are helpful tools that can simplify this process, such as Snyk Advisor, which analyzes packages by maintenance level, community, security posture, and popularity to help you gauge the health of open source packages you’re using.
Curious to read more about open source software risks? Read our post, 5 potential risks of open source software.
Key statistics from the State of Open Source Report
Data is knowledge, so Snyk surveyed developers and security professionals to learn about their open source security concerns, trends in vulnerabilities across packages and container images, and the practices employed by maintainers and organizations in securing their software. We released the findings in our State of Open Source Security report for 2020. Here are some of the key takeaways from the report.
Open source adoption is increasing
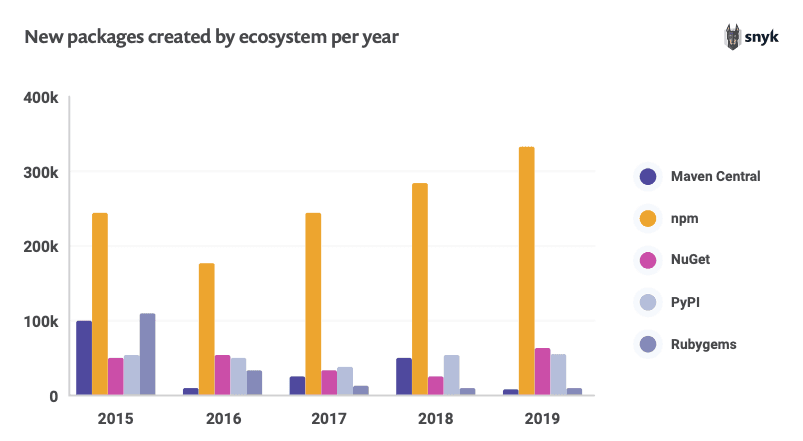
Open source ecosystems are experiencing continuous expansion, thanks to market demands and business realities. The leader was npm, with over 33% year-on-year growth and 1.8 million packages as of March 2022. The majority of OS vulnerabilities continue to be discovered in indirect dependencies:
npm: 86%
Ruby: 81%
Java: 74%
Open source security culture is shifting towards developers
Respondents indicated they see security as a responsibility that is shared across departments:
85% felt developers were responsible for open source security
55% felt security teams were responsible
35% felt operations had a role to play
Vulnerability trends
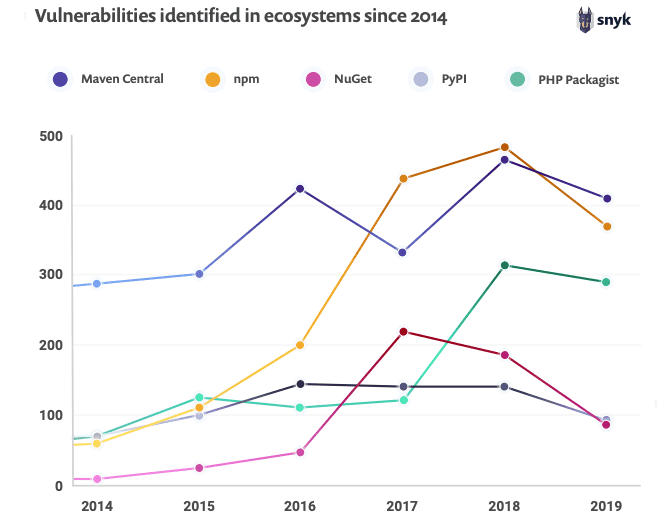
New vulnerabilities were down by 20% across the board, with cross-site scripting (XSS) vulnerabilities being the most commonly reported.
Container & orchestration challenges
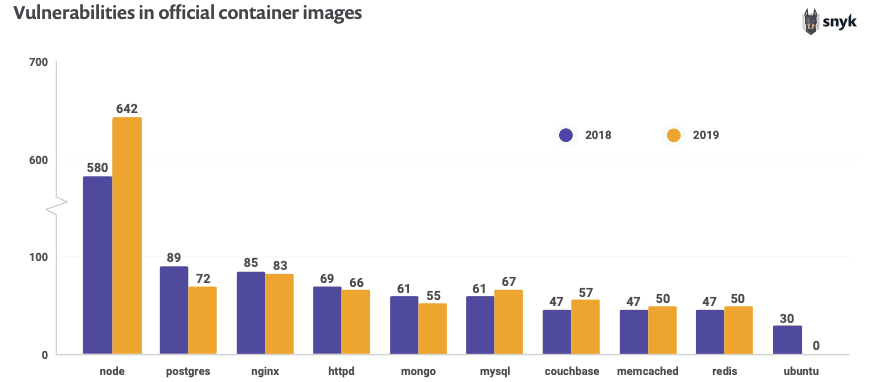
Official base images tagged as latest often include known vulnerabilities, most notably the official node image which has almost 700 known vulnerabilities. Over 30% of survey participants do not review Kubernetes manifests for insecure configurations, and requirements for security-related resource controls in Kubernetes are not widely implemented.
Open source security trends in 2022
Over the past year, we’ve seen a few trends dominating the conversation related to open source security, including supply chain security, cultural shifts around responsibility, a drop in the newly discovered vulnerabilities, the reliance on volunteer open source maintainers, and shifts in expectations around vulnerability remediation.
Supply chain security attacks are more common
Third-party software components live in a centralized repository, which makes up the software supply chain. This supply chain is an attractive attack vector since bad actors can attack vulnerable points in the development pipeline without needing to change software repositories: for instance, by exploiting design flaws with a dependency/namespace confusion attack, or exploiting third-party components to compromise user data and access internal systems.
Each link is a potential attack vector, so it’s important to secure the supply chain from source code to deployment. Supply chain vulnerabilities are not a new issue but were at the center of conversation in 2021 and were a recurring theme in President Biden’s cybersecurity executive order.
Shift in culture towards a shared responsibility for security
Who should be responsible for security? One of the most exciting trends we’ve seen is a shift towards shared responsibility among developers, security, and operations teams.
The shift towards a DevSecOps approach is positive, but 47% of respondents said they have no specific programs in place to drive shared responsibility, and only 15% of respondents implemented the security champions programs defined as a key security practice in the OWASP Software Assurance Maturity Model (SAMM). This shows there is a bridge between awareness of the need for shared responsibility and implementation in practice.
Based on Puppet’s State of DevOps report, we have also learned that as organizations mature with their DevOps practices, their security practices also mature.
“As DevOps practices improve, DevSecOps naturally follows. High-evolution organizations have shifted left, with majorities integrating security into requirements (51 percent), design (61 percent), build (53 percent), and testing (52 percent). In contrast, for most mid-level organizations, security is involved when there’s a scheduled audit of production (48 percent) and when there’s an issue reported in production (45 percent).”
Fewer vulnerabilities found
A surprising finding from the report is that new vulnerabilities are down 20% overall. This trend comes at a time when open source ecosystems are experiencing explosive growth, making it particularly noteworthy.
There is no clear reason why the growth of open source vulnerabilities has decreased while the landscape is more than doubling in some ecosystems, but it suggests that improvements in security awareness, practices, and tools are showing results.
We’ll continue to pay attention to this trend, but it’s still too early to become complacent around security controls and practices.
Open source maintainers are pushing back against corporations
We can expect to see more tension among open source maintainers who are dissatisfied with corporations and organizations monetizing products built with their software without funding the maintainers.
A 2021 Tidelift survey of 400 open source maintainers found that 46% of maintainers are not paid at all, and only 26% earn more than $1,000 per year for maintenance work. Over half (59%) have quit or considered quitting maintaining a project, and almost half of respondents listed lack of financial compensation as their top reason for disliking being a maintainer.
This sentiment is resulting in real-world consequences. For instance, in January 2022, the maintainer of the widely used npm package colors introduced offending code that results in an infinite loop and breaks any usage of the package.
The broken version of colors has been downloaded over 95,000 times. Colors is used in multiple other projects including the prompt command line helper (~500,000 weekly downloads) and AWS's own aws-cdk (~2 million weekly downloads), so it’s a major area of concern.
A similar incident also happened with the popular npm package faker, which is maintained by the same person, where the maintainer opened an issue stating they will no longer maintain the projects (which are used at numerous Fortune 500 companies) for free.
Vulnerability remediation timelines are still not meeting expectations
According to the 2020 Open Source Security survey, 47% of respondents said they expect a vulnerability to be fixed within a week of discovery, and nearly 18% expect a fix within a day.
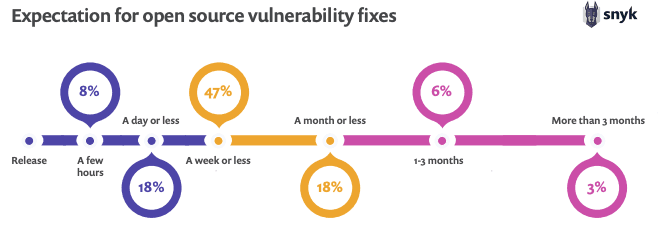
In actuality, only 35% of vulnerabilities in scanned projects were fixed in under 20 days, while 36% took 70 days or more, within an average fix time of 68 days.
It’s clear organizations need to manage expectations around their risk posture. They need to be cognizant of SLAs for open source vulnerability fixes, especially when an individual contributor is responsible for maintaining the code.
Key metrics for your open source security strategy
A good way to start is to be careful about tracking open source security metrics in the libraries you consume. Consider metrics like:
The number of days between when a vulnerability is discovered and when it’s fixed
Average time to merge a pull request when an issue is opened
The time required to fix code yourself
Answering these gives better visibility into your response to security issues in packages you’re leveraging, so you can build a strategy for managing components and uncovering and addressing vulnerabilities.
Furthermore, be proactive with the open source packages you use. Submit pull requests to maintainers so they’re aware of issues. Understand how open source software impacts your business, and build a business case for managing open source software in a systematic way.
6 Capabilities you should be looking for in an open source security tool
Security tools have a key role to play in open source security strategy. They create ways to automatically review open source code for known vulnerabilities, and reference vulnerability databases that can give insight into the potential impact a vulnerability will have, along with steps to remediate any issues. These tools can continuously monitor code production and integrate security and licensing/governance throughout the software development process.
1. Comprehensive view of packages and vulnerabilities affecting them
Since visibility of open source components and dependencies is part of the security challenge, having a way to automatically inventory and evaluate components gives control over the open source environment. Look for automation that identifies components across CI/CD pipelines and evaluates them for the level of threat they pose. Are vulnerable components actually being used by the application?
2. License management capability
Security tools can continuously check third-party and custom code for both vulnerabilities and license risk as code is written in the development environment, eliminating the need to scan code repositories.
3. Automation
Security tools allow you to automatically monitor and detect vulnerabilities. In the event of a breach, tools can then triage the damage and develop an appropriate response. You can set policies around fixes, requests, patches, and dependency upgrades to automate these processes as well.
4. Direct integrations into developer tooling, workflows, and automation pipelines
Integrating security directly into developer tools and processes helps streamline the process of securing code. Plugins allow developers to easily apply fixes directly within their CLI or IDE. GitHub integrations allow you to test repositories, projects, and pull requests and apply fixes with automated pull requests.
5. Up-to-date and enriched database that goes beyond known CVEs
Security tools go beyond public databases of known vulnerabilities to build proprietary, curated databases. These vulnerabilities include those with CVE numbers, those on security advisories, those identified by issue trackers, and those discussed on forums or social media, among others.
6. Continuous monitoring of projects
Security tools can continuously monitor applications in production to automatically prevent exploitation of vulnerabilities. This results in applications that effectively monitor themselves and are equipped to defend themselves against attacks or licensing issues that arise.
To learn more about how to choose a security tool to monitor open source components, read our guide, How to Choose SCA Tools.
6 benefits of using Snyk for your OSS Security
Snyk Open Source provides a developer-first security tool that embeds application security into the entire software development pipeline, allowing you to create and deploy applications built with open source software while securing code against vulnerabilities and licensing issues.
1. DevSecOps compatible
Snyk Open Source integrates into the SDLC from the first line of code. We’ve invested significantly into integrations to make security and license scanning as seamless as possible. This makes developers directly responsible for the security of their applications and allows for productive loops with security and operations teams.
We’ve also created a DevSecOps Hub, which highlights technology, processes, and people to help organizations develop a DevOps culture that effectively integrates security; and our DevSecOps Community which brings developers and security leaders together through a Support portal, virtual and live events, and an Ambassador program that supports security champions with a more direct connection to Snyk.
2. Fix issues within embedded developer workflows
Snyk Open Source embeds within developer tools like Atlassian Bitbucket, Visual Studio Code, Maven Central, GitHub, and JetBrains, allowing developers to access Snyk and uncover vulnerabilities and licensing issues within their tool of choice.
3. Low false positives
Snyk's team of security experts manages its database to ensure a low false-positive rate. They analyze and test each item in the database, assign a CVSS score and vector to each vulnerability, invest in proprietary research to uncover new vulnerabilities, and include hand-curated summaries with code snippets where applicable.
4. Dependency tree view
Snyk uses your application’s package manager to build a dependency tree and displays it in the Snyk UI. This helps to visualize which component is causing an issue and helps Snyk address it, even if the component is a transitive dependency. It also makes it possible to automate the process of building a Software Bill of Materials (SBOM) directly in developer workflows. Once you have your SBOM, you can check it for security vulnerabilities using Snyk's SBOM Checker.
5. Automated fixes
Snyk automatically suggests fixes for vulnerabilities from within the CLI, IDE, and CI/CD pipelines whenever they’re available. When fixes are not available for a dependency, Snyk can notify you when a fix becomes available or when new vulnerabilities are discovered for that vulnerability.
6. Governance/Licensing
Snyk Open Source License Compliance Management allows you to manage licenses from within developer workflows using automated policy enforcement and granular management. This allows you to monitor every step, from the first line of code to the deployed application, to ensure your projects do not violate any licenses.
Scan your open source dependencies for vulnerabilities
Automatically find, prioritize and fix vulnerabilities for free with Snyk.

FAQ Section
What is open source security?
Open source security refers to the risks developers and security teams are facing today when running third-party, open source code in their applications, and the processes, methodologies, and tools they are deploying to mitigate them. Recent attacks exploiting vulnerabilities in open source code have exacted huge costs from organizations, highlighting the importance of open source security and the need to execute and monitor related security strategies.
Why is open source security important?
Open source is powering the digital transformation we are witnessing today and is used by companies of all sizes, in all industry verticals. Yet it also comes with risks. Acknowledging these risks is an important first step, but should be followed up with investment and maintenance of a well-articulated open source security plan that includes continuous security testing and monitoring.
What is the risk of open source?
Developers are pulling in vast amounts of open source dependencies without any security control or visibility. These open source components are maintained by volunteers outside the organization, but maintainers have no obligation to update or secure components. Furthermore, due to its public nature, bad actors can learn about and exploit vulnerabilities whenever developers become aware of them. These are several of the risks of open source software.
Next in the series
Open Source Audits Explained
Open source auditing checks the open source software used in your applications for security vulnerabilities and license violations within the open source libraries or between the open source software and the product company.
Keep reading



















