Improved risk assessment with EPSS scores in Snyk
Daniel Berman
May 22, 2023
0 mins readThe number and complexity of software vulnerabilities is continuously growing. The ability of development and security teams to assess the threat level a given vulnerability poses and prioritize fix efforts accordingly greatly depends on access to as much context as possible about the vulnerability.
Snyk has always made it a priority to provide our users with the security intelligence needed to not only identify potential vulnerabilities in their applications but also be able to prioritize and fix them with as broad a context as possible. This is why we are happy to announce the addition of EPSS (Exploit Prediction Scoring System) to Snyk’s security intelligence for Snyk Open Source and Snyk Container vulnerabilities.
The latest EPSS model (EPSS v3) information is available starting today in the Snyk Vulnerability Database, and will gradually become available in additional Snyk worfklows such as the Snyk App UI, API, and reporting throughout the year.
What is EPSS?
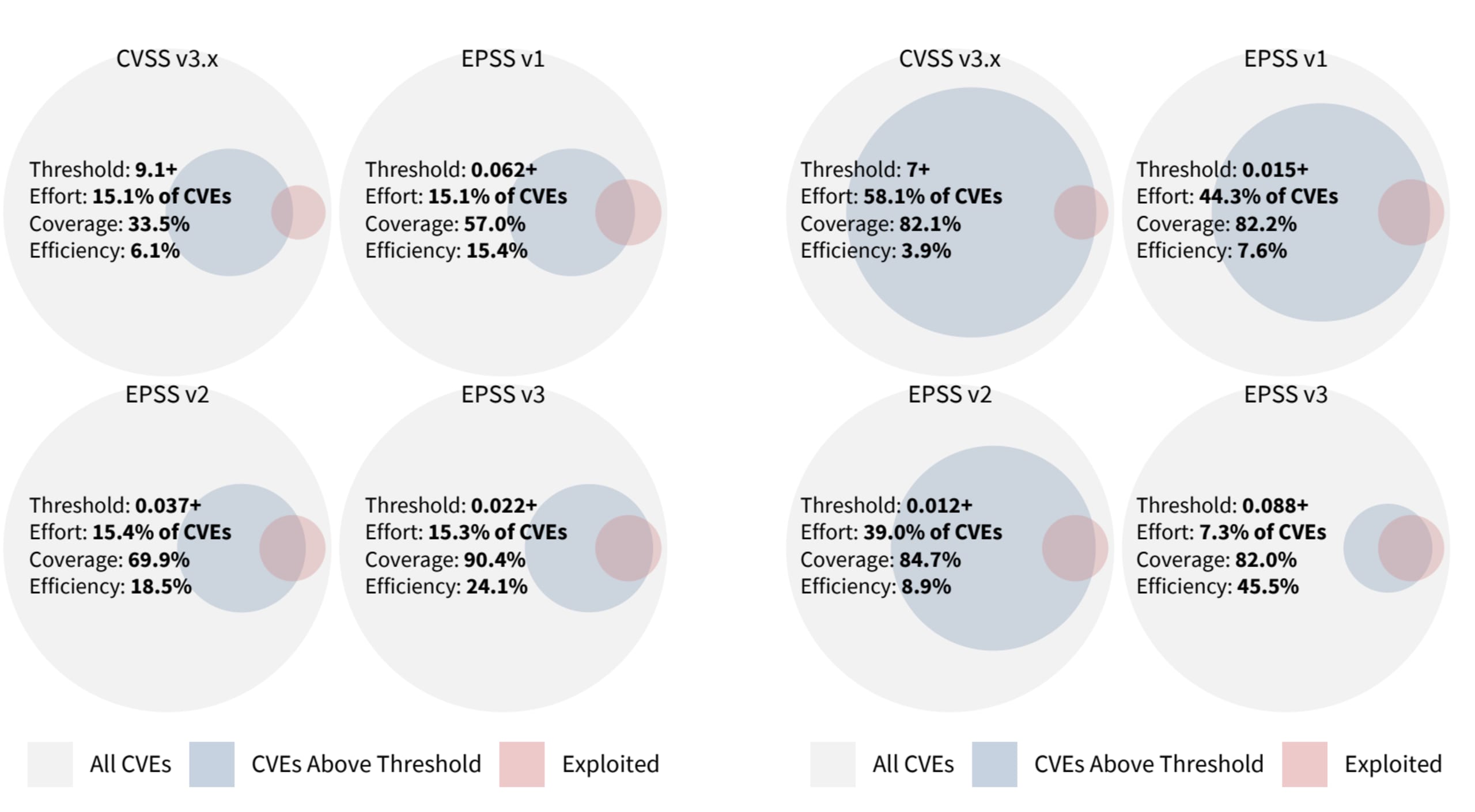
The FIRST-backed EPSS SIG (special interest group) was officially formed in 2020 with the goal of “assisting network defenders to better prioritize vulnerability remediation efforts.” The problem that the group of volunteer researchers and practitioners managing the project identified was that existing industry standards, such as CVSS, might be useful for measuring the severity of a vulnerability, but they are limited in their ability to assess the actual threat that it poses.
What does EPSS scoring do?
EPSS estimates the likelihood of a vulnerability being exploited, assigning it a probability score between 0% and 100%. The higher the score, the more likely the vulnerability will be exploited in the wild within a time period of the next 30 days. EPSS also places that score in context by producing a percentile, which is the proportion of vulnerabilities that are scored at or less than the vulnerability which therefore also indicates the level of threat the vulnerability poses.
The EPSS scores and percentiles are produced on a daily basis for all published CVEs. Currently, the scores can be downloaded as a CSV via a direct HTTP request from EPSS’s data and statistics webpage. There is also an API that can be used to consume the data.
How does EPSS compare with CVSS?
The Common Vulnerability Scoring System (CVSS) is a framework designed to capture the characteristics of a vulnerability and create a numerical score reflecting its severity (Low, Medium, High and Critical).
Both frameworks aim to help organizations tackle the same challenge — the challenge of prioritization — and they both are open frameworks, making their data publicly available for use at no cost. The key difference between the two lies in their approach, and understanding this difference is important when considering whether the two are mutually exclusive.
CVSS attempts to provide a standardized measurement of the severity of a vulnerability based on three metric groups: Base, Temporal, and Environmental. These metrics are meant to be calculated together in a sequential manner to produce a 1–10 score which determines the severity level assigned to a vulnerability. In reality, though, given the complexity involved in adding Temporal and Environmental metrics into the model, most organizations make do with using the Base Score, which, as CVSS documentation points out, is not enough to assess actual risk:
The CVSS Base Score should be supplemented with a contextual analysis of the environment, and with attributes that may change over time by leveraging CVSS Temporal and Environmental Metrics. More appropriately, a comprehensive risk assessment system should be employed that considers more factors than simply the CVSS Base Score. Such systems typically also consider factors outside the scope of CVSS such as exposure and threat.
This is the main reason why many security analysts and practitioners take CVSS with a grain of salt, understanding that it should be used together with additional context and information to better understand the level of risk posed by a vulnerability and prioritize fix efforts.
EPSS (as explained above) was designed to address this limitation in the CVSS framework. It is based on a data-driven machine learning model that combines current threat information from the CVE database with real-world exploit data pulled from multiple sources to predict the likelihood of a threat occurring.
CVSS | EPSS | |
Maintainer | FIRST | FIRST |
Score range | 0-10 | 0%-100% |
Score meaning | Severity of a vulnerability | Likelihood of a vulnerability being exploited in the next 30 days |
Data sources | Base, temporal and environmental metrics calculated into score | Variety of sources used to train an ML-powered model, including historical vulnerability data and daily exploit data |
Updates | Latest version: CVSS 3.1 (released on June 2019) | Scores are updated on a daily basis via an ML-powered process. The model itself is updated periodically. |
How does EPSS work?
EPSS uses a machine learning model to produce the score. To train this model, EPSS collects data from multiple data sources. This includes data on known vulnerabilities, associated exploits, and other factors that might influence exploitability. Data sources include the MITRE CVE List, NVD (National Vulnerability Database), and various threat intelligence feeds such as Metasploit and ExploitDB.
This data is then combined to train the EPSS prediction model and to ensure it can successfully predict the likelihood of exploitation for new, previously unseen vulnerabilities. As new vulnerability and exploit data becomes available, the model is updated to ensure its accuracy and relevance.
The first version of the model was released in 2021, and the latest update to the EPSS was released March 2023 (EPSS v3 or v2023.03.01). The latest model offers significant prediction results with improved efficiency.
Using EPSS with Snyk
As mentioned above, EPSS scores have been added to open source vulnerabilities listed on the Snyk Intel Vulnerability Database. When examining a specific CVE, the EPSS score is displayed in the Threat Intelligence box on the right-hand side of the page:

As seen in the example above, other than displaying the main EPSS measure of probability (0.04% in this case), Snyk is also displaying the percentile (6th percentile), which reflects probability relative to all other scores.
If you’re building application on top of Snyk CLI, EPSS scores can also be seen when viewing vulnerabilities as a JSON file.
Moving towards a more holistic risk assessment model
EPSS estimates the probability that a vulnerability will be exploited. But more than understanding what EPSS is, it is also important to understand what EPSS is not.
EPSS does not factor in additional environmental factors and it does not estimate the impact of a vulnerability should it be exploited. EPSS therefore, as stated by the EPSS SIG itself, “is not, and should not be treated as a complete picture of risk”. It is also worth pointing out that while the EPSS SIG has done an impressive job documenting the project, the model itself is not fully transparent to enable closer evaluation. Still, EPSS can and should be one of the risk factors used when assessing the risk a vulnerability poses and prioritizing, which is why we decided to gradually add it to our vulnerability data.
Looking forward, Snyk is working on a new risk assessment model that will incorporate a much more elaborate and comprehensive risk assessment model. This model will include both CVSS and EPSS, but also a long list of additional contextual risk factors that together inform upon the likelihood of a vulnerability being exploited and the impact in case it is indeed exploited, thus providing a more holistic and risk-based approach to prioritization and issue management.
Stay tuned for news on this!
Developer loved. Security trusted.
Snyk's dev-first tooling provides integrated and automated security that meets your governance and compliance needs.
