Prioritizing container vulnerabilities with exploit maturity
2020年9月9日
0 分で読めますHopefully, you’ve had a chance to catch up on Snyk’s launch of prioritization features that work across our product line. But if you haven’t you should definitely check out our blog post on the Priority Score feature and how Snyk uses Kubernetes details to influence the prioritization of vulnerabilities. Today, we want to share another bit of vulnerability detail that Snyk adds to help you prioritize which container vulnerabilities to fix: exploit maturity for Linux vulnerabilities.
This new data helps you quickly decide which vulnerabilities to focus your efforts on, which is particularly important in the container ecosystem as it’s not unusual to find 100s of vulnerabilities in a single container image. We’re pleased to announce that this exploit maturity data is now available in Snyk Container vulnerability scanning, and it’s a built-in factor in our new Priority Score calculations.

What is exploit maturity for containers and how does it influence the risk of a vulnerability?
Snyk’s security team started adding exploit maturity details to open source vulnerabilities in 2019 to help developers decide which issues to fix first, so the concept isn’t new. We refer to the maturity of any exploit code (exploit maturity for short) to measure how practical a vulnerability really is in the real world, relative to:
Whether the exploit has been published (is it “in the wild”?), and;
The actual “helpfulness” of those published exploits—meaning, whether the vulnerability really can be taken advantage of more easily due to those publications.
In other words, if there is no exploit available at all, it will be more difficult to take advantage of a vulnerability. At the same time, even if there is an exploit available, that does not necessarily mean that the vulnerability can easily be breached without some level of expertise.
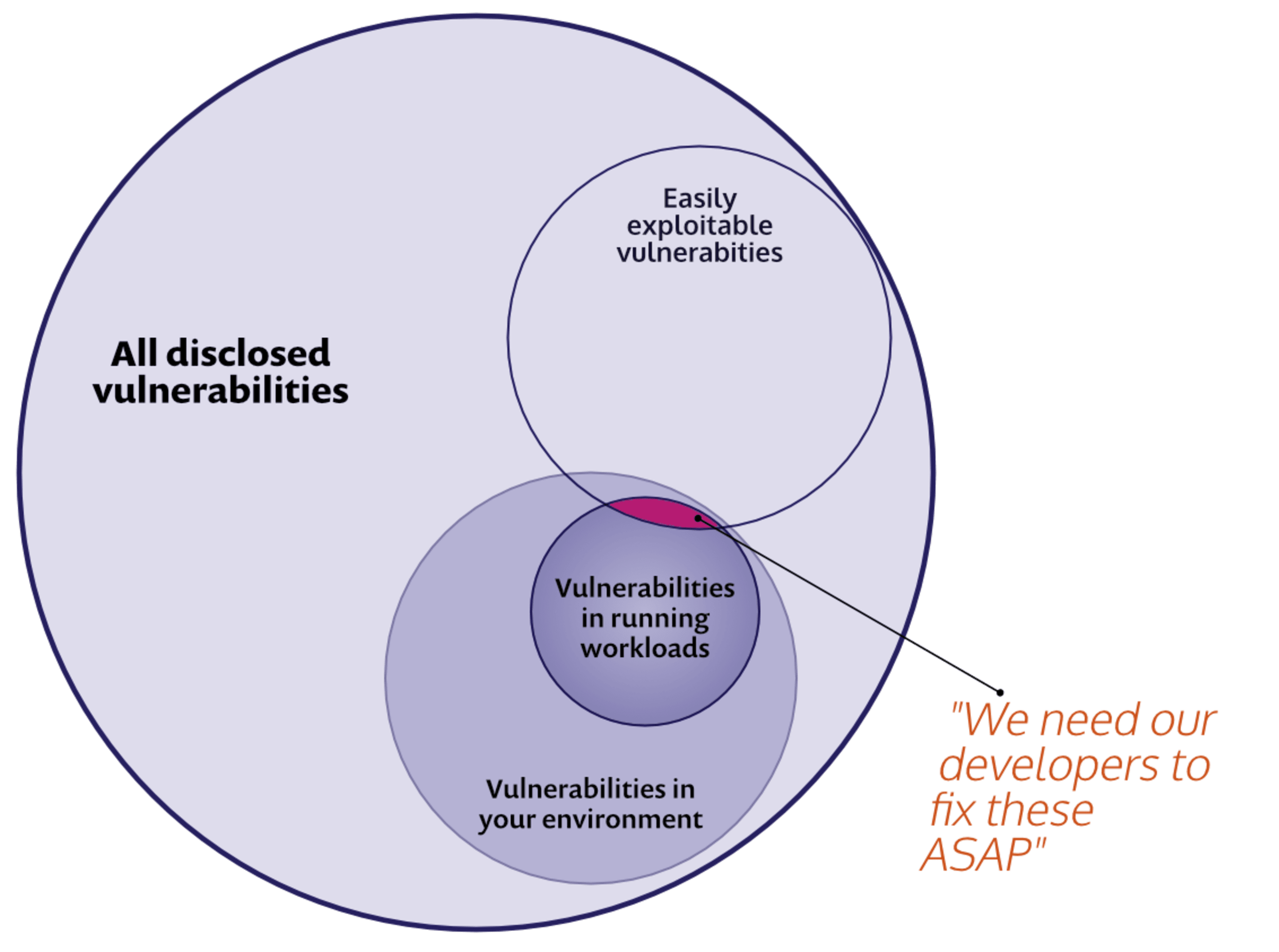
If you know the details of CVSS scoring, you might wonder why Snyk’s additional exploit maturity details are important. It’s all about usability and action for the typical developer end-user. The CVSS score takes a large number of data points into account. Snyk’s security researchers add exploit maturity details based on their own analysis to our database to make it simple to prioritize container and application vulnerability scanning reports based on the existence of exploits and their implementations.
Using Snyk Container exploit maturity in your workflow
We can look at a common use case, to see how the new Linux prioritization capability can be used in your workflows. We hear often that the first time folks see a container vulnerability report it can be...a little daunting. There might be hundreds of vulnerabilities in a given image. With Snyk, we’d start by identifying the base image and helping to pick an alternate, since that’s one of the fastest ways to cut out many vulnerabilities at once.
But there might still be many vulnerabilities left, so to focus your efforts, you want your app teams to focus on vulnerabilities in active workloads running in your Kubernetes clusters that also have mature exploits. Second, you want to provide similar results as part of your pipeline tests to flag vulnerabilities in container images that have “Mature” exploits with a “High” severity.
Finding and filtering container security vulnerabilities based on Exploit Maturity
The first part is to focus on running workloads that have matureor proof-of-concept exploits available. After all, these are actively running in our clusters and thus represent a particularly dangerous vector of attack.
Snyk makes it easy to view your vulnerabilities using the exploit maturity data for Linux vulnerabilities in conjunction with with the Kubernetes workload configuration data. Below, I’ve started with a report for my organization that shows only the vulnerabilities that are:
running in my cluster (the Projects filter) and
have a Mature or Proof of concept exploit.
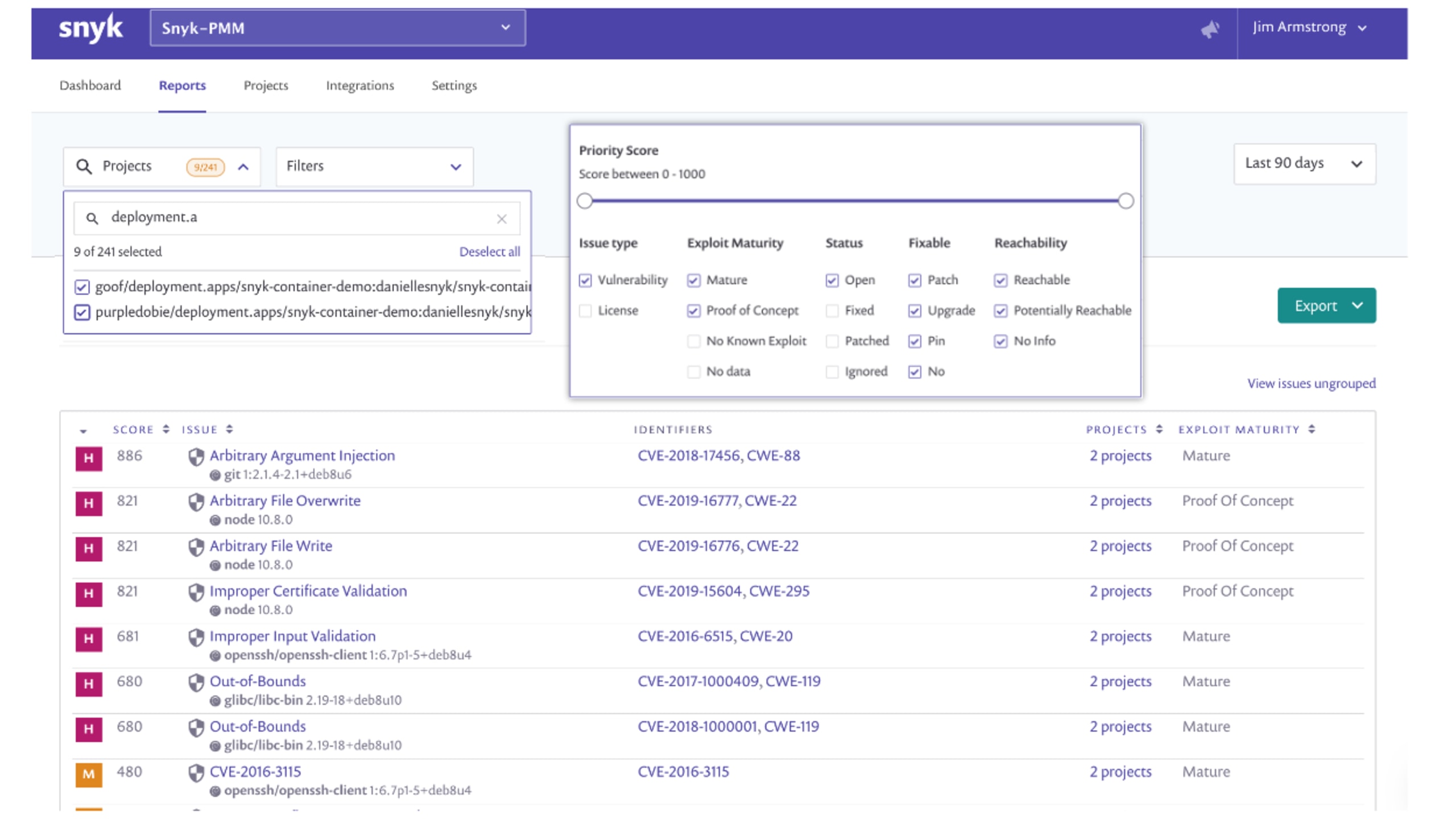
In this case, my report shows many detections matching these criteria and I can drill into one of those projects, as shown below, to get more specific details. You can see in the project view that I have once again filtered using Exploit Maturity (left side of the screen) and that I have an additional indicator of a mature exploit for the result shown. This information, combined with other factors such as the configuration of the running pods in the cluster, also informs the Snyk priority score.

Getting started
If you have a Snyk account and you’ve started using our Snyk Container product, you can begin using Linux exploit maturity data right now. Exploit maturity is part of all Snyk plans! If you haven’t tried Snyk Container, it’s also free to get started.
Get started with the Snyk Container walkthrough on Snyk Solutions Center.
Check out the Snyk Container documentation.
Stay secure!
開発者ファーストのコンテナセキュリティ
Snyk は、コンテナイメージと Kubernetes ワークロードの脆弱性を検出して、自動的に修正します。