Showing Snyk security information in GitHub code scanning
October 7, 2020
0 mins readLots of Snyk users use GitHubfor hosting their source code. Generally, that means looking in one place (GitHub) for source code, and another (Snyk) for information about vulnerabilities. Snyk has always looked to push security information to where developers are, for instance with local tools (like our CLI and IDE plugins) and with our GitHub pull requests and status checks.
With the launch of GitHub code scanning, we’re happy to be able to further embed security information (Snyk) in the native developer workflow, with updates to our GitHub Actions to support code scanning.
GitHub code scanning
Code scanning adds a new feature to the Security tab in GitHub and is available to all GitHub users as of today. With code scanning, you can hook up all of your security tools in one place and see all the vulnerabilities and security issues related to your repositories.
Code scanning surfaces security issues in your repositories before they reach production. This could be application source code, assets, configuration files, etc.
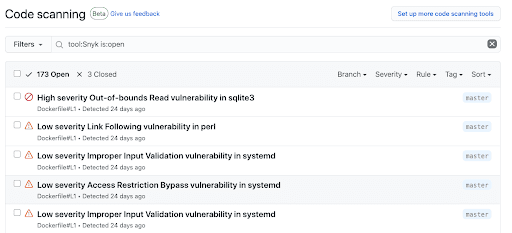
Snyk Container and Snyk Infrastructure as Code
Today both Snyk Container (for scanning container images) and Snyk Infrastructure as Code(for detecting misconfigurations in Kubernetes configuration files and Terraform code) support GitHub code scanning, using our existing Snyk GitHub Actions.
Here’s an example using the Snyk Action to test a Docker image for vulnerabilities, and then uploading a SARIF file to code scanning. SARIF is an open standard from OASIS used by code scanning as the interchange format for security issues.
name: Snyk Container and GitHub Security example
on: push
jobs:
snyk:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Build an image
run: docker build . -t some-image
- name: Run Snyk to check image for vulnerabilities
continue-on-error: true
uses: snyk/actions/docker@master
env:
SNYK_TOKEN: ${{ secrets.SNYK_TOKEN }}
with:
image: some-image
args: --file=Dockerfile
- uses: github/codeql-action/upload-sarif@v1
with:
sarif_file: snyk.sarifSo, with just the three extra lines in our workflow to use the upload-sarif action we can take data from Snyk and upload it to GitHub.
Snyk’s new Infrastructure as Code product also works with GitHub code scanning. Here we can detect misconfigurations in your Kubernetes JSON and YAML files or Terraform code and surface those issues directly in GitHub. The following workflow presents a simple example:
name: Snyk Infrastructure as Code and GitHub Security example
on: push
jobs:
snyk:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Run Snyk to check Kubernetes manifest file for issues
continue-on-error: true
uses: snyk/actions/iac@master
env:
SNYK_TOKEN: ${{ secrets.SNYK_TOKEN }}
with:
file: your/kubernetes-manifest.yaml
- uses: github/codeql-action/upload-sarif@v1
with:
sarif_file: snyk.sarifWith the above workflow up and running we’ll see security misconfigurations from Snyk appearing in GitHub.
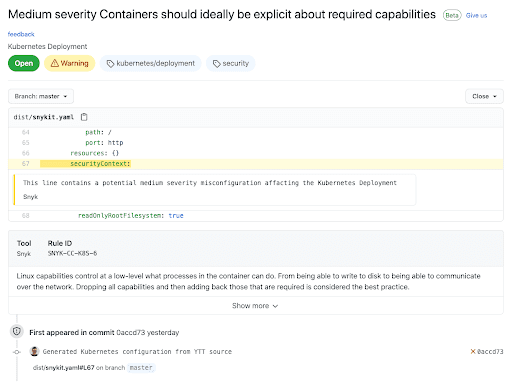
Here you can see details about the issue as well as the context of the line that has the problem and the commit that introduced it.
The Snyk Infrastructure as Code Action currently supports Kubernetes configuration files only, but we’ll be launching support for Terraform soon, and other configuration formats later.
Next steps
Please try out the Snyk GitHub Actions and new GitHub code scanning support and let us know what you think. We have some great ideas already about improving the Actions and expanding the GitHub code scanning support to all of Snyk’s functionality. Watch this space for even more features than embed security in the heart of the developer workflow.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
