Static Code Analysis Explained
What is static code analysis and when should you use it?
One of the fundamental building blocks of software is code quality. Improved software quality is directly linked to high-quality code. The quality of your code correlates with whether or not your app is secure, stable, and reliable. To sustain quality, many development teams embrace techniques like code review, automated testing, and manual testing.
While code review and automated tests are important for producing quality code, they will not uncover all issues in software. Because code reviewers and automated test authors are humans, bugs and security vulnerabilities often find their way into the production environment.
According to the State of Cloud Native Application Security Report, misconfiguration, and known unpatched vulnerabilities were responsible for the greatest number of security incidents in cloud native environments.
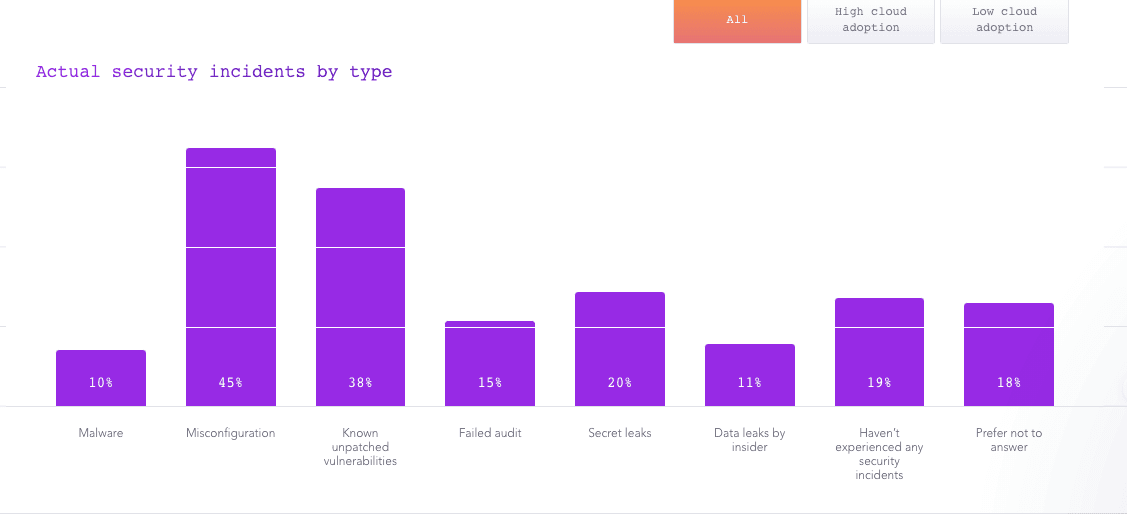
Source code analysis could prevent half of the problems that often slip through the cracks in production. Rather than putting out fires caused by bad code, a better approach would be to incorporate quality assurance and enforce coding standards early in the software development life cycle using static code analysis.
What is static code analysis?
Static code analysis, also known as source code analysis or static code review, is the process of detecting bad coding style, potential vulnerabilities, and security flaws in a software's source code without actually running it, a form of white-box testing.
Static code analysis will enable your teams to detect code bugs or vulnerabilities that other testing methods and tools, such as manual code reviews and compilers, frequently miss.
The fast feedback loop is a key tenet of the DevOps movement. Static code analysis helps you achieve a quick automated feedback loop for detecting defects that, if left unchecked, could lead to more serious issues.
Static code analysis is not only useful for checking code styles; it can also be used for static application security testing (SAST).
At a high level, a static code analyzer examines source code and checks for:
Code issues and security vulnerabilities
Quality of documentation
Consistency in formatting with overall software design
Compliance with project requirements, coding standards, and best programming practices
Violations of rules and conventions that affect program execution and non-functional quality aspects of a software system such as complexity and maintainability
Next, we’ll discuss why you should integrate static code analysis as part of the software development process.
Static Code Analysis (SCA) vs Static Application Security Testing (SAST)
Static Application Security Testing (SAST) applies static code analysis to find security issues. In general, static code analysis can be used to find various types of issues like style, formatting, quality, performance or security issues. SAST tools are designed specifically to find security issues with high accuracy, striving for low false positive and false negative rates, and providing detailed information about root causes and remedies of spotted vulnerabilities.
Choosing a Static Code Analysis Tool
Static application security testing has progressed significantly. Many modern SCA tools integrate into DevOps and agile workflows and can analyze complex, large codebases. This means better coverage, less confusion, fewer interruptions, and more secure applications.
But not all static code analysis tools offer robust features. For example, some are not environment- or platform-agnostic; and some support a limited set of frameworks and languages. In this section, we'll focus on helping you choose static code analysis tools that will help secure your application, which are primarily SAST tools.
Choosing a Static Application Security Testing tool depends on a number of factors, including your development environment, security budget, existing tools, frameworks, codebase size, languages, and development workflow. It’s crucial to choose the right static code analysis tool to boost productivity while minimizing developer frustration and additional costs.
Here are some questions to consider when choosing an open source or enterprise tool:
Is the tool developer-first?
Does it support industry coding standards?
Is it paid or free?
How hard is it to set up and use?
How accurate are the results?
Does it offer reporting and alerting functionalities?
Does it support your programming languages?
How actionable and reliable are the analysis results?
Does the tool provide summaries for code and security vulnerabilities?
How well does it integrate with your existing software development processes?
Open Source Static Code Analysis Tools:
Here are some of the top options for open source static code analysis tools. The tools in this list are either fully open source, or have a free tier.
Snyk Code: Available in a free plan, Snyk Code is a developer first SAST tool that covers a variety of languages including Python, Java, JavaScript and C++. Snyk works alongside developers as they code, and provides them with the information they need to prevent vulnerabilities from entering the codebase.
Bandit: Bandit is an open source tool designed to find common security issues in Python code.
Brakeman: A free vulnerability scanner designed for Ruby applications .
Spotbugs: Formerly known as "FindBugs" Spotbugs is a well known open source code analysis tool for finding bugs and vulnerabilities in Java code.
Graudit: Graudit is a script and signature set that allows you to find security flaws in source code using the GNU utility Grep.
Now let’s explore how to integrate SAST tools into the DevSecOps pipeline.
Making Static Code Analysis Work for You
Most development teams begin by statically analyzing code in the local environment through a manual process. But bottlenecks such as enforcing compliance become apparent over time, especially in an open source project with distributed contributors.
Integrating static application security testing into your entire DevSecOps pipeline is one way to ensure compliance. SAST tools like Snyk Code offer more robust integration through the DevSecOps life cycle and provide the highest levels of coverage you need to identify security risks for OSS containers, libraries, software, and other artifacts that may have open security vulnerabilities.
Here is what the MongoDB team leveraged:
"Before Snyk, our approach to open source was time-consuming and slow. We did many manual checks before releasing some of our products; we use a collection of smaller tools for others.
Our security team evaluated several SAST solutions in the market, and eventually adopted Snyk Code because of its automated remediation, developer-first approach, ease of use, quick deployment, and direct integration with developer tools and workflows like GitHub."
It’s not enough to statically check code locally; you must also incorporate SAST into your CI/CD pipeline. This will allow you to perform automated code reviews on your entire app portfolio throughout the pipeline and create sustainable, secure, and safe applications.
Second, you have to choose the right tool. Most SAST tools have poor accuracy and long scan times, eroding developer trust and returning far too many false positives. They’re ineffective and impede speed and agility. When there are too many false positives, teams start paying less attention to alerts.
A reliable modern SAST tool should be developer-friendly, less false-positive, and fast.
Likened to a spell checker for developers, Snyk Code is a static code analysis tool that scans for security vulnerabilities 10-50 times faster than other SAST tools, employs semantic analysis to uncover code performance and security bugs, reduces false positives to near-zero levels, makes developers' efforts more actionable and efficient.
Adopting the right SAST tool and integrating it into your pipeline will help you embed security into your pipelines and protect against vulnerabilities and issues that frequently make their way into production environments.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.