5 ways Snyk helps you to prioritize and fix your vulnerabilities
Josefa Riveros
18. Februar 2020
0 Min. LesezeitOur team has recently made some updates to how our reporting looks and feels, making it even easier for you to build out reports on application security that can be impactful for your company.
Struggling to put order into chaos?
Imagine you’ve just moved into a new house and bought some 'ready to assemble' furniture - how hard can it be, right? As you open the boxes, you're faced with a million screws, washers, weird plastic bits. "Is this part of the furniture or just part of the box?", you wonder to yourself. Suddenly, you start feeling overwhelmed with the mess laying out in front of you. Then you remember — this doesn't have to be so scary. There's an instruction manual! After some elbow grease (and a couple mistakes), you kick your feet up, feeling accomplished.
This is a pretty familiar feeling for lots of our customers when it comes to fixing the vulnerabilities in their projects. Unfortunately, in this case there's no instruction manual because every team has its own set of priorities. You've run a bunch of tests and now there's a pile of vulnerabilities staring back at you. "Is this vulnerability actually introducing a risk or is it something we can worry about later?", you wonder to yourself. There's that feeling again of being overwhelmed.
Where do you even start?! How can you prioritize these vulnerabilities so that your teams can make progress and have that same "I did it!" sense of accomplishment?
We've found that our customers can get really creative with our reporting, taking that pile of vulnerabilities and turning it into something more manageable that they can feel proud of. So, as part of the product development process, we asked them how they use reports, and learned a lot about what works for them.
We’d like to share some of these ideas with you, because while there is no single clear set of instructions, there are some tried and true methods that can help you better prioritize your company's vulnerabilities and start reducing that vulnerability count.
Creating a prioritized list for your developers
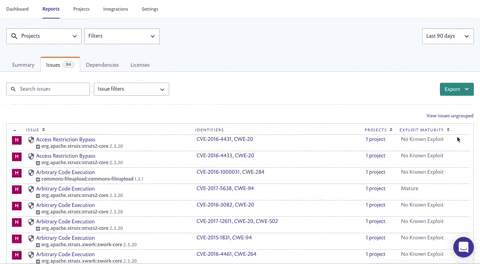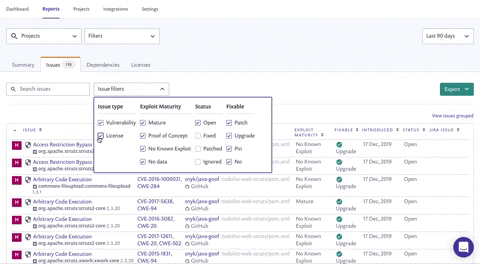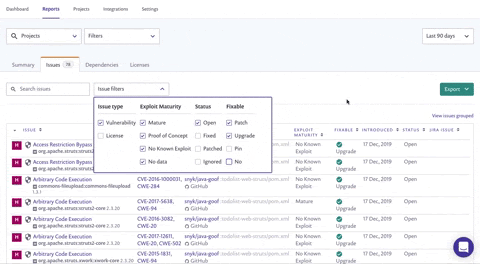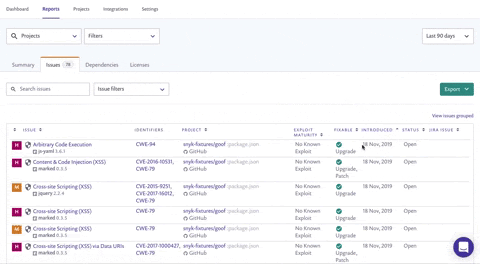
Back in November, we released exploit maturity data from the Project results and it has quickly become a favorite among our customers. Now, you can also filter on exploit maturity within the Issues tab in the Reports area to identify the specific vulnerabilities affecting your projects that have exploits in the wild ("mature" exploits as we refer to them). Security vulnerabilities with issues that have known exploits are considered much riskier than those that don’t and should be tackled first.
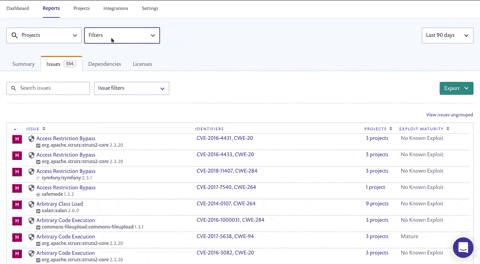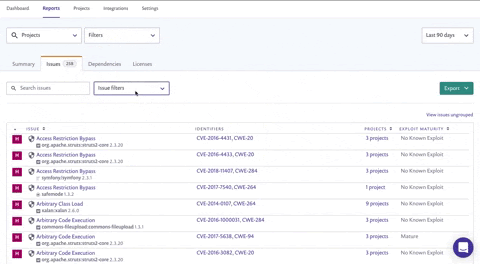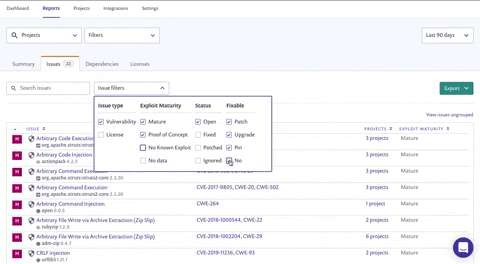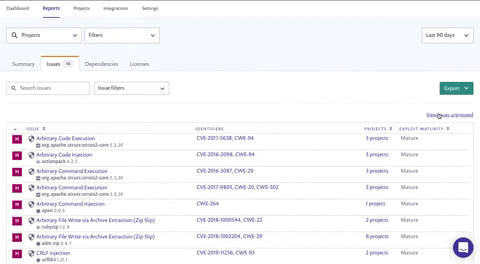
The Issues filters list now enables you to filter by:
Issue type - choose just Vulnerabilities to focus on security
Exploit maturity - choose Mature to focus on the highest risks in your project
Status - choose Open to focus on vulnerabilities you haven’t handled yet
Fixable - filter for vulnerabilities that can be fixed with the patch and upgrade options
We recommend that you narrow the scope further for even more actionable information: filter the data by "High Severity" from the top-level Filters list, and "Fixable" from the Issue filters. By doing this, you and your team can focus on the highest-risk vulnerabilities that can be fixed with relative ease by your developers. Filtering on high severity and "upgrade" or "patch" will provide you with a list of all projects that contain fixable, high-severity vulnerabilities that are also quick and impactful wins for your teams. Share this list with your team so they know which vulnerabilities to tackle first!
Sorting for fast action
Once you’ve filtered, your list might still be daunting.No worries though! You can further improve focus and priorities: view the grouped issues view and sort by "projects affected" to see which fixable vulnerability is the most prevalent throughout your organization. This allows you to focus on fixing the issues that will have the most widespread impact.
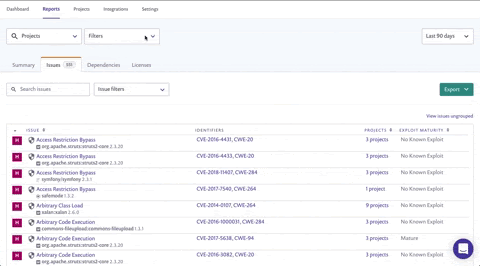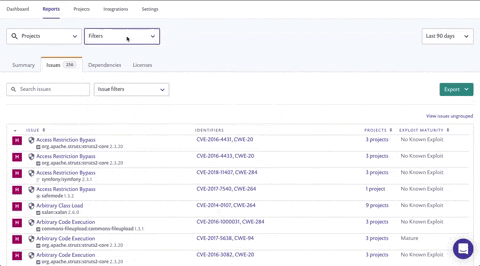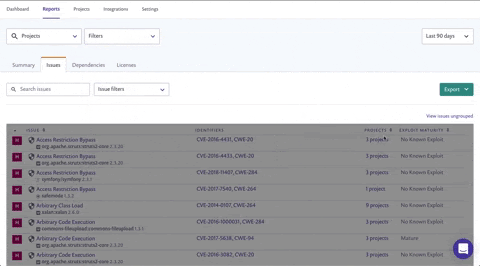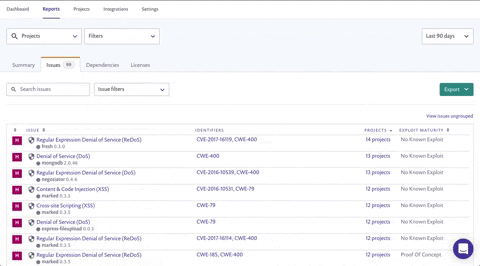
You can also access this list directly from the Summary tab by clicking the text below the high severity issues count, leading to an already filtered version of the Issues tab. Then all you'd need to do is sort the projects column.
Once you’re done with the highs, move onto the mediums!
Targeting dangerous vulnerabilities and avoiding data breaches
When the next event-stream or remote code execution vulnerability surfaces, every minute that goes by without a fix is critical; however, pulling together a list of all your affected projects can be a real headache.
Using the Search issues field on the Issues tab, search for a specific CVE (CVE-2018-11776), CWE (CWE-20) or issue type ('struts' for example) and see how many projects are affected. Click view issues ungrouped to view the issues split by individual projects so you can determine which teams to contact.
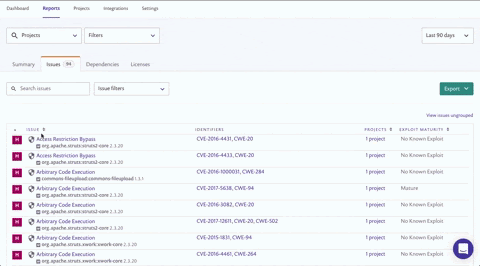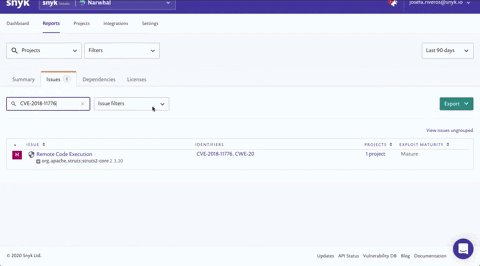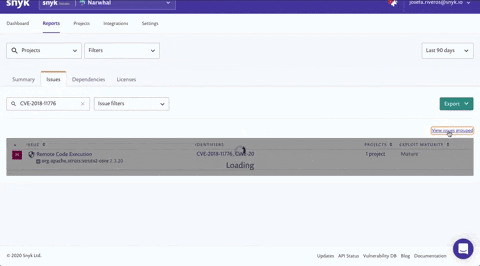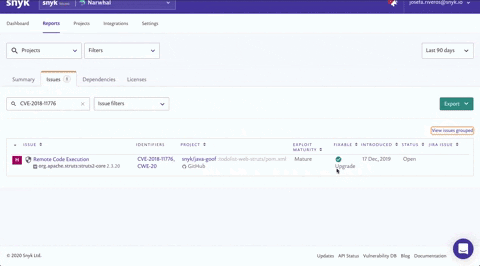
Customers have successfully implemented this technique for prioritization, thereby focusing on a specific vulnerability. We’ve learned they don’t just do this for urgent breaches though — as part of their work routine they often focus on specific vulnerabilities this way as well.
For example, you could ask your team to focus on fixing all of the Arbitrary Code Injection vulnerabilities within your organization. Once all of those are completed, the team can celebrate and pick another vulnerability to move onto.
Fixing vulnerabilities on time
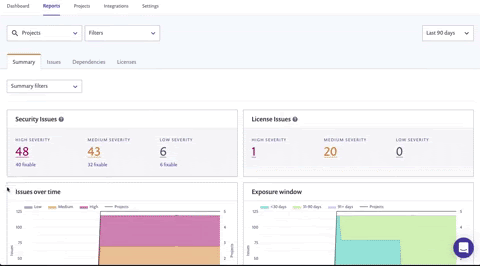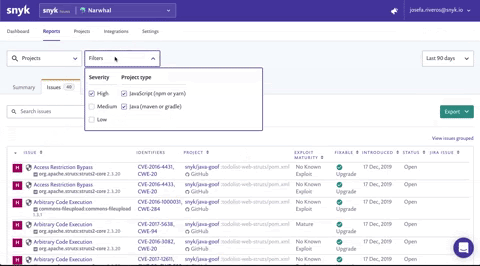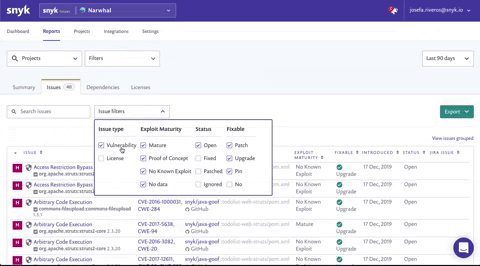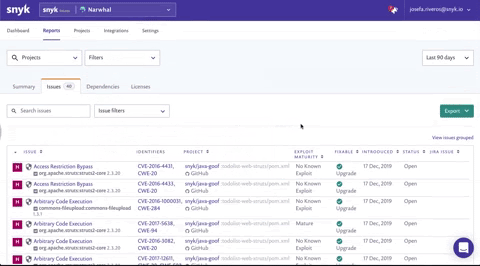
In an ideal world, your organization would never have vulnerabilities open for more than 30 days. But, we know that this isn't always the case — vulnerabilities can accumulate quickly and before you know it, some vulnerabilities have been open for 90, 180, 365 days!
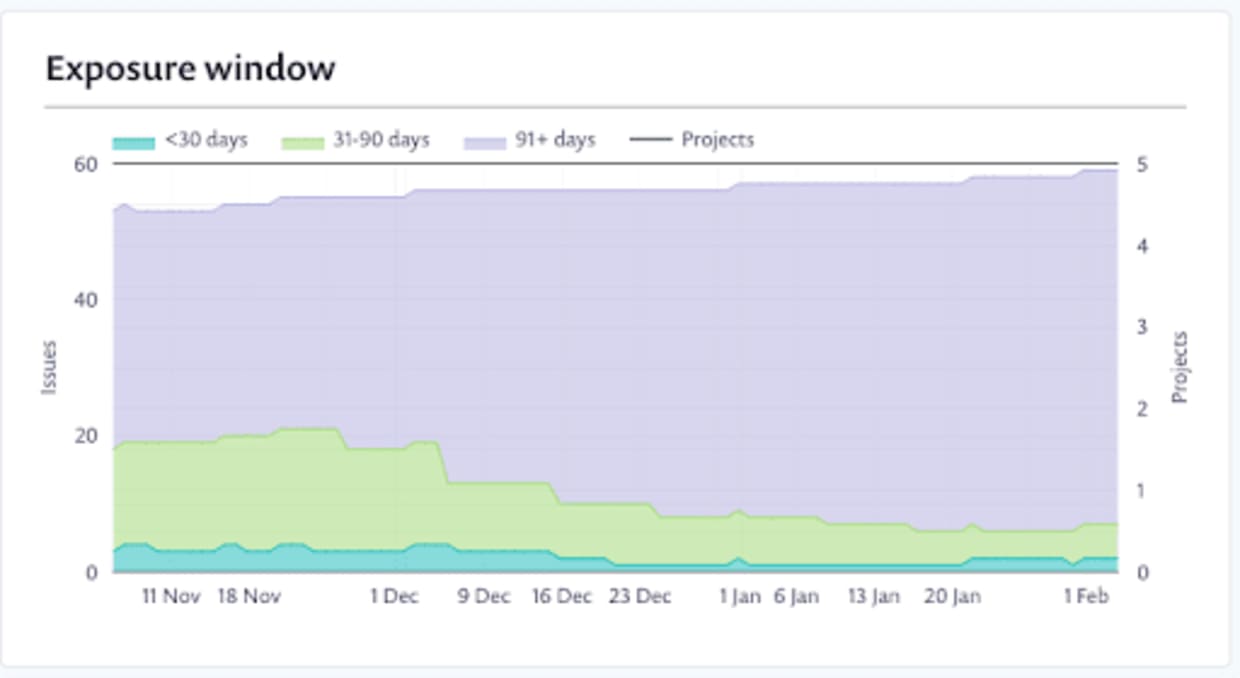
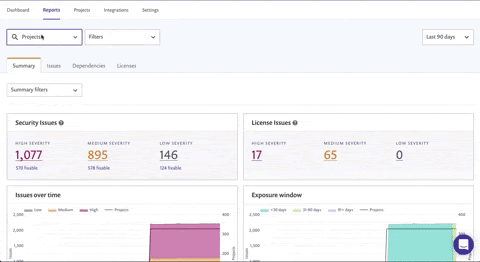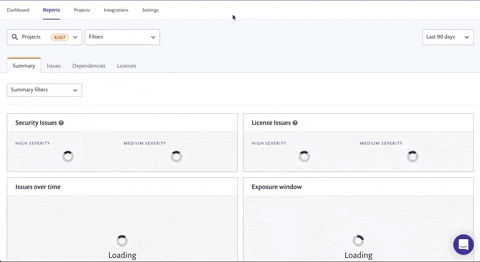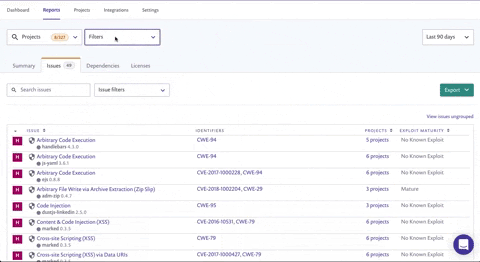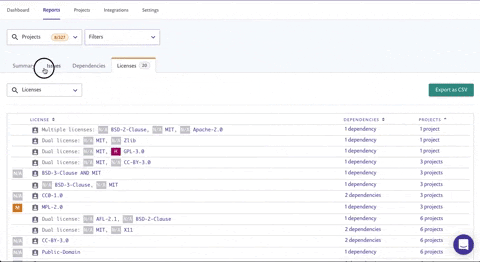
From the Summary tab, the "Exposure window" graph shows you at a glance how long the vulnerabilities in your organization have been open.
Go to the Issues tab, click ungrouped issues within the Issues tab, and view the introduced dates for the vulnerabilities within your organization. You can also sort this column in ascending order, to see which issues in your portfolio are the oldest. By applying a few filters on top of that, such as Open status, Upgrade and Patch fixables, and the Vulnerability issue type, you can identify the fixable vulnerabilities within your organization that have been lingering around for the longest period of time — directing your development teams to focus on clearing out the oldest issues first.
As they work through these issues, you’ll start to see some changes in the exposure window graph as well!
Focusing on your most important projects first
If you’d like to get laser focused on a specific subset of projects that make up a business-critical application for your team, select the corresponding projects from the Projects dropdown along with any of the options in the Filters list, now enabling you to navigate through the different tabs that comprise the entire report area. Now you can easily focus on prioritizing specific vulnerabilities or even take a deep dive into the dependency health (viewing deprecated packages for example), and into the license analysis of that subset of projects.
Beyond filters
This is just a small sampling of some of the reports that you can build directly in our platform. You can always export the information from the Issues tab as a PDF to share directly with colleagues, or export your the data from all reporting tabs as a CSV or via the API to augment and integrate with your own personal reporting tools and to build even more complex reports.
Getting started
Reports are available for Snyk Standard, Pro and Enterprise plans. It’s easy to get started. We’re keen to hear your own tips and tricks!
Happy filtering and stay secure!
Auto-Erkennung und -Fixing von Schwachstellen
Snyk bietet Security-Fixes als Pull-Request mit einem Klick und Korrekturempfehlungen für Ihren Code, Abhängigkeiten, Container und Cloud-Infrastrukturen.