Snyk brings infrastructure as code security to HashiCorp Terraform Cloud
Sarah Conway
May 4, 2022
0 mins readIn our mission to make Terraform Cloud workflows more streamlined and secure, we’re excited to announce our new native integration into HashiCorp Terraform Cloud. This integration embeds the security expertise and developer-friendly fixes of Snyk Infrastructure as Code (Snyk IaC) directly into Terraform Cloud, making the Terraform Cloud workflow one of the safest ways to provision and manage public cloud infrastructure.
In this blog post, we’ll cover why we built this, what a workflow in Terraform Cloud with the Snyk IaC run task looks like, and offer resources to quickly get started with improving your IaC security in every Terraform run task.
Why integrate with Terraform Cloud?
As the use of infrastructure as code continues to grow, development teams are increasingly tasked with writing and maintaining more configurations. But with growing usage comes increased risk. Developers are increasingly responsible for the security and compliance of their cloud deployments as well.
The problem is that knowing how to provision infrastructure securely is a major hurdle for development teams. The Snyk State of Cloud Native Application Security Report found that 69% of respondents had a misconfiguration or known unpatched vulnerability in their cloud native applications.
We built the Snyk Terraform run task integration to help developers more easily find and fix IaC misconfigurations and noncompliant security issues while they’re coding, reducing the risk of insecure infrastructure well before it’s deployed. This developer-first approach helps Terraform Cloud users securely define and manage cloud infrastructure across all major cloud providers, including AWS, Azure, and Google Cloud.
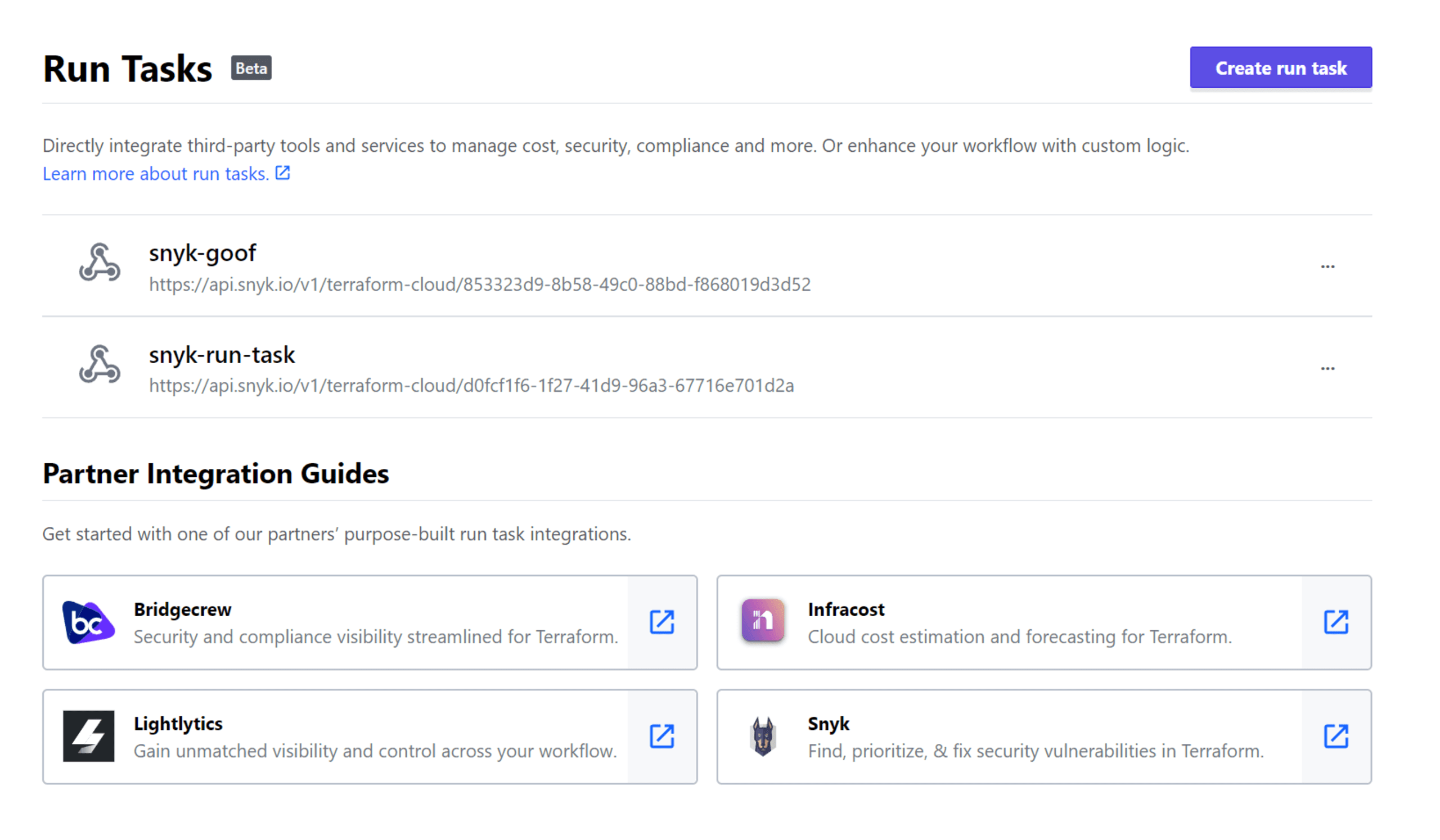
How does Snyk IaC automate security and compliance in a run?
Snyk IaC scans configuration files for Terraform and provides immediate feedback related to security and compliance. This helps developers prevent cloud misconfigurations early on — and throughout the delivery process — so they can ship more secure configurations in less time.
Snyk scanning uses static analysis to compare IaC files against its predefined set of security rules, which are based on industry standards, cloud provider best practices, and threat modeling exercises of new and emerging threats from Snyk security engineers.
Along with these rules, Snyk takes custom policies into account when scanning for potential misconfigurations in Terraform files.
What does a Snyk run task in Terraform Cloud look like?
The Snyk integration for Terraform Cloud enables development teams to scan Terraform Plan JSON files — which are previews of potential infrastructure changes — and compare the output against best practice security policies for all major public cloud providers and Kubernetes. Compatibility with Terraform Plan files also enables Snyk to improve security for other tools that output these files, such as Terragrunt and Atlantis.
More importantly, scanning Terraform Plan files, rather than individual files, allows developers to take a collective look at proposed changes to the infrastructure and minimize the risk of post-deployment surprises. The Terraform Plan file incorporates all modules and variables, offering a comprehensive picture of what the infrastructure will look like rather than relying solely on the resources specified in the individual configuration files.
In short, by using the Snyk run task in Terraform Cloud as a gate in your run, misconfigurations are automatically discovered before proposed changes are applied to the existing cloud infrastructure. This enables developers to shift IaC security left and make Terraform security an integral part of the development process.
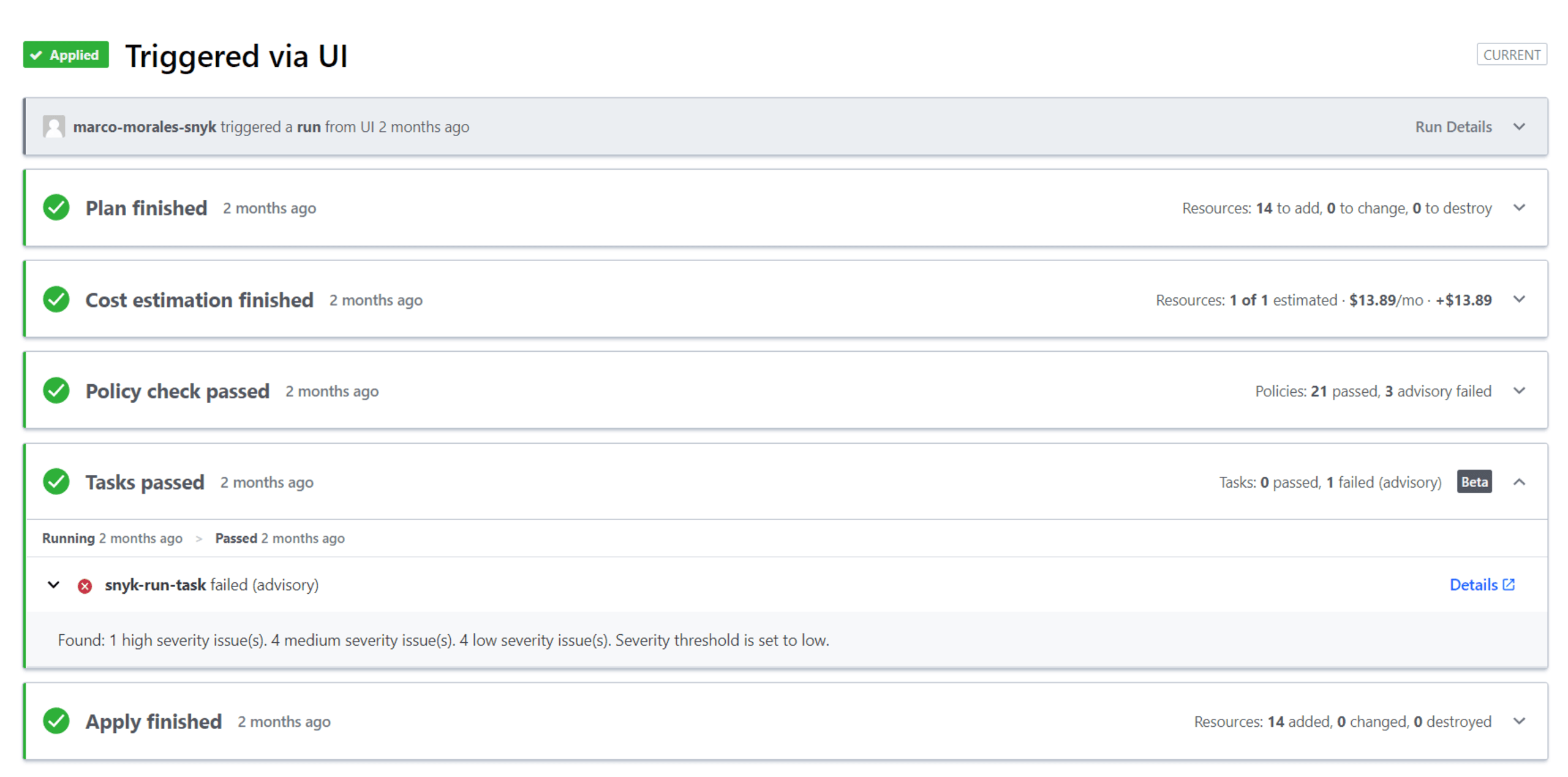
You can additionally customize the level of enforcement of your Snyk run task by choosing between Advisory — pausing and informing the user of failure — or Mandatory — which halts a run until a fix has been applied.

Customize enforcement level of policies to pause or prevent an Apply.
For every misconfiguration or noncompliance issue, there is structured security context and fix guidance geared towards the developer in Snyk. Get the issue, impact, and suggest fix in-line with the Terraform code in question.
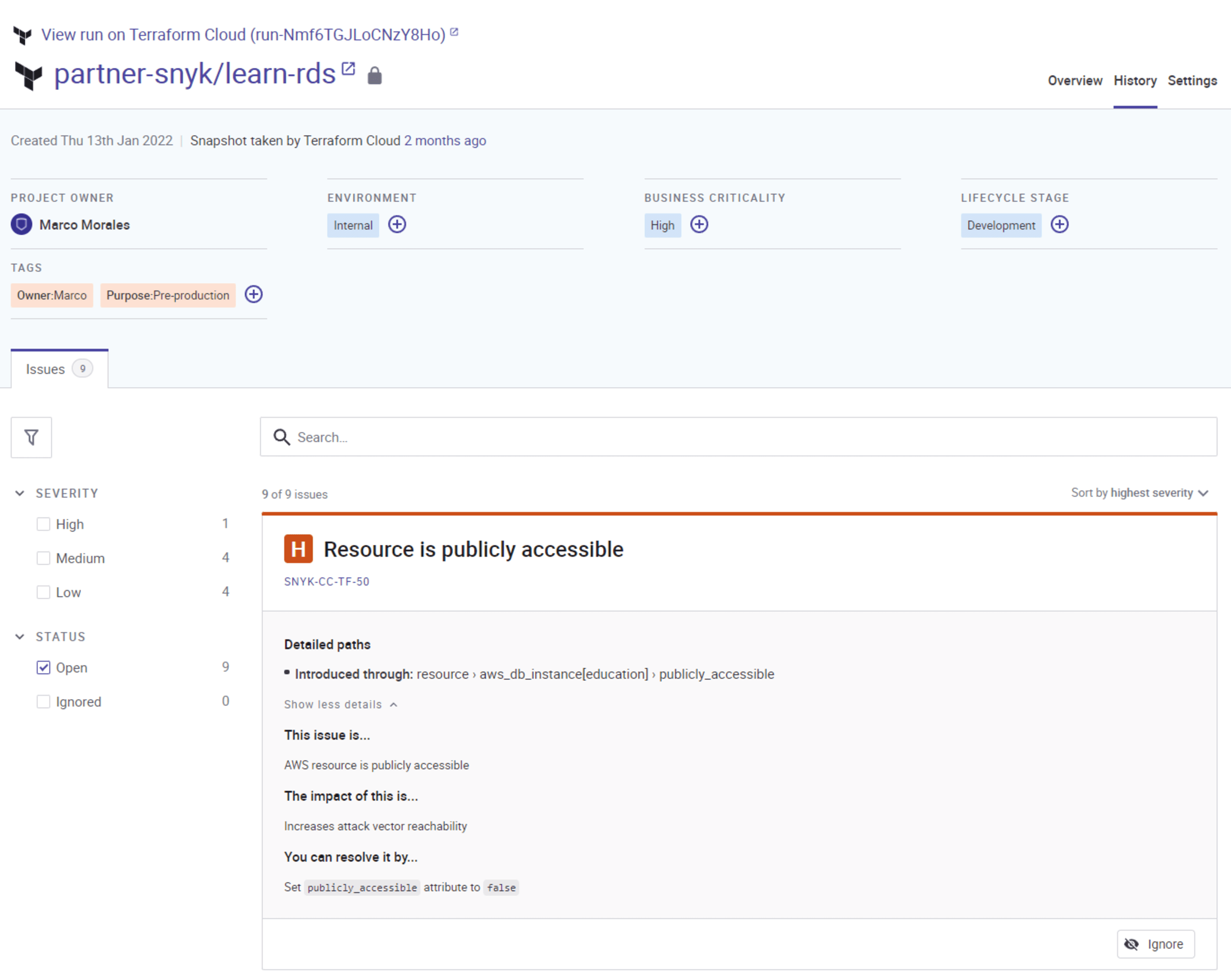
Resources for getting started with Snyk in Terraform Cloud
As part of Snyk’s effort to help developers solve configuration security issues, Snyk and HashiCorp created the 5 Best Practices for Securing Terraform Configurations cheat sheet to enable organizations to improve their IaC security and leverage policy as code with the Snyk run task for Terraform Cloud.
To get started, use our Streamline your IaC Security with Snyk and HashiCorp quick start guide to help your development teams quickly implement the Snyk and Terraform Cloud integration for detecting security vulnerabilities and enforcing security policies in minutes.
Secure infrastructure from the source
Snyk automates IaC security and compliance in workflows and detects drifted and missing resources.
